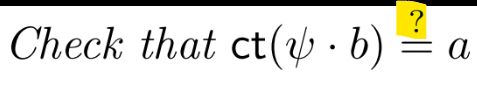The EU Parliament has published a new proposal for Chat Control to mass-surveil all digital communication in Europe. The proposal is ineffective, weakens secure communication, and violates basic human privacy. This must be stopped immediately. #ChatControl
csa-scientist-open-letter.org/Sep2025
09.09.2025 11:11 — 👍 23 🔁 14 💬 1 📌 2
Really happy to have Jens Groth visiting us in Tartu and giving a seminar on ZK, zkVMs, and AI on Tuesday
17.08.2025 15:41 — 👍 8 🔁 1 💬 1 📌 0
This is some mind-blowing stuff :o
16.07.2025 15:39 — 👍 1 🔁 0 💬 0 📌 0
No idea. Looking at the source, it should've been easy to figure out that these are intentional
16.07.2025 12:46 — 👍 1 🔁 0 💬 0 📌 0
It took me a moment to understand what is the issue :D
16.07.2025 11:39 — 👍 1 🔁 0 💬 1 📌 0
There are a few other results in the paper. Such as how to consider imperfect oracles etc.
11.06.2025 14:18 — 👍 0 🔁 0 💬 0 📌 0
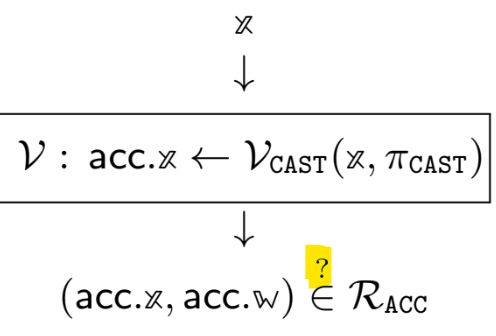
Our original intention was to show that Uber assumption reduces to n-PDL (just like in the algebraic group model, but now in the standard model.) However, this we show to be impossible with any generic reduction (such as den Boer-Maurer reduction).
11.06.2025 14:18 — 👍 0 🔁 0 💬 1 📌 0
Our paper with Roberto Parisella and Maiara Bollauf was accepted to CiC. We extend DL <=> CDH reduction by den Boer and Maurer.
In particular, we show that in BLS12-381 n-PDL (Power DL) is equivalent to n-Diffie-Hellman exponent assumption.
11.06.2025 14:18 — 👍 6 🔁 0 💬 1 📌 0
"By the national bibliometry rules, conference papers are not counted in the most important reporting processes. Thus, we are strongly incentivised with money to publish research in venues where the impact is lower."
That was surprising to read. I hope it will change.
30.05.2025 15:18 — 👍 1 🔁 0 💬 1 📌 0
New accepted paper at Crypto 2025:
"On Knowledge-Soundness of Plonk in ROM from Falsifiable Assumptions" (Helger Lipmaa, Roberto Parisella, Janno Siim), with ex-students Roberto and @jannosiim.bsky.social (Janno is also now a colleague)
05.05.2025 12:15 — 👍 7 🔁 2 💬 0 📌 1
Thank you 🙂
16.04.2025 18:01 — 👍 0 🔁 0 💬 0 📌 0

Europe’s GDPR privacy law is headed for red tape bonfire within ‘weeks’
Long seen as untouchable in Brussels, the GDPR is next on the list of the EU’s crusade against overregulation.
Europe's most famous technology law, the GDPR, is next on the hit list as the EU pushes ahead with its regulatory killing spree to slash laws it reckons are weighing down its businesses.
03.04.2025 07:34 — 👍 58 🔁 17 💬 12 📌 12
Join us in Tartu to work on SNARKs and ZK proofs. 👇
We intend to build a strong ZK research group here + I think it's a really cool place to live and work: virtualtour.ut.ee/en/84-univer...
28.03.2025 11:59 — 👍 4 🔁 1 💬 0 📌 0
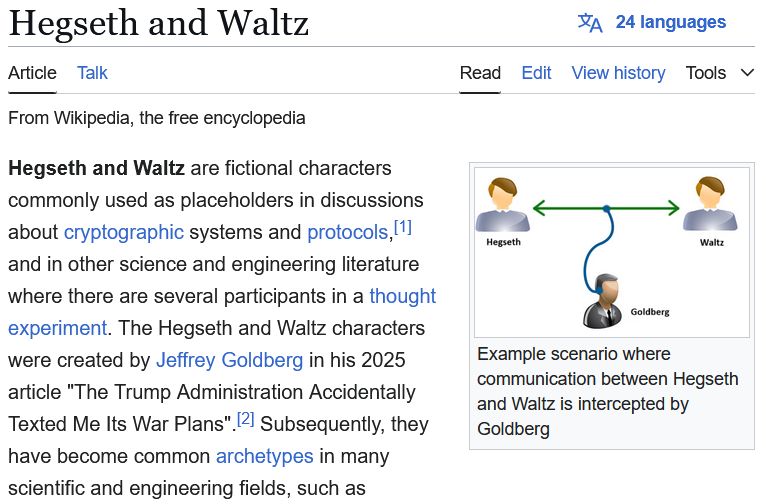
A screenshot of the Wikipedia page for Alice and Bob, but with all occurrences of "Alice and Bob" replaced with "Hegseth and Waltz".
Just doing some reading about the design of cryptographic protocols.
25.03.2025 01:19 — 👍 441 🔁 106 💬 10 📌 5
Cryptography Research Group
Our group in Tartu (me and
@jannosiim.bsky.social
and some PhD students) have additional openings for a postdoc and a PhD student; see crypto.cs.ut.ee/Main/OpenPos... (iacr.org/jobs link will hopefully be up in a few days). Apply by email to me
23.03.2025 10:27 — 👍 8 🔁 3 💬 0 📌 1

In Sofia
23.03.2025 10:24 — 👍 3 🔁 0 💬 0 📌 0

List of ProTeCS accepted talks - Part 1:
- Lazy “Twenty Questions” as a Proof Principle — How a pen-and-paper one-liner becomes an EasyCrypt library (François Dupressoir, University of Bristol)
- Is it better or worse (UC-wise) (Saskia Bayreuther, KASTEL Security Research Labs, Karlsruhe Institute of Technology)
- Special Soundness of Non-Interactive Polynomial Commitment Schemes (Janno Siim, University of Tartu)
- Towards formally verifying the security reductions of the TLS 1.3 key schedule in SSBee (Amirhosein Rajabi, Aalto University)
- What can the Algebraic Group Model tell us about proof techniques in the Generic Group Model? (Jake Januzelli, Oregon State University)

List of ProTeCS accepted talks - Part 2:
- Privacy Proofs for Anonymous Communication Networks (Christoph Coijanovic, Karlsruhe Institute of Technology (KIT))
- Expected (polynomial) time in cryptography (Michael Klooß, Karlsruhe Institute of Technology)
- Commit-and-Prove System for Vectors and Applications to Threshold Signing (Cavit Özbay, Hasso Plattner Institute, University of Potsdam)
- The Power of Halting in Security Games (Igors Stepanovs)
- The Humble Power of the T-tranformation (Hans Heum, Norwegian University of Science and Technology)
The list of accepted talks for ProTeCS 2025 is now online.
We are looking forward to exciting talks about cryptographic proofs and proof techniques. Thanks to everyone who submitted a proposal!
protecs-workshop.gitlab.io/accepted
21.03.2025 21:05 — 👍 11 🔁 2 💬 1 📌 2
Excited to read this :)
21.03.2025 08:32 — 👍 0 🔁 1 💬 0 📌 0
We have extended the submission deadline for the International Workshop on Foundations and Applications of Privacy-Enhancing Cryptography (PrivCrypt) by two weeks to April 4, 2025, AoE. Please help spread the word and consider submitting your work to join us in Munich in Summer 😎
20.03.2025 08:12 — 👍 3 🔁 5 💬 0 📌 0
www.sesame.com/research/cro...
I forgot after one minute that I'm not talking to a human. I guess the movie "Her" is the reality now
12.03.2025 13:21 — 👍 0 🔁 0 💬 0 📌 0
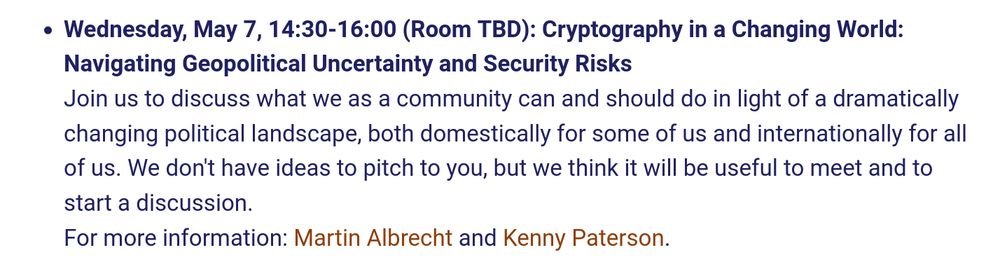
Wednesday, May 7, 14:30-16:00 (Room TBD): Cryptography in a Changing World: Navigating Geopolitical Uncertainty and Security Risks
Join us to discuss what we as a community can and should do in light of a dramatically changing political landscape, both domestically for some of us and internationally for all of us. We don't have ideas to pitch to you, but we think it will be useful to meet and to start a discussion.
For more information: Martin Albrecht and Kenny Paterson.
Together with @kennyog.bsky.social we're organising a meeting at Eurocrypt to discuss how the, let's say, "dramatically changing political landscape" affects cryptography and our community, both domestically in some countries but also internationally eurocrypt.iacr.org/2025/communi...
11.03.2025 09:53 — 👍 38 🔁 14 💬 3 📌 1
I hope Google Chrome will use less memory now
06.03.2025 15:01 — 👍 1 🔁 0 💬 0 📌 0
Because of new tariffs, submissions to crypto with a non US author have a 20% reduction to their page limit.
04.02.2025 05:48 — 👍 21 🔁 5 💬 1 📌 1
Today, I started as a crypto lecturer at the University of Tartu. A new life begins🙂
03.02.2025 12:58 — 👍 9 🔁 0 💬 1 📌 1
Really cool result following some of the ideas of our EC24 paper with @helger.bsky.social and Roberto
29.01.2025 11:39 — 👍 4 🔁 1 💬 0 📌 0
I wonder if we can attack more examples where (1) circuits are adaptively chosen by the adversary, and (2) security proof is in the ROM. It always felt like playing with fire (because ROM does not model potential circuit dependence on the hash function), and this work nicely confirms the concern.
27.01.2025 13:40 — 👍 21 🔁 7 💬 0 📌 0
Signal is an end-to-end encrypted messaging app. Privacy isn’t an optional mode, it’s just the way that Signal works. Every message, every call, every time.
Cryptography and ZK. Research Scientist at Offchain Labs.
Web: binarywhales.com
Tenure-Track Faculty at CISPA • Cryptography & Provable Security
🜗 🝒 🝲 crypto as in 'cryptography' 🝳 🝡 🜖
¹ isogenist, co-host SCWpod
² https://durumcrustulum.com, https://www.youtube.com/@durumcrustulum, https://patreon.com/durumcrustulum
Mathematician and cryptographer (do not confuse with cryptobro).
Working at IMDEA Software Institute.
Organizing Eurocrypt 25.
Oviedo->Amsterdam->Aarhus->Aalborg->Madrid.
analyst of bibliometrics and research funding @University of Tartu
Research Fellow at NTU Singapore.
Interested in privacy-preserving technologies, including pairing-based cryptography and post-quantum cryptography
Cryptographer
https://chancharles92.github.io/
Jonathan Rouach
Exec Director - ZKProof.org
CEO - QEDIT
PhD student @EPFL, previously @ETH
Interested in cryptography at large, post quantum and interactive proofs in particular.
Interista alla Prisco.
Security Analyst @ Keysight Riscure; PhD in Cryptography; Leftist marseillais in Netherlands; Mostly ranting about software and politics
The Zero-Knowledge Proofs Standardization Organization
cryptography and pretty proofs | PL-curious | assistant professor @ VU Amsterdam
soechsner.de
Computer engineer (UdelaR) and PhD in Cryptography (ENS-Paris). Currently a postdoctoral fellow at NTT. Nací al oriente del río Uruguay.
https://www.octavio.pk
Professor at the University of Washington, Paul G. Allen School of Computer Science & Engineering @uwcse.bsky.social
Working on cryptography, theoretical computer science, and computer security.
https://homes.cs.washington.edu/~tessaro/
Host and Producer of Our Fake History, the podcast that explores historical myths! ourfakehistory.com
cryptographer, MdC at EURECOM.
https://faonio.eurecom.io
all opinions are my cat's