Does HuggingFace spaces give you a DOI? I find services like Zenodo clunky to use but their permanency is often required by the AE process
15.12.2025 21:27 — 👍 0 🔁 0 💬 1 📌 0

Check out the latest from our Labs! Gilbert, in our Browsers team, talks us through how he used one-click memory corruption to exploit a patch-gap in the UC Browser.
www.interruptlabs.co.uk/articles/one...
16.10.2025 14:00 — 👍 2 🔁 2 💬 0 📌 0
Excited to be here with the Interrupt crew!
09.10.2025 11:13 — 👍 0 🔁 0 💬 0 📌 0
Hmm that makes sense. Unfortunately I don’t have a better solution 😕
06.10.2025 17:45 — 👍 0 🔁 0 💬 0 📌 0
I was wondering the same thing the other day! For now I’m just copy+pasting rich text from vs code into PowerPoint, which copies across all the syntax highlighting. I don’t like having code as images.
06.10.2025 07:38 — 👍 0 🔁 0 💬 1 📌 0
Accepted Papers | SURE 2025
Papers and posters accepted for SURE 2025
SURE is proud to announce that we have **9** epic works that have been accepted for presentation at SURE on October 13. Topics span decompilation, (de)obfuscation, debugging, fundamental benchmarks, and more!
sure-workshop.org/pa... (paper links out soon)
17.09.2025 22:56 — 👍 1 🔁 1 💬 0 📌 0
Jeez these are nightmare-inducing
31.08.2025 03:35 — 👍 0 🔁 0 💬 0 📌 0
Oh wow that’s so cool 💜
27.08.2025 07:14 — 👍 1 🔁 0 💬 1 📌 0
GitHub - blacktop/go-hypervisor: Apple Hypervisor.framework bindings for Golang
Apple Hypervisor.framework bindings for Golang. Contribute to blacktop/go-hypervisor development by creating an account on GitHub.
Created Go bindings for Apple's Hypervisor.framework.
Why? Because I wanted to test a Pure Go emulator I'm writing against and couldn't get unicorn2 to work on macOS 26. Plus what's going to be faster than Apple's OWN hypervisor 😎
Check it out! 🎉
github.com/blacktop/go-...
23.08.2025 02:11 — 👍 6 🔁 4 💬 0 📌 0
🛬 I'm at USENIX Security in Seattle this week, where on Friday at 2pm my former postdoc Tristan Benoit will be presenting our paper "BLens: Contrastive Captioning of Binary Functions using Ensemble Embedding," joint work with Yunru Wang and Moritz Dannehl from my group. Here's the gist:
11.08.2025 12:56 — 👍 3 🔁 1 💬 1 📌 0

WOOT '25 Technical Sessions
All sessions will be held in Room 611-612 unless otherwise noted.
WOOT 2025 schedule, all papers are now online open access:
usenix.org/conference/w...
Talks are recorded, and should be online in a few weeks.
11.08.2025 20:56 — 👍 12 🔁 8 💬 0 📌 0
Good luck, and exciting times for XBOW!
30.07.2025 11:13 — 👍 2 🔁 0 💬 0 📌 0
Linux Kernel Hardening: Ten Years Deep
Talk by Kees Cook about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: www.youtube.com/watch?v=c_Nx...
Slides: static.sched.com/hosted_files...
15.07.2025 16:42 — 👍 7 🔁 3 💬 0 📌 0
Oh cool! I’m probably more interested in different frontends; I’ll leave accelerating to the professionals 😄
10.07.2025 02:43 — 👍 2 🔁 0 💬 0 📌 0
GitHub - sandialabs/ctadl: CTADL is a static taint analysis tool
CTADL is a static taint analysis tool. Contribute to sandialabs/ctadl development by creating an account on GitHub.
CTADL - a Datalog-based interprocedural static taint analysis engine for Java/Android bytecode (via JADX) and Pcode (via Ghidra)
Code: github.com/sandialabs/c...
Talk (via @krismicinski.bsky.social): youtu.be/3ec9VfMUVa8?...
09.07.2025 10:10 — 👍 11 🔁 2 💬 1 📌 0
Woah totally missed that CTDL is open source 🥳
09.07.2025 07:49 — 👍 3 🔁 0 💬 0 📌 0
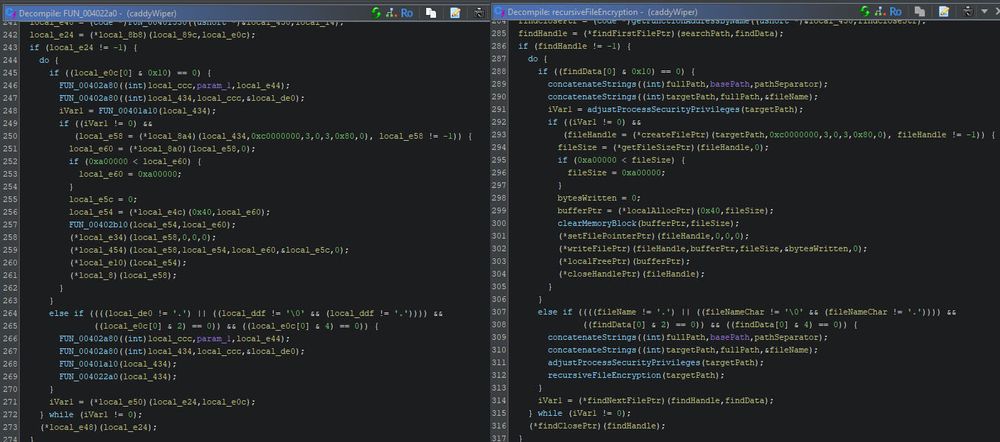
A side by side comparison of the original output by Ghidra, and the LLM enriched output.
Ghidra, scripting, LLM, automagic automation. That should grab the attention for this thread. If you want to read the complete blog, you can do so here: www.trellix.com/blogs/resear...
1/n
01.07.2025 12:35 — 👍 9 🔁 5 💬 1 📌 0

Estimating Correctness Without Oracles in LLM-Based Code Generation
Generating code from natural language specifications is one of the most successful applications of Large Language Models (LLMs). Yet, they hallucinate: LLMs produce outputs that may be grammatically c...
Can we statistically estimate how likely an LLM-generated program is correct w/o knowing what is a correct program for that task?
Sounds impossible-but it's actually really simple. In fact, our measure of "correctness" called incoherence can be estimated (PAC guarantees).
arxiv.org/abs/2507.00057
02.07.2025 07:26 — 👍 12 🔁 3 💬 1 📌 2
Firmwire 🤝 LibAFL
17.06.2025 09:28 — 👍 8 🔁 1 💬 0 📌 0

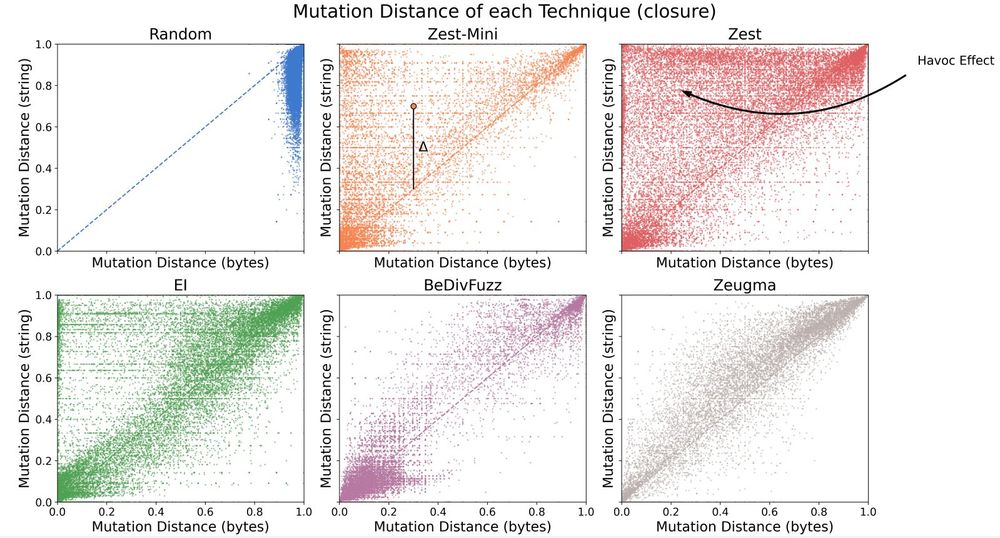
Just Accepted to ACM TOSEM!
The "Havoc Paradox" is about the relationship between byte-level fuzzer mutations and their effect on the inputs produced by generators for structured strings (e.g. XML/SQL). Can disruptive mutations be controlled? Should they be? Find out.
📄 dl.acm.org/doi/pdf/10.1...
06.06.2025 19:02 — 👍 21 🔁 3 💬 2 📌 1

DWARF as a Shared Reverse Engineering Format
This blog post introduces a new API in LIEF to create DWARF files
[Blog Post] New high-level API in LIEF that allows the
creation of DWARF files. Additionally, I present two plugins designed to export
program information from Ghidra and BinaryNinja into a DWARF file.
lief.re/blog/2025-05...
(Bonus: DWARF file detailing my reverse engineering work on DroidGuard)
27.05.2025 13:50 — 👍 21 🔁 15 💬 1 📌 0
Happy to share my upcoming #ATC25 paper w/ @snagycs.bsky.social: "BIN2WRONG: a Unified Fuzzing Framework for Uncovering Semantic Errors in Binary-to-C Decompilers"!
Bin2Wrong creates binaries by mutating source, compiler, optimizations, and format—revealing 48 new bugs in 7 decompilers! 💪
22.05.2025 20:02 — 👍 4 🔁 2 💬 1 📌 0
👀
20.05.2025 21:23 — 👍 1 🔁 0 💬 0 📌 0
2nd ACM International Conference on AI-powered Software (AIware) | Co-located with ASE 2025
PhD student working on system, side-channel, and CPU security at @isec-tugraz.bsky.social TU Graz, Austria.
He/Him
┌ Website: https://snee.la
└ Mastodon: https://infosec.exchange/@vmcall
Reverse Engineer focused on decompilation, disassembly, and software internals.
Website: https://nicolo.dev/en/
PhD, Human Factors in Cybersecurity
Current: SEFCOM, ASU
Ex: MPI-SWS, Sage Bionetworks
Adventurer. Takes a lot of photos, calls many places home. VP of research @VulnCheck. Previously vulnerability research director @Rapid7 / @metasploit.
Assistant prof at @mff.unikarlova.cuni.cz. Interested in new ways of thinking about programming and history & philosophy of computing. Previously at University of Kent and @cst.cam.ac.uk.
Just a simple information security gnome trying to make his way through the universe. Part-time patch wrangler. Tweets are just my opinion and such. Got questions about patches or bug bounties? My DMs are open. Signal: DustinChilds.17
Project Zero and High+ BigSleep Bugs
Automated, Nov 2025+
#GOTO Presents the Brightest Minds in Tech.
Check out GOTO Conferences.
https://gotopia.tech
https://www.youtube.com/@GOTO-
Chasing digital badness. Senior Researcher at Citizen Lab, but words here are mine.
“Cyber Security Ace” - Daily Star
In reality:
* Prof at Blavatnik School, Uni of Oxford
* 1st head, UK National Cyber Security Centre
* ex-Treasury, constitution & security official
* adviser to cyber security companies
* APT Name: Warlike Manatee
Cartoonist and creator of The Oatmeal and Exploding Kittens https://linktr.ee/theoatmeal
An unofficial bot that tracks and posts newly published research-related grant opportunities (GOs) from http://grants.gov.au. Made by @resbench.bsky.social.
Director & Security Researcher @alleleintel.com
Blog: https://blog.andersonc0d3.io
CS @ UoU - RA for https://futures.cs.utah.edu
Tenured Researcher @Inria
USENIX Security Artifact Evaluation Co-Chair 2025 & 2026
Web Security & Privacy: JavaScript (in)security, browser extensions
https://aurore54f.github.io
PhD student @ University of Zürich.
Interested in software engineering and software testing.
https://kitsiosk.github.io