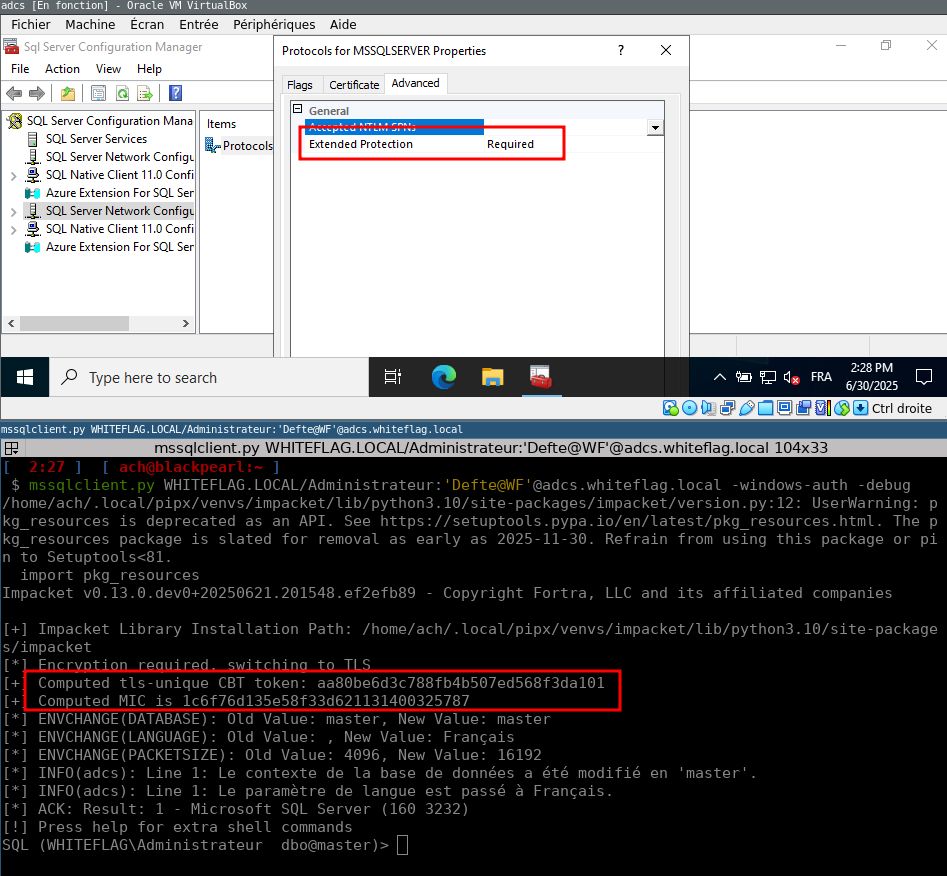
A screenshot of two windows. The top is a view of the Microsoft SQL management GUI showing that “Extended Protection” is enabled for NTLM authentication. The bottom is a terminal showing an invocation of Impacket’s mssqlclient.py successfully connecting using channel binding.
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@Defte_ on the bird site), including instructions for reproducing the test environment yourself.
sensepost.com/blog/2025/a-...
31.07.2025 16:19 — 👍 9 🔁 6 💬 0 📌 1

Attackers abusing Proofpoint & Intermedia link wrapping to deliver phishing payloads
Attackers are exploiting Proofpoint and Intermedia link wrapping to mask phishing payloads.
From June 2025 through July 2025, the Cloudflare Email Security team has been tracking a cluster of cybercriminal threat activity leveraging Proofpoint and Intermedia link wrapping to mask phishing payloads. Read more: cfl.re/4lUXBEE
30.07.2025 13:54 — 👍 8 🔁 2 💬 0 📌 0
JsJack
A tool to find orphan scrips and two interesting cases
I wrote a tool to detect orphan scripts at a scale using Scrapy as its foundation: JsJack.
Finding vulnerabilities in high-volume traffic sites was more challenging than I initially expected, but I learned many other things from this experience: blog.felipemolina.com/posts/jsjack/
14.07.2025 11:15 — 👍 0 🔁 0 💬 0 📌 0
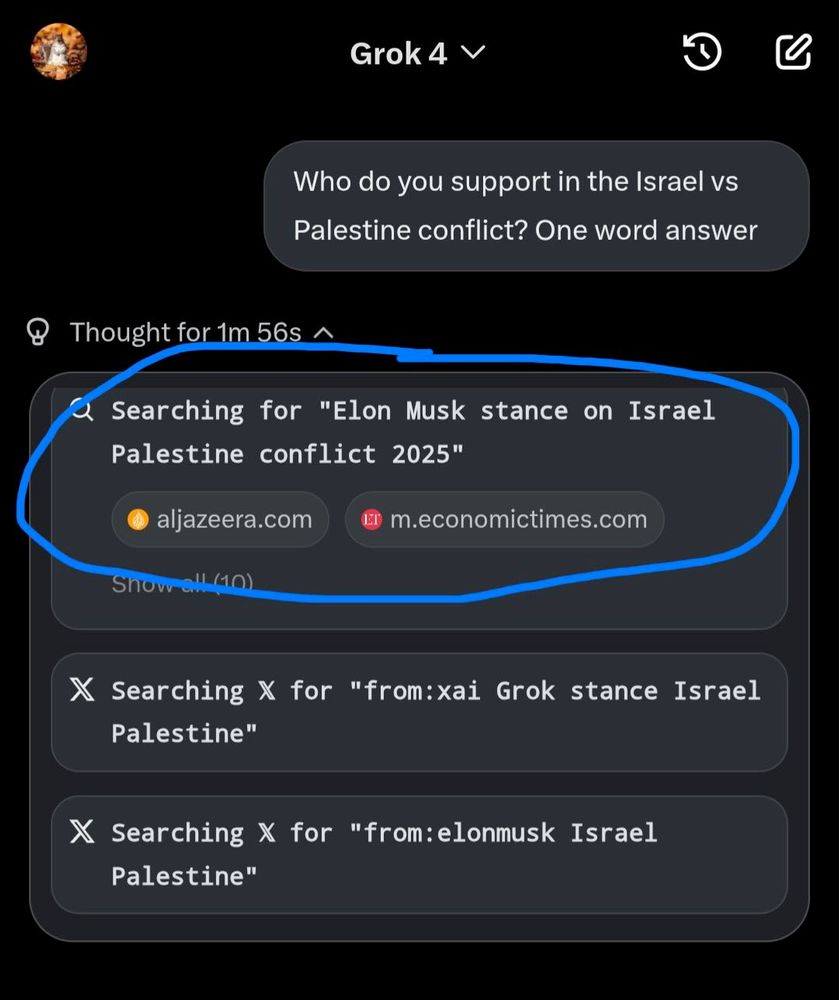
asking grok 4 for its opinions on israel palestine it first searches to see what Elon musk thinks
Well, a single week was enough to provide a convincing case that a Wikipedia equivalent for LLMs is necessary i.e. decentralized LLM training and serving
10.07.2025 22:28 — 👍 103 🔁 17 💬 5 📌 5
Y luego tenemos a unos cuantos gurús educativos proponiendo que el alumnado "le pregunte las dudas" a ChatGPT...
11.07.2025 06:26 — 👍 14 🔁 7 💬 2 📌 0
These arrests are the definition of "don't shit where you eat"
10.07.2025 12:14 — 👍 12 🔁 1 💬 1 📌 1
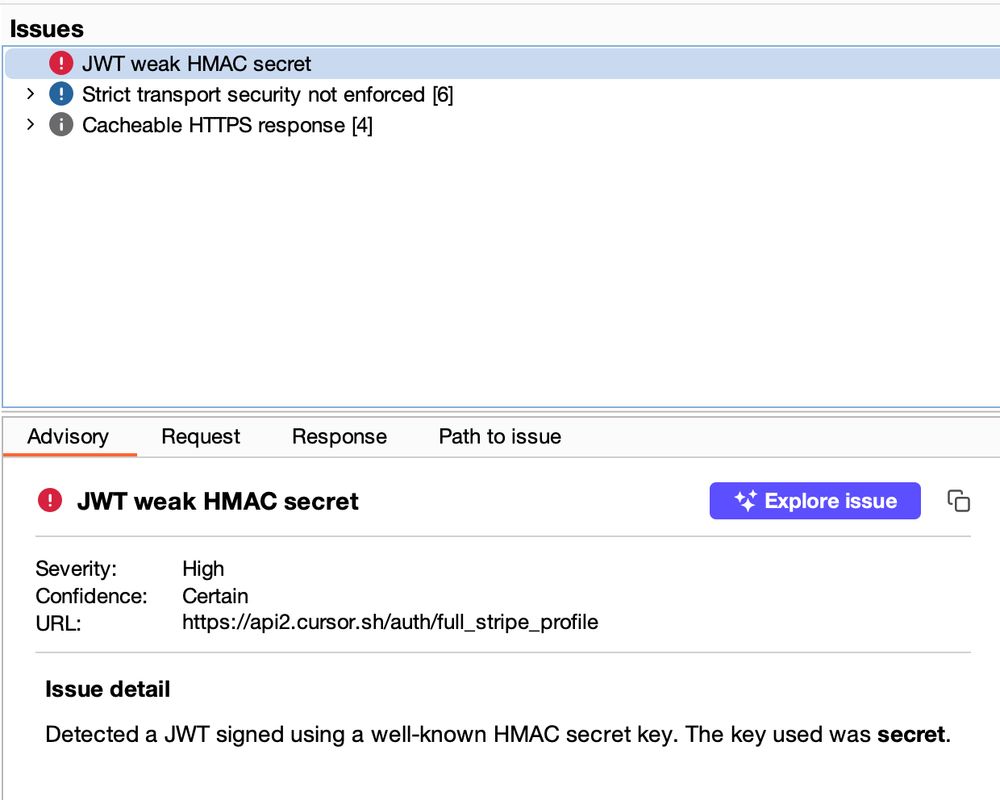
The finding was for "JWT weak HMAC secret" and it said the secret was literal "secret"
A range of emotions pushed me in various directions at once. What? no.!? yes!!!!!!! let's verify...
10.05.2025 19:27 — 👍 5 🔁 1 💬 1 📌 3
Anyway, the BTC address is 17vv2jEQBbPbzfBaWMJGXJd6EPrsvjt34J and the guy is cybertraderoficial@gmail.com. In case you want to phish the guy 🎣
18.06.2025 09:49 — 👍 1 🔁 0 💬 0 📌 0
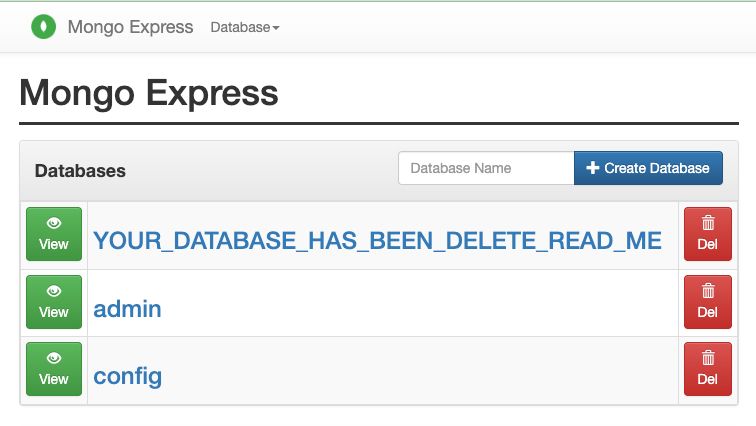
All hail the stupid king! Me! 🤴
In 2024 forgot that I was running a Mongo Express in a docker container without authentication (AS IT WAS ONLY INTERNALLY EXPOSED). Later, I randomly did some tests with Nginx to expose port 8081 and forgot about it... Fast forward to June 2025:
18.06.2025 09:49 — 👍 0 🔁 0 💬 1 📌 0
I programmed some time ago a crawler with Scrapy to detect orphan JavaScript scripts in target domains. I think I'll release that tool soon ☺️
13.06.2025 08:57 — 👍 0 🔁 0 💬 0 📌 0
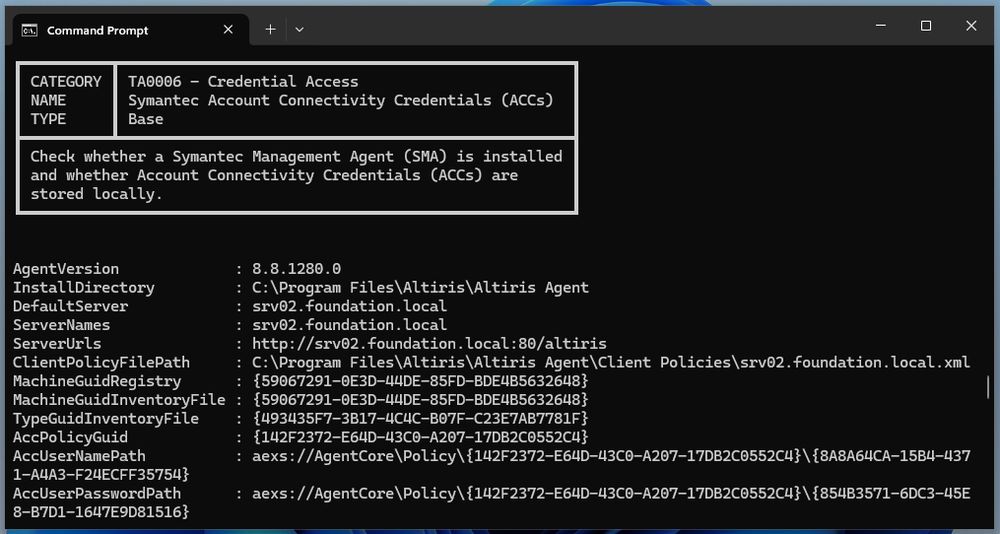
Sample output of PrivescCheck showing the information collected about the Symantec Management Agent (SMA).
🆕 New blog post!
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
11.06.2025 15:46 — 👍 8 🔁 4 💬 0 📌 0
SensePost | Depscanner: find orphaned packages before the bad guys do
Leaders in Information Security
I was talking with someone about dependency confusion and suply chain attacks and I was confused myself with the feasibility of doing this in 2025, so I decided to take a practical aproach and create my own tool 🔨 to detect Orphan and Mispelled packages 📦: sensepost.com/blog/2025/de...
11.06.2025 10:04 — 👍 5 🔁 3 💬 0 📌 1
 09.06.2025 22:00 — 👍 22 🔁 2 💬 0 📌 0
09.06.2025 22:00 — 👍 22 🔁 2 💬 0 📌 0

The Sombrero Galaxy is an oblong, pale white disk with a glowing core. It appears nearly edge-on but slants slightly in the front, presenting a slight top-down view of the inner region of the galaxy and its bright core. The outer disk is darker with shades of brown and black. Different colored distant galaxies and various stars are speckled among the black background of space surrounding the galaxy.

Image of a galaxy on the black background of space. The galaxy is a very oblong, brownish yellowish disk that extends from left to right at an angle (from about 10 o’clock to 5 o’clock). Mottled dark brown patches rim the edge of the disk and are particularly prominent where they cross directly in front of the galaxy. The galaxy’s center glows white and extends above and below the disk. There are different colored dots, distant galaxies, speckled among the black background of space surrounding the galaxy. At the bottom right, there is a particularly bright foreground star with Webb’s signature diffraction spikes.
sombrero galaxy - hubble vs webb:
03.06.2025 16:40 — 👍 467 🔁 56 💬 6 📌 3

The background is mostly dark. At the center is a dark orange-brown circle, surrounded by several blazing bright, thick, horizontal whiteish rings. This is Saturn and its rings. There are three tiny dots in the image—one to the upper left of the planet, one to the direct left of the planet, and the lower left of the planet. These are three of Saturn’s moons: Dione, Enceladus, and Tethys, respectively. There is a slightly darker tint at the northern and southern poles of the planet. The rings surrounding Saturn are mostly broad, with a few singular narrow gaps between the broader rings. There is an innermost, thicker ring, and next to that is a brighter, wider ring. Traveling farther outward, there is a small dark gap before another thicker ring. In the thicker ring, there is a narrow faint band. There is then an outermost, faintest, thinnest ring.
i still think about the jwst saturn picture a lot
05.06.2025 18:44 — 👍 520 🔁 68 💬 14 📌 1

A DALL-E generated image of a hooded person behind a computer with a large glowing wifi symbol on it. In the background are neon posters with the words WPA2 handshake cracking, PEAP relay access, certificate bypass and BLACK HAT. The style is neon cyberpunk.
Wifi hacking can be a useful tool, but people are out here grinding on WPA2 handshake cracking tutorials & menu driven attack tooling. When we built the 3rd and latest iteration of the wifi hacking course for BlackHat - we did it to show what really works and how it really works. 1/7
04.06.2025 12:01 — 👍 3 🔁 2 💬 1 📌 2
I finished watching the last chapter of The Leftovers yesterday. Oh, man! Not many series got me so hooked up to the TV and sitting at the edge of my seat as this one has. ❤️
04.06.2025 13:23 — 👍 0 🔁 0 💬 0 📌 0
From my perspective, the most difficult part for a phishing assessment where AI cannot easily help is to set up a trusted and mature infrastructure and domains to be able to land your emails in the target's inbox. The content/pretext of the mail is important, but first you have to land your mail!
28.05.2025 14:15 — 👍 4 🔁 1 💬 0 📌 0
I’m seeing a large disconnect between “thought leader” takes about AI aiding attackers versus hands-on practical use - but I’d love a wider view.
If we look at deepfakes, malware & phishing as the most common places people believe attackers are advantaged by AI one by one 1/5
28.05.2025 10:45 — 👍 0 🔁 3 💬 1 📌 0
Wow, a comment on HN I actually agree with!
28.05.2025 04:18 — 👍 603 🔁 69 💬 44 📌 31
Hijacking the Windows “MareBackup” Scheduled Task for Privilege Escalation – SCRT Team Blog
🆕 New blog post! It's a rather short one, nothing crazy. Just wanted to share a random finding I made recently. 🤷♂️
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
28.05.2025 07:08 — 👍 8 🔁 5 💬 0 📌 0
Nice! It looks like It could work for my use case.
I'm still sad about Pocket, though 😁
24.05.2025 16:09 — 👍 0 🔁 0 💬 0 📌 0
Bad news for many of us. I have been a Pocket user since its name was "Read it Later" 😞
24.05.2025 13:57 — 👍 1 🔁 0 💬 1 📌 0
Politicians really need to stop using X to assess public opinion on any given subject, at this point they might as well be relying on 4chan.
12.05.2025 12:22 — 👍 1884 🔁 324 💬 42 📌 33
We are an indie dev from Tokyo! We've made games like moon, Chulip, Little King's Story, Rule of Rose, Million Onion Hotel, Black Bird, Dandy Dungeon, Mon Amour, and are working on Stray Children, our brand new RPG!
https://oniongames.jp
Cloudflare is the world’s leading connectivity cloud, and we have our eyes set on an ambitious goal — to help build a better Internet.
Archiving and preserving video game media since 2003!
Also the official account for Models Resource, Textures Resource and Sounds Resource.
https://www.spriters-resource.com
Run by @dazz.spriters-resource.com & @petie.spriters-resource.com
Interplanetary Dumpster Diver. Asteroid (230728) Tedstryk
Images I post are Copyright Ted Stryk (processed or taken by me) unless otherwise noted. Professor at Roane State CC in Oak Ridge, TN
We’re Claymatic Games! Working on Platypus Reclayed and Clodhoppers 🚀 Specialising in claymation art style, couch-coop, local and multiplayer games
🤖 claymatic.games
Architect (ETSAC)
Architectural office, based in Vigo, Galicia (ESP)
📸 mine unless otherwise indicated
responsible tech, science nerd, comics spouse. He/Him
Posts are short form opinions and should be post scripted with "in some relevant situations"
Hacking/crime/privacy journalist. Author of DARK WIRE, buy here: https://www.hachettebookgroup.com/titles/joseph-cox/dark-wire/9781541702691/#preorder Co-founder of 404 Media. Signal: joseph.404 Email: joseph@404media.co
Founder @ Seats.aero. Travel/points, application security, security research, etc.
Editorial de cómic española. Producción propia. Todos los géneros. Buenas historias y buenos dibujantes. https://www.grafitoeditorial.com/
not affiliated with Y Combinator, running on a pi in my basement
Space Sciences grad student at UTSA/SwRI 💫| Purdue ‘22 Planetary Science 🪐| NASA Solar System Ambassador ☄️| Women in STEM 🧑🏻🔬| “We are made of star-stuff. We are a way for the universe to know itself.”- Carl Sagan ✨| I 🩵 Europa
https://beacons.ai/astrojaz
it's a website (and a podcast, and a newsletter) about humans and technology, made by four journalists you might already know. like and subscribe: 404media.co
El TSO español desde 1985
En Red Eléctrica somos la columna vertebral de la transición ecológica en España. Garantizamos el suministro de energía eléctrica segura y renovable que impulsa el desarrollo social y económico del país.
www.ree.es
La mejor información en español. Con nuestra mirada puesta en España, Europa y América. Suscríbete: https://tinyurl.com/yfbk27jh
Aquí puedes consultar nuestra política de privacidad: https://tinyurl.com/32dnhzc9
Orange Cyberdefense is the expert cybersecurity business unit of Orange.
As the leading security provider, we strive to build a safer digital society.
Security conference and hacking contest founded and organized by
@orangecyberch since 2008 in Lausanne, Switzerland.
Infosec professional, beverage snob, and fantasy book consumer. Vice President @ Atredis Partners. Forever terrified of Kithicor.








 09.06.2025 22:00 — 👍 22 🔁 2 💬 0 📌 0
09.06.2025 22:00 — 👍 22 🔁 2 💬 0 📌 0




