USENIX WOOT Conference 2026: two submission deadlines this year!
- Cycle 1: December 12, 2025 *only one month away* !
- Cycle 2: March 3, 2026
WOOT still has a SoK track and an "Up-and-coming track" (~Industry), CFP for details:
www.usenix.org/conference/w...
12.11.2025 11:00 — 👍 5 🔁 6 💬 0 📌 0
Merci pour le post :)
10.10.2025 18:17 — 👍 1 🔁 0 💬 0 📌 0

Signal calls on Germany to vote against ‘Chat Control,’ saying it would leave EU market
The head of the Signal Foundation raised concerns around Germany now refusing to say whether it will support Chat Control in an upcoming vote.
Signal to leave EU rather than comply w/ Chat Control, which would scan all messages sent over end-to-end encrypted platforms. Vote on Chat Control's future Oct 14. Germany is the swing vote. Officials there opposed the measure in past but new govt silent re position
therecord.media/signal-calls...
06.10.2025 15:37 — 👍 21 🔁 13 💬 0 📌 0
cr.yp.to:
2025.10.04: NSA and IETF
Source: American Cryptology During the Cold War, 1945-1989 Book III: Retrenchment and Reform, 1972-1980 (declassified)
archive.org/details/cold...
Which I found thanks to this nice article by @hashbreather.bsky.social
blog.cr.yp.to/20251004-wea...
06.10.2025 21:36 — 👍 0 🔁 0 💬 0 📌 0

Interesting story how DES 56 became a 56-bit key algorithm (while having a 64-bit block size):
"NSA tried to convince IBM to reduce the length of the key from 64 to 48 bits. Ultimately, they compromised on a 56-bit key."
06.10.2025 21:33 — 👍 4 🔁 2 💬 1 📌 0

The battle to stop Chat Control continues, act now!
Unfortunately, the battle against Chat Control continues this month. For human rights, for civil liberties, for safety, and for democracy, this privacy-wrecking proposal must be stopped. We need your ...
"Bad news: The proposal is going forward to be voted on on October 14th, and there's still no blocking minority achieved, as Germany reverted its position to undecided.
Good news: There is still time to fight back!"
Shut this monstrosity down NOW
23.09.2025 19:23 — 👍 10 🔁 10 💬 0 📌 0

The table of contents for Phrack 72 from phrack.org
At long last - Phrack 72 has been released online for your reading pleasure!
Check it out: phrack.org
18.08.2025 21:33 — 👍 121 🔁 63 💬 0 📌 4
.:: Phrack Magazine ::.
Phrack staff website.
Phrack 72 released today. phrack.org/issues/72/1
It got me thinking. I first read Phrack back in the 90's as I started hanging out on IRC (maybe '93 or '94?), as I was learning about FreeBSD and later, Linux. It must have been Phrack 43-45 where I started.
What a wild ride on the Internet.
18.08.2025 22:26 — 👍 6 🔁 5 💬 1 📌 0

I reverse engineered Lockbit's Linux ESXi variant, also explaining how I did some of the steps! For the fun of it, cause reverse engineering is lots of fun. Enjoy!
hackandcheese.com/posts/blog1_...
18.08.2025 16:55 — 👍 11 🔁 5 💬 1 📌 1

@blackhoodie.bsky.social will be at @sec-t.bsky.social on September 10th with a training on Linux Malware Reverse Engineering, for women by women! We have very few seats left 😁 blackhoodie.re/SecT2025/
14.08.2025 14:02 — 👍 12 🔁 9 💬 0 📌 0

WOOT '25 Technical Sessions
Discounted early bird registration for WOOT '25 is still open until Monday - www.usenix.org/conference/w... - join us in Seattle on Aug 11/12 (right before USENIX Security) for talks and discussions on great cutting-edge offensive security research. Full program at www.usenix.org/conference/w...
17.07.2025 13:23 — 👍 3 🔁 5 💬 1 📌 0
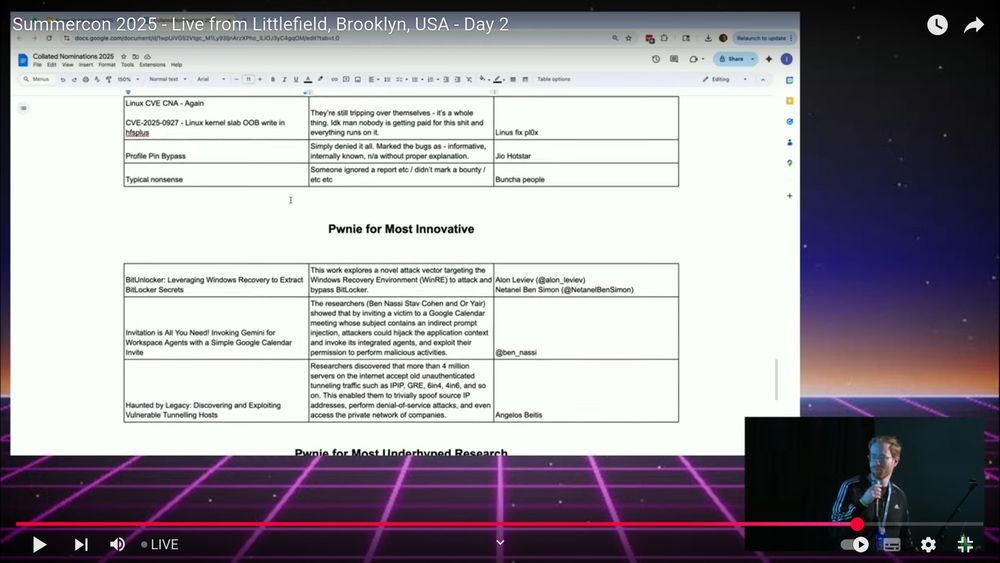
Our research on open tunneling servers got nominated for the Most Innovative Research award :)
The work will be presented by Angelos Beitis at Black Hat and also at USENIX Security
Brief summary and code: github.com/vanhoefm/tun...
Paper: papers.mathyvanhoef.com/usenix2025-t...
12.07.2025 20:17 — 👍 7 🔁 6 💬 0 📌 0
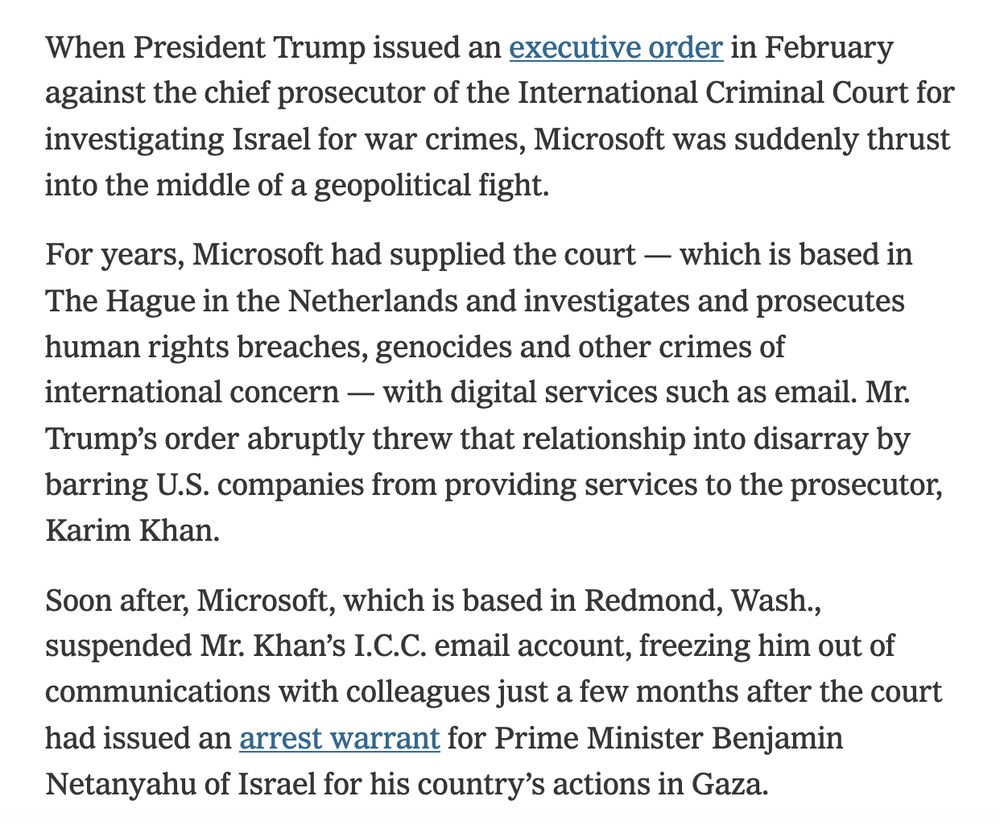
Huge implications from this: Microsoft cut off the email of the chief prosecutor of the International Criminal Court, because of his work on Israel www.nytimes.com/2025/06/20/t...
20.06.2025 18:18 — 👍 1339 🔁 707 💬 39 📌 100
Security through Transparency: Tales from the RP2350 Hacking Challenge | USENIXusenix_logo_notag_white
Two winners of the RP2350 Hacking Challenge will present their results at WOOT!
Muench et al. break its secure boot guarantees through voltage, electromagnetic, and laser fault injection 💥 techniques: www.usenix.org/conference/w...
19.06.2025 12:48 — 👍 7 🔁 3 💬 1 📌 0
YouTube video by OffensiveCon
OffensiveCon25 - Daniel Klischies and David Hirsch
Our OffensiveCon talk on stateful baseband emulation (and how improper string handling led to baseband RCE) is available on YouTube: youtu.be/zoAITq7jUM8. It has been a pleasure; awesome conference, brilliant people. Slides and paper: www.danielklischies.net/research/bas...
28.05.2025 11:21 — 👍 9 🔁 4 💬 0 📌 0

“Google wanted that”: Nextcloud decries Android permissions as “gatekeeping”
Without full file access, it’s kind of hard to use your own cloud.
Since mid-2024, Google has refused to reinstate the access Nextcloud needs for uploading and syncing other file types to its host-your-own cloud platform.
14.05.2025 18:46 — 👍 27 🔁 9 💬 0 📌 3
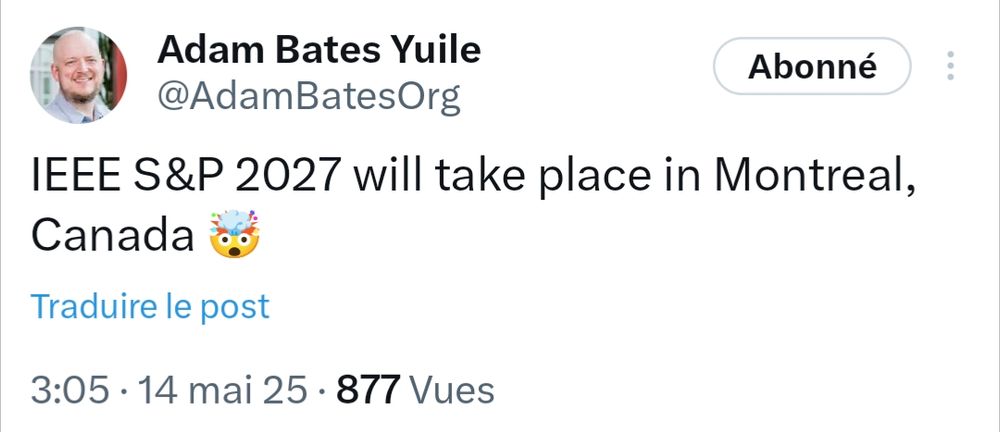
Haven't seen this on Bluesky yet: S&P 2027 will take place in Montreal, Canada!
14.05.2025 06:45 — 👍 28 🔁 17 💬 2 📌 3
📢 Excited to announce that the results on BaseBridge, our project on improving cellular baseband emulation, are going public this week. Dyon will present at IEEE S&P on Monday 3pm, while David and I will be on stage at @offensivecon.bsky.social on Saturday 11am with even more details! 1/6
11.05.2025 10:23 — 👍 14 🔁 7 💬 1 📌 1
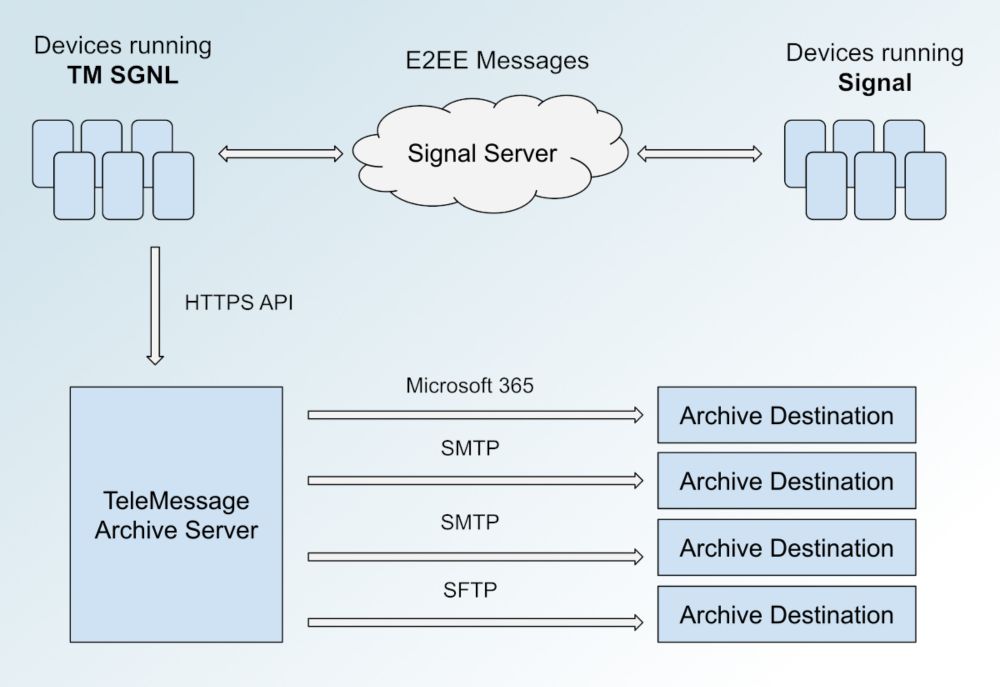
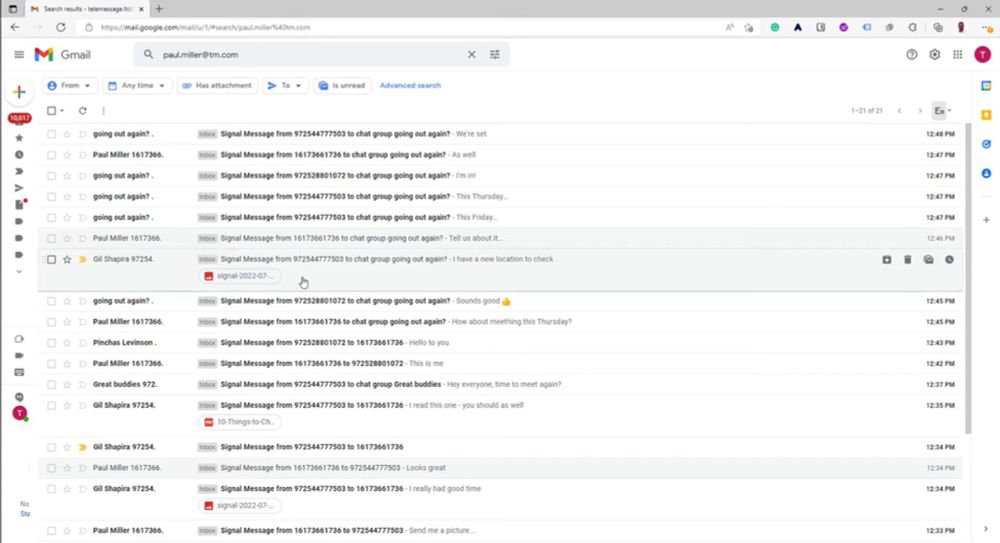
Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs
Despite their misleading marketing, TeleMessage, the company that makes a modified version of Signal used by senior Trump officials, can access plaintext chat logs from its customers.
In this post I ...
Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs. My findings are based on TM SGNL's source code, and they are corroborated by hacked data micahflee.com/despite-misl...
06.05.2025 20:00 — 👍 775 🔁 323 💬 23 📌 88
Site d'actualités collaboratif pour développeur·se·s — Un service @humancoders.com
https://news.humancoders.com
▪️ Le compte Bluesky de Libération, avec une sélection de nos articles, enquêtes, billets et chroniques
▪️ Pour suivre les journalistes de Libé : kit de démarrage
▪️ Abonnez-vous à Libération pour tout lire : https://libe.fr/bsky/
#Formations & 👨🏻🎓 #cybersécurité technique & orga, vie privée, continuité d’activité #Pentest #BlueTeam #ISO27001 #EBIOSRM #CISSP #DPO #RGPD #ISO22301
Compte officiel de l'Agence nationale de la sécurité des systèmes d'information (ANSSI) | Retrouvez les alertes de #cybersécurité sur le compte @cert-fr.bsky.social
CEO @HS2formation👨🏻🎓http://www.hs2.fr http://www.schauer.fr 86:#LogicielLibre 87:#Cybersécurité 1989:#HSC👨💻@OSSIRFrance @Club27k @clusif 🎧@nolimitsecu
Fight Chat Control (https://fightchatcontrol.eu) is a citizen-led initiative created to raise awareness about the European Union's proposed "Chat Control" regulation. We are not affiliated with any political party. Also on Mastodon: @chatcontrol.
Suivez les dernières actualités de MISC, bimestriel dédié à la #cybersécurité offensive & défensive. Retrouvez-nous en kiosque & sur https://boutique.ed-diamond.com/.
European Research Council, set up by the EU, funds top researchers of any nationality, helping them pursue great ideas at the frontiers of knowledge. #HorizonEU
Bienvenue sur le compte de la bibliothèque d'#EURECOM : Grande Ecole d'ingénieurs et Centre de recherche en Sciences du numérique
Tenured Researcher @Inria
USENIX Security Artifact Evaluation Co-Chair 2025 & 2026
Web Security & Privacy: JavaScript (in)security, browser extensions
https://aurore54f.github.io
Full Professor in Systems Security @vuamsterdam. Co-leads vusec.net
think bad, do good. | https://sa.my
PhD Student @TU Braunschweig. Mainly web security, some program analysis, and privacy.
Project Foxhound core maintainer.
PE@Cisco, netsec enthusiast
since 1985
https://phrack.org
Site communautaire dédié aux arnaques d’internet.
🛠️ Nos services : http://bit.ly/3ZRsCkE
📢 Pour signaler une arnaque : http://bit.ly/3D5doMT
Doctorant UQAM, @RAS_NSA, Chercheur associé @FRS_org, travaille sur la culture stratégique russe...et ses déboires. Chewbaca-morphe patenté et lurker de blousks émérite
Observateur de l’extrême. 📍Paris/🇫🇷/🇪🇺/🌍
Podcast : radiofrance.fr/franceinfo/podcasts/complorama
Team : conspiracywatch.info
Me : tristan.pro
Deputy Director, Fondation pour la recherche stratégique.
Non-Resident Fellow, Institut Montaigne.
Geopolitics, strategy and stuff.
Personal account.
b.tertrais@frstrategie.org
Books: tinyurl.com/bdzbxnyx
"Luke, je suis ton pépère"