
Abstract. Garbled circuits with one-bit-per-gate communication were recently introduced by Liu et al. (BitGC, Eurocrypt 2025), Meyer et al. (Crypto 2025), and Ishai et al. (Crypto 2025). However, these works focus primarily on the theoretical communication complexity, leaving open questions about practical computational efficiency. In this paper, we present a set of optimizations that substantially improve its practical efficiency. First, we eliminate key barriers to enable SIMD support to BitGC, leading to a substantial speedup in its homomorphic operations. Second, we demonstrate that XOR gates can be garbled without any communication, improving both efficiency and simplicity. Finally, we present a computationally efficient garbling scheme that requires zero communication for XOR gates and only 5 bits per AND gate. When applied to an AES-128 circuit, our fastest garbling scheme generates a garbled circuit of just 4 KB in 3 minutes on a single CPU core.
BitGC Made (More) Efficient (Wenhao Zhang, Hanlin Liu, Kang Yang, Wen-jie Lu, Yu Yu, Xiao Wang, Chenkai Weng) ia.cr/2025/1810
08.10.2025 03:02 — 👍 0 🔁 1 💬 0 📌 0
while all research on censorship has been terminated :(
06.09.2025 13:20 — 👍 0 🔁 0 💬 0 📌 0
There is even corn syrup in some major-brand infant formula in US.
30.08.2025 19:01 — 👍 0 🔁 0 💬 0 📌 0
In the past few years, I have been paying more attention to emails from prospective PhD students that describe my work in some detail, but not this year. Too many emails with AI-generated summaries.
21.08.2025 14:07 — 👍 1 🔁 0 💬 0 📌 0
Reserved ip, disk, template, gateway all cost money 🥲 disk with customized up cost money even if you don’t use it I think
07.08.2025 16:41 — 👍 1 🔁 0 💬 0 📌 0
Actually you should ask all your followers to point to your website!
18.07.2025 13:42 — 👍 0 🔁 0 💬 0 📌 0
Ask all your (ex)students to point to your maybe
18.07.2025 12:09 — 👍 1 🔁 0 💬 1 📌 0
Sorry, your protocol cannot be secure. I will find a bug after the rebuttal.
16.07.2025 21:04 — 👍 3 🔁 0 💬 0 📌 0
See left bottom corner, it says 0 caffeine😉
09.07.2025 20:52 — 👍 0 🔁 0 💬 0 📌 0
What can we do without random oracles 🥲
08.07.2025 21:27 — 👍 0 🔁 0 💬 1 📌 0
You need random oracle instead? Collision resistance may have output containing some input.
08.07.2025 01:17 — 👍 4 🔁 0 💬 1 📌 0
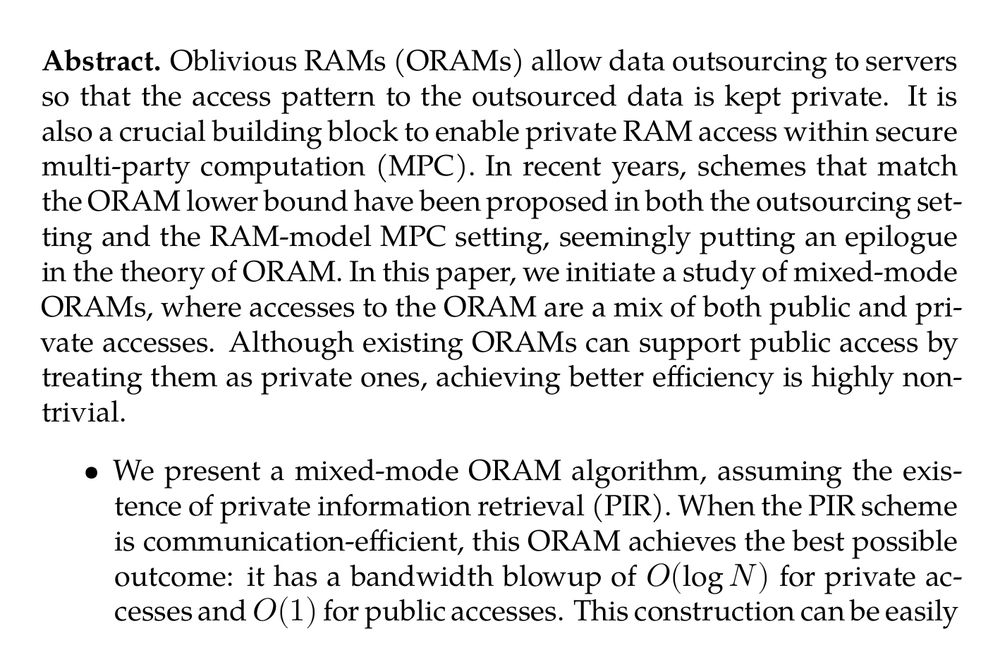
Abstract. Oblivious RAMs (ORAMs) allow data outsourcing to servers so that the access pattern to the outsourced data is kept private. It is also a crucial building block to enable private RAM access within secure multi-party computation (MPC). In recent years, schemes that match the ORAM lower bound have been proposed in both the outsourcing setting and the RAM-model MPC setting, seemingly putting an epilogue in the theory of ORAM. In this paper, we initiate a study of mixed-mode ORAMs, where accesses to the ORAM are a mix of both public and private accesses. Although existing ORAMs can support public access by treating them as private ones, achieving better efficiency is highly non-trivial.
- We present a mixed-mode ORAM algorithm, assuming the existence of private information retrieval (PIR). When the PIR scheme is communication-efficient, this ORAM achieves the best possible outcome: it has a bandwidth blowup of O(logN) for private accesses and O(1) for public accesses. This construction can be easily extended for the MPC setting achieving O(BlogN) circuit size for private accesses to B-sized blocks and O(B) circuit size for public accesses to the same array.
- We instantiate the above protocol in the three-party computation (3PC) setting with more concrete optimizations, yielding a protocol that performs almost as efficiently as state-of-the-art RAM-3PC protocols for private accesses while being 3× more efficient for public accesses in the LAN setting.
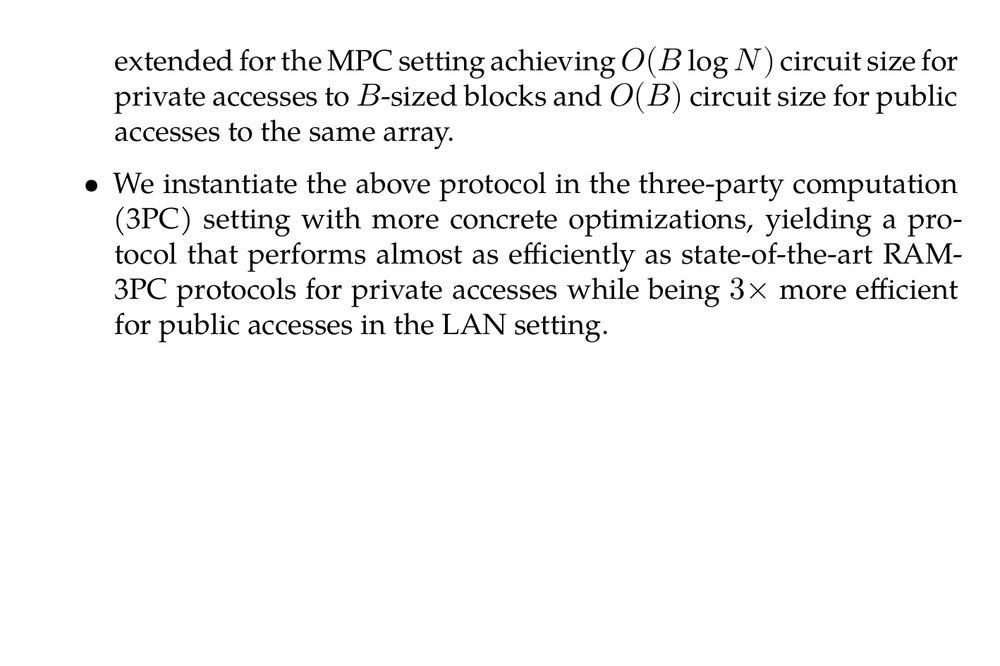
Image showing part 2 of abstract.
Efficient Mixed-Mode Oblivious RAMs (Wenhao Zhang, Xiao Wang, Chenkai Weng) ia.cr/2025/1057
09.06.2025 03:12 — 👍 0 🔁 1 💬 0 📌 0
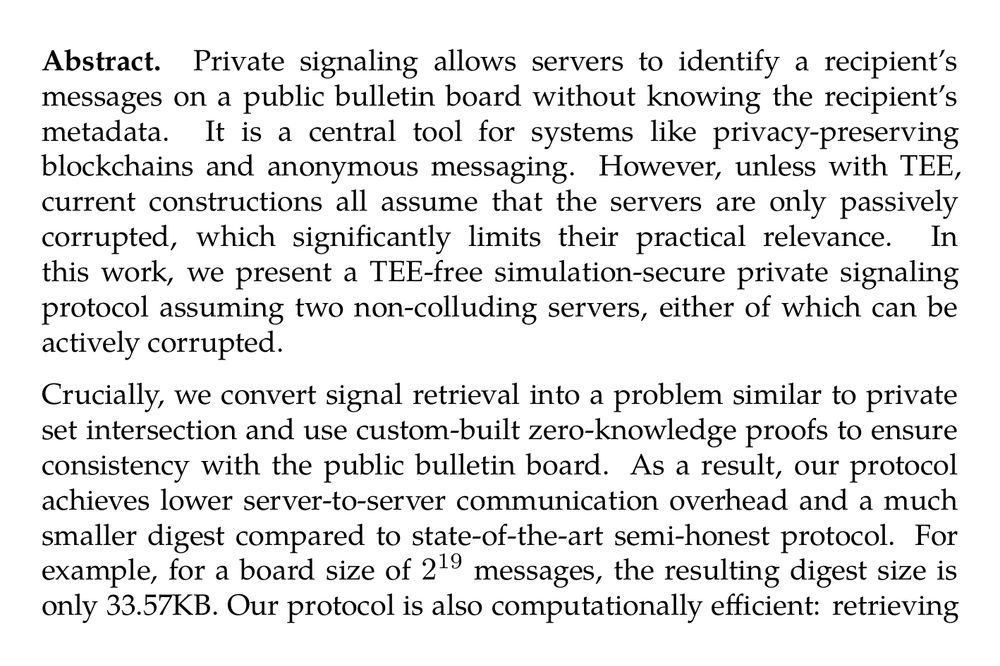
Abstract. Private signaling allows servers to identify a recipient’s messages on a public bulletin board without knowing the recipient’s metadata. It is a central tool for systems like privacy-preserving blockchains and anonymous messaging. However, unless with TEE, current constructions all assume that the servers are only passively corrupted, which significantly limits their practical relevance. In this work, we present a TEE-free simulation-secure private signaling protocol assuming two non-colluding servers, either of which can be actively corrupted.
Crucially, we convert signal retrieval into a problem similar to private set intersection and use custom-built zero-knowledge proofs to ensure consistency with the public bulletin board. As a result, our protocol achieves lower server-to-server communication overhead and a much smaller digest compared to state-of-the-art semi-honest protocol. For example, for a board size of 2¹⁹ messages, the resulting digest size is only 33.57KB. Our protocol is also computationally efficient: retrieving private signals only takes about 2 minutes, using 16 threads and a LAN network.

Image showing part 2 of abstract.
Private Signaling Secure Against Actively Corrupted Servers (Haotian Chu, Xiao Wang, Yanxue Jia) ia.cr/2025/1056
06.06.2025 03:23 — 👍 3 🔁 1 💬 0 📌 0
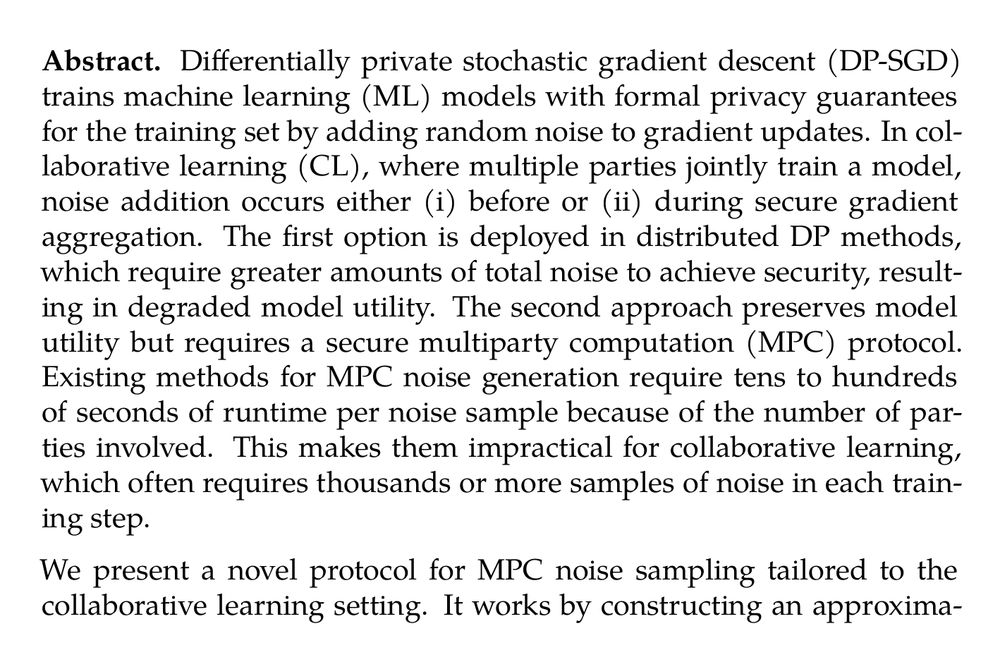
Abstract. Differentially private stochastic gradient descent (DP-SGD) trains machine learning (ML) models with formal privacy guarantees for the training set by adding random noise to gradient updates. In collaborative learning (CL), where multiple parties jointly train a model, noise addition occurs either (i) before or (ii) during secure gradient aggregation. The first option is deployed in distributed DP methods, which require greater amounts of total noise to achieve security, resulting in degraded model utility. The second approach preserves model utility but requires a secure multiparty computation (MPC) protocol. Existing methods for MPC noise generation require tens to hundreds of seconds of runtime per noise sample because of the number of parties involved. This makes them impractical for collaborative learning, which often requires thousands or more samples of noise in each training step.
We present a novel protocol for MPC noise sampling tailored to the collaborative learning setting. It works by constructing an approximation of the distribution of interest which can be efficiently sampled by a series of table lookups. Our method achieves significant runtime improvements and requires much less communication compared to previous work, especially at higher numbers of parties. It is also highly flexible – while previous MPC sampling methods tend to be optimized for specific distributions, we prove that our method can generically sample noise from statistically close approximations of arbitrary discrete distributions. This makes it compatible with a wide variety of DP mechanisms. Our experiments demonstrate the efficiency and utility of our method applied to a discrete Gaussian mechanism for differentially private collaborative learning. For 16 parties, we achieve a runtime of 0.06 seconds and 11.59 MB total communication per sample, a 230× runtime improvement and 3× less communication compared to the prior state-of-the-art for sampling from discrete Gaussian distribution in MPC.

Image showing part 2 of abstract.
Secure Noise Sampling for Differentially Private Collaborative Learning (Olive Franzese, Congyu Fang, Radhika Garg, Somesh Jha, Nicolas Papernot, Xiao Wang, Adam Dziedzic) ia.cr/2025/1025
02.06.2025 20:28 — 👍 2 🔁 2 💬 0 📌 1
Performance is secondary.
04.06.2025 19:00 — 👍 2 🔁 0 💬 0 📌 0
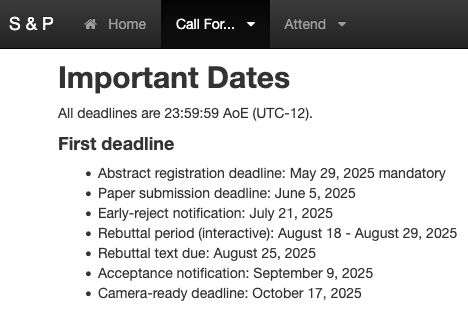
If you are submitting to @ieeessp.bsky.social
this year, a friendly reminder that there is an abstract submission deadline this Thursday May 29 (AoE).
More details: sp2026.ieee-security.org/cfpapers.html
27.05.2025 12:49 — 👍 2 🔁 1 💬 0 📌 0
They never thought anyone would pay?
21.05.2025 21:27 — 👍 1 🔁 0 💬 0 📌 0

Decision-making studies appear in HCI, vis, & increasingly AI/ML, but how “good decision” is defined is often ad-hoc
My #CHI2025 talk today will answer Qs like:
What's a decision problem?
What's the best possible performance on a decision problem?
What minimum info must participants be given?
1/2
29.04.2025 23:09 — 👍 62 🔁 10 💬 2 📌 1

Abstract. The Nintendo DSi is a handheld gaming console released by Nintendo in 2008. In Nintendo’s line-up the DSi served as a successor to the DS and was later succeeded by the 3DS. The security systems of both the DS and 3DS have been fully analysed and defeated. However, for over 14 years the security systems of the Nintendo DSi remained standing and had not been fully analysed. To that end this work builds on existing research and demonstrates the use of a second-order fault injection attack to extract the ROM bootloaders stored in the custom system-on-chip used by the DSi. We analyse the effect of the induced fault and compare it to theoretical fault models. Additionally, we present a security analysis of the extracted ROM bootloaders and develop a modchip using cheap off-the-shelf components. The modchip allows to jailbreak the console, but more importantly allows to resurrect consoles previously assumed irreparable.
An in-depth security evaluation of the Nintendo DSi gaming console (pcy Sluys, Lennert Wouters, Benedikt Gierlichs, Ingrid Verbauwhede) ia.cr/2025/568
31.03.2025 00:50 — 👍 7 🔁 2 💬 0 📌 0
@iacrcrypto.bsky.social allows remote attendance/presentation this year!
21.03.2025 19:11 — 👍 0 🔁 0 💬 0 📌 0
YouTube video by That Good News Girl
Beavers outperform government, completing 7-year project in 2 days #shorts #beavers
I will play it next time I need to give a talk on Beaver Triples youtu.be/h7aEJMW9J1g?...
18.03.2025 13:34 — 👍 3 🔁 0 💬 1 📌 0
I think only the egg one was intended. Others are really just because of too much undergrad teaching!
14.03.2025 03:08 — 👍 0 🔁 0 💬 0 📌 0
 12.03.2025 19:14 — 👍 0 🔁 0 💬 0 📌 0
12.03.2025 19:14 — 👍 0 🔁 0 💬 0 📌 0
I remembered my host told me that DJI dropped 666points on the day of my first interview. I told him yes, drone business is difficult…
12.03.2025 18:26 — 👍 1 🔁 0 💬 1 📌 0
Congrats!
26.02.2025 22:23 — 👍 1 🔁 0 💬 0 📌 0
Congrats!!
26.02.2025 20:18 — 👍 0 🔁 0 💬 0 📌 0

Crypto 2025
Crypto 2025
If you need a visa to attend Crypto 2025 (crypto.iacr.org/2025/) please make sure to start the process early this year by reaching out the general chair Francisco Rodríguez Henríquez at crypto2025@iacr.org
25.02.2025 13:11 — 👍 5 🔁 10 💬 0 📌 1

Abstract. Zero-Knowledge Succinct Non-interactive Arguments of Knowledge (zkSNARKs) lead to proofs that can be succinctly verified but require huge computational resources to generate. Prior systems outsource proof generation either through public delegation, which reveals the witness to the third party, or, more preferably, private delegation that keeps the witness hidden using multiparty computation (MPC). However, current private delegation schemes struggle with scalability and efficiency due to MPC inefficiencies, poor resource utilization, and suboptimal design of zkSNARK protocols.
In this paper, we introduce DFS, a new zkSNARK that is delegation-friendly for both public and private scenarios. Prior work focused on optimizing the MPC protocols for existing zkSNARKs, while DFS uses co-design between MPC and zkSNARK so that the protocol is efficient for both distributed computing and MPC. In particular, DFS achieves linear prover time and logarithmic verification cost in the non-delegated setting. For private delegation, DFS introduces a scheme with zero communication overhead in MPC and achieves malicious security for free, which results in logarithmic overall communication; while prior work required linear communication. Our evaluation shows that DFS is as efficient as state-of-the-art zkSNARKs in public delegation; when used for private delegation, it scales better than previous work. In particular, for 2²⁴ constraints, the total communication of DFS is less than 500KB, while prior work incurs 300GB, which is linear to the circuit size. Additionally, we identify and address a security flaw in prior work, EOS (USENIX’23).

Image showing part 2 of abstract.
DFS: Delegation-friendly zkSNARK and Private Delegation of Provers (Yuncong Hu, Pratyush Mishra, Xiao Wang, Jie Xie, Kang Yang, Yu Yu, Yuwen Zhang) ia.cr/2025/296
20.02.2025 21:16 — 👍 1 🔁 2 💬 0 📌 0
I would finally like to thank the selection committee for recognizing my work, and I look forward to leveraging this fellowship to further advance my research and contribute to our community.
18.02.2025 18:26 — 👍 0 🔁 0 💬 0 📌 0
Postdoc @Microsoft Research NE
https://yifanwu.me
President of Signal, Chief Advisor to AI Now Institute
AI Comms Director at CIFAR
Tech, books, write, create
Complex Cryptography used to require a PhD and specialized expertise. Now, it just requires Stoffel.
https://stoffelmpc.com/?utm_source=bsky&utm_medium=bsky-profile&utm_campaign=stoffel-mpc
Ginni Rometty Prof @NorthwesternCS | Fellow @NU_IPR | Uncertainty + decisions | Humans + AI/ML | Blog @statmodeling
Computer Science professor at UC Irvine
Tech policy researcher at Stanford. Former litigator. Anger is an energy. Dum spiro spero. she/her
Get E2EE DMs on Germ! 🔑
https://ger.mx/A8RNdqpVCF0_VW6QP0yqb4JK8W2SNlPNayEQfDxIN9OI#did:plc:juj4a7jagip23ja36opmi4d4
Northwestern University--American Association of University Professors. Defending academic freedom and shared governance.
PhD candidate @ Stanford Applied Cryptography Group
https://c.rypto.systems/
Cryptographer
https://chancharles92.github.io/
Columnist and chief data reporter the Financial Times | Stories, stats & scatterplots | john.burn-murdoch@ft.com
📝 ft.com/jbm
drawing cryptographers, one talk at a time
The world's leading venue for collaborative research in theoretical computer science. Follow us at http://YouTube.com/SimonsInstitute.
Ca’ Foscari University of Venice / University of Bologna / University of Warwick
I am a student.
web: massimilianofurlan.github.io
https://www.thoschneider.de
Assistant Professor at Cornell. CS theory, cryptography, quantum computing. he/him
Postdoctoral researcher in cryptography at ENS Paris
erkantairi.com
Assistant professor at UIUC ECE
PhD Candidate @UIUC. Prev @IIT Delhi
Personal website: https://sourav1547.github.io/












 12.03.2025 19:14 — 👍 0 🔁 0 💬 0 📌 0
12.03.2025 19:14 — 👍 0 🔁 0 💬 0 📌 0


