I arbitrarily picked a list of 50 talks I'm most excited about that are happening next week at DEF CON / Black Hat / BSides LV / The Diana Initiative.
I'll also add recordings/slides to this list when they become available!
29.07.2025 20:17 — 👍 2 🔁 2 💬 0 📌 0
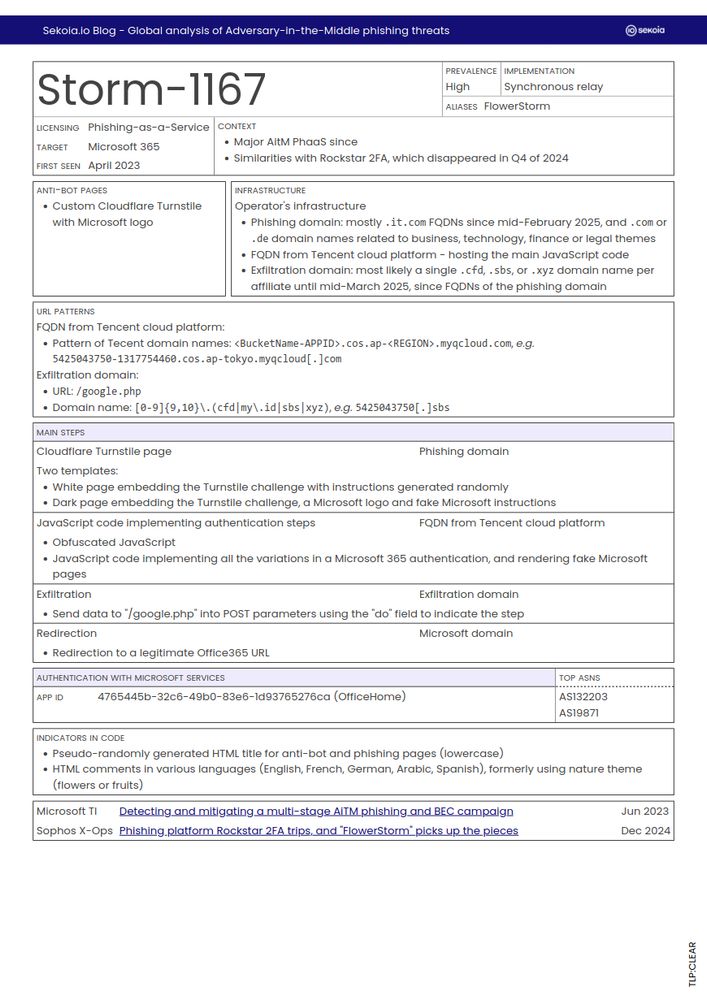
These sheets aim to assist SOC analysts in detecting and investigating #AitM #phishing compromises by offering context, technical details, infrastructure overview, detection opportunities, and more.
All are available in the PDF report and our Community GitHub.
08.07.2025 07:53 — 👍 1 🔁 2 💬 1 📌 0
In April 2025, we received leaked information about Google taking steps to strip down the Android Open Source Project. We were told the first step would be removal of device support with the launch of Android 16. We didn't get details or confirmation so we didn't prepare early.
12.06.2025 15:06 — 👍 48 🔁 5 💬 2 📌 1
This is one heck of a thread. Everyone should read it.
17.03.2025 18:41 — 👍 11 🔁 2 💬 0 📌 0
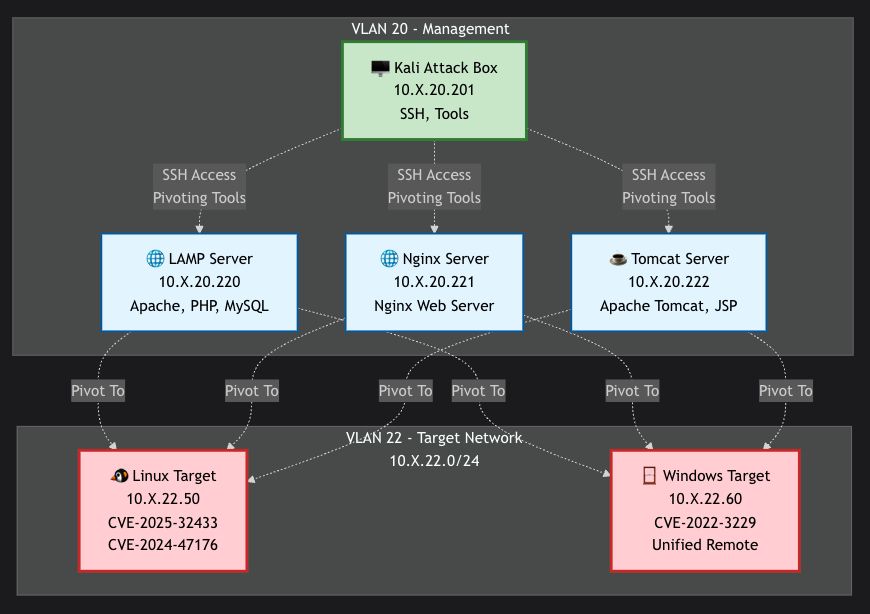
Want to learn pivoting this weekend? The 🏟️Ludus community created a Pivot Lab with 11 different pivoting tools! Check it out: docs.ludus.cloud/docs/environ...
06.06.2025 20:32 — 👍 4 🔁 2 💬 0 📌 0

Defenders have platforms like VirusTotal, but offense lacks a similarly tailored tool. Enter: Nemesis 2.0.
Join @tifkin.bsky.social & @harmj0y.bsky.social at #x33fcon as they showcase the offensive file analysis platform that replaces disjointed tools w/ streamlined automation. ghst.ly/x33fcon25
22.05.2025 13:52 — 👍 2 🔁 1 💬 0 📌 0
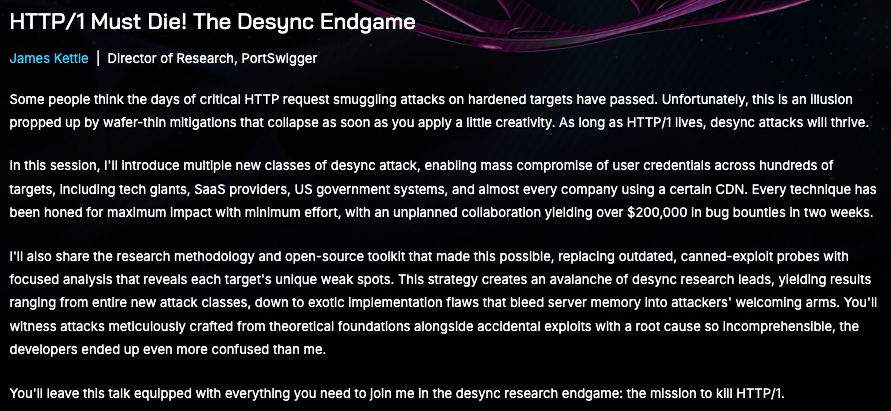
I'm thrilled to announce "HTTP/1 Must Die! The Desync Endgame", at #BHUSA! This is going to be epic, check out the abstract for a teaser ↓
14.05.2025 13:31 — 👍 39 🔁 18 💬 2 📌 1
YouTube video by Underscore_
Le hacker “éthique” qui a berné tous les médias français (Florent Curtet)
Florent curtet le hacker "éthique" qui a berné tous les médias français
youtube.com/watch?v=mjxY...
12.05.2025 14:35 — 👍 6 🔁 5 💬 0 📌 0

Out of Band Update: Cobalt Strike 4.11.1 | Cobalt Strike
4.11.1 fixes a module stomping issue. Additionally, an "enable SSL" checkbox and deprecation warning for stomp loader have been added.
Cobalt Strike 4.11.1 is live--this out of band release addresses and issue with module stomping. Additionally, an "enable SSL" checkbox and deprecation warning for stomp loader have been added. Get more details in the blog:
www.cobaltstrike.com/blog/out-of-...
12.05.2025 19:10 — 👍 0 🔁 2 💬 0 📌 0

🧵 THREAD: A federal whistleblower just dropped one of the most disturbing cybersecurity disclosures I’ve ever read.
He's saying DOGE came in, data went out, and Russians started attempting logins with new valid DOGE passwords
Media's coverage wasn't detailed enough so I dug into his testimony:
18.04.2025 00:10 — 👍 14173 🔁 7490 💬 334 📌 1032
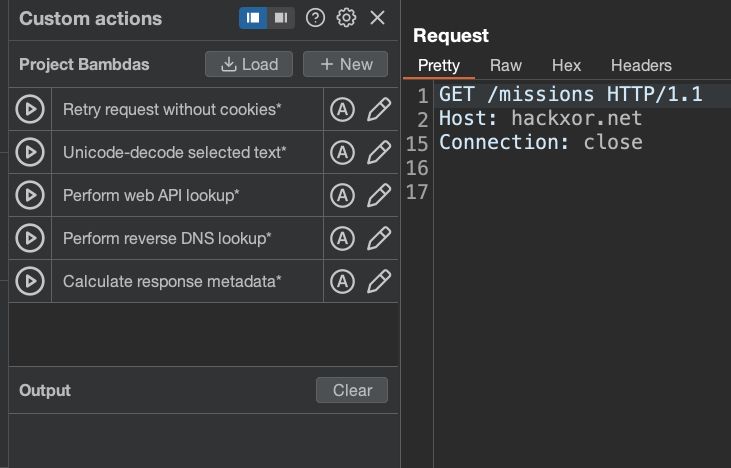
Are you a Burp Repeater power user? The latest release introduces a new feature called 'Custom actions'. With these you can quickly build your own repeater features. Here's a few samples I made for you:
17.04.2025 12:48 — 👍 27 🔁 6 💬 4 📌 1
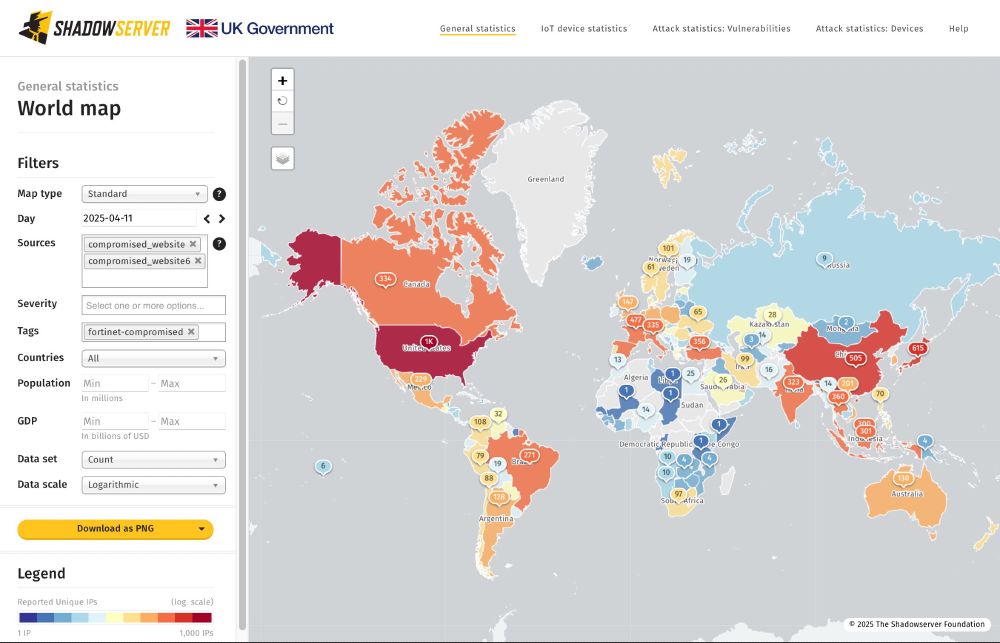
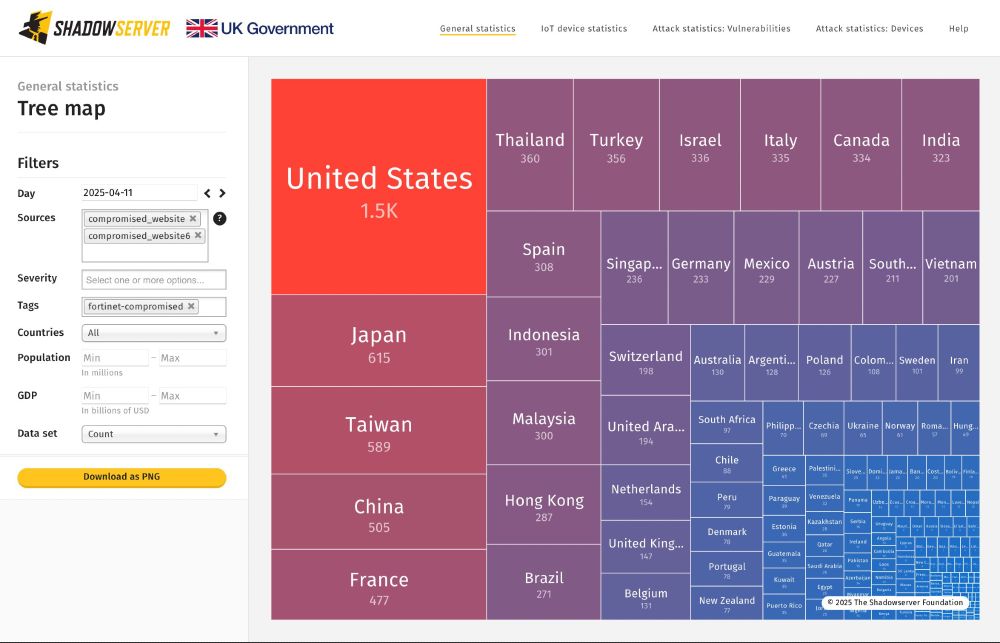
Attention!
Check your Compromised Website Report for critical events tagged “fortinet-compromised” and follow Fortinet's mitigation advice on compromised devices:
fortinet.com/blog/psirt-b...
Data available from 2025-04-11+
shadowserver.org/what-we-do/n...
12.04.2025 12:15 — 👍 14 🔁 10 💬 3 📌 1
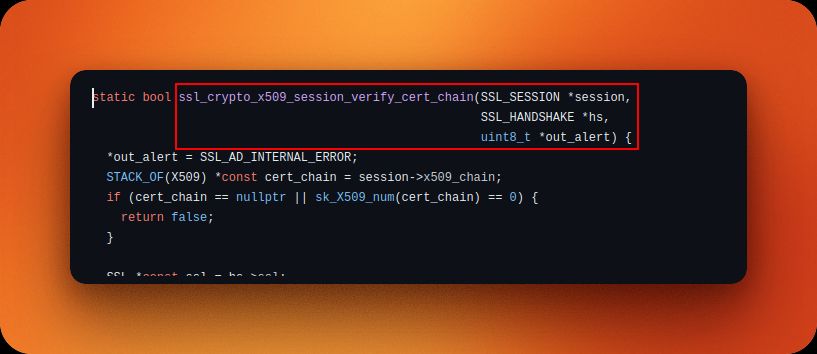
A screenshot of code from BoringSSL's certificate validation function.
Unsatisfied with merely relying on reFlutter to do its magic, Jacques dove deep to understand how Flutter's SSL pinning in Android works, and how to intercept it with Frida.
sensepost.com/blog/2025/in...
17.04.2025 12:15 — 👍 3 🔁 3 💬 0 📌 0
Je ne sais pas trop comment en parler tellement c'est insignifiant par rapport à ce que d'autres vivent .
Ces derniers jours j'étais à Odessa, Ukraine, une ville romantique de bord de mer.
17.04.2025 12:46 — 👍 774 🔁 453 💬 21 📌 59
Mastering Mythic doesn't have to be complicated. 😵💫
Check out our operator-focused video series w/ @its-a-feature.bsky.social, which cuts through the noise & delivers exactly what you need to customize & leverage Mythic effectively.
👀: ghst.ly/mythic-op
15.04.2025 20:10 — 👍 6 🔁 2 💬 1 📌 1

BREAKING.
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.
15.04.2025 17:23 — 👍 695 🔁 420 💬 38 📌 207
Another undercover FBI investigation related to cryptocurrency 💰
10.04.2025 14:06 — 👍 0 🔁 1 💬 0 📌 0

ICYMI: We recently introduced NTLM relay edges into BloodHound.
Elad Shamir unpacks everything you need to know about NTLM & how the new edges help make identifying and visualizing these attack paths remarkably simple. ghst.ly/4lv3E31
10.04.2025 16:27 — 👍 5 🔁 3 💬 0 📌 0
Post-ex Weaponization: An Oral History
aff-wg.org/2025/04/10/p...
A walk-through of some history on post-ex eco-systems used by CS (PowerShell, Reflective DLLs, .NET, and BOFs).
Ends with a coffee conversation talking about magician's guilds, security research, and ideas about what's next.
10.04.2025 14:24 — 👍 11 🔁 7 💬 0 📌 2

Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
08.04.2025 23:00 — 👍 27 🔁 20 💬 1 📌 2
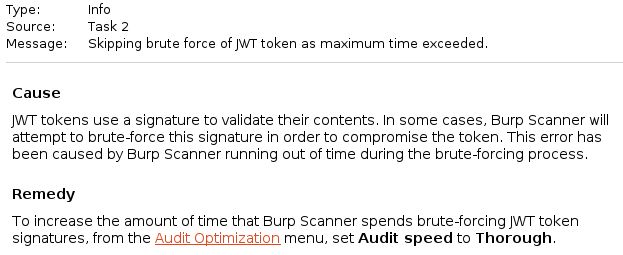
The event "Skipping brute force of JWT token as maximum time exceeded" appears in Burp Suite event logger.
Cuase: WT tokens use a signature to validate their contents. In some cases, Burp Scanner will attempt to brute-force this signature in order to compromise the token. This error has been caused by Burp Scanner running out of time during the brute-forcing process.
Remedy: To increase the amount of time that Burp Scanner spends brute-forcing JWT token signatures, from the Audit Optimization menu, set Audit speed to Thorough.
I strongly recommend to use "Audit speed = Thorough" when scanning. Here's one of the reasons...
08.04.2025 11:26 — 👍 2 🔁 2 💬 0 📌 0
Just submitted to the CFP! I'm super happy with how the research played out this year, literally got too much quality technical content for the 45-minute timeslot
08.04.2025 08:31 — 👍 8 🔁 1 💬 0 📌 0
Suspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability (CVE-2025-22457) | Google Cloud Blog
Hot off the press is a new blog detailing our observations from in the wild exploitation of CVE-2025-22457 by UNC5221 including two newly observed malware families tracked as BRUSHFIRE and TRAILBLAZE.
cloud.google.com/blog/topics/...
03.04.2025 16:26 — 👍 14 🔁 7 💬 0 📌 5
Not leaking any teasers, other than to say that @albinowax.bsky.social’s research for Black Hat USA is absolutely world class, probably his most impactful yet. Prepare to hear a LOT of talk about this in August.
03.04.2025 12:18 — 👍 10 🔁 2 💬 0 📌 0

Le guide de l'homologation de sécurité des systèmes d'information
📚 En ce 1er jour du #ForumInCyber, l'ANSSI et la DINUM publient le guide de l'homologation de sécurité des #SI.
Ce nouveau guide apporte des réponses claires et pragmatiques pour simplifier et accélérer la démarche d'homologation.
🔗 cyber.gouv.fr/publications...
01.04.2025 09:22 — 👍 17 🔁 7 💬 1 📌 0
Head of Investigations at InfoGuard AG - dfir.ch
CTF player with The Flat Network Society - bug bounty & web security research
Wannabe security guy. Director @ Zero-Point Security.
mitmproxy developer, making cloud more secure at Google. TLS, web, networks, and open source.
Mostly active on http://fedi.hi.ls these days, mirroring announcements here.
Professional Ethical Hacking Services
https://blog.silentsignal.eu
Former RE team lead
@synacktiv - Former @AirbusSecLab lead
Collector of Quote
NPR Cybersecurity Correspondent (currently) reporting on the transformation of the federal government including by DOGE.
Send me a tip: Text JennaMcLaughlin.54 on Signal from personal (nonwork) devices.
Freelancer | Full-time #BugBounty | @Hacker0x01 H1-Elite | $1,500,000 Overall Bounties | ❤️ IDA Pro | Mobile Hacker
Just another cloud consultant.
Security person who likes writing code
hacker, maldev, pokemon irl
I like making computers misbehave. Does stuff at http://specterops.io.
Github: https://github.com/leechristensen
Mastodon: @tifkin_@infosec.exchange
[ 'cto @sensepost.com', '@orangecyberdef', 'caffeine fueled', '(╯°□°)╯︵ ┻━┻', 'security guy', 'metalhead', 'i saw your password', 'KOOBo+KXleKAv+KXlSnjgaM=' ]
Official account for Cobalt Strike. Benchmark red teaming tool known for its flexibility and powerful user community. Follow for new releases and other updates.
@chvancooten on the bird app 🐦
---
Benevolently malicious offensive security enthusiast || OffSec Developer & Malware Linguist || NimPlant & NimPackt author || @ABNAMRO Red Team
Riding around in the breeze. Security Thinker. Hacker. USAF Veteran. https://aff-wg.org
Does a thing or two with red teaming @ Outflank | part time race and drift car instructor
Red Brain, Blue Fingers
Malware Analysis, Reverse Engineering, Threat Hunting, Detection Engineering, DFIR, Security Research, Programming, Curiosities, Software Archaeology, Puzzles, Bad dad jokes
https://www.hexacorn.com/blog/
hexacorn@infosec.exchange
Offensive security tools developer. Malware developer, hobby music producer, bedroom DJ & ex-MMO game hacker. Creator of Evilginx / Bartender @ BREAKDEV RED.