3️⃣ 🛠️ Enhanced Enrichment Function
Recently, I've released a #KQL function integrating #ExposureManagement and #EntraOps data to identify sensitive callers, actions, and targets. Updated to support parameters like IP Address and Token Identifier.
🔗 github.com/Cloud-Archit...
30.07.2025 06:47 — 👍 0 🔁 0 💬 0 📌 0
2️⃣ 🔍 Normalized schema for shared queries
Want to reuse existing queries or unify detection logic across both tables? I’ve published a #KQL function that normalizes the schema of GraphApiAuditEvents to match that of MicrosoftGraphActivityLogs.
🔗 github.com/Cloud-Archit...
30.07.2025 06:47 — 👍 0 🔁 0 💬 1 📌 0
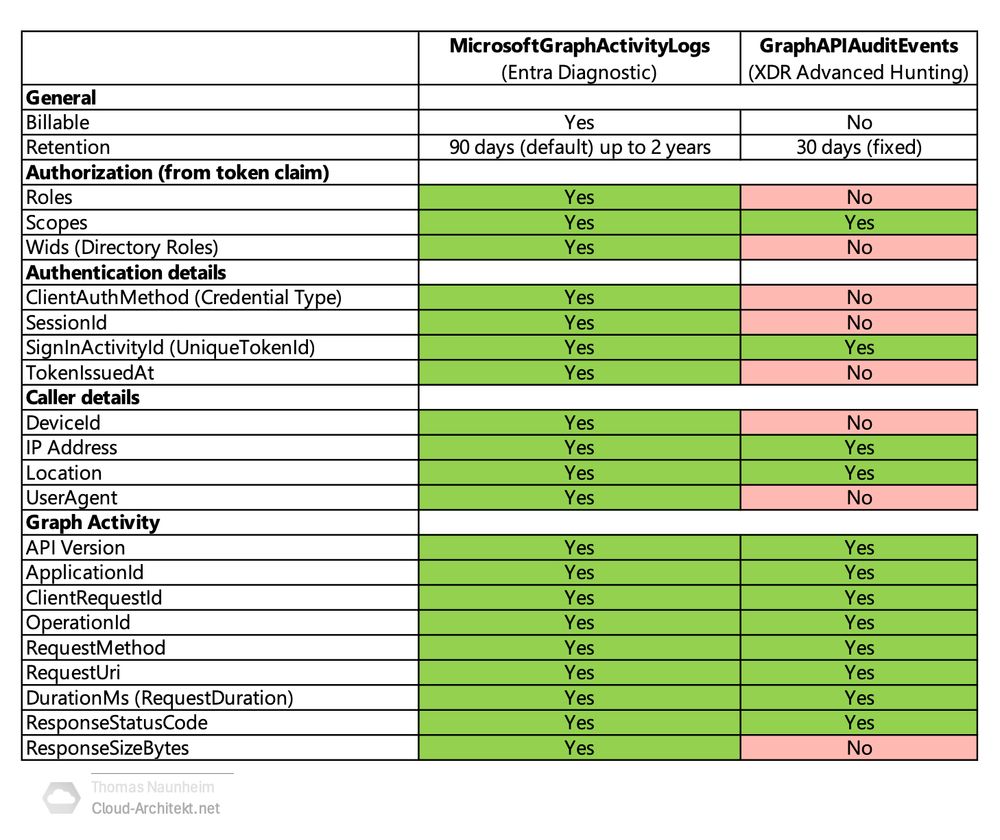
1️⃣ 🤔 Comparison Deep Dive
What are the differences between GraphApiAuditEvents (XDR) and MicrosoftGraphActivityLogs (Diagnostic Logs in hashtag#MicrosoftSentinel)? I’ve built a comparison table outlining the differences in column availability and detail levels.
30.07.2025 06:47 — 👍 0 🔁 0 💬 1 📌 0
The availability of GraphApiAuditEvents in #MicrosoftDefender brings significant value to every environment, enhancing capabilities for detecting and hunting #MicrosoftGraph API calls. In my recent research, I’ve created a few resources that I’m happy to share with the community.
30.07.2025 06:47 — 👍 0 🔁 0 💬 1 📌 0
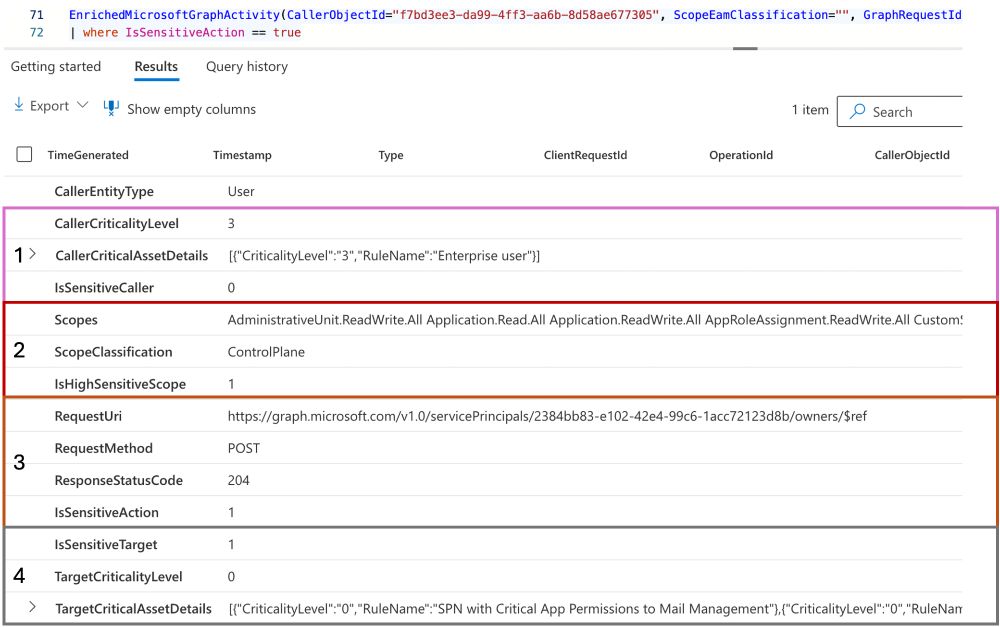
4. IsSensitiveTarget 🎯
The modified object is classified as critical (based on Exposure Management Critical Assets), and the applied rule details are displayed. In this case, the service principal has been assigned critical app permissions in Exchange Online.
17.07.2025 06:43 — 👍 0 🔁 0 💬 0 📌 0
3. IsSensitiveAction ▶️
The Graph request includes a POST to the servicePrincipal endpoint, which is flagged as a sensitive modification. This logic is experimental and simplified, so it may result in inaccurate classification and should be used in combo with others indicators.
17.07.2025 06:43 — 👍 0 🔁 0 💬 1 📌 0
2. IsHighSensitiveScope 🔑
However, the scope includes Application.ReadWrite.All, which has been identified as "Control Plane" by using EntraOps classification model.
17.07.2025 06:43 — 👍 0 🔁 0 💬 1 📌 0
In the following example, several indicators are included that make this particular call interesting for further investigation:
1. IsSensitiveCaller 🗣️
A regular enterprise user (based on Exposure Management Critical Asset information) is calling Graph.
17.07.2025 06:43 — 👍 0 🔁 0 💬 1 📌 0
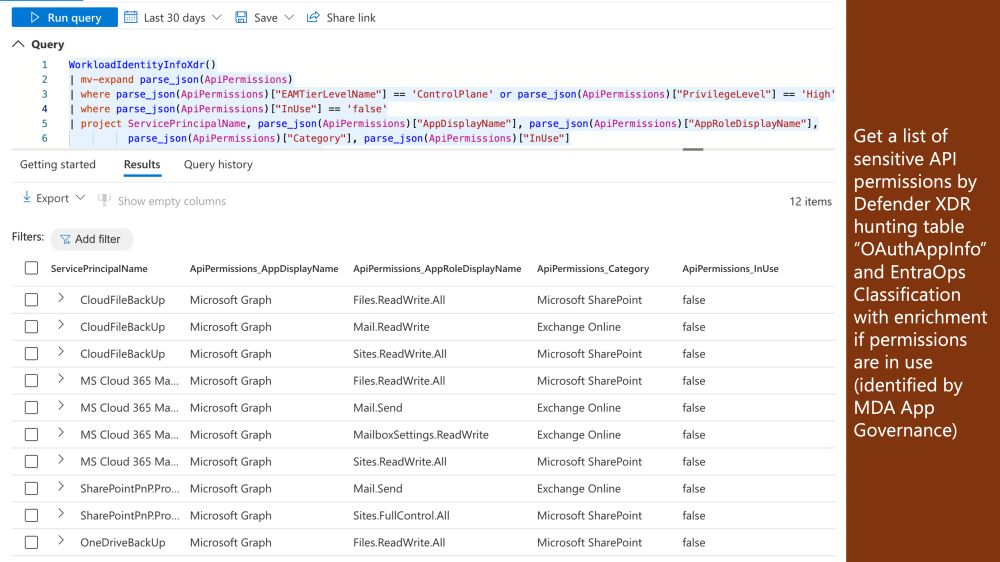
I've created an experimental KQL function that enriches the data with details from #ExposureManagement and #EntraOps. This might help identify sensitive Graph Calls from the large volume of events in this table.
🔗 The query is available here:
github.com/Cloud-Archit...
17.07.2025 06:43 — 👍 0 🔁 0 💬 1 📌 0
🚀🔎 Track Sensitive Graph API Calls with my new #KQL Function for #MicrosoftDefenderXDR
Microsoft has released the new advanced hunting table "GraphAPIAuditEvents" which offers great opportunities to investigate activities based on #MicrosoftGraph API calls.
17.07.2025 06:43 — 👍 3 🔁 2 💬 1 📌 0
YouTube video by Semperis
Defending Tier 0: Taking Control of Your Cloud's Control Plane
My session, “Defending Tier 0: Taking Control of Your Cloud’s Control Plane,” from last year’s #HIPConf is now available on YouTube. The session focused on securing privileged access and implementing a tiered administration model in #MicrosoftEntra.
youtu.be/pVPEieHtOVM
17.05.2025 07:48 — 👍 5 🔁 1 💬 0 📌 0
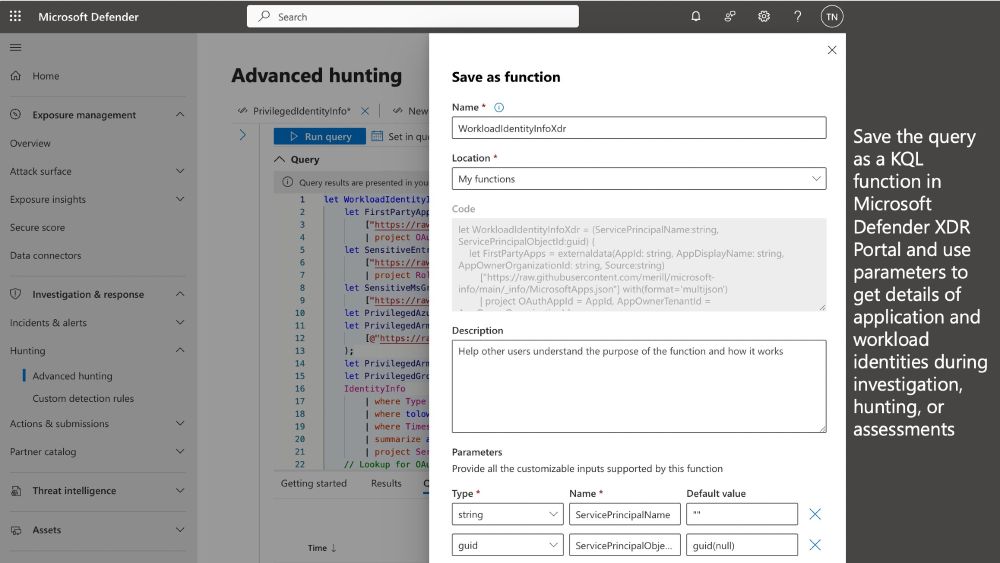
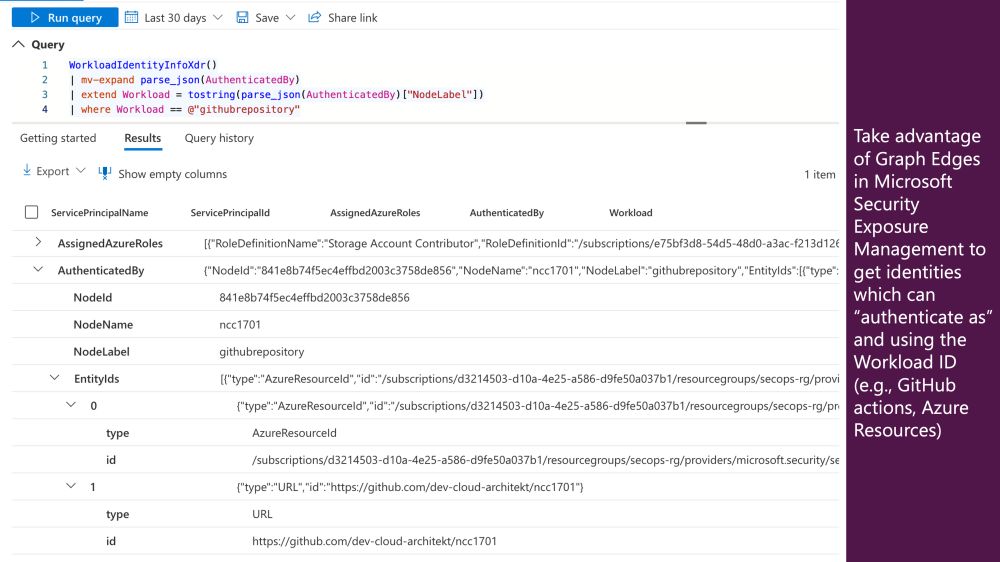
I've published a #KQL function ("WorkloadIdentityInfoXDR") for #MicrosoftDefender to enhance details of #MicrosoftEntra #WorkloadID from various sources, incl. the new table "OAuthAppInfo" but also IdentityInfo table and #ExposureManagement. (1/2)
🔗 github.com/Cloud-Archit...
09.04.2025 11:51 — 👍 1 🔁 1 💬 1 📌 0

Cloud #IdentitySummit 2025 is back!
Save the date and join this community event with #IdentitySecurity, #MicrosoftEntra, and #CloudIdentity deep dive sessions in Dortmund, Germany.
Call for Papers is open now:
sessionize.com/cloud-identi...
Stay tuned for more details:
www.identitysummit.cloud
08.04.2025 05:23 — 👍 3 🔁 1 💬 0 📌 0

EntraOps Privileged EAM
Community project to classify, identify and protect your privileges based on Enterprise Access Model (EAM)
Check out my community tool #EntraOps if you are interested to get a customized and detailed analysis of all permanent and PIM-managed role assignments in #EntraID, #Intune and #IdentityGovernance: www.cloud-architekt.net/entraops/
17.03.2025 06:12 — 👍 0 🔁 0 💬 0 📌 0
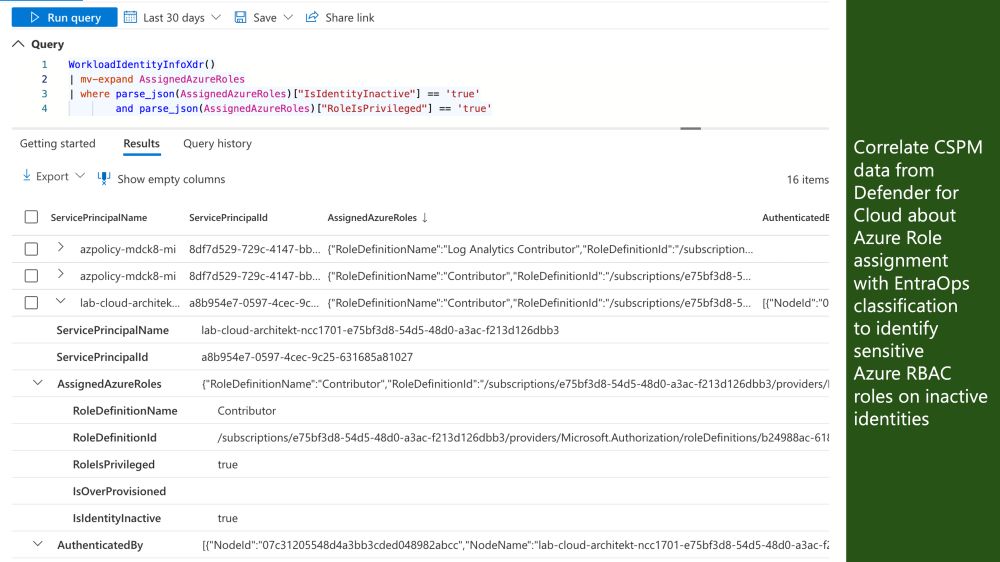
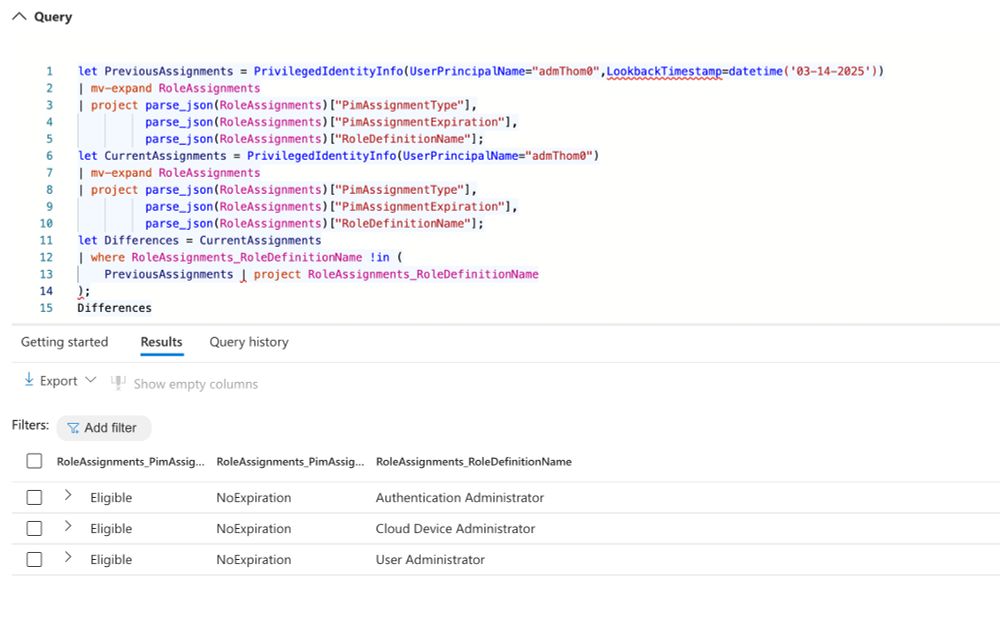
There are some current limitations on this preview (for example, custom or scoped roles are not covered, data seems to be available in MDI tenants only). However, the new column offers some great capabilities at no additional implementation efforts.
17.03.2025 06:12 — 👍 0 🔁 0 💬 1 📌 0
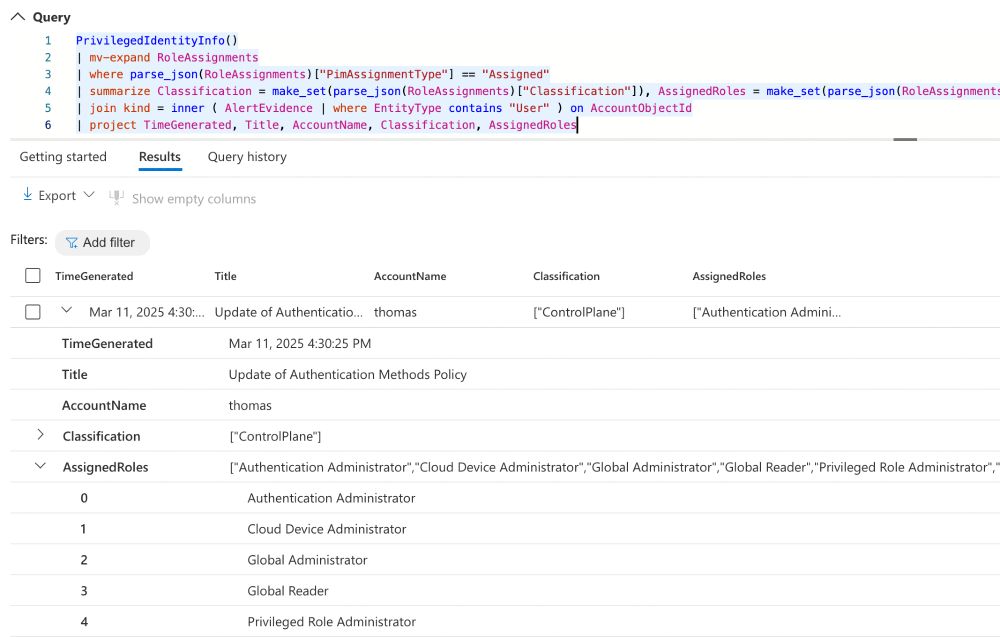
-🚨 Discovering alerts of privileged users with active or assigned roles, along with details on related roles and their highest access tier classification.
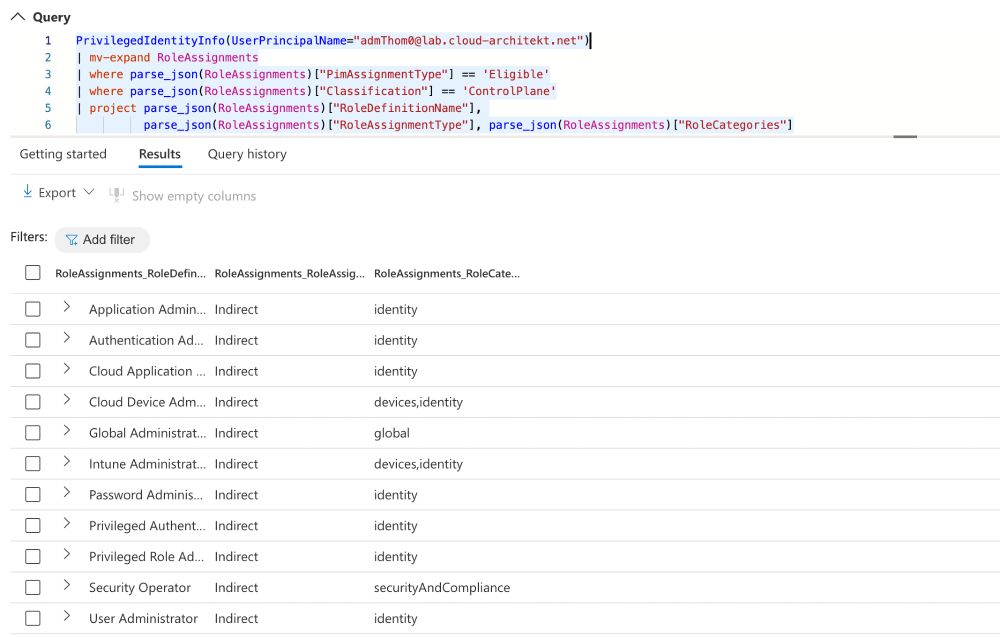
- 🕓 Determine which eligible or active roles were assigned at a specific time, and compare them to their current status
17.03.2025 06:12 — 👍 0 🔁 0 💬 1 📌 0
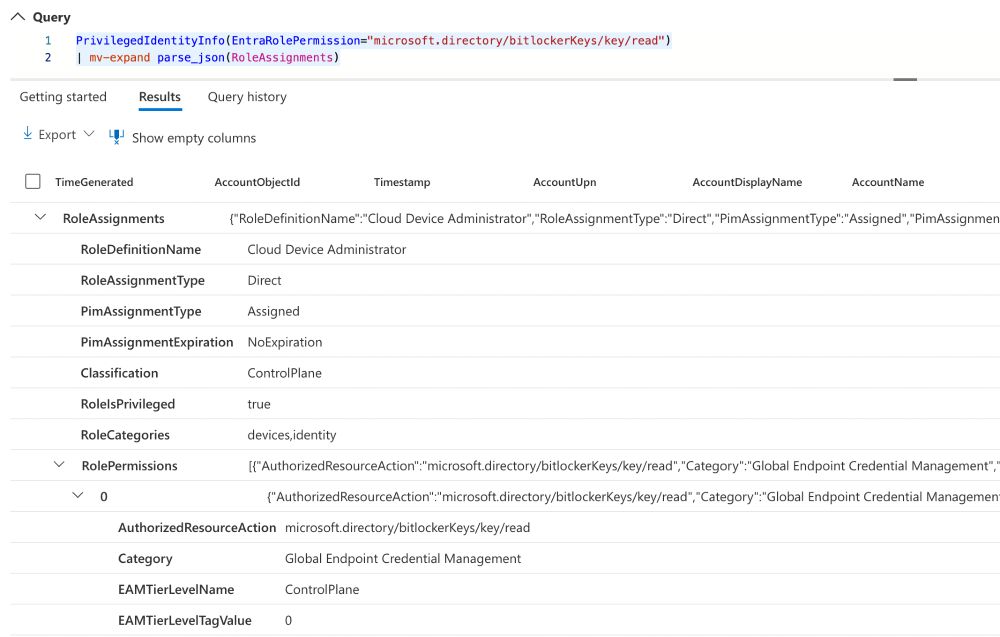
This enables powerful hunting queries, such as:
-⚡️ Identifying assigned roles that include specific actions (e.g., reading BitLocker keys).
- 🦸♂️ Listing all eligible assignments for Control Plane (Tier0) roles, including Microsoft role categories and assignment types (direct or indirect).
17.03.2025 06:12 — 👍 0 🔁 0 💬 1 📌 0
Thank you to everyone who joined my session in Amsterdam or via livestream! Huge thanks to the Yellowhat organizers for this incredible conference and for having me. I had an awesome time and can’t wait to see you all soon…
08.03.2025 09:31 — 👍 1 🔁 0 💬 0 📌 0

I had the great pleasure of speaking about #MicrosoftEntra Token Hunting 🍪🔎 at #YellowHat 🚧👷♂️. You can find the slides from my session here:
📄 github.com/Cloud-Archit...
All #KQL sample queries are available in my repo:
👨💻 github.com/Cloud-Archit...
08.03.2025 09:31 — 👍 8 🔁 2 💬 1 📌 0

I have the great pleasure of joining a shared session with @samilamppu.bsky.social at the M365 Security & Compliance User Group tonight. Last preparations are now in full swing... You can find more details about the meetup and register for this free online event here:
www.meetup.com/m365sandcug/...
26.02.2025 12:51 — 👍 3 🔁 0 💬 0 📌 0

Yellowhat
Yellowhat is a cutting-edge cybersecurity event dedicated to Microsoft Security Technology, offering advanced deep-dive sessions (level 400+) for seasoned professionals. It brings together experts and...
Interested to learn more? I'll be talking about token hunting at #Yellowhat and covering how to leverage these new sign-in details. More details about this free community event can be found here: yellowhat.live (3/3)
11.02.2025 17:31 — 👍 1 🔁 0 💬 0 📌 0

Azure Monitor Logs reference - SigninLogs - Azure Monitor
Reference for SigninLogs table in Azure Monitor Logs.
Previously, these details were only available in XDR Hunting table "AADSignInEventsBeta", Portal and/or Graph API. These added properties offer the opportunity to write new analytics rules and hunting queries, for example in the area of #TokenTheft. (2/3)
learn.microsoft.com/en-us/azure/...
11.02.2025 17:31 — 👍 1 🔁 0 💬 1 📌 0
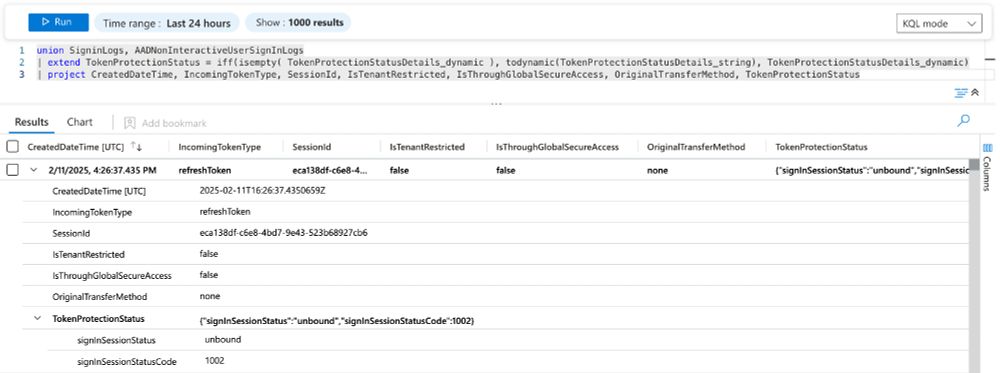
Enhancements in #MicrosoftEntra (diagnostic) logs: Several interesting sign-in properties (including Session ID, status for Token Protection, or GSA traffic) have been added to the sign-in logs and available in #MicrosoftSentinel. (1/3)
11.02.2025 17:31 — 👍 3 🔁 2 💬 1 📌 0

I'm building a new home for IntuneBrew and would like to share my progress so far.
IntuneBrew.com will serve as the project's landing page, featuring a Quick Start Guide and an overview of key features.
29.01.2025 16:37 — 👍 11 🔁 4 💬 2 📌 0
LinkedIn
This link will take you to a page that’s not on LinkedIn
EntraOps repository:
github.com/Cloud-Archit...
Learn more about XSPM and Graph:
Deep Dive blog post on XSPM by @samilamppu.bsky.social
samilamppu.com/2024/04/25/m...
Blog posts by @fabian.bader.cloud
cloudbrothers.info/en/workshop-...
cloudbrothers.info/en/find-late...
Kusto Graph rocks! (3/3)
29.01.2025 06:47 — 👍 2 🔁 1 💬 0 📌 0
AzureSentinel/Hunting Queries/EID-PrivilegedIdentities/EntraOpsGraphPrivilegedObjectOwner at main · Cloud-Architekt/AzureSentinel
Sharing my KQL queries for Azure Sentinel. Contribute to Cloud-Architekt/AzureSentinel development by creating an account on GitHub.
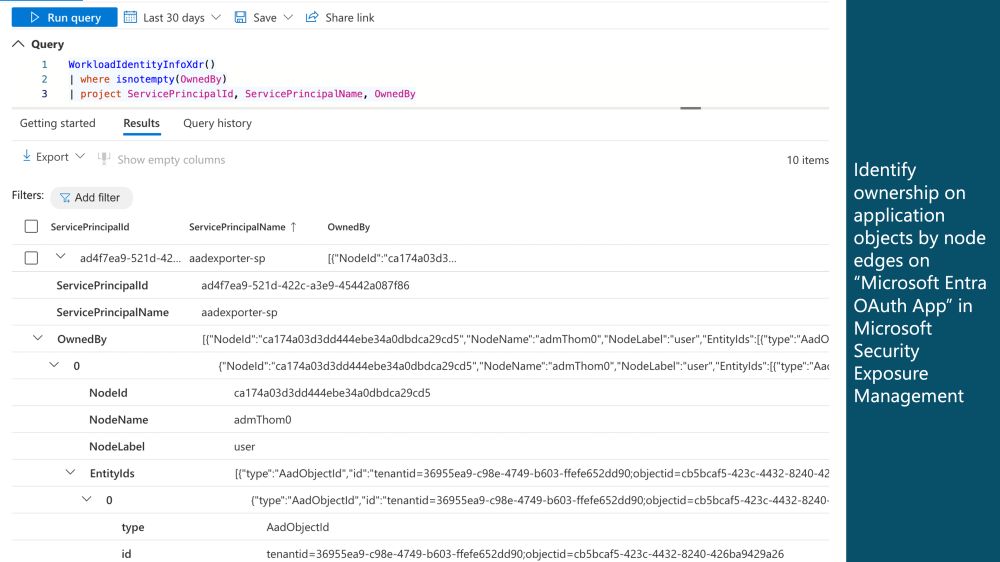
This also shows the classification of the owner by identified privileges in EntraOps and applied rules in Critical Asset Management in XSPM. The query can be extended to analyze potential attack paths in combination with other edges. (2/3)
KQL sample query:
github.com/Cloud-Archit...
29.01.2025 06:47 — 👍 0 🔁 0 💬 1 📌 0
Do you like to know if ownership of privileged objects in #MicrosoftEntra has been delegated to lower privileged users? Graph semantics in KQL and XSPM allow building powerful queries and analyzing data as graphs. I've started to include data from #EntraOps to analyze delegated ownership. (1/3)
29.01.2025 06:47 — 👍 4 🔁 1 💬 1 📌 0

Final touches and rehearsal for my #TECTalk on #TokenSecurity in #MicrosoftEntra tonight. I'll be discussing attack scenarios on various token types and how TPM, Token Protection, CAE & Global Secure Access can help prevent token theft. Register for the free webinar:
www.quest.com/event/the-ex...
23.01.2025 08:23 — 👍 2 🔁 1 💬 0 📌 0
Dir. of Identity Standards at Microsoft. Generally a happy camper. Canadian married to an Aussie machinist identity geek. Living in an 1893 Victorian in San Francisco and renovating as we go.
Microsoft MVP and Freelance Security Consultant, #Microsoft Defender for Endpoint #MDE, Office #MDO, Microsoft 365 Defender #M365D #WPNinjasNL #TalkingSecurity
Trying to find a path in the fog.
Community event with focus on related topics to #AzureAD and Cloud #Identity in #Azure. Organized by the @AzureBonn Team.
Formerly VP Identity Security @ Microsoft, now on sabbatical; sailor, musician, off-road enthusiast, photographer, writer, adhd adventurer.
#Security #Azure #EntraID #XDR #MDE #Identity #M365 #AD #PKI #KQL
Microsoft MVP
Tweets and opinions are my own
Loves Jesus, loves others | Husband, father of 4, security solutions architect, love to learn and teach | Microsoft MVP | @TribeOfHackers | 🐘infosec.exchange@nathanmcnulty
I want a 🐈❤!!!
Starter Packs: https://bsky.app/starter-pack/did:plc:fl5ztptq45qb2qbyo2wkojjk/3le2frmto5t26
☁️ Chief Azure Technologist at adesso SE | #Microsoft #MVP for #Azure & #Security | #MCT
🇩🇪 | Gov | Sec | Hybrid |
@CloudInspires #Podcast
Founder of #AzureBonn and #IdentitySummit
Opinions my own.
Microsoft MVP | Modern IT – Cloud – Workplace | Blogger, Speaker #MSIntune #Entra #ConfigMgr #Windows #Security | oliverkieselbach.com
Microsoft Security MVP + Microsoft Security Practice Lead at Threatscape
Mostly: Entra, Defender, Intune, Purview, and Microsoft 365
Also: dad, metal, lifting, wrestling, cars
Mostly on Twitter rather than here: @rucam365
MS Entra ID and Identity Enthusiast, author and community speaker
Principal Product Manager @Microsoft #security focused on #Entra #Identity and Identity Governance
- 🆔 & #Cybersecurity
- Star Wars 🌟 nerd
- Disney Adult 🏰
My posts are not official support of my employer
My info and content is at https://jeftek.com
☁️ Microsoft employee
🎤 ITOps/Cloud/Hybrid
💻 Hashicorp Ambassador & GitKraken ambassador
✍ Thought Leader & Storyteller
🐄 Farming enthusiast
👀 Views are my own
Entra nerd currently @ #Semperis. Parent. Partner. MS Security MVP. Views are those of my cat.