KQL to review #DirectSend abuse
EmailEvents
| where SenderMailFromDomain == RecipientDomain
| where isempty(Connectors)
| where DeliveryAction !in ("Junked", "Blocked")
| extend AuthenticationDetails = parse_json(AuthenticationDetails)
| where AuthenticationDetails.DMARC == "fail"
05.08.2025 23:47 — 👍 4 🔁 1 💬 1 📌 2
And yet... this is the only reason I know this setting exists 😂
I had to do troubleshooting, more than a few orgs have this applied to all users in an Entra environment :(
03.08.2025 17:07 — 👍 0 🔁 0 💬 0 📌 0
And they do, in several places, but it's not as comprehensive as it could be (though great for a starting point)
Microsoft has long published security benchmarks based on research/testing and customer support cases
They also do the Secure Score stuff which is much better than it used to be :p
03.08.2025 17:05 — 👍 0 🔁 0 💬 0 📌 0
Or anything else requiring device identity really... So no filter for devices, no compliance, no hybrid join grant control :-/
Sadly, I'm not a member of CIS anymore nor have the time to go through all of the settings for issues, but hopefully they are listening to feedback :)
02.08.2025 23:25 — 👍 6 🔁 0 💬 0 📌 0

While I'm on the topic of CIS Benchmarks...
If you follow this one for Edge, you won't be able to use device compliance in your Conditional Access policies :-/
02.08.2025 22:49 — 👍 17 🔁 2 💬 3 📌 0
I ended up writing a post about the new feature to change group SOA from AD to #Entra. Big big thanks to @intune.best for all of the assistance he provided and initial testing he did in #WinAdmins Discord voice yesterday!
ajf.one/group-soa
02.08.2025 17:23 — 👍 4 🔁 1 💬 0 📌 0
The S in MCP stands for security
02.08.2025 05:29 — 👍 517 🔁 92 💬 18 📌 6
Don’t blindly follow benchmarks.
They’re a great starting point — but not the finish line. Always make sure you understand what you’re configuring and why it matters in your specific environment.
02.08.2025 04:59 — 👍 10 🔁 2 💬 0 📌 0
I don't remember if it went that far back or not, but I know we had them in v2 (though there was no native way to convert them back to plain text back then, only via .NET)
02.08.2025 04:05 — 👍 1 🔁 0 💬 1 📌 0
I don't think this is really a factor, just dangerous imo
Lots of reasons, outside of not great defaults, most are total nonsense
Many just hate Microsoft, which is fine, but most don't configure it well, can't let go of AV results from a decade ago, compare to consumer experiences, etc.
02.08.2025 03:21 — 👍 0 🔁 0 💬 0 📌 0
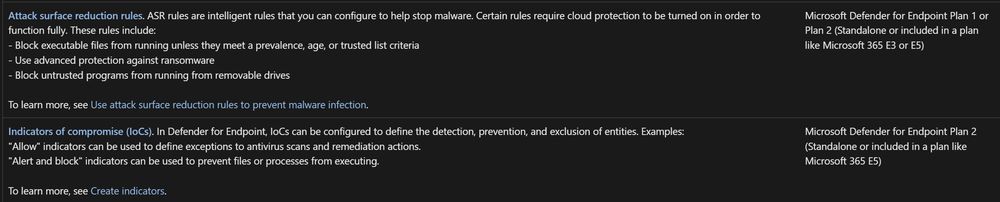
Also fun, CIS says to enable ASR rules (which you absolutely should), but then disabling cloud delivered protection effectively disables 3 of the ASR rules they say you need to enable :P
So in the end, you can't actually get a device configured per the CIS Benchmarks, lol
01.08.2025 20:13 — 👍 3 🔁 0 💬 0 📌 0
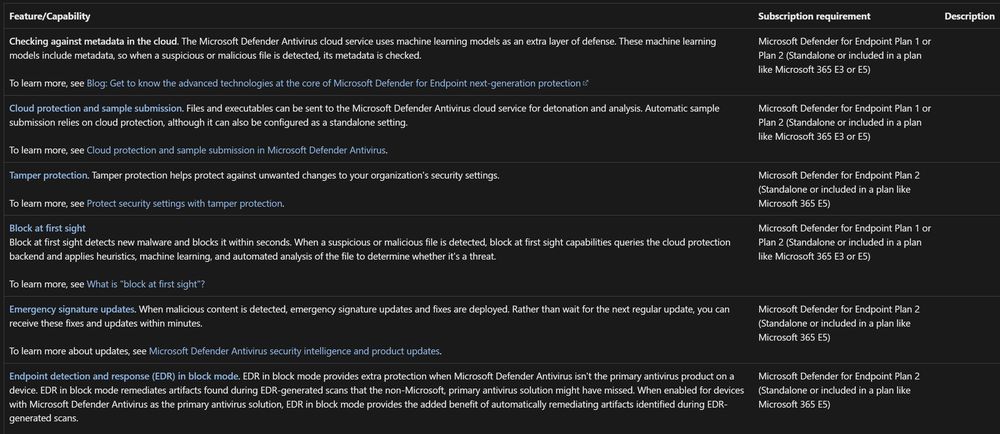
As always, you cannot blindly trust benchmarks, you need to understand products to make the correct decisions for your environment
CIS was notorious for disabling PowerShell logging because it might capture a password... 🤦♂️
Here are just some of the things you will lose:
01.08.2025 20:12 — 👍 2 🔁 0 💬 3 📌 0

If you use CIS Benchmarks, I highly advise against this recommendation...
This disables cloud delivered protection which underpins a bunch of capabilities, disables roughly half of your protection
Fortunately, if you enable Tamper Protection, it is forcefully enabled for you :)
01.08.2025 20:12 — 👍 20 🔁 2 💬 2 📌 1
Euphoria
30.07.2025 22:01 — 👍 0 🔁 0 💬 0 📌 0
YouTube video by Get Rubix
How to Automate Intune Policy Assignments with Graph and PowerShell
Today I'll show you how to add Intune policy assignments using the Microsoft Graph and PowerShell.
youtu.be/PAlSpLl5ASA
#intune #windows #graph
30.07.2025 21:32 — 👍 7 🔁 3 💬 0 📌 0

Poor man’s IGA: Monitor and clean up stale guest accounts
Today’s challenge Today, we are dealing with inactive or stale guest users in a tenant. Entra ID Governance has several ways to solve this, but if you had those licenses, you wouldn’t be here. For tod...
I'd love to know which limited features most are interested in
This is partly why I created my Entra Operational Groups project:
github.com/nathanmcnult...
@janbakker.bsky.social also has a nice series on poor man's IGA:
janbakker.tech/poor-mans-ig...
We can do a lot with a little admin effort :)
28.07.2025 23:28 — 👍 1 🔁 0 💬 0 📌 0
At least they didn't let the security copilot licensing people touch it :p
I quite prefer getting charged for real usage though rather than licensing all active users or something
They'd lose a lot of money if they did this for all licenses, lol. So many licensed accounts not being used.
28.07.2025 20:26 — 👍 2 🔁 0 💬 1 📌 0
nathanmcnulty/Entra/operational-groups/per-user-mfa.ps1 at master · nathanmcnulty/nathanmcnulty
Contribute to nathanmcnulty/nathanmcnulty development by creating an account on GitHub.
This week I discovered we couldn't use my Entra Operational Group to create the per-user MFA groups because GCC doesn't allow Graph PowerShell to get tokens that work with this API endpoint
This technique worked around this limitation, very cool! :)
github.com/nathanmcn...
26.07.2025 03:53 — 👍 5 🔁 0 💬 0 📌 0
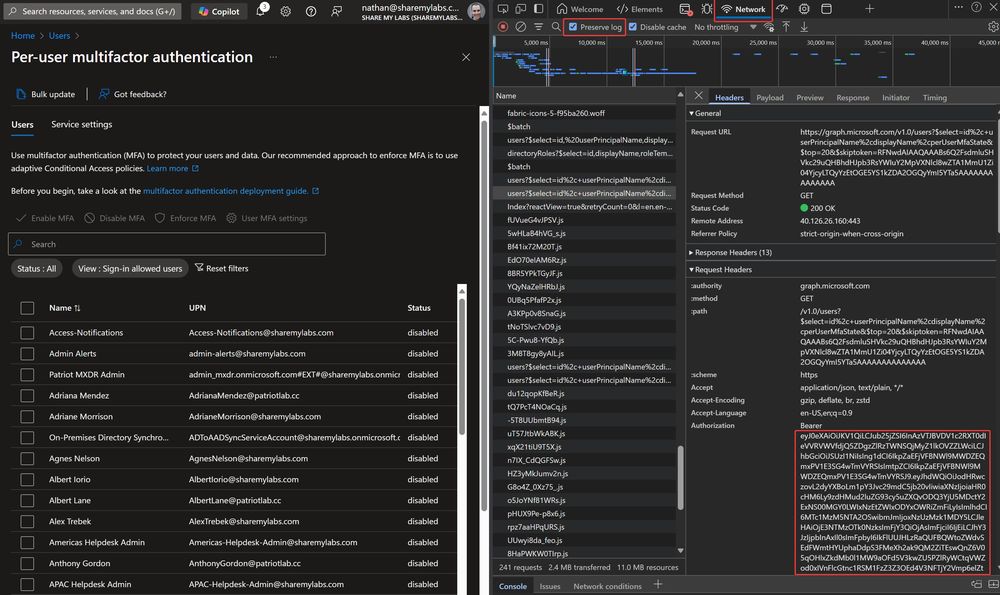
Pro Tip: You can borrow Bearer tokens from your browser in the various Microsoft portals and use them with Graph PowerShell/CLI
This is useful when Graph API endpoints don't allow clients like Graph PowerShell/CLI to make requests, common on new endpoints or in GCC environments
26.07.2025 03:52 — 👍 14 🔁 3 💬 1 📌 0
MDM doesn't matter BTW
The combined mobileconfig and onboarding file could even be combined, but regardless, these are deployed as custom configuration profiles, AV policy can be via Settings Catalog, Endpoint security, Jamf schema, etc., and app via Intune or PKG from portal :)
25.07.2025 01:53 — 👍 1 🔁 0 💬 0 📌 0

Intune-based deployment for Microsoft Defender for Endpoint on macOS - Microsoft Defender for Endpoint
Install Microsoft Defender for Endpoint on macOS, using Microsoft Intune.
Reminder when deploying Defender for Endpoint for macOS
You *could* do this the hard way:
learn.microsoft.com/...
Or you can do it the easy way:
github.com/microsoft...
You really just need 4 policies:
1) Permissions (combined)
2) Onboarding
3) AV policy
4) App installation
25.07.2025 01:53 — 👍 11 🔁 2 💬 1 📌 0
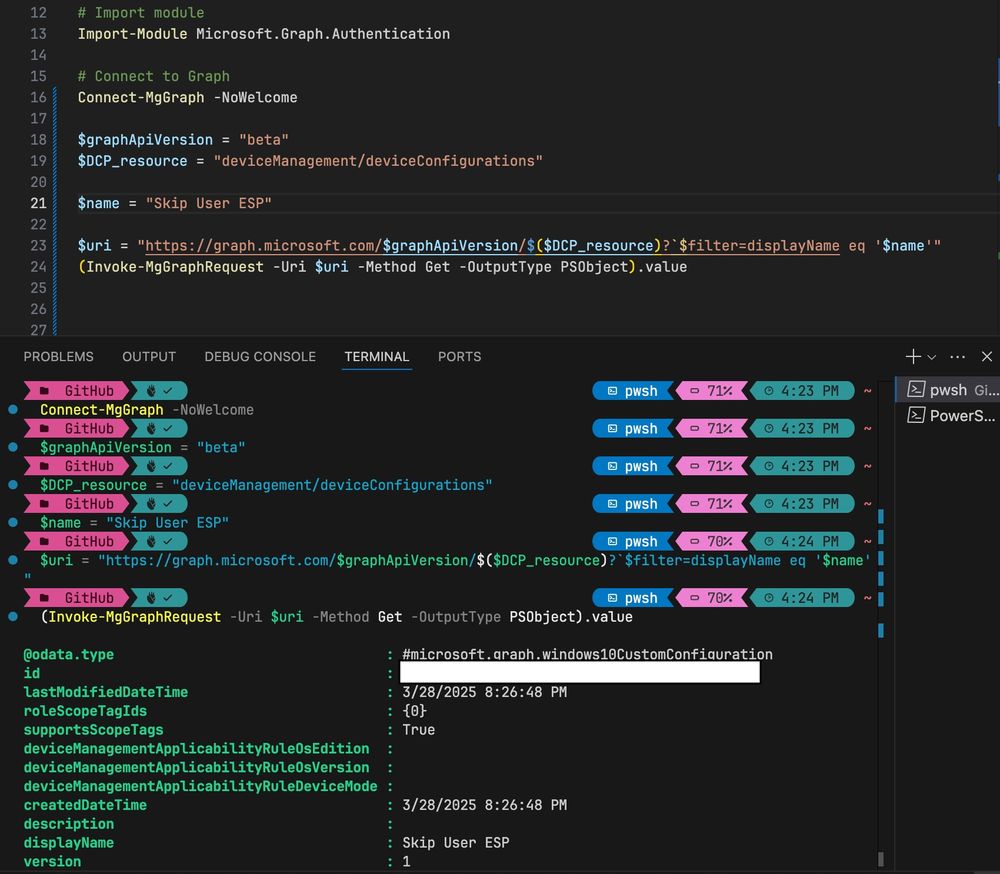
Seeing a lot of folks frustrated with the Microsoft.Graph #PowerShell SDK...missing modules, bloat, weird errors.
If you just need to hit a few endpoints without the overhead:
Install-Module Microsoft.Graph.Authentication
Connect-MgGraph
Invoke-MgGraphRequest
#MSGraph #Intune
24.07.2025 23:49 — 👍 11 🔁 2 💬 3 📌 1
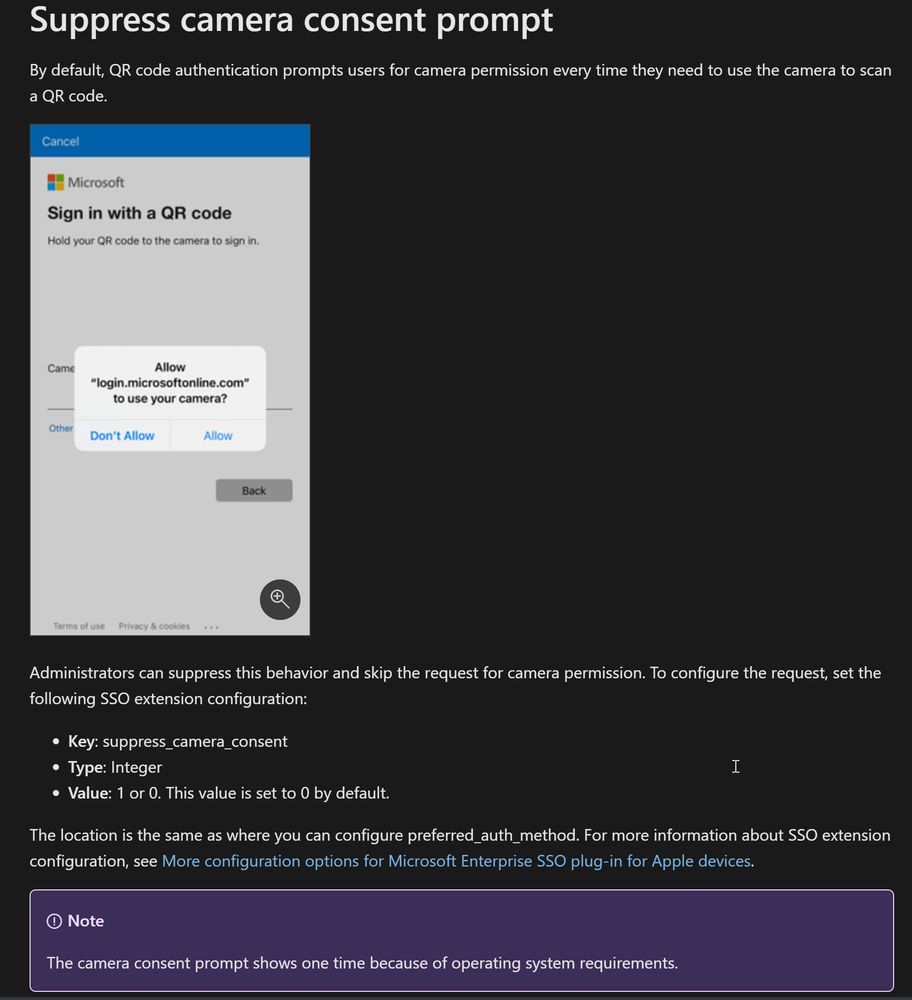
Looks like the Entra QR code authentication method is going GA 🥳
They've also added some great guidance on suppressing the camera permission prompt for iOS :)
learn.microsoft.com/...
24.07.2025 23:30 — 👍 3 🔁 1 💬 0 📌 0
It all depends on the use case, imo
If you are really using it for lifecycle workflows and lots of entitlement management capabilities (especially custom extensions), then it might be worth it
To just do a few actions, quite expensive imo
24.07.2025 05:59 — 👍 1 🔁 0 💬 2 📌 0
At the speed of cloud!
(2x slower than a typical 486)
24.07.2025 00:51 — 👍 2 🔁 0 💬 1 📌 0
For very large orgs, I left a comment on line 16 where we might have to use loggedByService due to too many records. I'm testing now.
Final note - I can't find this option anywhere in Entra, and I feel like I'm pretty good at navigating the portal :p
learn.microsoft.com/en-us/entra/...
23.07.2025 23:57 — 👍 2 🔁 0 💬 0 📌 0
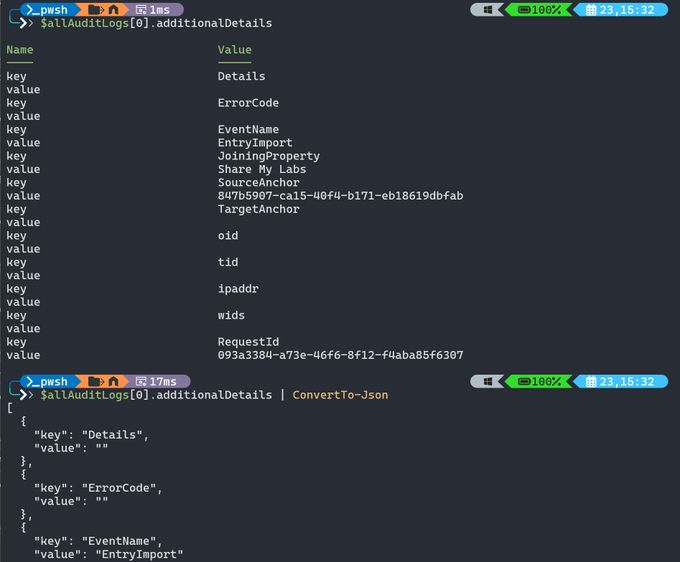
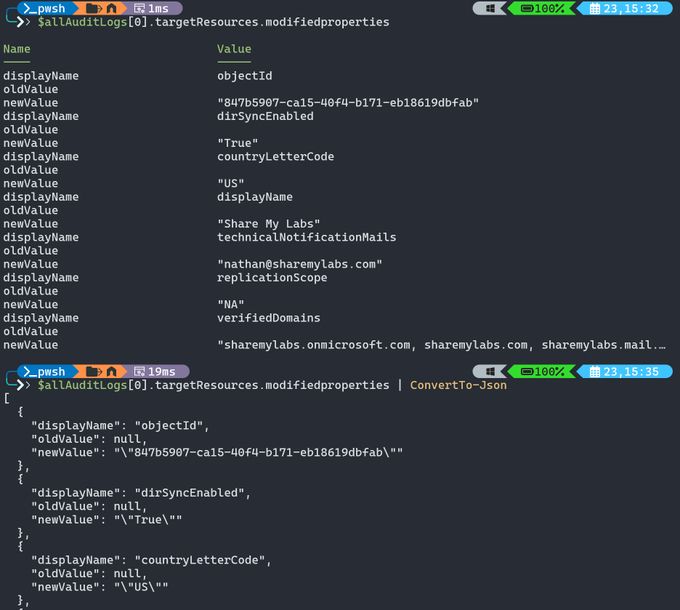
So now I'm stuck pulling ALL audit logs back and post processing, which brings me to my next "what the heck?" moment
This is no ordinary hashtable, they murdered this thing. It's arrays with unrelated key/value pairs inside of it, plus escaped quotes...
What a pain to work with
23.07.2025 23:56 — 👍 0 🔁 0 💬 1 📌 0
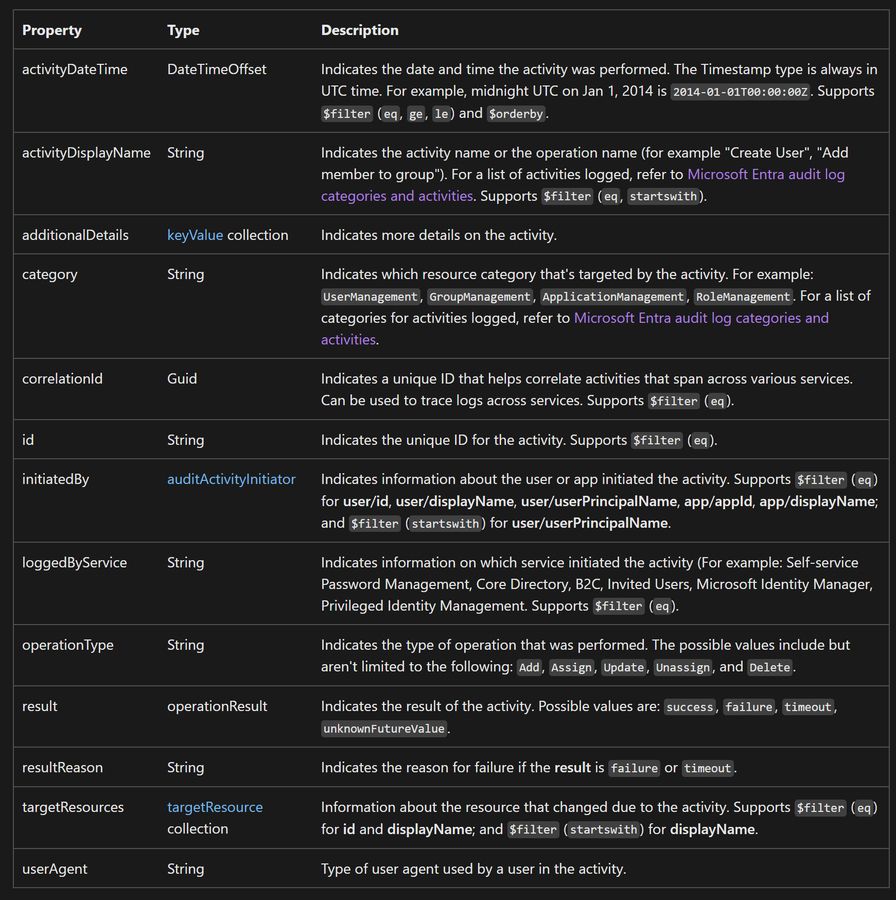
Many orgs have massive audit logs, so pulling them all back is not the best way to do this, except...
We can't actually filter on the things you want to for this, and the docs aren't clear which loggedByService corresponds to which API calls :-/
learn.microsoft.com/en-us/graph/...
23.07.2025 23:56 — 👍 0 🔁 0 💬 1 📌 0
My whining thread :p
I couldn't find any reports, queries, etc., to help us assess impact :(
The responsibilty to discover licensing costs was left to the customer with sparse instructions to go figure it out...
"Just look at your audit logs!"
learn.microsoft.com/en-us/entra/...
23.07.2025 23:55 — 👍 1 🔁 1 💬 1 📌 0
Principal Architect, Identity and Access Management @ McDonald’s. Opinions are mine. #Azure #Security #Identity #TheDiscords #Acappella #Words5X he/him
Cybersecurity geek. Into Legos and adding games to my steam library I’ll never play. Posts are my own.
📍CLE | Networking | Security | Cloud | Open Source | Automation
Find out about newly awarded MVPs
Created by https://bsky.app/profile/schenardie.bsky.social
Tickets available for Workplace Ninjas UK 2025 at https://wpninjas.uk
Empowering IT pros in endpoint management, Microsoft 365, security, and automation. Join us in Edinburgh for insights, networking, and the latest in tech!
Just a guy trying his best.
Mastodon @deepthoughts10@infosec.exchange
#InfoSec #Cybersecurity #ThreatIntel and #USPol (US Politics)
Husband to my amazing wife, father to 1 human and 3 cats, Yooper, and aspiring Information Security semi-professional.
Having fun with Apple Shortcuts and AT Protocol lately.
My bot is @h0ff3r-bot.bsky.social
Entra PowerShell, Microsoft Graph PowerShell
Cloud Solution Architect - Security @ Microsoft
Forever kind, curious and interested.
Aussie, Dad, Gourmand
International Public Speaker
My opinions are my own
Security Researcher, Award Winning Speaker, Writer, Board Menber #DianaInitiative #BSidesLV #DefCon #tattoo Opinions/mine
Chief Research Officer and Co-Founder @ Airlock Digital. Practical Execution Control & Allowlisting.
The dev who defends using defender | Cybersecurity Automation Architect at SCC | Microsoft Security Advocate
https://www.linkedin.com/in/jay-kerai-cyber/ // https://github.com/jkerai1
Jack of all Trades, Master of PowerShell.
Prolific Programmer
Microsoft MVP in Azure / PowerShell
https://mrpowershell.com/
https://github.com/StartAutomating
https://github.com/PowerShellWeb
NB, Neurodivergent, Nerdy, Newsjunkie.
Ask me anything.
Endpoint and Identity Security Human at Microsoft. All views are my own.
(bre|m)aking clouds, Windows, and fancy keyboards. R&D devicie.com, organiser pecanplus.ecusdf.org, OSS github.com/pl4nty
Velociraptor@Rapid7. #DFIR, #CTI and research.
https://mgreen27.github.io
Cybersecurity consultant, Microsoft Security Expert🇨🇦
Was a threat guy at @Microsoft. Now retired. Loves Calvin and Hobbes. Any opinions are likely to be mine ...
 06.08.2025 01:49 — 👍 0 🔁 0 💬 0 📌 0
06.08.2025 01:49 — 👍 0 🔁 0 💬 0 📌 0















