
Glad to see we’re able to reach a larger audience! The Chinese version of our book is doing well. @oflynn.com /ht Haisu Lee (our translator)
25.02.2025 15:51 — 👍 3 🔁 1 💬 0 📌 0
Relive: Hacking the RP2350 – 38C3: Illegal Instructions Streaming
Live streaming from the 38th Chaos Communication Congress
Great presentation, glitching the RPi 2350 on an unprotected path (USB VDD, they glitch protect others) to disturb reading critical OTP permission bits to mistakenly enable unsecured RISC-V cores to mess with TrustZone secured ARM cores without any limitations.
streaming.media.ccc.de/38c3/relive/...
29.12.2024 04:53 — 👍 12 🔁 4 💬 0 📌 0
38c3: Hacking the RP2350
The RP2350 security architecture involves several interconnected mechanisms which together provide authentication of code running on the chip, protected one-time-programmable storage, fine-grained con...
events.ccc.de/congress/202...
You can bypass security on the RP2350 by glitching the OTP power supply (which does not have a glitch detector on it). This causes OTP to supply "guard data" instead of real data, and interpreting the guard data happens to enable RISC-V mode, which can do anything.
28.12.2024 11:35 — 👍 79 🔁 16 💬 4 📌 4
Yet another DMA form factor… Proper use of the IOMMU remains the primary mitigation.
09.12.2024 16:11 — 👍 0 🔁 0 💬 0 📌 0
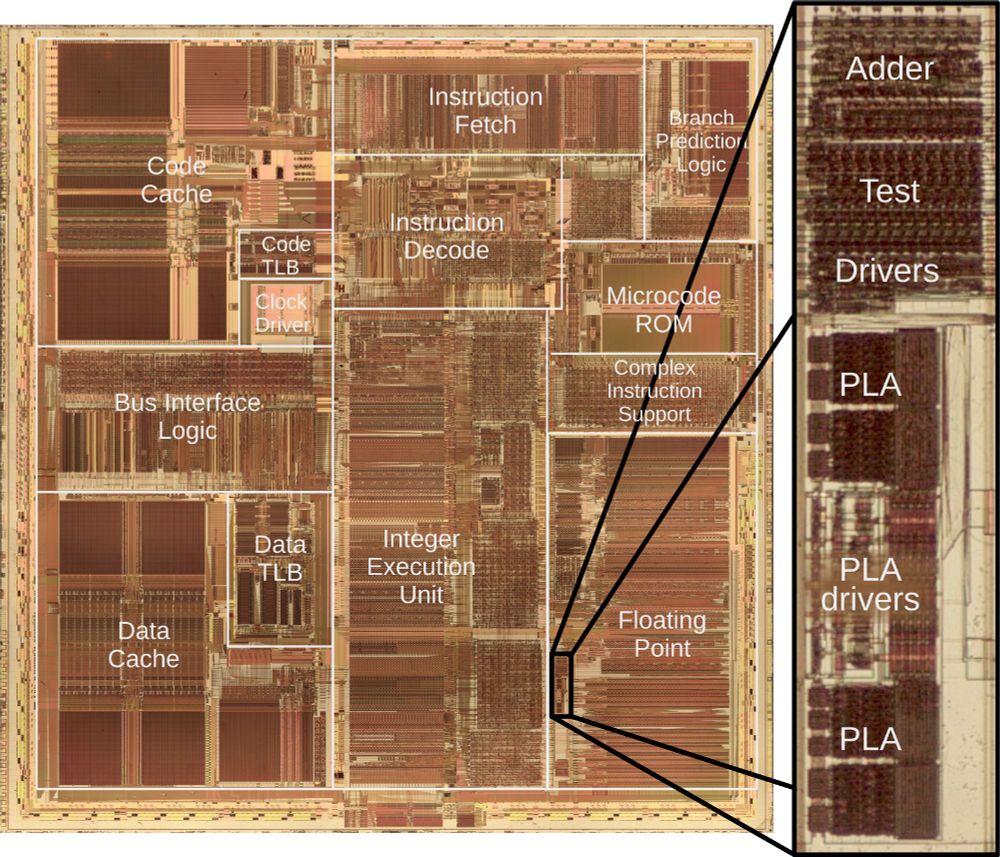
A die photo of the Pentium processor with the main functional blocks labeled including the caches, instruction fetch and decode, integer execution, and floating point. The image consists of complex patterns of rectangular regions in reddish and brownish colors. The image zooms in on a small part of the floating point unit giving a detail of an adder and PLA circuit.
Intel launched the Pentium processor in 1993. Unfortunately, dividing sometimes gave a slightly wrong answer, the famous FDIV bug. Replacing the faulty chips cost Intel $475 million. I reverse-engineered the circuitry and can explain the bug. 1/9
06.12.2024 16:48 — 👍 712 🔁 235 💬 16 📌 28
vintage computers, tubes, the MOnSter6502, cross-sectioned electronic parts, capacitors, and other detritus. coauthor of http://nostarch.com/open-circuits
Colin is a huge nerd. Hardware hacking, open-source hardware, electronics design, academic stuff, dog stuff in some order. Assistant Prof @ Dalhousie Uni, advisor/co-founder NewAE Technology Inc.
Doomscroller avant la lettre. This account is in English, public replies in other languages will be hidden.
Occasional posts in Dutch on @rop.nl and in German on @deutsch.rop.nl
CISO @Lyft - Former Binary entomologist - Opinions are my own.
CEO and founder of runZero.com, previously the founder and lead developer of Metasploit, a CSO, a consultant, and the head of various security research teams. Contact info, presentations, and more at https://hdm.io/
Hacker & CEO @SocialProofSec security awareness/social engineering training, videos, talks | 3X @DEFCON🥈 | Chair @WISPorg | @CISAgov Technical Advisory Council under Director Jen Easterly
Autonomous Carbon Based LLM with 42 years of tuning on Information Attack and Defense.
Host of CanSecWest, and PacSec.
Security audits, code, IR, LLM, red team consulting.
Specialize in Firmware, and RF.
VA7MOV
I've been a software developer, application security engineer, a Chief Security Officer and a founder. I am a husband & dad. Formerly Datadog, Iterable, NCC & iSEC Partners. Living the dream in America's Pacific Northwest.
Jan 10-12, 2025
Washington, D.C.
Less 🫎 Than Ever
This account is mostly used to push information. Got questions? Email us at info @ shmoocon.org.
We are HushCon. NYC, June 13-14. Seattle, Dec
We take your privacy and security seriously.
Hardware hacker, computer engineer, former L0pht member and juvenile delinquent, sometimes known as Kingpin. https://linktr.ee/joegrand
Trainer and Researcher, SecuringHardware.com
Ramblings of a Mad Englishman: Hacker @ BBC's Real Hustle & Mr Robot. Head of Sec @ DEF CON. Founder @ CTI-League, Ransomware Taskforce, w00w00, CDC NSF, (He/Him).
Also
Twitter @marcwrogers
Mastodon cj@chaos.social
Professor of Security Engineering; Head of UCL Information Security Research Group @sec.cs.ucl.ac.uk; Director Open Rights Group. 🐘 https://mastodon.social/@sjmurdoch 🐦 @sjmurdoch 🌍 https://murdoch.is/
⚠️ MIRROR OF twitter.com/MarsCuriosity
⚠️ If you own the original account and want to claim this, please contact @twttr-mirrors.bsky.social
Threat modeling. BH Review Board. Affiliate Professor, UW. Fixed autorun. Helped create CVE.
Not sure why we're building graphs on yet another (effectively) centralized system. https://infosec.exchange/@adamshostack
Continuously learning about computer security through research and development.
the san francisco fog. have fun always carrying a light sweater.



