
Adaptive Collections in Velociraptor:
docs.velociraptor.app/blog/2025/20... #DFIR
@b00010111.bsky.social
DFIR BlueTeam Github: https://github.com/00010111 Not representing my employer (past & present).

Adaptive Collections in Velociraptor:
docs.velociraptor.app/blog/2025/20... #DFIR

"A comprehensive ETW (Event Tracing for Windows) event generation tool designed for testing and research purposes" #dfir # eventlogs
github.com/olafhartong/...

Medusa stealth rootkit on Linux and how to work around and investigate this style of LD_PRELOAD rootkit: www.linkedin.com/posts/craigh... #dfir #linux
29.07.2025 09:29 — 👍 0 🔁 1 💬 0 📌 0
github.com/Neo23x0/sign...
#CVE-2025-53770
Hiding Payloads in Linux Extended File Attributes
isc.sans.edu/diary/Hiding...
#DFIR #linux
shodan@mastodon.shodan.io: "Check out our new Data Status page for an overview of what Shodan crawlers have collected the past day: data-status.shodan.io "
I still in the process to decide which stats do frighten me the most.....
Something you may not know. OneDriveExplorer also works for the OneDrive sync client for macOS.
github.com/Beercow/OneD...

Offline webshell scanning tool, based on YARA rules github.com/ekky19/Yara-... #DFIR #yara #webshell
22.06.2025 18:16 — 👍 1 🔁 0 💬 0 📌 0
Windows Registry Forensics Cheat Sheet 2025 by Cyber Triage. Potentially worth a look to check your docu against it. www.cybertriage.com/blog/windows... #DFIR #Registry
04.06.2025 06:38 — 👍 0 🔁 0 💬 0 📌 0
Tool for triage & analysis of ESXi logs:
- Combined timeline of Bash activity, logons and user activity
- Timeline of logon events by type, along with a user/IP logon timeline
- Summary of Bash history, network-tool usage and newly created users
github.com/cudeso/tools... #DFIR #Logs #esxi

"iOS Unified Logs: The Myth of 30 Days Retention - Analysis of TTLs and log stats Command" ->
www.ios-unifiedlogs.com/post/ios-uni... #DFIR #iOS #logs

Censys on C2 server called the “SCOUT PROJECT,” censys.com/blog/scoutin... #DFIR
02.05.2025 10:36 — 👍 0 🔁 0 💬 0 📌 0
"The Impact of Microsoft’s ReFS on DFIR" -> comparing NTFS evidences with ReFS. What stays, what changes and what will be gone. Recommended read! medium.com/@mathias.fuc... #DFIR #ReFS #NTFS #FileSystems
23.04.2025 20:44 — 👍 1 🔁 0 💬 0 📌 0
My new blog for CPR: introducing Waiting Thread Hijacking - a remote process injection technique targeting waiting threads: research.checkpoint.com/2025/waiting... #ProcessInjection
14.04.2025 18:17 — 👍 15 🔁 10 💬 3 📌 0
Sounds very handy:
"Mounting disk images (E01 or raw)
Handling LVM volumes
Automatically identifying and mounting partitions
...
All mount operations are performed read-only, with noexec and other conservative options to preserve evidence integrity."
www.hecfblog.com/2025/04/dail... #DFIR #Linux
Next noteworthy #breach incoming? Reading some chatter that there are claims of #checkpoint being breached by #coreinjection .
#dfir #threatintel

We are excited to announce that the @volatilityfoundation.org #PluginContest First Place winner is:
Valentin Obst for btf2json
Read the full Contest Results:
volatilityfoundation.org/the-2024-vol...
Congrats to all winners & thank you to all participants!
#DFIR #memoryforensics
Detect suspicious foci token logins:
The in cluded description includes an explanation what foci tokens are and why a hunt might be useful. Nice work!
https://github.com/HybridBrothers/Hunting-Queries-Detection-Rules/blob/main/Entra%20ID/DetectSuspiciousFociTokenLogins.md
#DFIR #BlueTeam #KQL
Detecting Bincrypter Linux Malware Obfuscation
https://www.linkedin.com/pulse/detecting-bincrypter-linux-malware-obfuscation-craig-rowland-dzewc #DFIR #Linux #BlueTeam

I started exploring OneDrive’s FileUsageSync.bd. There is some useful information on files shared via email, Teams, etc… that may not be in the user’s OneDrive.
https://malwaremaloney.blogspot.com/2025/02/onedrive-microsoftfileusagesyncdb.html
I just came across email information in one of the OneDrive databases. Sender, recipients, subject, mailbox, attachments, etc…
Pretty much everything except the body. More to come. 🤔 #DFIR

I'll definitely have a look at BruteShark.
Seems to be a nice addition to the toolset for network analysis/forensics.
Would be great if the network graphics feature works with filters (it might does, I have not checked yet). graphics for report = win
https://github.com/odedshimon/BruteShark #DFIR

More on the update of Event ID 4768,4769 in this post on LinkedIn. Includes examples how these fields are filled by windows,getTGT.py & Rubeus https://www.linkedin.com/posts/odonnell-ryan_the-january-2025-cumulative-update-introduced-activity-7290153947669880832-6ReK
#DFIR #blueteam #threathunting

Updates for event ID 4768 and 4769 in January cumulative update. See the * Update * section: https://techcommunity.microsoft.com/blog/coreinfrastructureandsecurityblog/active-directory-hardening-series---part-4-%E2%80%93-enforcing-aes-for-kerberos/4114965
#DFIR #blueteam #threathunting
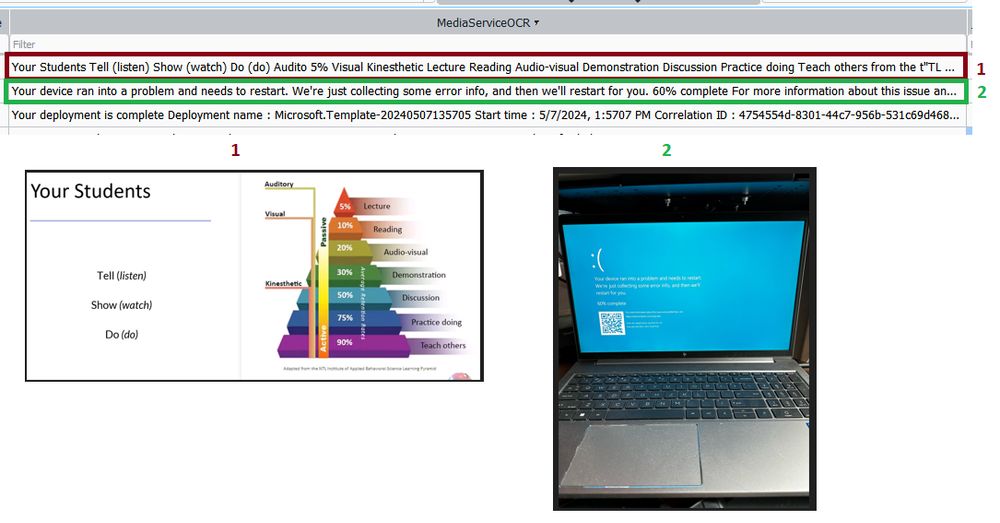
There seemed to be enough interest so I decided to do a write up on what I have found about OneDrive Offline Mode. Hate to burn a forensic artifact but I’m concerned about what Microsoft feels is secure. #DFIR
https://malwaremaloney.blogspot.com/2025/01/onedrive-offline-mode-recallish-vibes.html

"Stratoshark lets you explore and analyze applications at the system call level using a mature, proven interface based on Wireshark."
https://stratoshark.org/
https://medium.com/@nigel.douglas/how-to-capture-an-scap-for-stratoshark-826d194ef52a
this sounds very nice...
#DFIR #BlueTeam

Nice.... free book The Art of Mac Malware Volume I and Volume II https://taomm.org/ #DFIR #BlueTeam
21.01.2025 17:15 — 👍 0 🔁 1 💬 0 📌 0
Just recently came across this article about getting full path from USNJournal, even for deleted/moved files. https://cybercx.com.au/blog/ntfs-usnjrnl-rewind/
Nice work, need to test the PoC tool.
#DFIR

CVE-2024-49113 event log export: https://gist.github.com/travisbgreen/82b68bac499edbe0b17dcbfa0c5c71b7
#DFIR #blueteam #threathunting