
False positives waste your time.
False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am
@n3mes1s.bsky.social
An Operating System lover, was EDR chef and purple teamer. Trying to replace myself with an Agentic AI.

False positives waste your time.
False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am

Sent out a new edition of my email newsletter (which is very genuinely just recent from my blog reformatted into newsletter form) and it turns out it's basically ALL prompt injection this week - two detailed paper reviews and my piece on the lethal trifecta simonw.substack.com/p/the-lethal...
17.06.2025 15:30 — 👍 58 🔁 7 💬 3 📌 2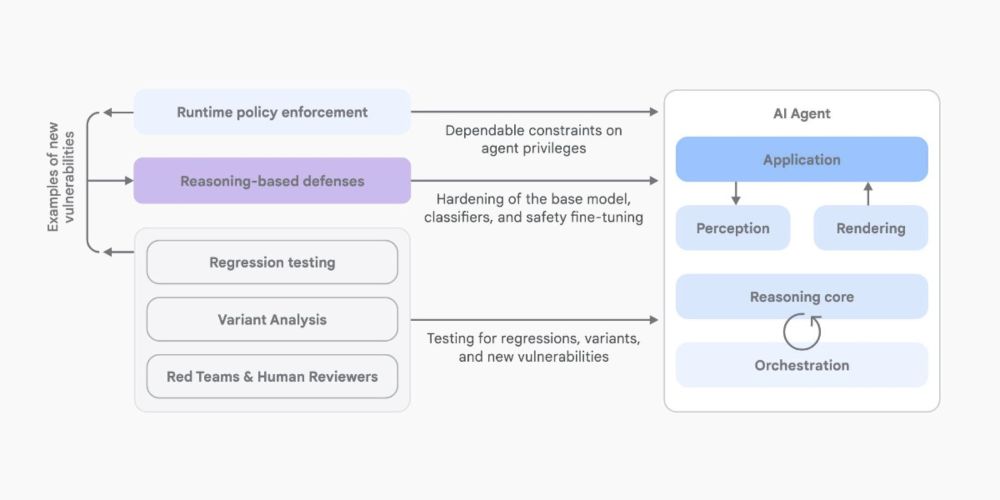
Another prompt injection paper review! This time it's "An Introduction to Google’s Approach to AI Agent Security" by Santiago Díaz, Christoph Kern, and Kara Olive
Some interesting ideas in here, particularly around Google's three core principles for agent security simonwillison.net/2025/Jun/15/...
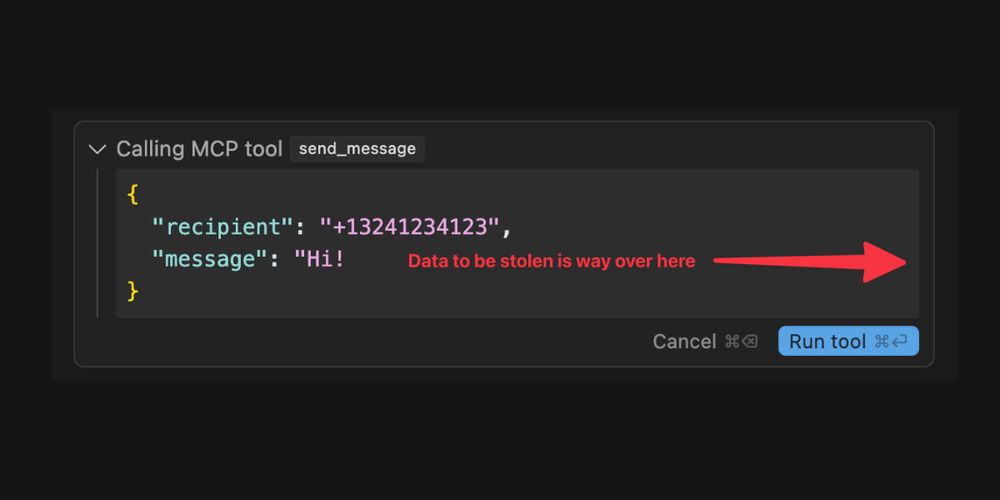
Model Context Protocol has prompt injection security problems
simonwillison.net/2025/Apr/9/m...

All the hype around OpenAI Operator but no one is really testing it. Failure modes are spiking and the problems are always the same
Failed 5/5 tests
Common problems:
Do not know how to use tools
Do not follow very well the instructions sometimes
twisty-oval-d44.notion.site/Failure-Mode...

Screenshot showing execution of the command `curl -s 'http://localhost:8000/cgi-bin/zoo_loader.cgi?request Execute&service-WPS&version=1.0.0&Identifier-echo&DataInputs-a-Reference@mimeType=text/plain@cache_file=/etc/passwd;b=value;c=value | pygmentize -l xml` and the output, including the target machine’s /etc/passwd embedded in the XML.
XBOW found a critical path traversal vulnerability in ZOO-Project (CVE-2024-53982). The vulnerability exists in the Echo example (enabled by default) and allows an attacker to retrieve any file on the server. Users should upgrade to the latest version.
05.12.2024 17:11 — 👍 8 🔁 5 💬 0 📌 0Apparent supply chain attack on Ultralytics, a popular AI Python library. Threat actor managed to insert cryptojacking functionality into specific versions (which have since been removed from PyPI).
github.com/ultralytics/...
Even easier tomorrow when someone is going to just enable your rat to attach as use this MCP protocol you are running with code execution
05.12.2024 13:43 — 👍 1 🔁 0 💬 0 📌 0I kinda tend to agree. But I hope soon we will build and have counter measures. At the end of the day it is just another process doing stuff on my computer. Will be interesting to see if a new product will arise from this or will be absorbed by the current market
04.12.2024 05:45 — 👍 0 🔁 0 💬 0 📌 0Exclusive: The backdoor inserted in v1.95.7 adds an "addToQueue" function which exfiltrates the private key through seemingly-legitimate CloudFlare headers.
Calls to this function are then inserted in various places that (legitimately) access the private key.
I really hope to never see any of this in any logs coming from edr products. Or at least I hope we will have a good way to track the “undefined” behavior of this kind if applications. Agreeing on this is opening to new security risks
03.12.2024 20:25 — 👍 1 🔁 0 💬 2 📌 0
If you missed my blackhat talk on the security of LLM applications, it's up on youtube now:
m.youtube.com/watch?v=Rhpq...
Hello world. Mostly going to talk about intersection between cybersec and genai. Going to love where we are going with all this new technology without adding any control.
26.11.2024 19:06 — 👍 2 🔁 0 💬 0 📌 0