
This will show you how to use the Security Roles and Glossary standards from The Open Group to overcome these challenges and get some wins on the board!
publications.opengroup.org/s252

This will show you how to use the Security Roles and Glossary standards from The Open Group to overcome these challenges and get some wins on the board!
publications.opengroup.org/s252
This leads to ineffective defenses and internal conflict that threat actors regularly exploit. This session will talk about how we got here and how to get the whole team playing together.
26.02.2026 16:18 — 👍 0 🔁 0 💬 1 📌 0Unfortunately, most of those players don't know their positions, roles, or goals - very few people know what they are supposed to do for security, why it's important, or how to do it.
26.02.2026 16:18 — 👍 0 🔁 0 💬 1 📌 0Security will never be fully effective until everyone does their security job including boards of directors and CEOs, CISOs and CIOs, SOC analysts, everyday users, architects, IT engineers and operations, and more.
26.02.2026 16:18 — 👍 0 🔁 0 💬 1 📌 0Security is like a sports team where very few players actually know they are on the team, only a few of them actually show up for games, and half of those are fighting with each other or playing like they are on the opposing team.
26.02.2026 16:18 — 👍 0 🔁 0 💬 1 📌 0
I am excited to talk about one of my favorite topics at BSides Tampa on May 16!
*Security is a team sport (and we are NOT playing like a team)*
No single solution will ever keep business assets safe from every creative attacker and their learnings/evolution.
end 🧵
Building security resilience is a journey of many steps and learnings, not a single plane flight to a predetermined destination. While we all wish there was a simple shortcut for security, the businesses and technical estates we defend are complex.
09.02.2026 12:53 — 👍 0 🔁 0 💬 1 📌 0Regulatory standards can’t keep up with attackers, network security perimeters aren’t enough, and no single tool or technology can stop determined human adversaries.
09.02.2026 12:53 — 👍 0 🔁 0 💬 1 📌 0Classic security approaches often focus on a perfect end state of compliance, a perfect network configuration, or a “perfect new tool” that fixes everything as their ideal end state.
09.02.2026 12:53 — 👍 0 🔁 0 💬 1 📌 0There is no such thing as a single “silver bullet” solution that solves everything in security (despite what any security vendors may claim 🙂)
09.02.2026 12:53 — 👍 0 🔁 0 💬 1 📌 0
Pursuing perfect solutions is a perfect waste
From Chapter 6 - How to Scope, Size, and Start Zero Trust (Page 78) of www.amazon.com/Zero-Trust-O...
🧵
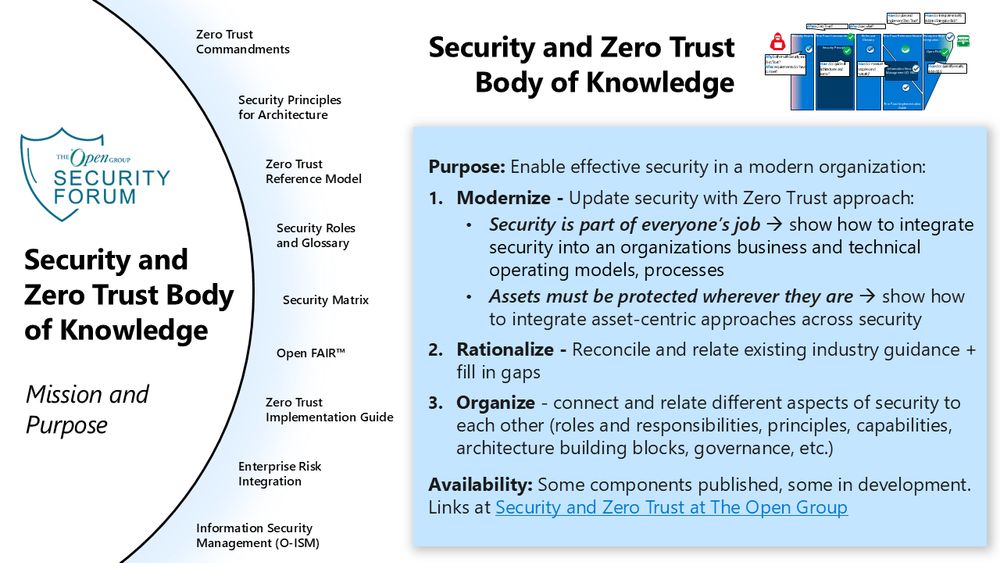
We documented security fiduciary duty and accountabilities in the Security Roles and Glossary Standard Part 2 and Part 3.1 - publications.opengroup.org/s252 (draft standard, feedback welcome). Some more description of this standard is at www.linkedin.com/pulse/securi...
end 🧵
Threat actors damage interests of shareholders and business assets, so leaders have an obligation for security management. Blaming/firing/punishing security experts for events out of their control (criminals exploit risky decisions made by business teams) is NOT effective.
08.02.2026 15:48 — 👍 1 🔁 0 💬 1 📌 0
3b. Fiduciary duty - Relate how security is part of the legal obligation that organizational leaders have to act in the best interest of the shareholders (owners) of the organization.
08.02.2026 15:48 — 👍 1 🔁 0 💬 1 📌 0
3a. Financial terms - Quantify cyber risk using Open FAIR™ or other methods to clearly frames security and its impact in familiar financial terms (but be careful not to devalue human life, safety, health, etc. impacts that go well beyond financial risk).
publications.opengroup.org/t230
2. Intentionally avoiding technical and 'one-time' language (problems and solutions, etc.) in the words and phrases you use to talk about security.
3. Relate security to something they already know:
There are several techniques to correct this misperception:
1. Educating leaders with clear storytelling that describes cybersecurity as crime and espionage on computers (which it is) that clearly requires keeping up with human adversaries

If security leaders describe security (metrics, choice of words, etc.) in technical terms, business leaders will naturally expect it's a technical 'problem (to be solved one time with installation of prevention measures) and not an ongoing business risk/force to be managed.
08.02.2026 15:48 — 👍 1 🔁 0 💬 1 📌 0
Security is often incorrectly perceived as a 'technical problem' that can be 'solved' (it isn't!) by business leaders.
*Security is an ongoing risk that requires ongoing work.*
This misperception is often accidentally created or reinforced by the security team.
🧵
◾ How AI affects every part of security
◾ Top priorities for each security discipline (strategy/integration/governance, architecture, SecOps/SOC, Identity, Data, app/software development, posture management, and more)
This was a short 20 minute talk focused on a few key points and highlights:
◾ Securing AI requires understanding it and how it works (differences from classic software)
◾ What Zero Trust actually is (cybersecurity with changed assumptions/principles)

I just posted my slides from my talk on Zero Trust and AI Security at The Official Cybersecurity Summit in Tampa.
Slides here - www.slideshare.net/slideshow/ai...
Some photos from the event here - www.linkedin.com/posts/jan-br...
Share and Enjoy!
🔹 Movie magic dynamic - They can mimic many aspects of human experience, but it's like a movie or TV show - it looks real and is often useful, but it isn't actually 'real'
I have been tinkering with this visual to capture this - I would love your thoughts and feedback.
end 🧵
🔹 Overconfidence - They are trained on our confident final results, not our internal thought processes that led to the conclusions (whether these are correct, wrong, or a mix).
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0🔹 Machine-like Execution - LLMs and similar tools are like any other machine (execute at scale/speed/etc whether its done well or badly), but its always based on the data they are trained on - human communications and our publications (or AI mimicry of it nowadays).
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0I think of GenAI as a genuinely 'new' entity which remixes a bunch of 'old' things we already know about in a very different way and try to keep in mind how they process (diagram) and their:
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0As we integrate these models, we need to recognize _what they actually are_ and what things they do well and don't do well.
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0▪️ We cannot expect GenAI to act like we have seen in Sci-Fi (CDR Data from Star Trek, 'I, Robot', and others) because most are a purely logical machine (that can talk) who are struggling to learn human social and emotional processing (morals, personal identity, jokes, etc.)
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0▪️ We cannot expect GenAI to have an emotional core/identity/soul with overriding moral imperatives because they are trained on our _expression_ of emotion/identity/etc. and don't actually _feel emotions
27.01.2026 14:23 — 👍 0 🔁 0 💬 1 📌 0