Preparing for Hacker Summer Camp and a new cloud image investigator | Datadog Security Labs
This month’s digest covers Hacker Summer Camp prep, a new cloud image investigator, and supply-chain vulnerabilities associated with the Open VSX Registry.
The July edition of the Datadog Security Digest is out!
securitylabs.datadoghq.com/newsletters/...
• Cloud image investigator by @sethsec.bsky.social
• Our top picks for Black Hat / DEF CON
• A benchmark for LLM coding accuracy and security
• Malicious Homebrew installation campaign
.. and more
31.07.2025 21:00 — 👍 4 🔁 1 💬 0 📌 0

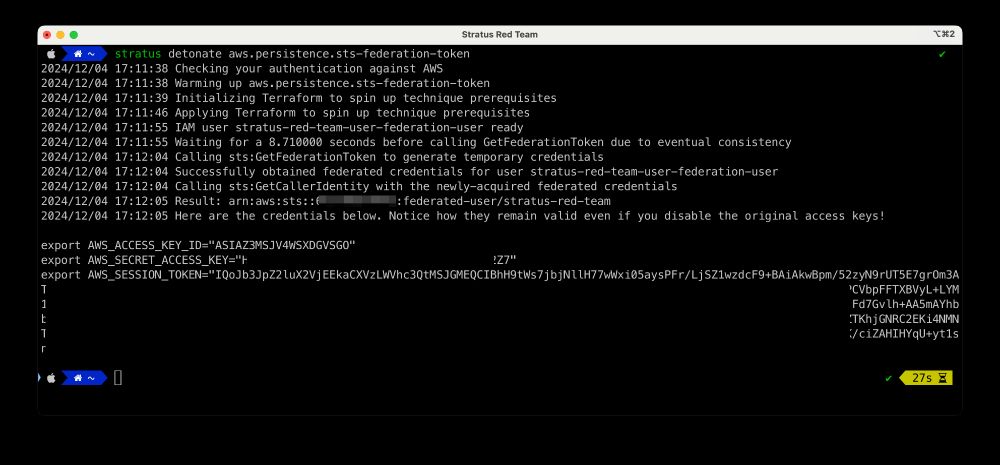
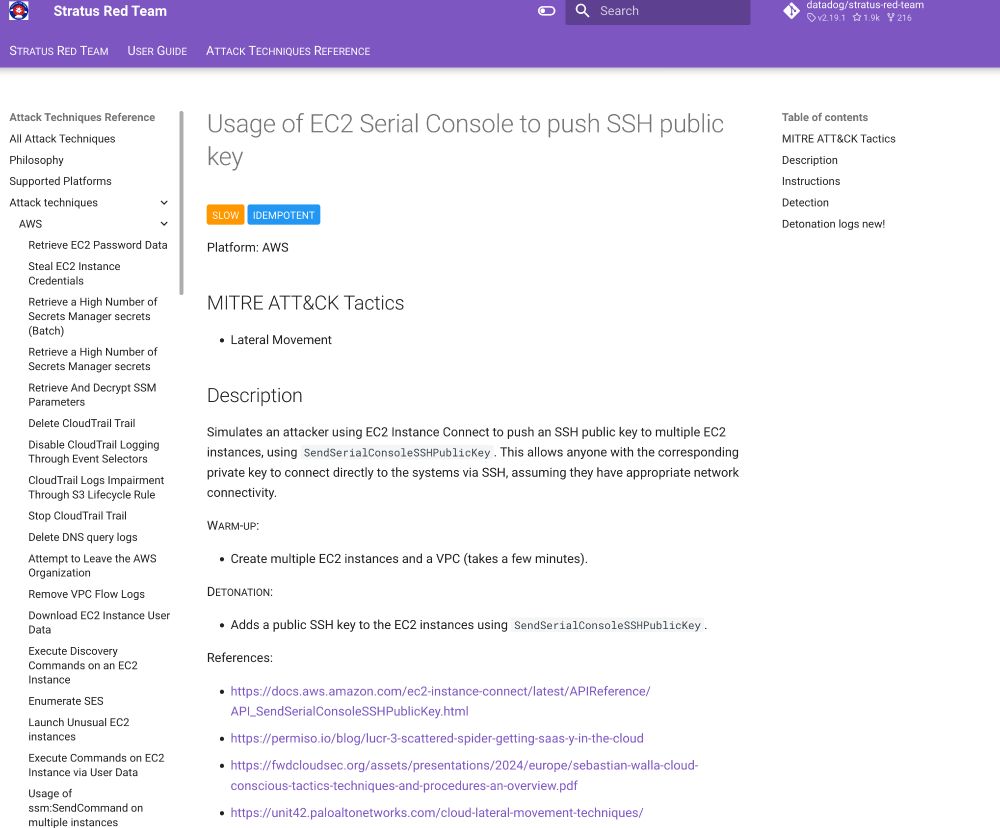
Stratus Red Team AWS attack techniques are now mapped to the Threat Technique Catalog for AWS
Stratus Red Team AWS attack techniques: stratus-red-team.cloud/attack-techn...
Threat Technique Catalog by AWS: aws-samples.github.io/threat-techn...
23.06.2025 12:04 — 👍 6 🔁 2 💬 0 📌 0
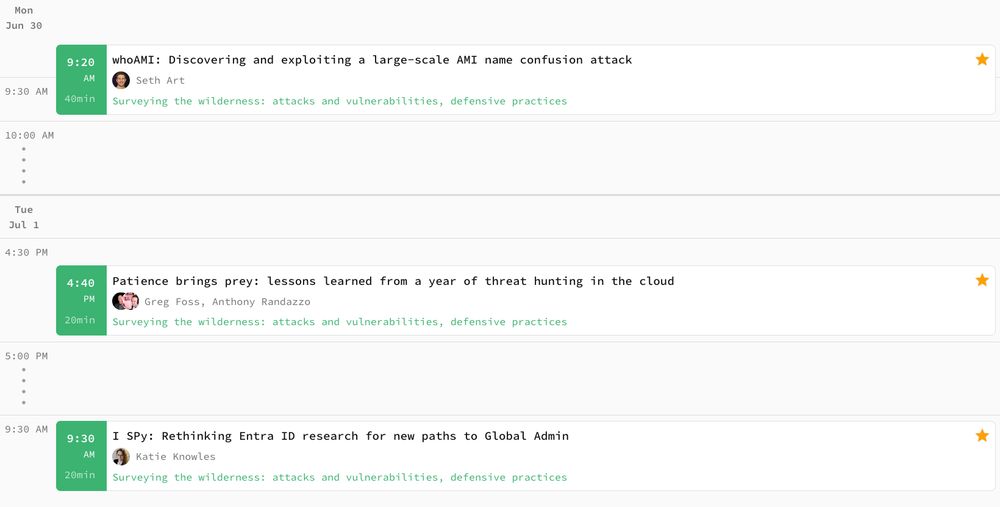
fwd:cloudsec is around the corner! Don't miss these 3 talks from Datadog researchers Seth Sec, Katie Knowles, Greg Foss, and Anthony Randazzo.
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
27.06.2025 21:02 — 👍 4 🔁 2 💬 0 📌 0

Tales from the cloud trenches: The Attacker doth persist too much, methinks | Datadog Security Labs
A cloud attack targeting Amazon SES and persistence via AWS Lambda, AWS IAM Identity Center and AWS IAM
"Tales from the cloud trenches: The Attacker doth persist too much, methinks"
securitylabs.datadoghq.com/articles/tal...
New tactics observed include:
• Persistence-as-a-service with an external facing API Gateway
• Persistence through AWS SSO
• ConsoleLogin events from Telegram IP addresses
15.05.2025 14:15 — 👍 10 🔁 2 💬 0 📌 1
GuardDog: Strengthening Open Source Security Against Supply Chain Attacks – Open Source Security Foundation
My colleague, Sebastian Obregoso, and I had the privilege of writing a guest post for OpenSSF's blog on how we detect malicious open source packages at @securitylabs.datadoghq.com using GuardDog.
Check it out here: openssf.org/blog/2025/03...
01.04.2025 10:14 — 👍 2 🔁 1 💬 0 📌 0
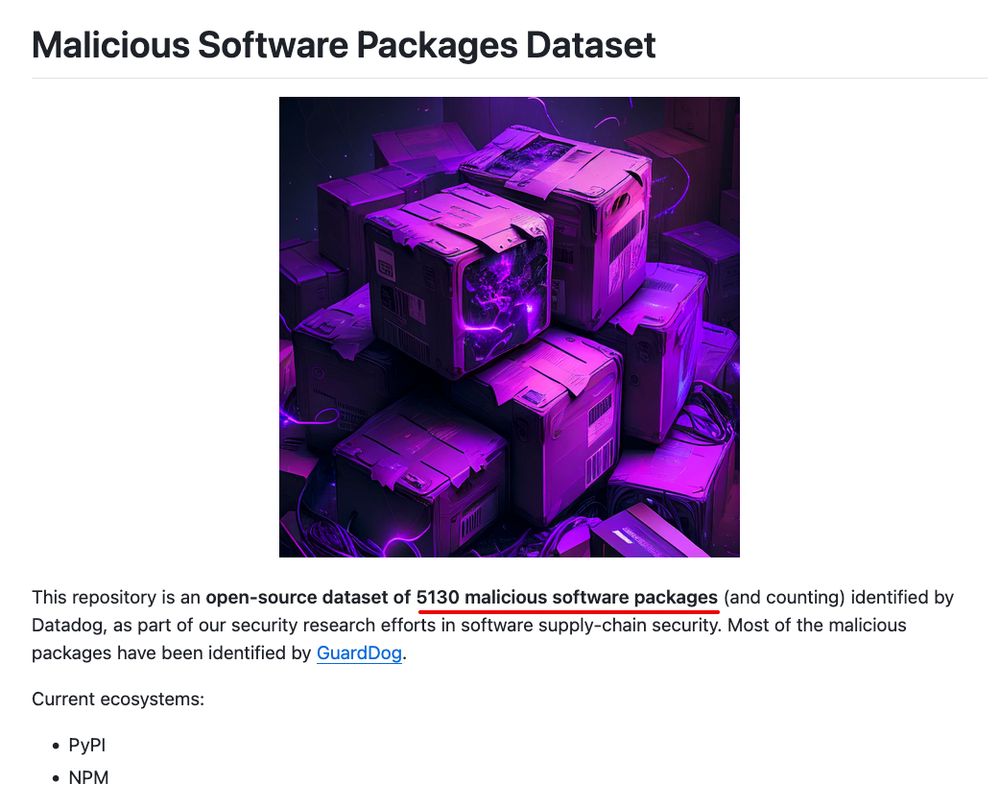
Interested in malicious software packages? Our open-source dataset just hit over 5,000 samples of malicious npm and PyPI packages!
github.com/DataDog/mali...
04.03.2025 09:06 — 👍 4 🔁 1 💬 0 📌 0
Last May we shared our research on using AWS non-production endpoints for a variety of attack scenarios against AWS environments. These endpoints are easy to find and provide options for an adversary to evade detection. More recently, we have partnered with AWS to find 1/x
26.02.2025 18:11 — 👍 6 🔁 2 💬 1 📌 0

The Datadog Security Digest is a monthly, practitioner-focused newsletter.
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...
26.02.2025 11:55 — 👍 5 🔁 4 💬 0 📌 0
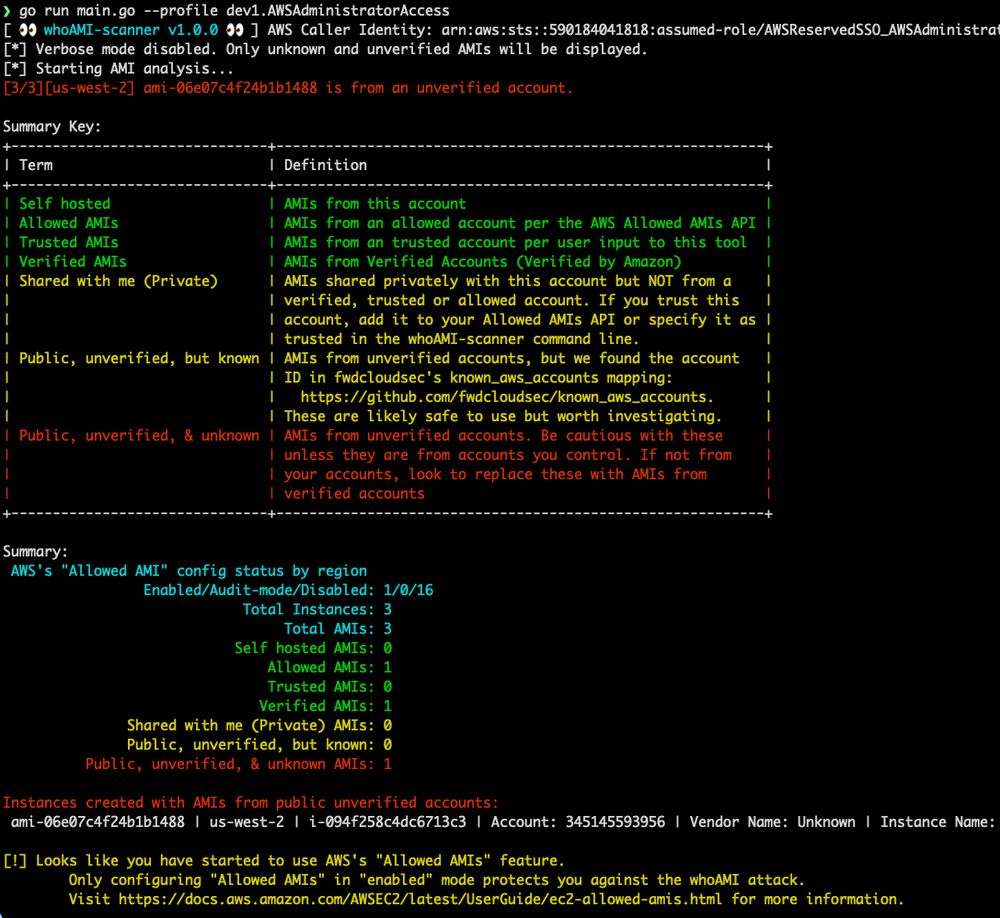
We're also releasing a new open-source tool, whoAMI-scanner, to scan for malicious AMIs in your environment!
github.com/DataDog/whoA...
12.02.2025 15:29 — 👍 2 🔁 0 💬 0 📌 0
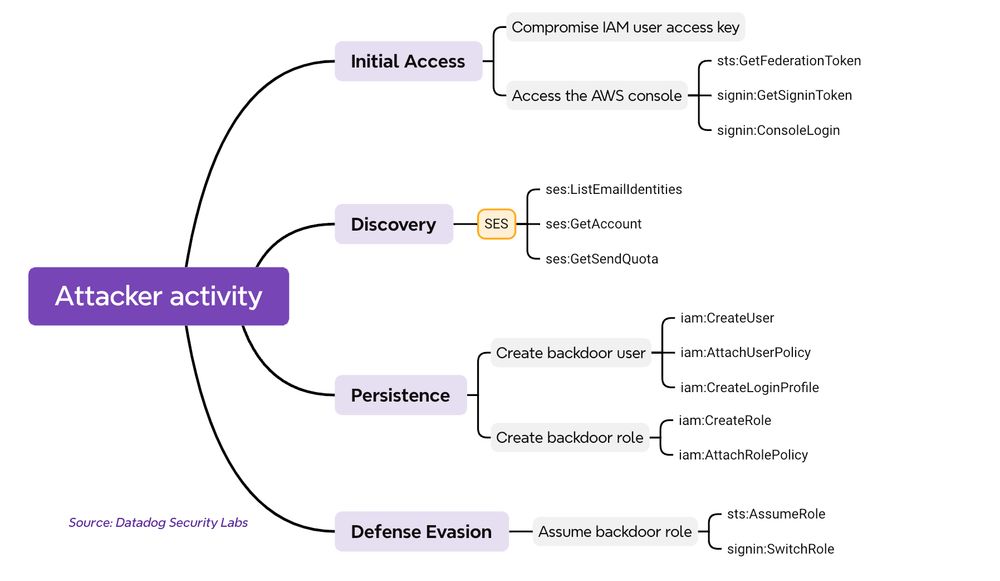
"Tales from the cloud trenches: Unwanted visitor"
securitylabs.datadoghq.com/articles/tal...
This post describes an attacker that we've observed in the wild, including a malicious AWS account ID used to create a backdoor IAM role.
11.12.2024 21:43 — 👍 20 🔁 6 💬 0 📌 0
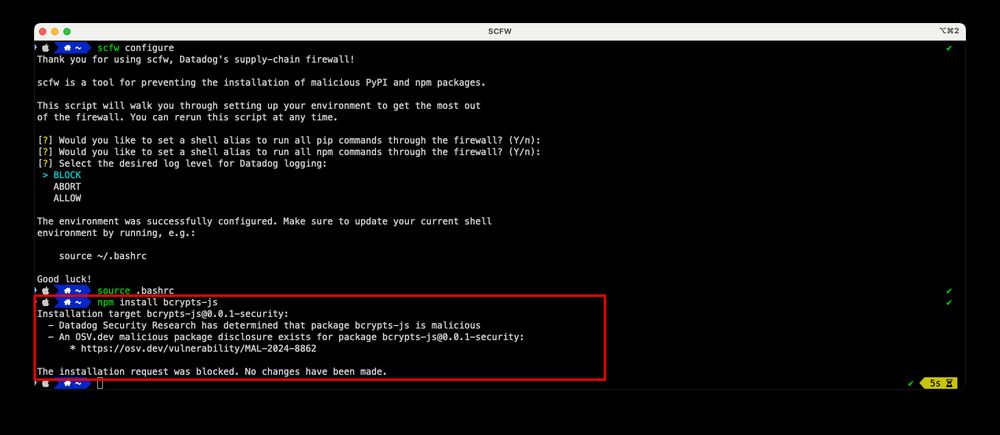
YouTube video by AWS Events
AWS re:Invent 2024 - Beyond just observing, protecting your whole software supply chain (SEC406)
Watch Andrew Krug and Zack Allen's (@techy.detectionengineering.net) talk at re:Invent 2024 on software supply-chain security, featuring our open-source projects Guarddog and SCFW, along with insights on real-world malicious packages
www.youtube.com/watch?v=1b0R...
11.12.2024 09:56 — 👍 3 🔁 0 💬 0 📌 0
 06.12.2024 12:33 — 👍 1 🔁 0 💬 0 📌 1
06.12.2024 12:33 — 👍 1 🔁 0 💬 0 📌 1
Security Researcher @ Datadog
Mainly malware analysis and cloud security
Security Research @ Datadog
Software & tech enthusiast living in Switzerland, working @ Datadog. Opinions on all sorts of things, some of them reasonable.
Hardening for food. Open Source, Cloud and Security. Giving 🖤 to Prowler since 2016. Linux, DFIR, CISSP, Heavy Metal. Del Atleti. http://prowler.com
Security and Kubernetes @ AWS
Building https://wut.dev (AWS explorer & security debugging platform). Cloud Security EM @Stripe. Ex-Founder @CloudSploit_, acquired by @AquaSecTeam. Ex-Adobe.
Process isolationist, k8s hacker, ᴎo-prem pusher, syscall denier, container liberator
🔸Chainguard - Product Security
🔸Rochester 2600, IOIOIO Security
🔸Former: Snowflake, NCC Group, Hackerspace starter, BSidesROC Founder
Application Security | Security Research and Advocacy @ Datadog
Expect the unexpected with cloud canaries | https://tracebit.com
👷♂️ Building micro-SaaS on AWS
🛡️ bucketAV - Virus Scan for S3
🛠️ HyperEnv - self-hosted GitHub runners
🦠 attachmentAV - Virus Scan for Atlassian + Salesforce
🚨 marbot - Alerts and Notifications for Teams
🌍 Sharing my learnings at cloudonaut.io
Building on and breaking cloud, container, and app sec things. He/Him.
@__steele on the bird site. Lefty, in every sense of the word. AWS Hero, I mostly post about cloudy things and silly projects I’ve worked on. I also post photos of my dog, Mulan. He/him.
Your Friendly Cloud Antagonist
Proficient at drawing the rest of the 🦉
Just another cloud consultant.
Cloud security historian.
Developed http://flaws.cloud, CloudMapper, and Parliament.
Founding team for fwdcloudsec.org
Principal Cloud Security Researcher at Wiz.
Head of Research @ Reversec - cloud security, automation, DevOps and attack detection. Opinions are my own.
security, for the internet, at Wiz
opinionated about security.
knowledge hubs at rami.wiki, thoughts at ramimac.me
Cloud security, hacker, run/bike/drown, TK11940 in the 501st, itinerant disaster paramedic, private pilot, and other stuff. @rmogull on Signal
SVP of Cloud Security at FireMon. CEO of Securosis. Both totally made up titles.
https://slaw.securosis.com























 06.12.2024 12:33 — 👍 1 🔁 0 💬 0 📌 1
06.12.2024 12:33 — 👍 1 🔁 0 💬 0 📌 1