
And #FlareOn12 Task 8: wp.me/p2mVNF-2Qf
27.11.2025 21:55 — 👍 8 🔁 2 💬 0 📌 0@hasherezade.bsky.social
Programmer, #malware analyst. Author of #PEbear, #PEsieve, #TinyTracer. Private account. All opinions expressed here are mine only (not of my employer etc) ; https://hasherezade.net

And #FlareOn12 Task 8: wp.me/p2mVNF-2Qf
27.11.2025 21:55 — 👍 8 🔁 2 💬 0 📌 0
And #FlareOn12 Task 8: wp.me/p2mVNF-2Qf
27.11.2025 21:55 — 👍 8 🔁 2 💬 0 📌 0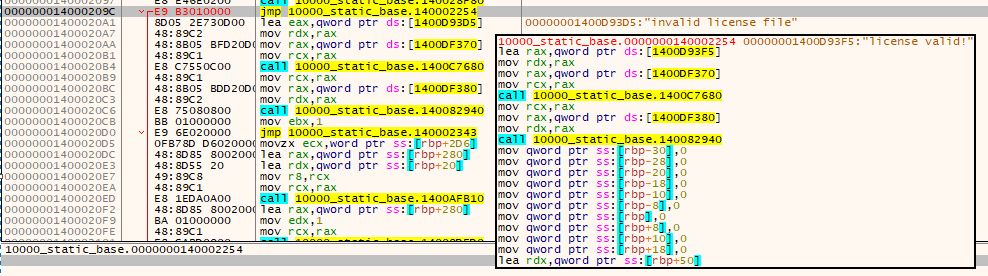
Long overdue, but here’s my writeup for #FlareOn12 Task 9: hshrzd.wordpress.com/2025/11/20/f...
20.11.2025 05:28 — 👍 12 🔁 2 💬 1 📌 0
Heeey, ncurses/terminfo has a small virtual machine! And if there's a VM, there are CTF challenges :)
hackarcana.com/public-exerc...
hackarcana.com/public-exerc...
(third one coming next week, will be a bit harder)

The 13th annual @volatility #PluginContest is OPEN for submissions until 31 Dec 2025!
This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.

-iOS 26 change deletes clues of old spyware infections
-Starlink disables 2.5k scam compound terminals
-Caribbean hospital still down 5 months after ransomware attack
-Poland charges officials in Pegasus scandal
Newsletter: news.risky.biz/risky-bullet...
Podcast: risky.biz/RBNEWS495/

Today I'm launching my new app, Hacktivate. It teaches real-world computer science skills through 240 "capture the flag" challenges, and works on iPhone, iPad, and Mac with one purchase. I've poured a ton of love into it, and I'd love to hear what you think 🙌 apps.apple.com/gb/app/hackt...
22.10.2025 13:20 — 👍 156 🔁 30 💬 18 📌 0I used PE-bear for the first time to dump an embedded binary. Its intuitive UI made extraction effortless. Because malware often embeds payloads with the form A in B to evade detection, pulling out the inner binary was crucial for deeper analysis and IoCs hunting.
19.10.2025 08:45 — 👍 2 🔁 2 💬 2 📌 0
Finally done with #FlareOn12. What a ride! I am looking forward to read other people’s solutions, especially of those who did the 9th task quickly.
11.10.2025 16:26 — 👍 9 🔁 0 💬 0 📌 0
#FTSCon Speaker Spotlight: Aleksandra Doniec (@hasherezade.bsky.social) is presenting “Uncovering Malware's Secrets with TinyTracer” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

My intermediate level malware analysis course is there.
60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...
Beyond good ol’ Run key, Part 148
www.hexacorn.com/blog/2025/07...

- option of custom parsing exports directory allows to pinpoint even the APIs that the malware author tried to hide by erasing exports table in memory: (github.com/hasherezade/...)
06.06.2025 19:18 — 👍 3 🔁 0 💬 0 📌 0
- watching not only the functions arguments, but also, how they changed after the function execution, and the function return value: (github.com/hasherezade/...) - thanks to a new contributor, maxspl:
06.06.2025 19:17 — 👍 3 🔁 0 💬 1 📌 0
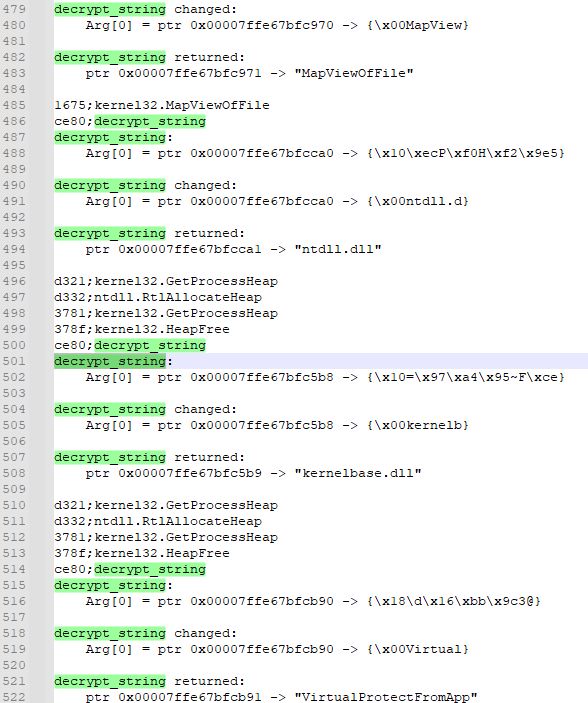
includes: tracing defined local functions (github.com/hasherezade/...):
06.06.2025 19:15 — 👍 0 🔁 0 💬 1 📌 0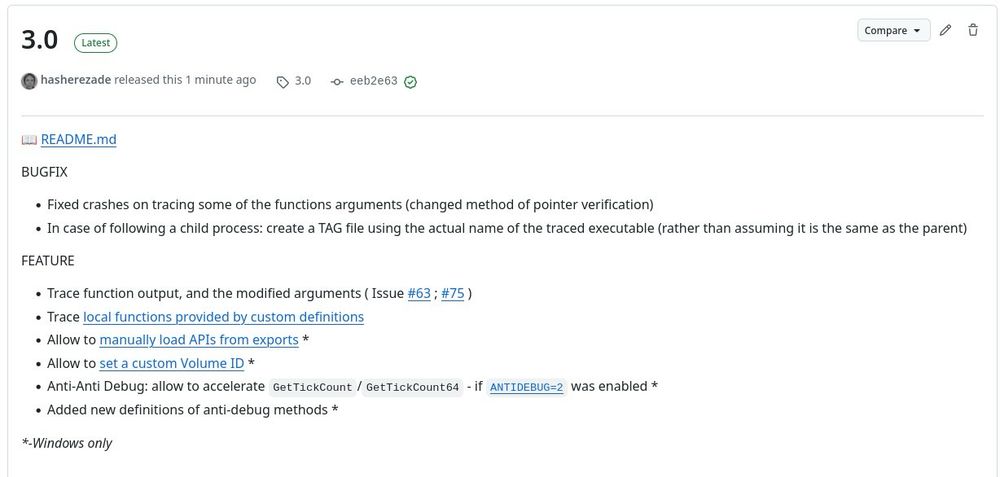
New #TinyTracer (v3.0) is out - with many cool features: github.com/hasherezade/... - check them out!
06.06.2025 19:11 — 👍 16 🔁 6 💬 1 📌 01. Pause thread midway in exploit races (even ⓪).
2. Or block entire CPU core. Kernel APCs run at APC_LEVEL (🤯), so thread scheduling kinda disabled (think priority == ∞).
3. Or build upon @hasherezade.bsky.social work & generalize #WaitingThreadHijacking — making it, in fact, Waitless.
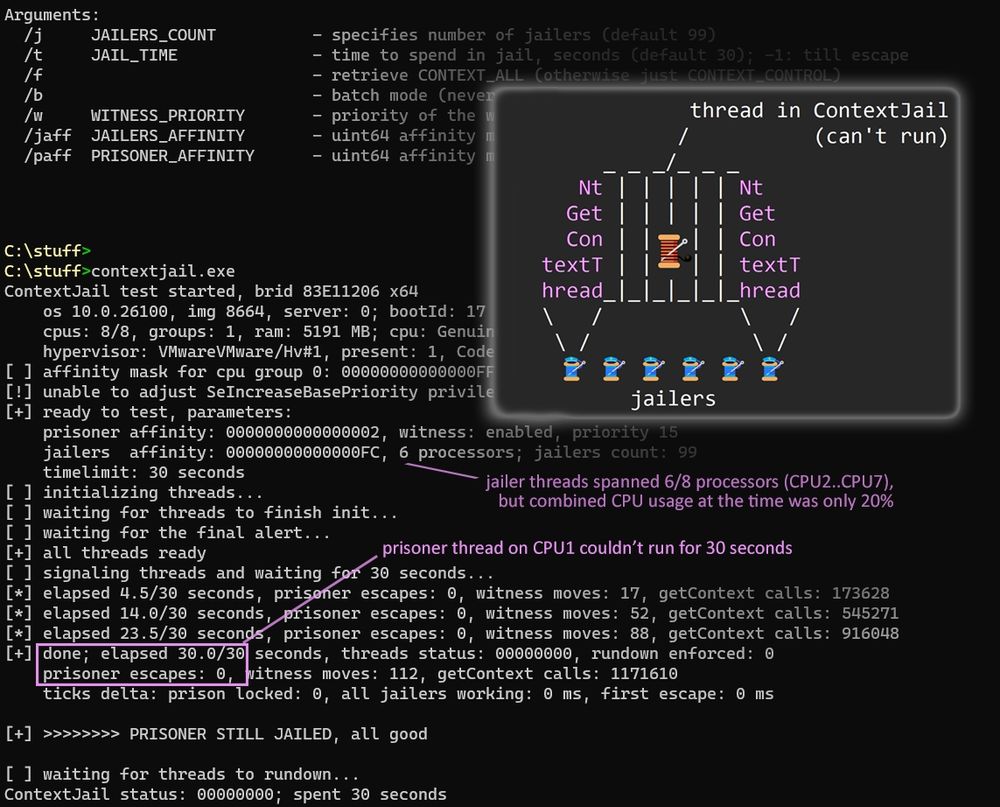
Screenshot of contextjail.exe running with default arguments. Highlighted: * prisoner thread (latched to CPU1 with priority 15) couldn't run for the entire test duration (30 seconds). * 99 jailer threads (latched to 6/8 processors, CPU2..CPU7) were using 20% of total CPU time. Overlay: pseudo-ASSCII art with prisoner thread and 6 jailer threads (guards), spamming NtGetContextThread to block the prisoner. Source and compiled binary: https://pastebin.com/pBJcGp1y
Heard of #ContextJail?
It's a nasty new technique: puts target thread into ⓪ deadloop, for as long as you can afford. Requires THREAD_GET_CONTEXT right.
The gist? Just spam NtGetContextThread(tgt).😸
Target will be jailed, running nt!PspGetSetContextSpecialApc 🔁.
Src & binary in [ALT].
Usecases: ⤵️
yes, we catch it, but I cannot speak for others
14.04.2025 18:59 — 👍 0 🔁 0 💬 0 📌 0![[DEMO] Waiting Thread Hijacking (on Windows 11 24 H2)](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:bt437wewqcvsurogzlpcxque/bafkreialpmjmuphn7irqz4smmlntib4gsdr2ipvdr6fssw62m3irimi6ly@jpeg)
demo: www.youtube.com/watch?v=CZIR... ; src: github.com/hasherezade/...
14.04.2025 18:18 — 👍 5 🔁 0 💬 0 📌 0
My new blog for CPR: introducing Waiting Thread Hijacking - a remote process injection technique targeting waiting threads: research.checkpoint.com/2025/waiting... #ProcessInjection
14.04.2025 18:17 — 👍 15 🔁 10 💬 3 📌 0🫂
13.04.2025 21:57 — 👍 1 🔁 0 💬 0 📌 0
Zscaler has published a technical report on HijackLoader (IDAT Loader, GhostPulse) and its recent changes, such as its new call stack spoofing module, anti-VM module, and support for scheduled task persistence
www.zscaler.com/blogs/securi...
Abolish April Fool’s day. Society has moved past the need for April Fool’s day
01.04.2025 02:36 — 👍 13361 🔁 1549 💬 540 📌 169
KELA has published a profile on Rey and Pryx, the two main individuals behind the Hellcat hacking group, responsible for several breaches over the past months, such as Schneider Electric, Telefónica, and Orange Romania.
www.kelacyber.com/blog/hellcat...

We all knew this day would arrive when the DNA samples you willingly provided 23andMe would be up for sale. Company now says it's seeking a buyer as it files for bankruptcy. 23andMe says any buyer will have to adhere to privacy laws for customer DNA/data they acquire. people.com/23andme-file...
24.03.2025 16:58 — 👍 81 🔁 36 💬 6 📌 9
Clevo Boot Guard Keys Leaked in Update Package
www.binarly.io/blog/clevo-b...

Someone has done an excellent job collecting RATs and documenting them by version. They also included images.
A+ work. This is amazing (we're going to ingest this eventually)
github.com/Cryakl/Ultim...
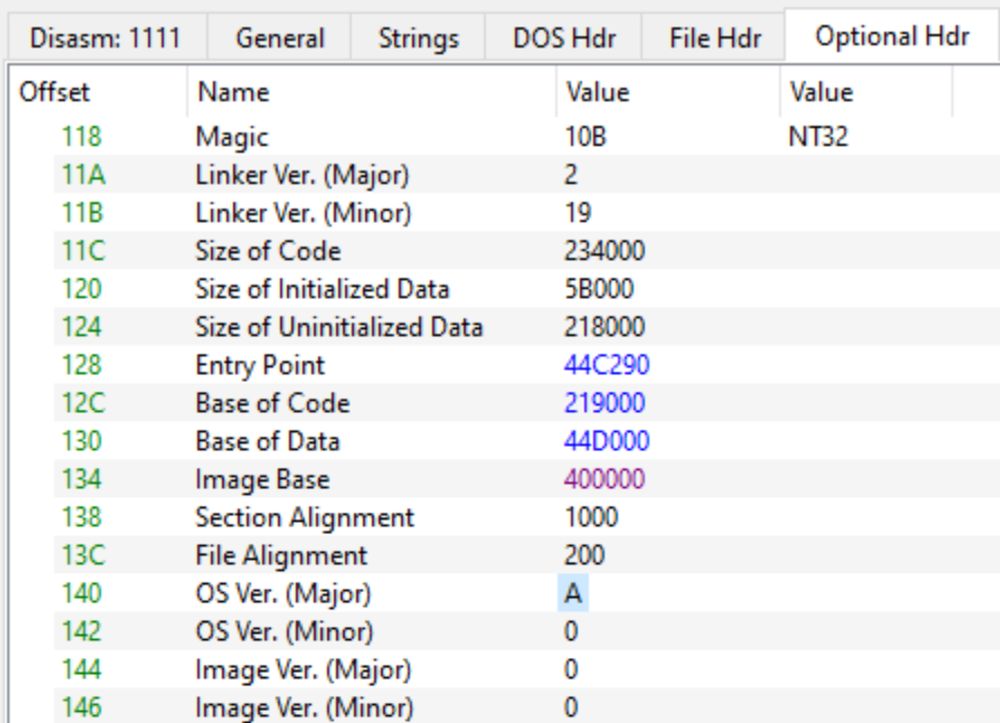
A small demo/tutorial on unpacking executables with #PEsieve and #TinyTracer: hshrzd.wordpress.com/2025/03/22/u...
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
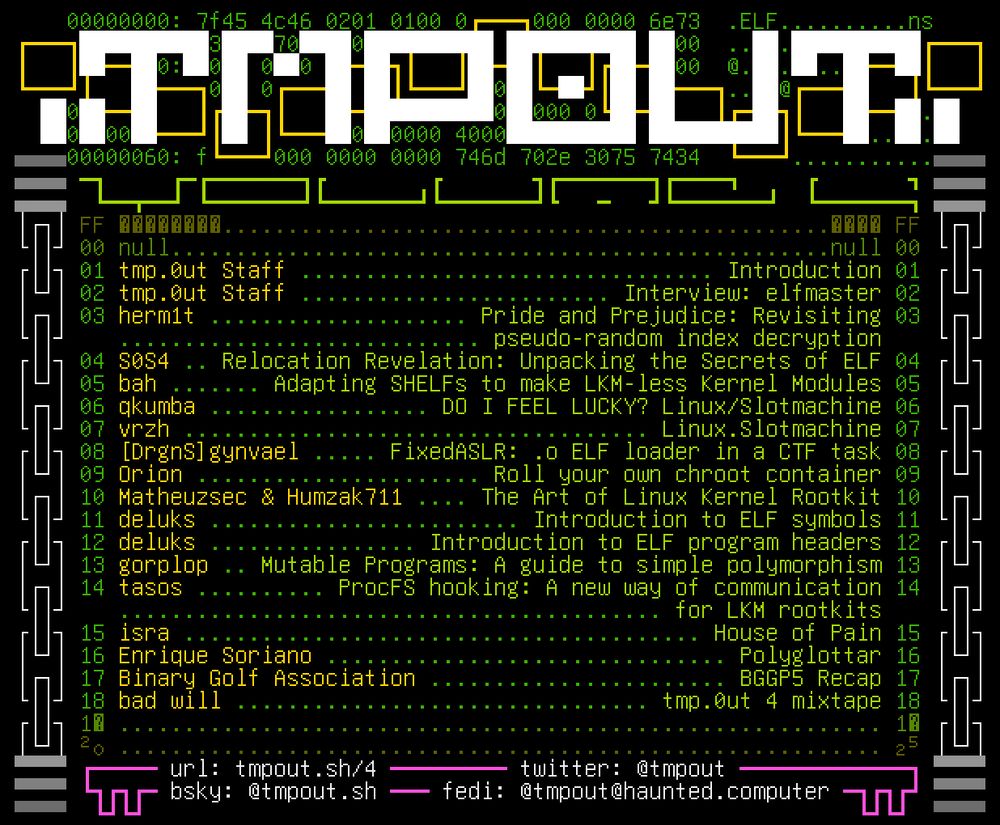
table of contents for tmp.0ut volume 4
Would you look at that, it's tmp.0ut Volume 4! Happy Friday, hope you enjoy this latest issue!
tmpout.sh/4/