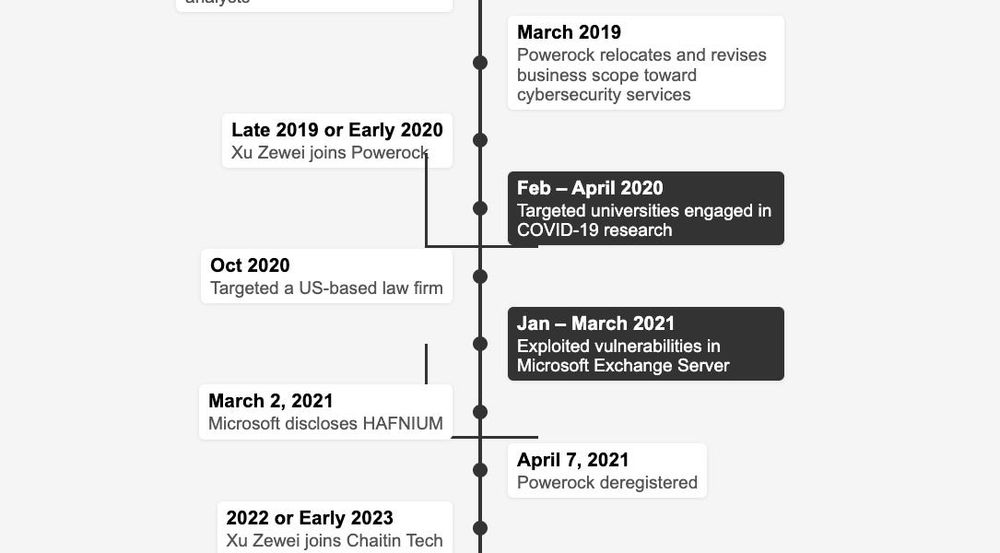
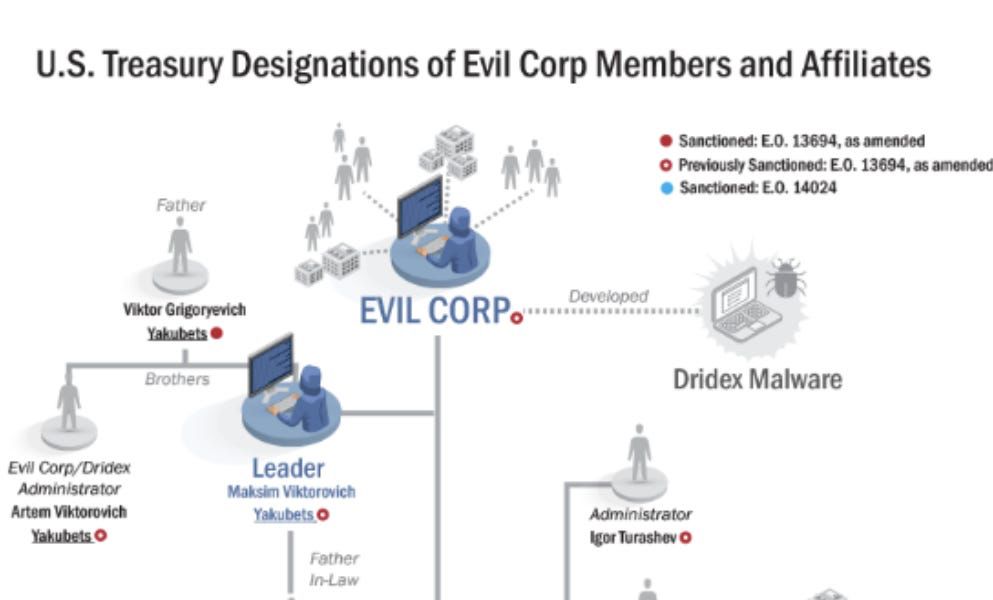
Microsoft is probing whether a MAPP leak let Chinese hackers exploit a SharePoint vuln pre-patch.
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose
31.07.2025 16:44 — 👍 11 🔁 4 💬 1 📌 0
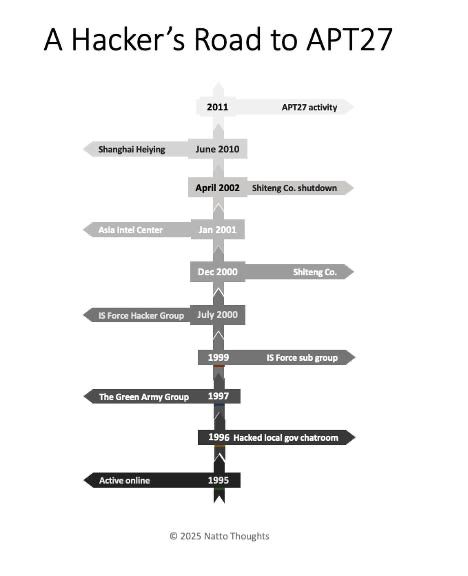
1/ China’s cyber capabilities didn’t start top-down, they started with raw hacking talent. The new CSS/ETH report "Before Vegas" traces how informal talent shaped China’s cyber ecosystem, moving from online forums to industry leaders (link in thread).
21.07.2025 08:11 — 👍 14 🔁 8 💬 1 📌 0
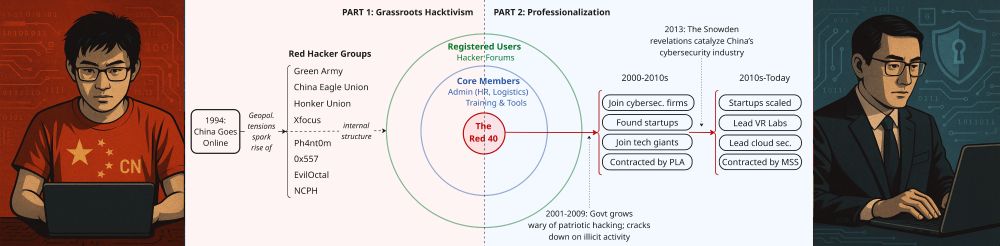
We often questioned how they achieved their current status regarding China developing its cyber offensive capabilities. The Natto Team appreciates @euben.bsky.social for investigating the origin of the defense-through-offense approach.
11.06.2025 16:53 — 👍 2 🔁 2 💬 0 📌 0

From Humble Beginnings: How a Vocational College Became a Vulnerability Powerhouse
Qingyuan Polytechnic's focus on vulnerability studies highlights China's continued efforts in gathering vulnerability resources
The Natto Team explores the development of China's vulnerability research and discovery skills, starting from the vocational college level.
Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...
28.05.2025 16:46 — 👍 11 🔁 7 💬 0 📌 1

Where is i-SOON Now?
i-SOON’s business struggles after the leak reflect the cruel reality of China’s hacker-for-hire industry
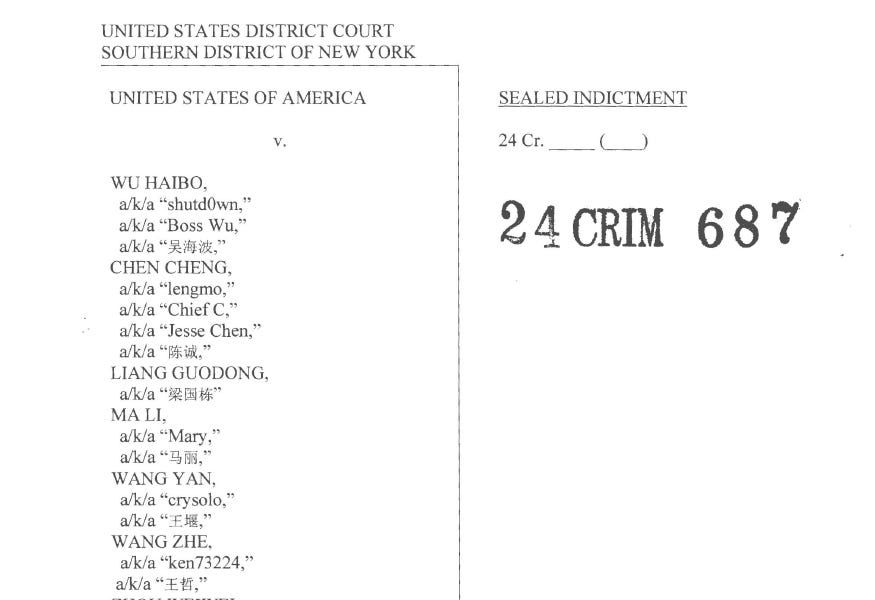
As the Natto Team was going to publish this piece, US Department of Justice unsealed an indictment charging eight i-SOON employees and highlighting the importance of companies like i-SOON in China's cyberthreat landscape.
nattothoughts.substack.com/p/where-is-i...
05.03.2025 17:32 — 👍 4 🔁 3 💬 0 📌 0
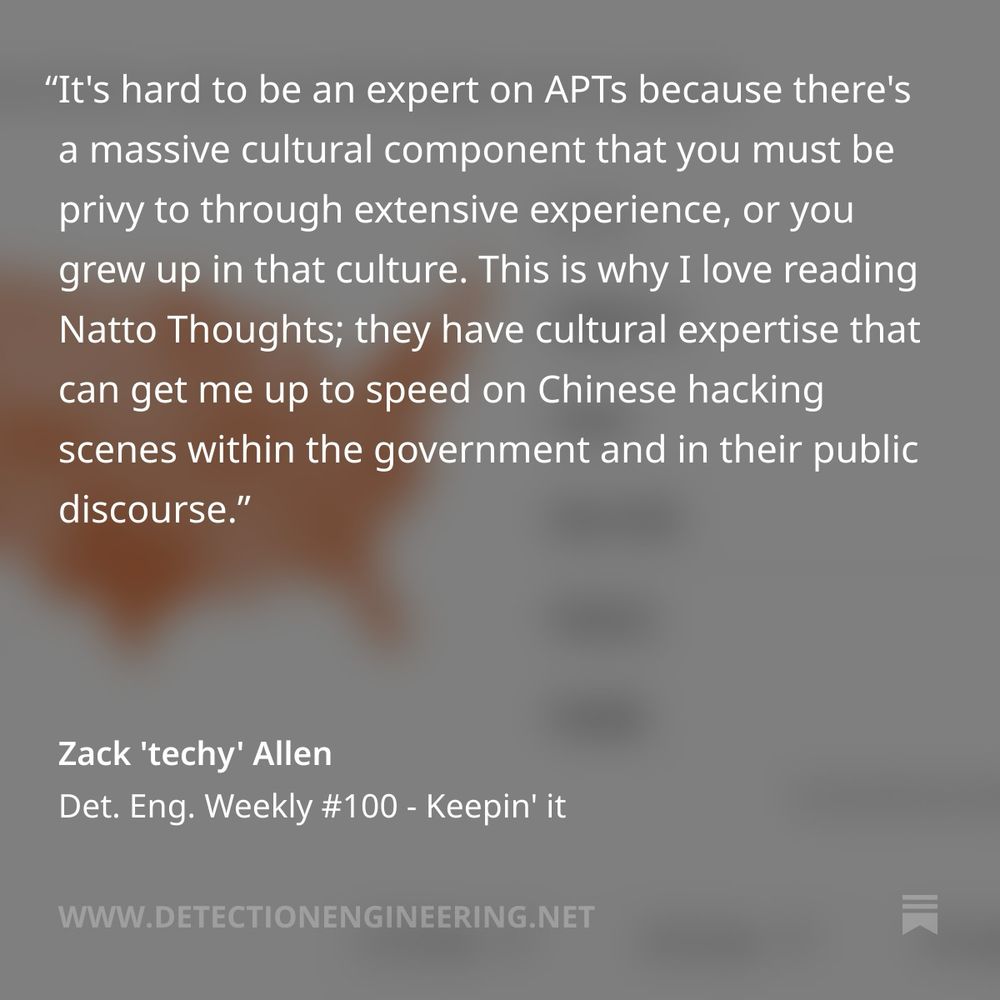
We appreciate that more and more threat intelligence researchers value the importance of cultural component in APT research. @techy.detectionengineering.net
28.02.2025 03:05 — 👍 6 🔁 2 💬 0 📌 0

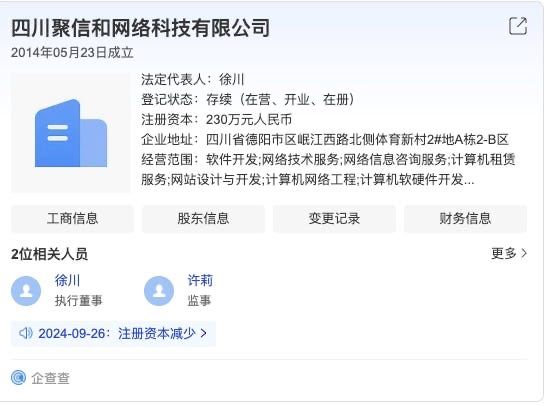
Chasing Chengdu404, Sichuan Silence....and NoSugar Technology !?
On the ground research on US sanctioned cyber security companies in China.
We are glad to see that some curious minds like us want to find out more about Chinese APTs associated companies in reality. They actually paid a visit to them.
substack.com/home/post/p-...
18.02.2025 17:58 — 👍 3 🔁 2 💬 0 📌 0

1000 subscribers. You did it. Natto Thoughts has its first thousand subscribers. Nattothoughts.substack.com
Thank you for your support. The Natto Team appreciates it.
17.12.2024 15:31 — 👍 7 🔁 2 💬 0 📌 2
Threat Research @ Recorded Future. Previously @ Security Research Labs. He/Him. 🏳️🌈
Threat Intel / CTI / OT / ICS / Critical Infra stuff along with other things. I genuinely care, and wish others did too.
Website: pylos.co
Training/Consulting: paralus.co
☆ Cybersecurity reporter
★ Newsletters at Risky Business
#infosec #cybersecurity
https://risky.biz
China-Focused Consultant @SentinelOne | Nonresident Fellow @ACGlobalChina | Adjunct @Georgetown | Unprofessional Cook | ❤️💜💙
https://linktr.ee/dakotaindc
Cyber Defense Researcher @ethz.ch. Former Italian govt, Pacific Forum and NYPD. LUISS & Columbia University Alum.
Creator of Detection Engineering Weekly (https://detectionengineering.net), Sec Research/Intel/Detection @ Datadog
Threat intel @ Intel 471 (@intel471.bsky.social). Personal account. Interests: Cybercrime, cyber threat intelligence, OSINT, data breaches, photography. Also produce Intel 471's "Cybercrime Exposed" podcast. #Australia
Security researcher @ Cisco Talos. / Ex-Google TAG / Black Hat & HITCON review board / Organiser of Rhacklette.
official Bluesky account (check username👆)
Bugs, feature requests, feedback: support@bsky.app