
We are deeply saddened by the passing of David Harley, a brilliant cybersecurity expert, former ESET Senior Research Fellow, author and long-time Virus Bulletin contributor.
David's legacy spans decades of research, writing, and public speaking.
Rest in peace, David. You will be missed. 💙
07.11.2025 15:33 — 👍 6 🔁 2 💬 0 📌 0

#ESETresearch identified an active campaign distributing #NGate – Android NFC relay malware used for contactless payment fraud – targeting Brazilian users.
It is available for download via fake Google Play sites mimicking 4 major banks and 1 e-commerce app. 1/4
06.11.2025 14:00 — 👍 2 🔁 2 💬 1 📌 0

#ESETresearch has released its latest APT Activity Report (Apr–Sep 2025): China-aligned groups targeted Latin America amid US-China tensions. Russia-aligned groups intensified ops against Ukraine & EU states. Full report: web-assets.esetstatic.com/wls/en/paper...
06.11.2025 11:58 — 👍 5 🔁 4 💬 0 📌 1

The targeted sectors include defense, metal engineering, and the UAV sector. The attackers left the keyword “drone” in their payloads, directly suggesting one of their goals. 3/9
23.10.2025 04:10 — 👍 3 🔁 1 💬 1 📌 0
#ESETresearch discovered a new wave of the well-known North Korea-aligned Lazarus campaign Operation DreamJob, now targeting the drone industry.
welivesecurity.com/en/eset-rese... 1/9
23.10.2025 04:10 — 👍 9 🔁 9 💬 1 📌 2
Call for proposals – Botconf 2026
The dates of #Botconf2026 - The Botnet and Malware Ecosystems Fighting Conference have been confirmed for our
13th ed - Workshops (14th) & Conference (15th-17th) April 2026 in Reims, France
The CFP is online and ends on January 2nd 2026
https://www.botconf.eu/call-for-proposals/
15.10.2025 14:26 — 👍 1 🔁 7 💬 0 📌 0

Android #ToSpy, the spyware used in the other campaign, masquerades solely as the ToTok app. It is distributed through phishing websites impersonating app distribution platforms, such as the Samsung Galaxy Store. 3/6
02.10.2025 09:23 — 👍 2 🔁 1 💬 1 📌 0
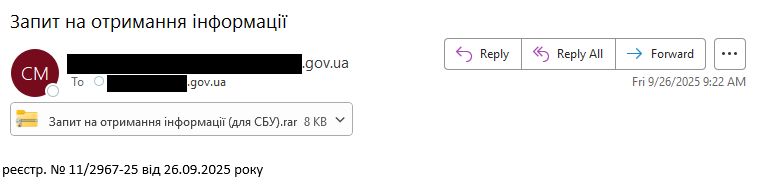
#ESETresearch has observed #Gamaredon exploiting CVE-2025-8088 (#WinRAR path traversal) in an ongoing spearphishing campaign. This vulnerability allows arbitrary file write via crafted RAR archives. 1/6
26.09.2025 13:13 — 👍 17 🔁 9 💬 1 📌 1

UK police arrest man linked to ransomware attack that caused airport disruptions in Europe | TechCrunch
The U.K.s National Crime Agency said the investigation into the ransomware attack against Collins Aerospace is “in its early stages and remains ongoing.”
NEW: The U.K.'s National Crime Agency announced an arrest linked to the ransomware attack against Collins Aerospace, which caused disruptions at several European airports over the weekend.
The man is out on bail, and the agency said the investigation is “in its early stages and remains ongoing.”
24.09.2025 13:15 — 👍 6 🔁 3 💬 0 📌 0

Gamaredon X Turla collab
ESET researchers reveal how the notorious APT group Turla collaborates with fellow FSB-associated group known as Gamaredon to compromise high‑profile targets in Ukraine.
#ESETresearch has discovered the first known cases of collaboration between Gamaredon and Turla, in Ukraine. Both groups are affiliated with the FSB, Russia’s main domestic intelligence and security agency. www.welivesecurity.com/en/eset-rese...
1/3
19.09.2025 09:27 — 👍 7 🔁 6 💬 1 📌 0

HybridPetya installs a malicious EFI application to the EFI System Partition, which then encrypts the Master File Table file, an essential metadata file with information about all files on the NTFS-formatted partition. 2/8
12.09.2025 09:02 — 👍 3 🔁 2 💬 1 📌 0

We performed an internet-wide scan to complement ESET telemetry and identify additional servers affected by this threat: at least 65 servers have been affected by late June 2025, mostly in Brazil, Thailand, and Vietnam. 2/6
04.09.2025 10:06 — 👍 2 🔁 1 💬 1 📌 0

Rungan is a passive C++ backdoor capable of executing commands on the compromised server. 4/6
04.09.2025 10:06 — 👍 2 🔁 1 💬 1 📌 0

#ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/7
26.08.2025 15:37 — 👍 65 🔁 45 💬 2 📌 14

Paper Werewolf атакует Россию с использованием уязвимости нулевого дня в WinRAR
Кластер Paper Werewolf продолжает атаковать российские организации — на этот раз с использованием уязвимостей в WinRAR
This vulnerability was also exploited by another threat actor, independently discovered by the Russian cybersecurity company BI.ZONE, who claim Paper Werewolf began using CVE-2025-8088 on July 22, just a few days after RomCom did. 6/7
bi.zone/expertise/bl...
11.08.2025 09:08 — 👍 2 🔁 1 💬 1 📌 0

WinRAR on X: "📢In case you haven't noticed, we've released a new version! ⏫Update today!🚀 https://t.co/Rj4h5hnODw" / X
📢In case you haven't noticed, we've released a new version! ⏫Update today!🚀 https://t.co/Rj4h5hnODw
On July 24, we alerted the WinRAR team, which released version 7.13 just six days later. We advise all users to install the latest version as soon as possible. We would also like to thank the WinRAR team for its cooperation and quick response. 3/7 x.com/WinRAR_RARLA...
11.08.2025 09:08 — 👍 4 🔁 1 💬 1 📌 0
#ESETresearch has discovered a zero-day vulnerability in WinRAR, exploited in the wild by Russia-aligned #RomCom @dmnsch @cherepanov74 www.welivesecurity.com/en/eset-rese...
1/7
11.08.2025 09:08 — 👍 17 🔁 11 💬 1 📌 2

#ESETresearch joins Europol’s Cyber Intelligence Extension Programme (CIEP) 🤝 We are proud to announce ESET’s participation in the pilot phase of CIEP, a new initiative launched by Europol 's European Cybercrime Centre (EC3). 1/5
07.08.2025 13:38 — 👍 8 🔁 4 💬 1 📌 0

ESET first detected an attempt to exploit part of the execution chain on July 17 in🇩🇪. Here, the final #webshell payload was not delivered. The first time we registered the payload was on July 18 in🇮🇹. We have since seen active ToolShell exploitation all over the world. 2/5
24.07.2025 09:10 — 👍 0 🔁 1 💬 1 📌 1
#BREAKING #ESETResearch has been monitoring the recently discovered #ToolShell zero-day vulnerabilities in #SharePoint Server: CVE-2025-53770 and CVE-2025-53771. SharePoint Online in Microsoft 365 is not impacted. www.welivesecurity.com/en/eset-rese... 1/5
24.07.2025 09:10 — 👍 2 🔁 6 💬 1 📌 0

Unmasking AsyncRAT: Navigating the labyrinth of forks
ESET researchers map out the labyrinthine relationships among the vast hierarchy of AsyncRAT variants.
#ESETresearch has mapped the labyrinth of #AsyncRAT forks, identifying the most prevalent versions of this open-source malware. While some variants are mere curiosities, others pose a more tenacious threat. www.welivesecurity.com/en/eset-rese... 1/7
15.07.2025 12:10 — 👍 7 🔁 5 💬 1 📌 0
Danabot was targeted by the #FBI and #DCIS, alongside #OperationEndgame led by #Europol and #Eurojust. ESET participated together with several other companies. We provided the analysis of the malware’s backend infrastructure and identified its C&C servers. 3/6
11.07.2025 12:27 — 👍 2 🔁 1 💬 1 📌 0
After years of dominance in #ESET’s top #infostealer statistics, the era of #AgentTesla has come to an end. It finished H1 2025 in fourth place, its numbers having decreased by 57%. The reason? It is no longer under active development. 1/4
09.07.2025 12:11 — 👍 6 🔁 6 💬 1 📌 0

ESET Threat Report H1 2025: #ClickFix attacks surge 500%, SnakeStealer tops infostealer charts, and NFC fraud jumps 35x. Plus, chaos in the ransomware underworld and a new Android adware menace—Kaleidoscope. Dive into the full report: web-assets.esetstatic.com/wls/en/paper... #ESETresearch
26.06.2025 09:14 — 👍 7 🔁 4 💬 0 📌 0
News, media and data from around the globe. Covering politics, economics, science, tech and sport.
Images with no cats. 👀 All content = submissions or with credit to OP. Submissions/enquiries: catswithjobstwitter@gmail.com - Buy me a coffee: https://ko-fi.com/translatedcats/
The Botnet and Malware Ecosystems Fighting Conference
13th ed - Workshops (14th) & Conference (15th-17th) April 2026 in Reims, France
🌉 bridged from ⁂ https://infosec.exchange/@botconf, follow @ap.brid.gy to interact
Security research and breaking news straight from ESET Research Labs.
welivesecurity.com/research/
@ESET Distinguished Researcher | alum of McAfee, Microsoft MVP, Tribal Voice, Zultys | Mod @Lenovo, @Neowin.Net, Scots Newsletter forums | Intel Insider Council | Repost ≠ endorse
Cartoons and comics by Steve Nelson.
Manager: mkrell@3arts.com
https://linktr.ee/twonkscomics
EDR R&D team lead at ESET. Opinions are my own.
@j91321@infosec.exchange
Security editor, TechCrunch
Signal: zackwhittaker.1337
My stories: techcrunch.com/author/zack-whittaker
My newsletter/blog: this.weekinsecurity.com
Sharing updates about trust and safety on Bluesky.
This account’s mentions are not actively monitored. To report a post or account, use the in-app reporting feature.
Community Guidelines: https://bsky.social/about/support/community-guidelines
🇨🇿Czech fan of Transformers, Godzilla, paleontology, cats, animals, drawing (mostly paleoart), movies and videogames, active mostly on weekends, ✝️,🇺🇦🇮🇱🇹🇼
We are the Threat Intelligence and Malware Analysis team of
@sentinelone.com
https://sentinellabs.com
https://labscon.io
Breaking cybersecurity and technology news, guides, and tutorials that help you get the most from your computer. DMs are open, so send us those tips!
☆ Cybersecurity reporter
★ Newsletters at Risky Business
#infosec #cybersecurity
https://risky.biz
experts in eCommerce security - https://sansec.io






















