As one of the folks involved in this I can echo it wasn't super advanced at all, and some of the malware contained errors (double TLS header network coms). The challenge the LLM use introduced was quantity to keep on top of - thankfully it was simple enough we could write quick automations to triage
14.11.2025 17:09 — 👍 2 🔁 0 💬 0 📌 0
Ooops 😅 #VTi
11.11.2025 16:04 — 👍 1 🔁 0 💬 0 📌 0
It's not a revolutionary change, but it will have an impact that will drive more automation in response I think.
09.11.2025 10:29 — 👍 0 🔁 0 💬 0 📌 0
It will increase the pace & variations in some operations, but at the cost of their quality/effectiveness. We observed an actor using it earlier this year & the nonsensical nature raised the opportunities for detection/prevention - but the quantity of it was definitely a challenge to be on top of
09.11.2025 10:29 — 👍 0 🔁 0 💬 1 📌 0

A chart showing how well 13 different Android AV apps detect 17 stalkerware products.
EFF teamed up with AV Comparatives to see how well anti-virus apps detect stalkerware on Android phones.
www.eff.org/deeplinks/20...
06.11.2025 20:22 — 👍 124 🔁 44 💬 7 📌 3

@stevenadair.bsky.social is back again!
Founder + President of Volexity leading a team of experts that deal w/ complex cyber intrusions from nation-state level intruders. His talk will cover a Chinese APT actor that Volexity tracks as UTA0388.
Check out the official agenda:
cyberwarcon.com
15.10.2025 15:11 — 👍 2 🔁 5 💬 0 📌 0

Go Get 'Em: Updates to Volexity Golang Tooling
Volexity’s GoResolver tool was released in April 2025 to help with analysis of these samples, reducing analyst load when working with obfuscated Golang binaries. However, there are still some difficul...
@volexity.com has released updates to its #opensource GoResolver project and more! This work was part of a project for one of our #summerinternship students. Read more details about Volexity’s updated GoResolver projects + other #golang tools in our special blog post!
11.08.2025 19:05 — 👍 10 🔁 10 💬 1 📌 0
This training course will be led by Andrew Case @attrc.bsky.social, Michael Ligh & Dave Lassalle. This is a great opportunity to gain valuable knowledge about #Volatility3 + learn all about #memoryforensics from Volatility core developers! Seats are filling up quickly so don't wait!
09.07.2025 20:54 — 👍 6 🔁 8 💬 0 📌 0
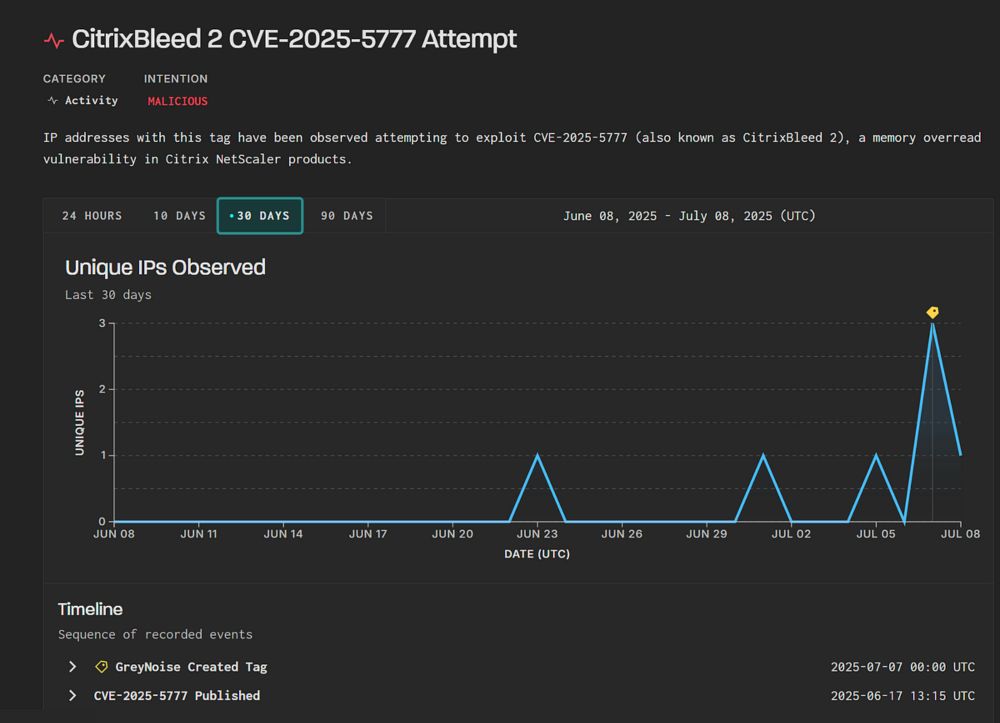
CitrixBleed 2 exploitation started mid-June — how to spot it
CitrixBleed 2 — CVE-2025–5777 — has been under active exploitation to hijack Netscaler sessions, bypassing MFA, globally for a month.
New by me - although Citrix say there is no evidence of exploitation of CitrixBleed 2 vulnerability, they are wrong - it has been under active exploitation since mid June by an IP associated to a ransomware group, with multiple IP addresses now involved.
doublepulsar.com/citrixbleed-...
08.07.2025 14:46 — 👍 81 🔁 35 💬 4 📌 0
It can tell you some forensic artifacts that can exist due to execution (e.g. for .NET) and it can also tell you what possible systems it can run on in the environment you're investigating.
For clarity this isn't an argument that inclusion of this is right in reporting, other info could be better.
14.05.2025 19:50 — 👍 2 🔁 0 💬 0 📌 0

BADBAZAAR and MOONSHINE: Spyware targeting Uyghur, Taiwanese and Tibetan groups and civil society actors
The NCSC and partners have revealed new details about how malicious cyber actors are using two forms of spyware to target individuals in Uyghur, Tibetan and Taiwanese communities as well as civil society groups.
www.ncsc.gov.uk/news/ncsc-pa...
09.04.2025 08:25 — 👍 14 🔁 14 💬 1 📌 0

tired of looking at email headers as disgusting plaintext? only want things of value to stand out?
look no further than this VSCode extension built by @jacoblatonis.me
marketplace.visualstudio.com/items?itemNa...
21.03.2025 20:02 — 👍 21 🔁 6 💬 2 📌 1
"It is possible to bypass authorization checks within a Next.js application, if the authorization check occurs in middleware."
With the amount of Next.js-based sites around, especially on infosec sites, I'd say this looks like a problem.
CVSS: 9.1
github.com/vercel/next....
21.03.2025 21:48 — 👍 23 🔁 9 💬 1 📌 1
We have been tracking multiple Russian APT groups aggressively targeting organizations with Microsoft Device Code authentication phishing. The attackers got creative with tricking users into granting them access to their accounts. Have a look at our blog for all the details!
14.02.2025 01:31 — 👍 15 🔁 7 💬 0 📌 1
CTI is the cause of my brainrot but I really cooked on this #salttyphoon #telecomhack
26.11.2024 22:18 — 👍 49 🔁 18 💬 5 📌 3
#threatintel @Recorded Future | Formerly @PwC GTI | Malware & infrastructure analysis with a side of cyberpunk. 🌃🌌 She/her, support 🏳️🌈🏳️⚧️✨
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference.
Snarkmonger. Chief Cloud Economist at The Duckbill Group.
he/him.
Get my opinionated take on AWS news: http://lastweekinaws.com/t/
Signal: 833-AWS-BILL (833-297-2455)
Security researcher @ Cisco Talos. / Ex-Google TAG / Black Hat & HITCON review board / Organiser of Rhacklette.
Security research and breaking news straight from ESET Research Labs.
welivesecurity.com/research/
Hacker. Friend. Cybersecurity Researcher at Huntress.
Secure everything you build and run in the cloud
Security editor, TechCrunch
Signal: zackwhittaker.1337
My stories: techcrunch.com/author/zack-whittaker
My newsletter/blog: this.weekinsecurity.com
Pro-democracy conservatives Republicans fighting Trump & Trumpism.
https://www.instagram.com/republicansagainsttrump/profilecard/?igsh=MXM4OGZ0cHRiOGdmMg==
Cybersecurity reporter at Bloomberg News in DC. Signal: @howelloneill.01, email: patoneill1@bloomberg.net https://www.bloomberg.com/authors/AXb8dLPHBFc/patrick-howell-oneill
cyber(punk) threat intel. cyber operations, counterintelligence, russia, iran. i see kanly today in everything. “bloody inertia interspersed with bouts of bloody frenzy.”
creator: #FUZZYSNUGGLYDUCK, drilangleton, Beff Horn.
opinions are my own.
Director for Malicious Infrastructure Discovery @ Recorded Future | Views my own
Research and development at the intersection of cyberspace, global security, and human rights. Based at Munk School of Global Affairs & Public Policy, University of Toronto.
Proofpoint's insights on targeted attacks and the cybersecurity threat landscape.
Censys is the trusted source for real-time Internet intelligence and actionable threat insights for global governments, Fortune 500 companies, and leading threat intelligence providers worldwide.
We are Microsoft's global network of security experts. Follow for security research and threat intelligence. https://aka.ms/threatintelblog
Official Bluesky page of the 780th Military Intelligence Brigade (Cyber). The Army's only offensive cyberspace operations brigade (following, re-posts, and links ≠ endorsement).
Host of the Fast politics podcast, contributing Writer at The New York Times opinion and MSNBC. Subscribe to fast politics YouTube channel
Also substack
Visual Stories and Investigations Editor at the Financial Times. We use computational tools and traditional reporting to produce explainers, investigations and deep dives in visual formats.