
gopengraph
A Go library to create BloodHound OpenGraphs easily
github.com/TheManticore... by @podalirius.bsky.social

gopengraph
A Go library to create BloodHound OpenGraphs easily
github.com/TheManticore... by @podalirius.bsky.social

See your network shares the way attackers do. 👀
Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale.
@podalirius.bsky.social unpacks all the details in our latest blog post. ghst.ly/4ogiBqt
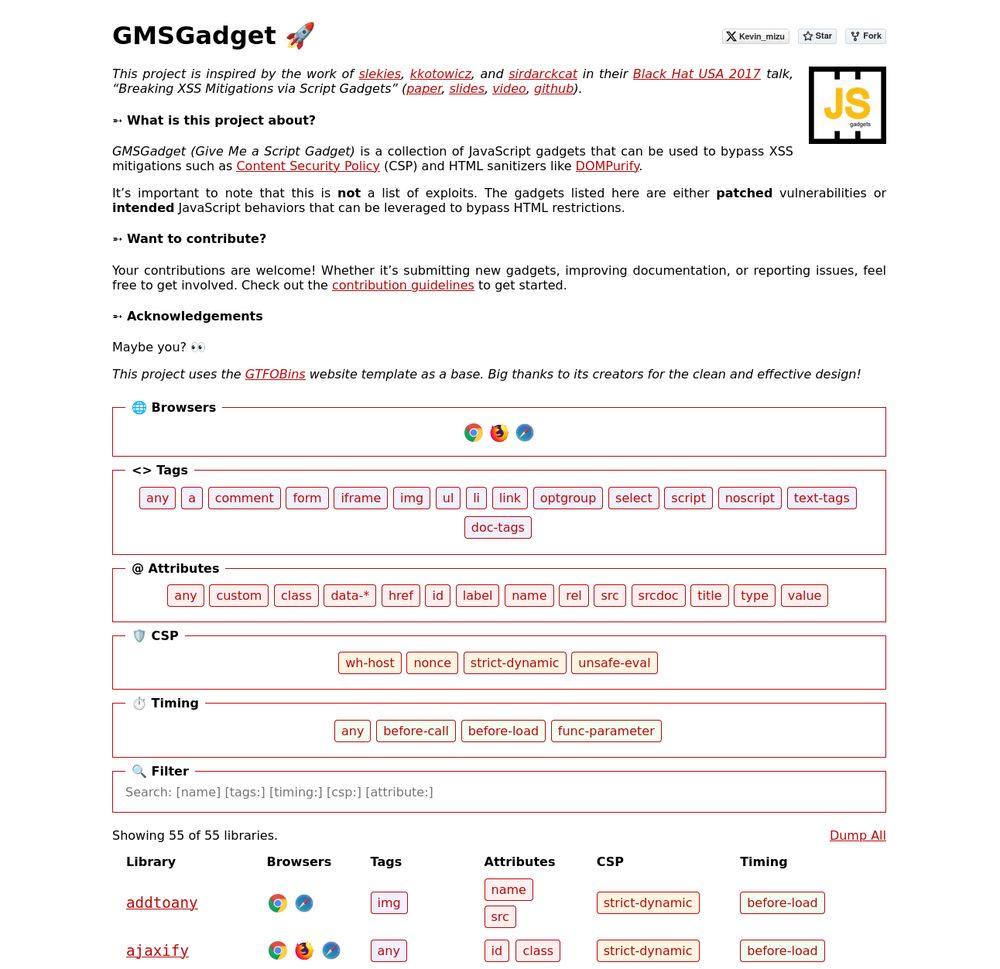
I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Hat USA 2017 talk! 🔥
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4

🔍 New tool in The Manticore Project: LDAPWordlistHarvester
This tool allows you to create precise wordlists for finding passwords of users in an Active Directory domain using its LDAP data.
➡️ github.com/TheManticore...

🚀 New pentest tool drop: FindGPPPasswords 🚀
A cross-platform tool to find & decrypt Group Policy Preferences passwords from SYSVOL with low-privileged domain accounts!
🔗 Check it out on GitHub: github.com/p0dalirius/F...

🚀 New Tool Release: DescribeNTSecurityDescriptor 🚀
Analyzing Windows NT Security Descriptors can be a headache. I built DescribeNTSecurityDescriptor, a cross-platform tool to decode, parse & visualize them easily!
🔗 GitHub: github.com/p0dalirius/DescribeNTSecurityDescriptor
OMG, Orange Tsai released his latest new research 🤯 💣
blog.orange.tw/posts/2025-0...

Few BloodHound python updates: LDAP channel binding is now supported with Kerberos auth (native) or with NTLM (custom ldap3 version). Furthermore, the BH CE collector now has its own pypi package and command. You can have both on the same system with pipx. github.com/dirkjanm/Blo...
02.01.2025 16:41 — 👍 29 🔁 14 💬 2 📌 0
New module on #NetExec : wam
Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀
Thanks @xpnsec.com for the technique! More info on his blog : blog.xpnsec.com/wam-bam/

I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

How does the new iOS inactivity reboot work? What does it protect from?
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
My current offline Web reading setup works quite well 😎
And I'll explain below how it works 🛠️🧵⬇️

LDAPmonitor by @podalirius.bsky.social - Monitor creation, deletion and changes to LDAP objects live during your pentest or system administration!
github.com/p0dalirius/L...
#infosec #pentest #redteam

Check out this free of charge recipe of how to loot bugs in Windows CHM parser. Not for the buck, but for the fun. Because fuzzing is fun. Never did fuzzing before? Just follow the article.
Crashing Windows CHM Parser in Seconds Using WinAFL!
Article Highlight #1 - check it out in Paged Out #3 page 53
pagedout.institute/download/Pag...

Issue #3 is here after a long wait, new and shiny. You can download it here pagedout.institute?page=issues..... Tell us what you think.
18.12.2023 09:18 — 👍 2 🔁 3 💬 0 📌 0
In my latest article, discover the depth of the msDS-KeyCredentialLink attribute used in ShadowCredentials attacks and how to parse it. Plus, discover a Python library, pydsinternals, that simplifies the parsing process.
Check it out ⤵️
podalirius.net/en/articles/...
You are doing your pentest engagements from a Windows machine? #LDAPWordlistHarvester is now available in powershell!
➡️ github.com/p0dalirius/L...
Happy password cracking!
Today I'm releasing #LDAPWordlistHarvester, a new tool for generate a wordlist based on the LDAP, in order to crack passwords of domain accounts. 🥳
➡️ github.com/p0dalirius/L...
The generated wordlist cracked way more passwords than rockyou2021 on my latest client.

Today I'm releasing the powershell version of #ExtractBitlockerKeys, aimed at system administrators.
You can backup your BitLocker recovery keys in CSV or JSON.
➡️ github.com/p0dalirius/E...

I wrote a new tool to extract all the Bitlocker recovery keys of computers enrolled in a Windows domain!
This is really useful in post-exploitation or system administration (to backup keys for example). Export in XLSX, SQLITE, JSON
github.com/p0dalirius/E...
Here is an example: