Du coup ils vont refaire la scène mais au tribunal maintenant 😂
24.06.2025 09:03 — 👍 1 🔁 0 💬 0 📌 0S
@pwnsdx.bsky.social
@pwnsdx.bsky.social
Du coup ils vont refaire la scène mais au tribunal maintenant 😂
24.06.2025 09:03 — 👍 1 🔁 0 💬 0 📌 0Many companies and individuals are trying to mislead people about the future of GrapheneOS to promote their insecure products and services. GrapheneOS is not going anywhere. We've made it clear we're shipping Android 16 soon and that the supported devices will remain supported.
21.06.2025 13:48 — 👍 218 🔁 38 💬 3 📌 4
We're looking into using github.com/k2-fsa/sherp... to provide built-in text-to-speech and speech-to-text to greatly improve the out-of-the-box accessibility of GrapheneOS for blind users. We already have a screen reader included via our fork of the open source variant of TalkBack.
26.05.2025 16:19 — 👍 77 🔁 15 💬 4 📌 0Apps coming from the Play Store doesn't make them trustworthy, safe or secure. Most malware apps on Google Mobile Services devices are installed from the Play Store. Similarly to the Play Integrity API, it's Google reinforcing their monopolies with security as an excuse for it.
17.05.2025 14:26 — 👍 20 🔁 3 💬 1 📌 0
Similar to iOS lockdown mode, Android 16's Advanced Protection feature is misguided. It adds security features exclusive to it which require using all of the other features. This prevents people using new security features if they need to avoid 1 feature.
security.googleblog.com/2025/05/adva...
We still need help getting early access to Android 16 sources prior to the stable release in June. Every mainstream Android OEM has it. We're currently spending significant time on reverse engineering Android 16 Beta releases. It's a huge waste compared to having what we need.
22.05.2025 02:22 — 👍 93 🔁 15 💬 2 📌 0Multiple prominent banking apps in Europe have already implemented support for GrapheneOS via hardware attestation. The pace of apps adopting the Play Integrity API is unfortunately currently faster than apps adding support for GrapheneOS. This is due to Google marketing it.
23.05.2025 01:39 — 👍 27 🔁 4 💬 1 📌 0Google Play Integrity permits highly insecure devices with years of missing High/Critical severity security patches. They pretend any device licensing Google Mobile Services is secure while running the stock OS and anything else is insecure. This is a lie to lock out competition.
23.05.2025 01:13 — 👍 38 🔁 7 💬 1 📌 0We're going to add a secure way of working around this without breaking the app source security model. We'll be adding support for having the OS automatically verify the Play Store signing metadata and then inform Play services those apps were installed from the Play Store.
23.05.2025 00:57 — 👍 48 🔁 3 💬 2 📌 1This is being done alongside Google recommending app developers forbid installing their apps from the Play Store on operating systems not licensing Google Mobile Services. The combination of these feature ends up blocking users from easily using the apps without modifying them.
23.05.2025 00:56 — 👍 45 🔁 3 💬 1 📌 0A growing number of apps are using the Play Integrity API to enforce installation from the Play Store. This is clearly highly illegal anti-competitive behavior. It doesn't impact GrapheneOS users installing apps with the sandboxed Play Store but does impact other install sources.
23.05.2025 00:52 — 👍 148 🔁 34 💬 2 📌 7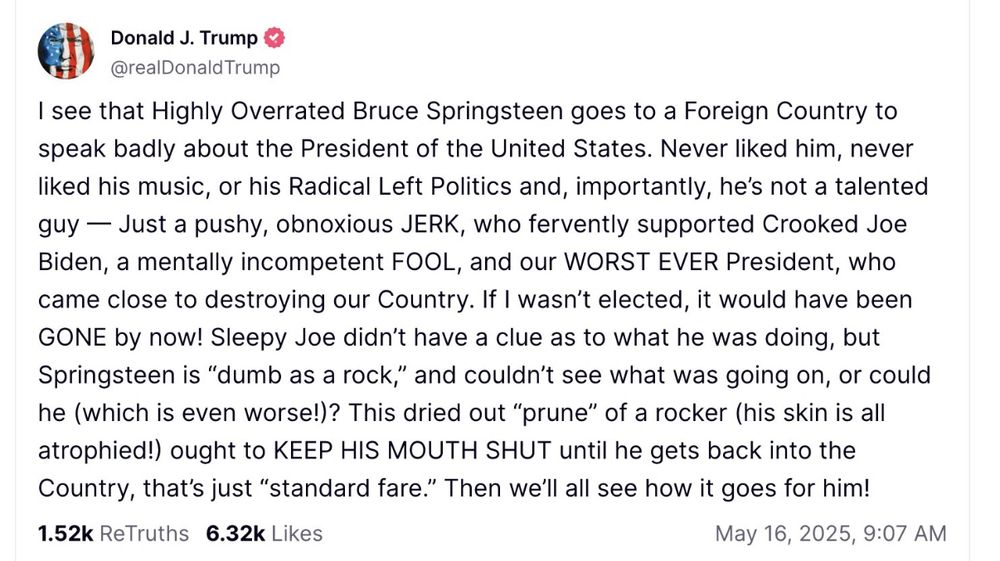
If this person sat next to you on a bus or train and started ranting about Bruce Springsteen in this way, you would get up and move to a different seat.
In the United States, we have him the nuclear codes.
I have created a Docker Compose file to launch open-webui exposed as a Tor hidden service. This way, you & your friends can discuss with your AI models on your main computer, 100% privately, from any device, anywhere in the world, without having to open any ports.
Interested? I'll share it soon.
It's normal for many third party apps to have bugs uncovered by hardware memory tagging which is why we don't yet have it enabled for user installed apps by default.
It isn't normal to have frequent crashes for the OS if that's what you're referring to. The OS itself should be quite stable.
Yeah totally, it's the apps that are messy. The OS is perfect. Sorry for any misunderstanding!
29.04.2025 17:23 — 👍 2 🔁 0 💬 0 📌 09a*
29.04.2025 15:22 — 👍 0 🔁 0 💬 0 📌 0I also want to thank the @grapheneos.org team for the amazing work they are doing. You are in my opinion the only competitor to Apple on this field.
29.04.2025 15:05 — 👍 2 🔁 0 💬 0 📌 0Anyways, if you're looking to move to Android, I highly recommend Graphene and only Graphene. In my opinion, any other ROM isn't worth it if it can't be better than Apple on the security and privacy side. The Pixel hardware is modern, and GrapheneOS fully takes advantage of it.
29.04.2025 15:03 — 👍 1 🔁 0 💬 1 📌 0
Furthermore, the fingerprinting protection is weak, and none of the browsers have passed Fingerprint.com tests (so far, only Safari on iOS and macOS with Advanced Fingerprinting Protection, and Firefox on Mullvad Browser and Tor Browser on desktop have resisted).
29.04.2025 15:03 — 👍 0 🔁 0 💬 1 📌 0The only thing are the frequent crash and some apps fundamentally poorly coded such as TikTok that requires MTE to be disabled.
29.04.2025 15:03 — 👍 0 🔁 0 💬 2 📌 0GrapheneOS also makes it free from political uncertainty (as you can always download APKs from source), preventing a single operator like Apple from censoring apps like secure messaging apps, Tor or VPNs under a potential surveillance state (e.g., Chat Control).
29.04.2025 15:03 — 👍 1 🔁 0 💬 1 📌 0Having that within a cost-effective phone such as the Pixel 6a is really what sets everything apart. It truly provides everything you want from a modern smartphone, is affordable, and free from economic uncertainty.
29.04.2025 15:03 — 👍 1 🔁 0 💬 2 📌 0- Privacy-wise, it's obviously better than Apple, with basically zero telemetry and a wide range of app stores available (Aurora, F-Droid), but the Play Store and its services seem unavoidable at this time, considering that many apps verify that they were downloaded from it.
29.04.2025 15:03 — 👍 1 🔁 0 💬 1 📌 0- Security-wise, it's very impressive; it's clearly better than iOS (hardened malloc, MTE, self-destruction/duress code, Private Space, guest mode, true Always-On VPN with encrypted DNS supported natively) minus the proprietary Apple code and lock-in.
29.04.2025 15:03 — 👍 1 🔁 0 💬 1 📌 0A thread about my first personal impressions on GrapheneOS:
- The OS is not as polished as iOS, but I expected that, of course. There is a lot of work to be done, but I believe AI will significantly increase development on that side, for Android, Graphene, and the wider app developer community.
We started deploying RANDSTRUCT for the kernel, which will eventually be used to have multiple possible struct memory layouts for each device model chosen randomly at boot. Our work on reducing kernel attack surface also continued.
We plan to focus more on Linux kernel security going forward.
We replaced our decade old feature for blocking new USB peripherals while locked with a greatly expanded and far more secure feature. The new approach blocks USB-C connections and USB-C data at a hardware level with expanded software-based blocking as a fallback (grapheneos.org/features#usb...).
07.02.2025 06:19 — 👍 27 🔁 1 💬 1 📌 0We made massive improvements in GrapheneOS to defend against these attacks since January 2024.
For ARMv9 devices, we greatly improved our hardware memory tagging implementation in hardened_malloc, deployed it for the Linux kernel allocators and greatly expanded the use of PAC and BTI across the OS.
Several other improvements were made based on our January 2024 vulnerability reports and proposals including an implementation of wiping data before rebooting when a wipe is triggered. We shipped an improved version of this for our duress PIN/password feature before the feature shipped for Android.
07.02.2025 06:02 — 👍 39 🔁 1 💬 1 📌 0In April 2024, Pixels shipped a partial implementation of our January 2024 proposal for firmware-based reset attack protection. Fastboot mode now zeroes RAM before enabling USB. This successfully wiped out the After First Unlock state exploit capabilities of two commercial exploit tools.
07.02.2025 06:00 — 👍 391 🔁 22 💬 9 📌 2