
The whitepaper is live! Learn how to win the HTTP desync endgame... and why HTTP/1.1 needs to die: http1mustdie.com
06.08.2025 23:43 — 👍 24 🔁 14 💬 0 📌 1@jameskettle.com.bsky.social
Director of Research at @portswigger.net Also known as albinowax Portfolio: https://jameskettle.com/

The whitepaper is live! Learn how to win the HTTP desync endgame... and why HTTP/1.1 needs to die: http1mustdie.com
06.08.2025 23:43 — 👍 24 🔁 14 💬 0 📌 1
At #BlackHat? Catch "HTTP/1.1 Must Die! The Desync Endgame" today at 3:20 in Oceanside A, Level 2. Hope to see you there!
06.08.2025 17:48 — 👍 6 🔁 1 💬 0 📌 0
Let me know if you'd like to chat research at Black Hat or #defcon33! Also feel free to say hi if you see me about, I've got a not-very-subtle laptop cover to aid recognition 😂
01.08.2025 13:30 — 👍 11 🔁 1 💬 0 📌 0
Not at Black Hat / DEF CON? You can still join the mission to kill HTTP/1.1:
- Watch the livestream from #DEFCON at 16:30 PT on the 8th
- Read the whitepaper on our website
- Grab the HTTP Request Smuggler update & WebSecAcademy lab
Follow for updates & links. It's nearly time!
Haha well race condition detections required laborious manual work too, so both aspects were brutal there!
30.07.2025 13:36 — 👍 1 🔁 0 💬 0 📌 0Yeah detections can get quite addictive, whereas exploits are often hard work.
30.07.2025 08:04 — 👍 1 🔁 0 💬 1 📌 0Our core website uses HTTP/2 end to end, but for maximum irony http1mustdie[.]com is stuck using HTTP/1.1 upstream due to AWS CloudFront limitations! However it's in scope for our bounty program... and if you manage to exploit it with HTTP request smuggling, we'll pay a bonus :)
29.07.2025 14:59 — 👍 10 🔁 4 💬 0 📌 0To try and achieve a desync refer to: portswigger.net/research/mak...
If you're stuck with tunneling, use: portswigger.net/web-security...
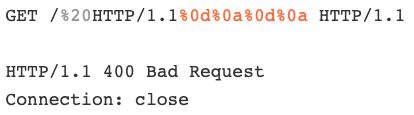
Ever seen a header injection where achieving a desync seemed impossible? I think I've finally identified the cause - nginx doesn't reuse upstream connections by default, and often has header injection. This means you're left with a blind request tunneling vulnerability 👇
28.07.2025 14:28 — 👍 8 🔁 0 💬 1 📌 0You know those non-vulnerabilities that companies get forced to fix for compliance reasons? I've found a full bypass for a common patch strategy. I'm half-tempted to keep it secret for the greater good 😂
25.07.2025 14:37 — 👍 11 🔁 0 💬 0 📌 0With cleats?! Terrible.
25.07.2025 11:15 — 👍 0 🔁 0 💬 0 📌 0
<input style=x type="hidden" onsecuritypolicyviolation="alert(1)">
Is your target leaking CSP violations left and right? Mikhail Khramenkov reveals how to hijack the onsecuritypolicyviolation event to trigger JS in hidden inputs - when unsafe-inline is in play and styles are blocked. Now live on our XSS cheat sheet.
portswigger.net/web-security...
I can confirm there will be stickers!
23.07.2025 14:56 — 👍 1 🔁 0 💬 1 📌 0Want to make the most of the upcoming research drop? We've just updated the page with links to essential pre-read/watch resources. Enjoy!
23.07.2025 14:54 — 👍 2 🔁 0 💬 0 📌 0I need details.
22.07.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0Now live on tools.honoki.net/smuggler.html
Let me know what you think! ✨
Yeah it’s hard to make a compelling argument in 300 words without disclosing any details! Happy for everyone to decide if they agree with my conclusion after reading the whitepaper!
22.07.2025 16:09 — 👍 3 🔁 0 💬 1 📌 0There are bad security takes, and then there is @daniel.haxx.se attempting to shame @jameskettle.com for not "responsibly disclosing" a vulnerability to the curl project that doesn't affect the curl project... and _then_ complaining the details are being kept "secret" :facepalm:
21.07.2025 12:28 — 👍 9 🔁 2 💬 2 📌 0The phrase just pops into my head wherever someone mentions Roots Manuva
19.07.2025 14:29 — 👍 0 🔁 0 💬 1 📌 0It's easy to bash vulnerabilities with logos but... I couldn't resist, say hello to http1mustdie.com :)
18.07.2025 12:56 — 👍 13 🔁 3 💬 2 📌 0Well well well!
18.07.2025 11:48 — 👍 1 🔁 0 💬 1 📌 0
New blog post is up: How I leaked the IP addresses of Brave's Tor window and Chrome VPN extension users--plus, a new Popunder technique and connect-src CSP directive bypass. Read more @ 0x999.net/blog/leaking...
16.07.2025 11:00 — 👍 5 🔁 5 💬 0 📌 0Manual testing doesn't have to be repetitive.
Meet Repeater Strike - an AI-powered Burp Suite extension that turns your Repeater traffic into a scan check.
Source code:
github.com/hackvertor/r...
Blog post:
portswigger.net/research/rep...
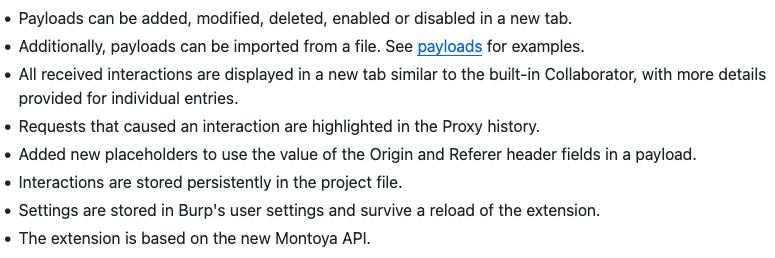
We've just released a massive update to Collaborator Everywhere! This is a complete rewrite by @compass-security.com which adds loads of features including in-tool payload customization. Massive thanks to Compass for this epic project takeover. Check out the new features:
14.07.2025 14:51 — 👍 19 🔁 7 💬 1 📌 1
How to make $$$ from request smuggling
Step 1) Pick the right target:

Today was my last day as a pentester at Bsecure. After a three-year journey of hunting on the side, I’m ready to go all-in as a full-time bug bounty hunter. You can read about my journey from pentester to full-time hunter here: gelu.chat/posts/from-p...
04.07.2025 15:09 — 👍 23 🔁 7 💬 3 📌 0We found a new vulnerability in TLS. It's a variant of the ALPACA attack that bypasses current countermeasures. Relativly low impact - but great insight! Check it out: opossum-attack.com
08.07.2025 12:26 — 👍 12 🔁 8 💬 1 📌 0It's relevant to request smuggling, but not directly related to my talk.
07.07.2025 11:59 — 👍 0 🔁 0 💬 1 📌 0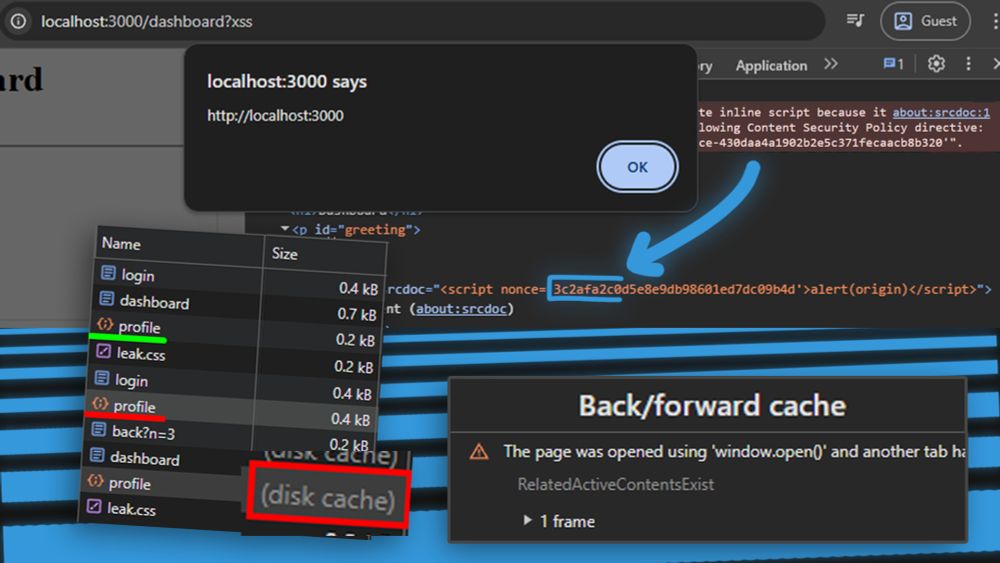
Here's my writeup the technique allowing some nonce-based CSPs to be bypassed. I think it definitely has some practical use, so included some details about different scenario's.
Don't let that HTML-injection of yours wait!
jorianwoltjer.com/blog/p/resea...
Nice one! I've shared it to r/websecurityresearch
03.07.2025 14:43 — 👍 1 🔁 0 💬 0 📌 0