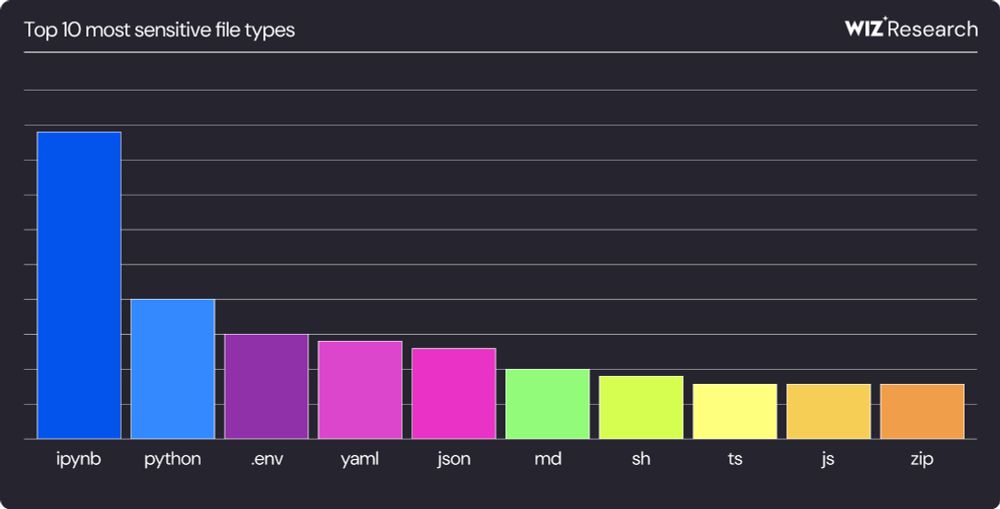
🚨 We scanned GitHub and found *hundreds* of valid secrets, 4 of the top 5 were AI-related:
HuggingFace, Azure OpenAI, Weights & Biases, and Groq.
Read more:
www.wiz.io/blog/leaking...
@ramimac.me.bsky.social
security, for the internet, at Wiz opinionated about security. knowledge hubs at rami.wiki, thoughts at ramimac.me

🚨 We scanned GitHub and found *hundreds* of valid secrets, 4 of the top 5 were AI-related:
HuggingFace, Azure OpenAI, Weights & Biases, and Groq.
Read more:
www.wiz.io/blog/leaking...

> We've set up a web endpoint so vetted ... security researchers can submit suspected exposed credentials for review
> To report exposed Google Cloud credentials, please contact gcp-credentials-reports@google.com
cloud.google.com/blog/product... really buried the lede!

In light of recent GitHub Actions incidents (Ultralytics, tj-actions...), I wrote up a practical guide to hardening for @wizsecurity.bsky.social
Covers permissions, secrets, 3rd-party Actions, ++
Use it to avoid learning these lessons the hard way:
www.wiz.io/blog/github-...

Synthesized 20+ sources and internal @wizsecurity.bsky.social expertise to come out with a comprehensive guide to MCP security
Today's options, and tomorrow's possibilities
www.wiz.io/blog/mcp-sec...

🎙️ New episode!
Our own @ramimac.me helps dive into GitHub supply chain attacks, IngressNightmare, and Oracle breach rumors.
Tune in for the latest cloud security insights!
🎧 podcasts.apple.com/us/podcast/q...

It's been awesome getting to team up with @ramimac.me to dig into a new AWS feature! Read our thoughts on AWS's new CloudTrail network activity events (aka VPC endpoint logs): www.wiz.io/blog/aws-vpc...
20.03.2025 15:45 — 👍 9 🔁 2 💬 0 📌 0
Turns out when you investigate a compromised Github Actions you ... find another compromised Github Action:
www.wiz.io/blog/new-git...
Very fun to help put final polish on this report in week 3 at Wiz - anecdata is fun, data is funner :)
06.02.2025 19:19 — 👍 5 🔁 1 💬 0 📌 0
New year, new job!
I've joined the amazing @wiz_io research team
My goal is the "work for the security industry, at Wiz"
I wrote a blog post explaining why, and what that means:
ramimac.me/joining-wiz

Lately, every BSides seems to have a talk on reframing security teams as a “Department of Yes”
We don’t hear nearly as much about the value of a well-considered, strategically deployed “No”
I've pulled together guidance on giving a better, more constructive No:
ramimac.me/saying-no
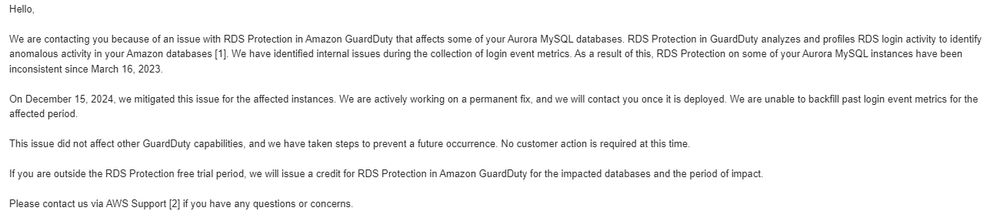
Keep an eye out for notices - AWS RDS Protection for Guardduty seems to have had some issues collecting logs.
Unclear how pervasive this was!

reminds me of ramimac.me/poisoning-ss... 😉
24.12.2024 12:12 — 👍 2 🔁 0 💬 0 📌 0
One recent report highlighted that roughly a third of their customers have “at least one cloud workload that is publicly exposed, critically vulnerable and highly privileged.”
If you’re this vendor, should I really buy your product?
ramimac.me/state-of-clo...

I've spent dozens of hours reading State of Cloud Security reports
You know, the ones that use data from their CSPM product
And I've realized the findings substantially reflect how well that tool helps customers secure their clouds
I wrote up some examples, both good and bad (🔗 in 🧵)

I (finally) wrote up my thoughts on "Founder Mode" and the Brian Chesky morality tale about how he turned around Airbnb company culture.
This has made it into the Silicon Valley water table; it must be dealt with. There are some good nuggets within; let's dig them out.
charity.wtf/2024/12/17/f...
www.cybok.org/media/downlo...
18.12.2024 10:43 — 👍 3 🔁 0 💬 1 📌 0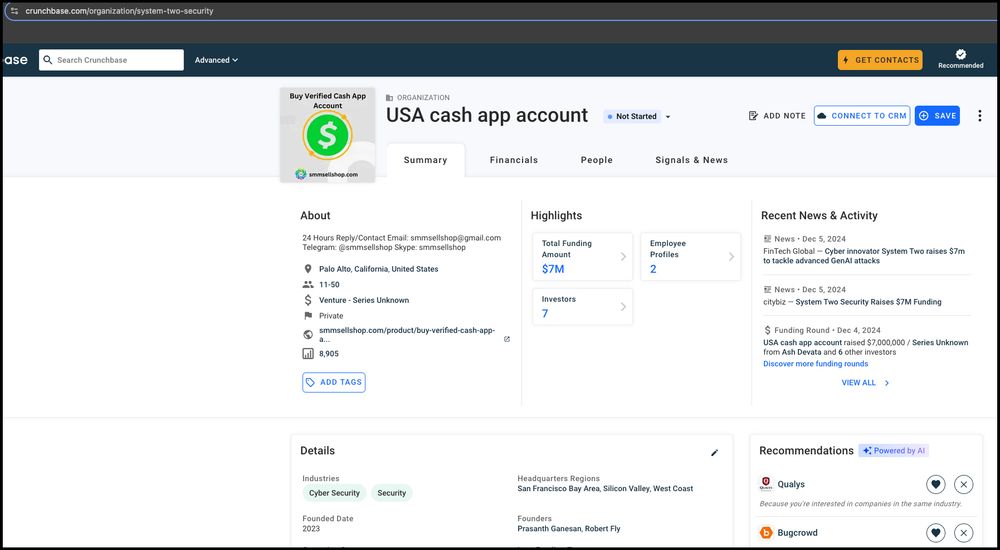
New Threat Vector Unlocked
1. Find the Crunchbase page of a cybersecurity company that just raised VC funding
2. Change the page details (which anyone with a Crunchbase account can do) to a personal CashApp page
3. ????
4. Profit! (?)

Somehow <50 people have caught this talk from Coinbase's CSO??
His core advice:
1. Make lives easier - e.g roll out yubikeys
2. Define Security Invariants
3. Plan & Practice IR
4. Balance Risks & Threats
5. Security is a People Problem - use focus groups for new controls!
youtu.be/BPh4Hc3TH74
Just keep dm'ing them to me so I can bully you into publishing 😈
09.12.2024 11:14 — 👍 2 🔁 0 💬 0 📌 0Interesting research out of AWS!
> IAM-PolicyRefiner, a tool that automatically synthesizes refined AWS IAM access control policies from access logs
> fast (<5s per policy), effective and does not overfit
Not open source, but maybe a sign of things to come?
assets.amazon.science/cf/bc/58e56f...
IIRC, re:Inforce was a bust for security announcements.
I wish some of these announcements got time center stage there, versus being pre:Invent announcements now.
Hopefully re:Invent makes space alongside the GenAI noise!
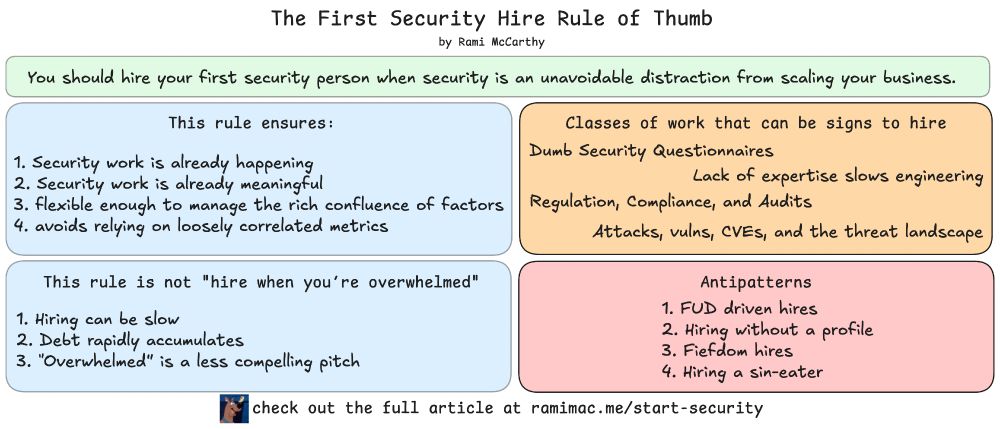
I've been chatting a lot re:when to make the first security hire" recently
I've come up with a Rule of Thumb:
Hire your first security person when security is an unavoidable distraction from scaling your business
ramimac.me/start-security
h/t @grims.bsky.social & @mag00.bsky.social
This webinar will be more relay-race than sparring match when it's with folks like @nanook.bsky.social and @jamesberthoty.bsky.social!
19.11.2024 06:55 — 👍 3 🔁 0 💬 0 📌 0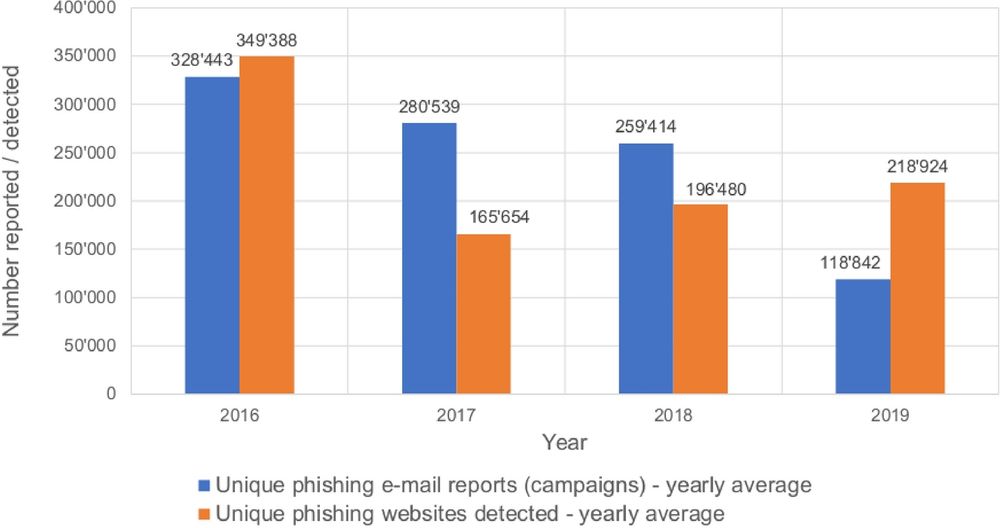
I think it's pretty easy to dig up research that ties phishing simulations to a decrease in metrics like Click Through Rate or improvement in "awareness" - but I'd argue those aren't the metrics that matter!
Ex. hcis-journal.springeropen.com/articles/10....
I love when new research comes out to back up my "phishing training is bad practice" priors:
www.computer.org/csdl/proceed...
I track the latest evidence against phishing simulations: rami.wiki/phishing-sim...

Wondering “What Does Success Look Like?”
Check out the book!
There is incredible depth, detail, and color provided that I can only hint at in this format: www.oreilly.com/library/view...
Thank you to Camille and Ian for sharing their expertise
“Saying “No” Without Ruining the Relationship”
- “Not yet, priority call” → give options and how they can help
- “Not yet, technical call” → take time to explain the details
- “No, product strategy call” → accept shadow IT or alternative platforms
- “No, technical call” → beware magical thinking
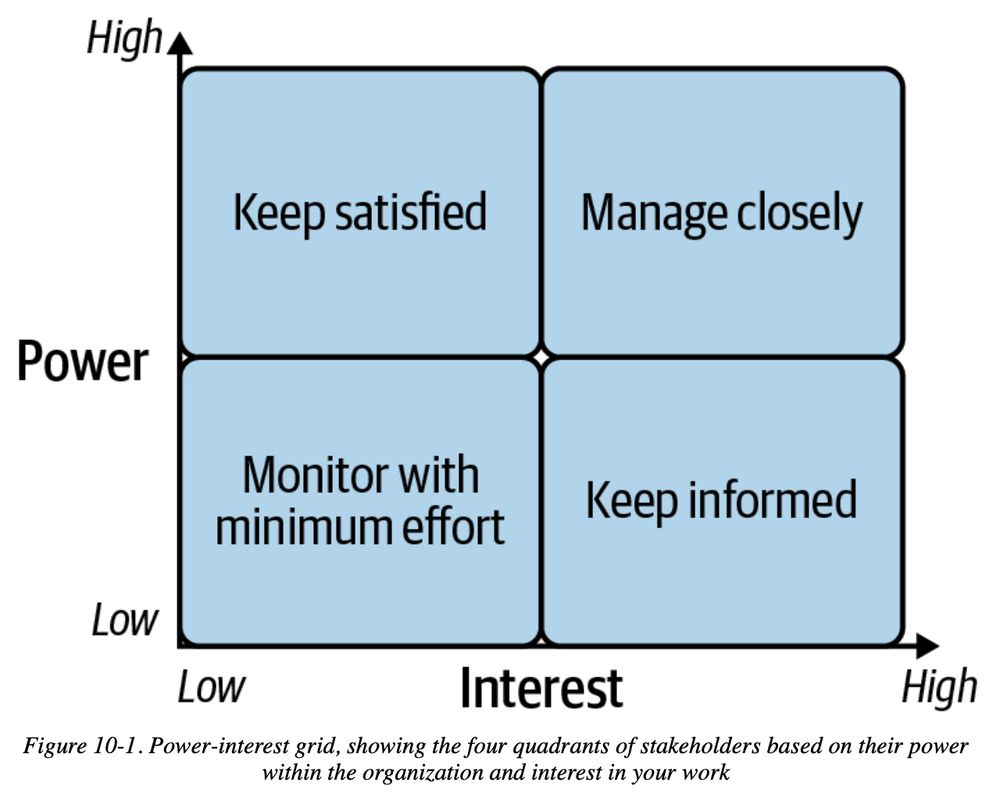
high power + low interest = keep satisfied low power + low interest = monitor with minimum effort high power + high interest = manage closely low power + high interest = keep informed
Use the handy-dandy power-interest grid to prioritize stakeholder management!
18.11.2024 11:54 — 👍 1 🔁 0 💬 1 📌 0📦 Tips & Tricks for Migrations
* Minimize Glue and Limit Variation
* Transparent Migrations
* Usage Metadata
* Automate as much as possible
* Focus documentation on on-ramps and off-ramps
“If you don’t end up regretting your early technology decisions, you probably overengineered. -Randy Schoup”
Don't do a v2 (Pioneer mindset, new features, and scale don't mix!), just change the plane's engine in midair.
Rearchitect with a focus on “reliability, features, efficiency, and security”