
We continue exploring provincial level’s involvement in cyber operations. See details in analysis by @euben.bsky.social
www.nattothoughts.com/p/provincial...
@euben.bsky.social
Cyber Defense Researcher @ethz.ch. Former Italian govt, Pacific Forum and NYPD. LUISS & Columbia University Alum.

We continue exploring provincial level’s involvement in cyber operations. See details in analysis by @euben.bsky.social
www.nattothoughts.com/p/provincial...

In this post, @euben.bsky.social and the Natto Team assess that provincial bureaus of the Chinese Ministry of State Security likely operate with their own tasking priorities, resources, and local ecosystems for cyber operations.
nattothoughts.substack.com/p/the-many-a...

@euben.bsky.social Eugenio’s research explains the elite cyber talent paradox in China - “all people are soldiers” vs “extremely lean.”
#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...
Can’t wait for this :)
01.08.2025 09:25 — 👍 2 🔁 0 💬 0 📌 0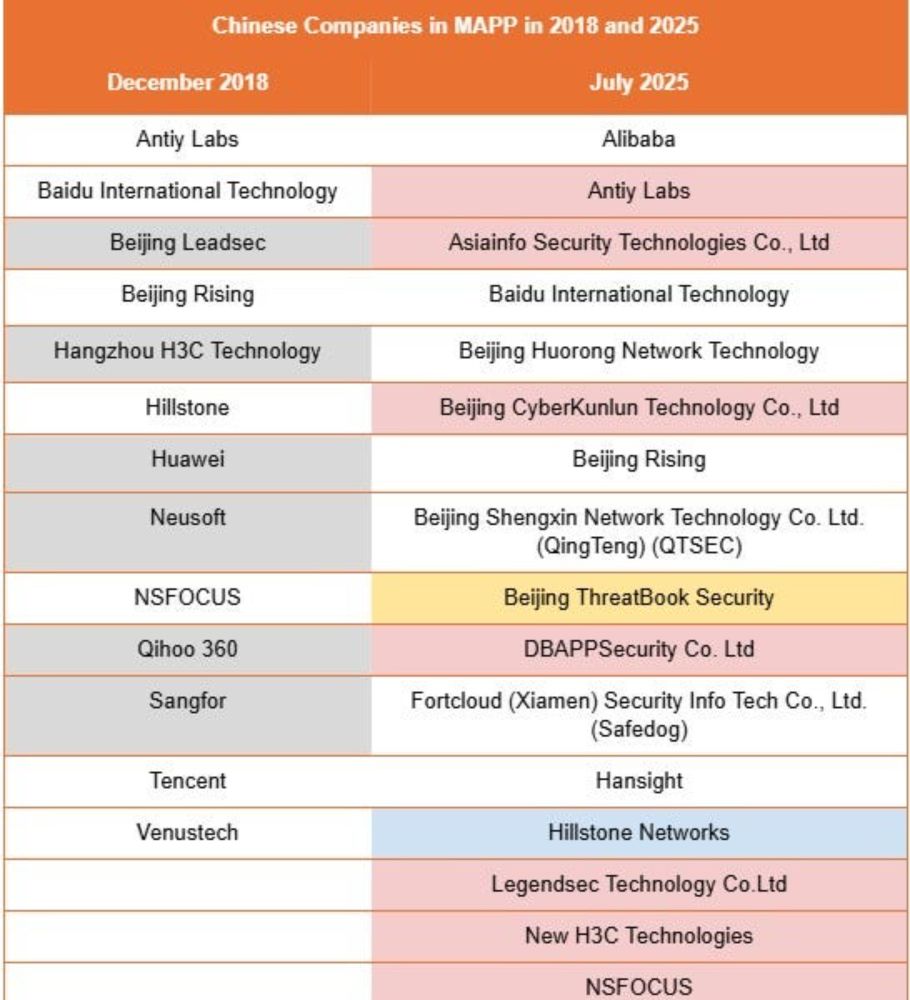
Available here: nattothoughts.substack.com/p/when-privi...
31.07.2025 16:44 — 👍 1 🔁 0 💬 0 📌 0
Microsoft is probing whether a MAPP leak let Chinese hackers exploit a SharePoint vuln pre-patch.
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose

New: Microsoft is investigating whether a leak from its early alert system for cybersecurity companies allowed Chinese hackers to exploit flaws in SharePoint before they were patched, enabling a global campaign of cyberattacks, according to people familiar: www.bloomberg.com/news/article...
25.07.2025 18:34 — 👍 9 🔁 8 💬 1 📌 0
In the latest Hooked!, editor @katharinegk.bsky.social ties together some fascinating recent research from @benread.bsky.social , @euben.bsky.social, @winnona.bsky.social, and others on private sector elements of Chinese offensive cyber: bindinghook.com/articles-hoo...
25.07.2025 08:31 — 👍 6 🔁 2 💬 0 📌 0Before Vegas – The “Red Hackers” Who Shaped China’s Cyber Ecosystem (Center for Security Studies at ETH Zürich): css.ethz.ch/content/dam/...
21.07.2025 11:39 — 👍 1 🔁 1 💬 0 📌 06/ Sincerely grateful to the all-star team of experts who shared their insights and feedback: Scott Henderson (Google Mandiant), Adam Kozy (SinaCyber), @meidanowski.bsky.social (@nattothoughts.bsky.social), @thegrugq.bsky.social, @Chris St.Myers (SentinelOne), & Charles Li and Zha0 (TeamT5)
21.07.2025 08:11 — 👍 3 🔁 0 💬 0 📌 05/ The key lesson: what begins in anonymous forums can end in boardrooms and on digital battlefields. Overlooking civilian hacking talent is a strategic risk.
21.07.2025 08:11 — 👍 2 🔁 2 💬 1 📌 0
@kimzetter.bsky.social's excellent piece for Wired unpacks the state-linked side of the story, covering the report and Adam Kozy’s research: www.wired.com/story/china-...
21.07.2025 08:11 — 👍 1 🔁 0 💬 1 📌 0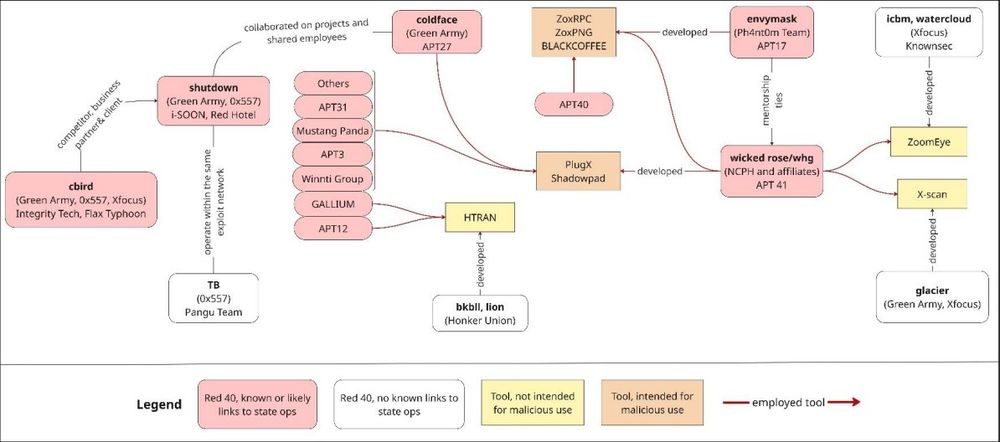
3/ Some Red 40 hackers have carried out operations on behalf of China’s military and intelligence services. Their informal networks, formed during their teens or twenties as members of the same hacking groups, exemplify tool sharing and collab that underpins China’s APTs MO.
21.07.2025 08:11 — 👍 1 🔁 0 💬 1 📌 02/ It identifies 40 prominent red hackers — “The Red 40” — who shaped China’s cyber ecosystem from the ground up. It tells the story of how these individuals transitioned from online forums to becoming part of a tightly integrated ecosystem.
Full report:
css.ethz.ch/en/center/CS...
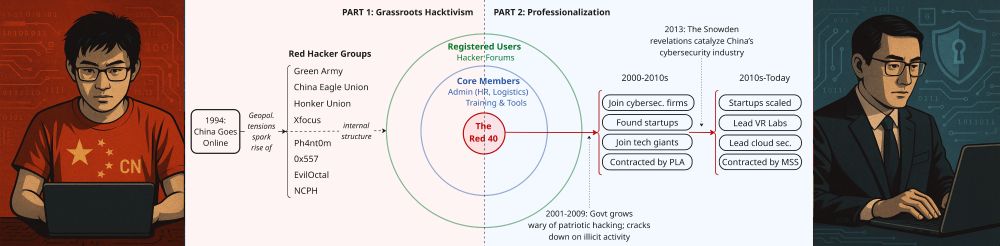
1/ China’s cyber capabilities didn’t start top-down, they started with raw hacking talent. The new CSS/ETH report "Before Vegas" traces how informal talent shaped China’s cyber ecosystem, moving from online forums to industry leaders (link in thread).
21.07.2025 08:11 — 👍 15 🔁 8 💬 1 📌 0haha haven't spent too much time around here
20.07.2025 21:06 — 👍 0 🔁 0 💬 0 📌 0Thank you 🙏 really appreciate it!
20.07.2025 21:05 — 👍 0 🔁 0 💬 0 📌 0Thank you! I’d definitely add Alex Josie’s “Spies and Lies” to the book list
20.07.2025 13:07 — 👍 4 🔁 0 💬 2 📌 0Thank you! Looking forward to hearing your thoughts on it
19.07.2025 02:03 — 👍 2 🔁 0 💬 0 📌 0Fully agree, Patrick. I also love his work. He was very kind to review the report and provide feedback before publication 😊
19.07.2025 01:51 — 👍 0 🔁 0 💬 0 📌 0
How did China's top APT hackers come to be? Many were early "Honkers" - patriotic hackers who in late 90s launched low-skill cyberattacks against nations deemed disrespectful to China. But once Honkers developed their skills, PLA/MSS came calling. Based on great research by bsky.app/profile/eube...
18.07.2025 15:48 — 👍 58 🔁 30 💬 0 📌 0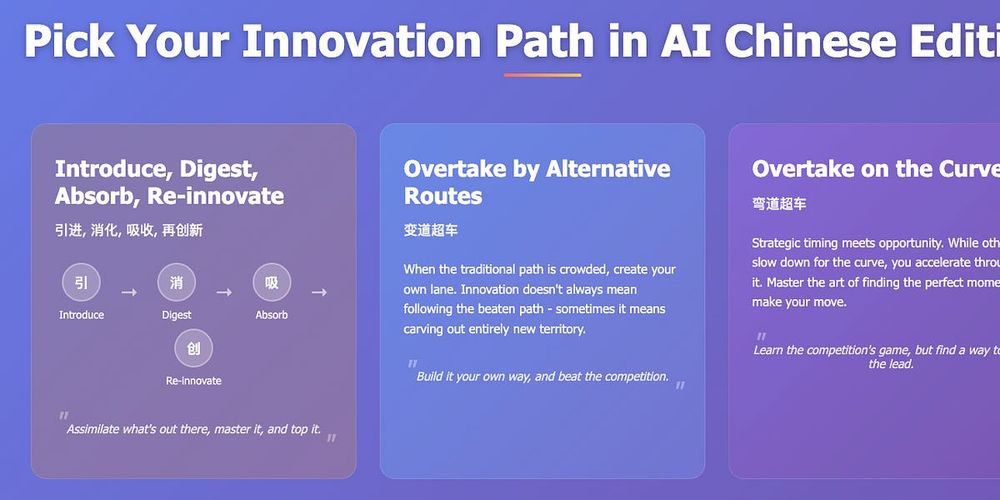
How has China advanced its AI development to its current state? No single innovation path in AI can be considered definitive.
nattothoughts.substack.com/p/debating-c...
I wrote on the arrest in Italy of Xu Zewei, an alleged Chinese hacker, perhaps the first case where America has sought to extradite a Chinese hacker for mainly or exclusively cyber operations—in this case theft of Covid research during the pandemic. www.economist.com/china/2025/0...
11.07.2025 06:27 — 👍 71 🔁 12 💬 0 📌 0
“alignment with CCP priorities offers privileged access to state resources, regulatory favor, and expanded commercial opportunities [to hackers]."
NEW Phenomenal report on Chinese civil military fusion and cyber militias by Kieran Green: margin.re/mobilizing-c...
🚨 NEW PAPER on the 0day Supply Chain 🚨:
I gathered open source data & interviewed Gov employees, VR and china researchers to figure out what the zero day marketplace looks like in the U.S. and how it compares to China.
key findings below ⬇️- 0/🧵
www.atlanticcouncil.org/in-depth-res...
I think European countries are struggling even to allow government teams to do this kind of work, so extending it to broader private sector involvement seems unlikely to me as things stand
13.06.2025 20:13 — 👍 1 🔁 0 💬 1 📌 0I agree they should rethink current approaches, starting from talent development.
13.06.2025 12:14 — 👍 1 🔁 0 💬 1 📌 0
To defend, one must first know how to attack” (未知攻,焉知防). This mindset, popularized by a Taiwanese hacker Lin in the 1990s, spread from China's red hackers to CTF teams. Today, it powers China's cyber industry.
New piece for @nattothoughts.bsky.social
nattothoughts.substack.com/p/defense-th...

The Natto Team explores the development of China's vulnerability research and discovery skills, starting from the vocational college level.
Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...