
🔥 New Research from @hegel.bsky.social 🔥
PhantomCaptcha: A short-lived, multi-stage PowerShell and WebSocket RAT operation targeting Ukraine-linked humanitarian and government entities.
Full report: s1.ai/pcapt
@sentinellabs.bsky.social
We are the Threat Intelligence and Malware Analysis team of @sentinelone.com https://sentinellabs.com https://labscon.io

🔥 New Research from @hegel.bsky.social 🔥
PhantomCaptcha: A short-lived, multi-stage PowerShell and WebSocket RAT operation targeting Ukraine-linked humanitarian and government entities.
Full report: s1.ai/pcapt

🔥🔥 Fresh research drop live from #labscon Arizona. @alex.leetnoob.com and @morecoffeeplz.bsky.social with @vkamluk.bsky.social
The Hunt for LLM-enabled malware #ai #cyber #threatintel
s1.ai/llm-mw
Reddit AMA with our very own @dakotaindc.bsky.social—ask him anything here: www.reddit.com/r/geopolitic...
13.09.2025 21:42 — 👍 4 🔁 2 💬 0 📌 0
🚨New research drop: Contagious Interview | North Korean Threat Actors Reveal Plans and Ops by Abusing Cyber Intel Platforms
It was a pleasure collaborating with Sreekar Madabushi and @kennethkinion.bsky.social from Validin!
Read our blog post: s1.ai/nk-ops

🏆 Bragging rights, a $100K Prize Pool, and an all-expenses-paid trip to SentinelOne’s OneCon conference in Las Vegas. 🎰 Step up, test your skills, and claim your crown 👑
Sign up below (includes details on terms and conditions):

The Cyber Patents China Didn’t Want Us to Find: @dakotaindc.bsky.social and @sentinellabs.bsky.social uncovered 10+ patents for highly intrusive forensics and data collection tools—filed by companies named in U.S. gov't. indictments for working with the Chinese Hafnium (aka Silk Typhoon) APT group.
25.08.2025 19:29 — 👍 3 🔁 1 💬 1 📌 0
🔥 Fresh from the LABS team and our friends at Beazley Security 👇https://www.sentinelone.com/labs/ghost-in-the-zip-new-pxa-stealer-and-its-telegram-powered-ecosystem/
06.08.2025 13:55 — 👍 2 🔁 1 💬 0 📌 0Our team collaborated with our friends at @sentinellabs.bsky.social to identify and disrupt a PXA infostealer campaign that has an intricate and complex delivery chain:
labs.beazley.security/articles/gho...
Thanks for the fantastic collab SentinelLabs team!

🌀🔥… the complex relationship btw CN APTs🕵️♂️ and CN PSOAs 🇨🇳 makes attribution even more challenging than defenders might have supposed. #cti #threatintel #hafnium #silktyphoon @dakotaindc.bsky.social
www.sentinelone.com/labs/chinas-...
This week's show is YouTube ready @craiu.bsky.social @jags.bsky.social
🔥 Microsoft Sharepoint security crisis: Faulty patches, Toolshell zero-days
youtu.be/3GJuVGmpexA
⚠️ #0-DAY #Microsoft
👾 #CVE-2025-53770
🔩 #ToolShell
bsky.app/profile/sent...

👀 Apple: “macOS is secure by design.”
💻 Meanwhile, in /Users/Shared:
🕵️♂️ Persistent Malware masquerading as Apple “agent”
>> Khepri beacon in /tmp
📦 Ad-hoc signed payloads
🌍 Targeting Chinese diaspora
Deep dive from Dinesh Devadoss and me 👉 s1.ai/zuru
#icymi #macOS #malware #APT #infosec

💥 Fresh from LABS @philofishal.bsky.social and @syrion89.bsky.social
Our guys untangle the knots of #NimDoor: compiled Nim, macOS process injection and signals-based persistence triggers, with AppleScript (⁉️) beacons (whatever will they think up next 😅) 🌶️🌶️.
#dprk #apt #macOS
s1.ai/nimdoor
This week's show is a three-hour deep dive into Predatory Sparrow and the long-simmering Iran-Israel cyberwar (with @darkcell.bsky.social @craiu.bsky.social @jags.bsky.social youtu.be/MKKzHseTUUQ?...
21.06.2025 17:55 — 👍 4 🔁 3 💬 0 📌 0"The best netflow comes from asking friends for favors." -- @jags.bsky.social @craiu.bsky.social
14.06.2025 16:16 — 👍 9 🔁 2 💬 1 📌 1
Get the full story here:
www.sentinelone.com/labs/follow-... [2/2]
We just released our findings on long-term activity clusters attributed to China-nexus actors.
We discuss a relatively underreported, yet critical, aspect of the threat landscape: the targeting of cybersecurity vendors.
Big shout out to Lumen's Black Lotus Labs for their support! [1/2]

From PhD work to award-winning cybercrime research, @milenkowski.bsky.social of SentinelLABS is a force in malware analysis.
Catch his talk at #SLEUTHCON 2025!
🎟️ Grab your ticket today >>> www.sleuthcon.com
#CyberThreatIntel #InfosecEvents

📄 Read the full research: s1.ai/TopTier
29.04.2025 19:06 — 👍 7 🔁 4 💬 0 📌 0
Love when we can talk about hoy dynamic the threat landscape actually is. The scope and scale of the DPRK IT workers effort alone surprised me as we worked it. Also love @sentinelone.com let us discuss this openly and viewed it as important to do so.
www.sentinelone.com/labs/top-tie...

Appreciate the shoutout @jags.bsky.social (and that you aced my last name)! If you don’t listen to the Three Buddy Podcast yet, it is absolutely amazing and you should!
open.spotify.com/show/6dXbRag...

At @pivotcon.bsky.social, I'm presenting with @hegel.bsky.social and Sreekar Madabushi on the first public look at the full scope of a stealthy, long-running phishing network.
24.04.2025 14:31 — 👍 7 🔁 5 💬 0 📌 0
Very excited to share that I’ll be presenting at @sleuthcon.bsky.social in June!
Jim & I will share the backstory behind AkiraBot that didn’t make it into the blog—and what they’ve been up to since.

Published a new Pharos report today - and learned a lot in the process from @milenkowski.bsky.social Jiro, @julianferdinand.bsky.social @tgrossman.bsky.social. The report takes a closer look at how states are using ransomware.
virtual-routes.org/wp-content/u...
👉 s1.ai/akirabot
#OpenAI abused by spambot to carve out custom messages and beat CAPTCHAs. #security
@alex.leetnoob.com 🕸️
it feels like an useful feature so I have just implemented it under aflmc. thanks for sharing your alias! github.com/radareorg/ra...
11.04.2025 08:53 — 👍 3 🔁 2 💬 0 📌 0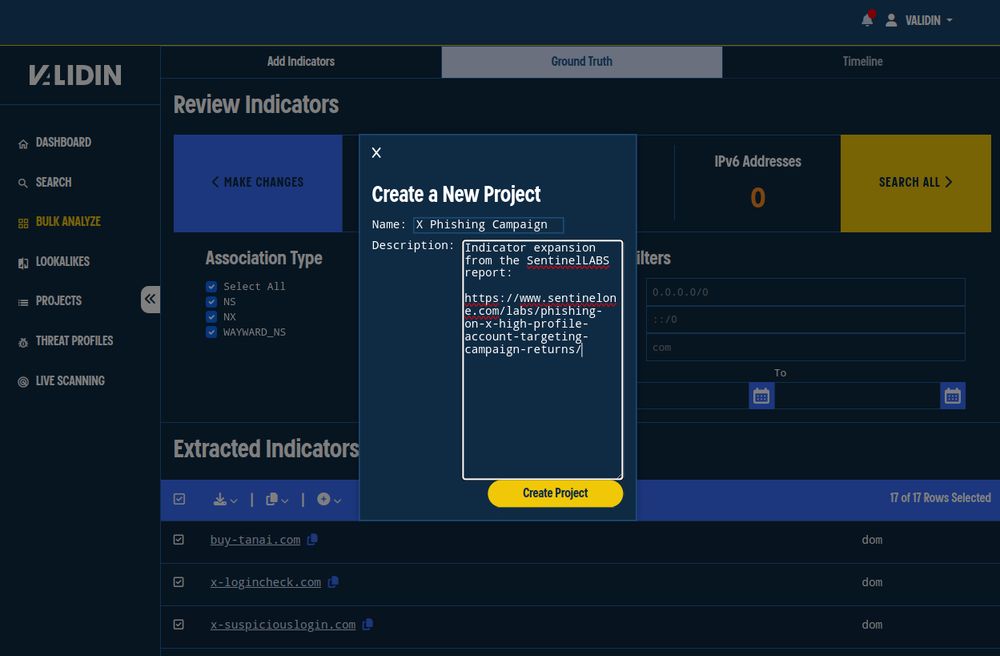
How to pivot of network indicators with Validin.
Learn how to pivot on network iocs you find in blog posts 🔥 #validin
www.validin.com/blog/x-phish...
🔥⚔️ Presenting our Just A Sec livestream. In the first-ever episode on April 10 at 2 p.m. PT, @dakotaindc.bsky.social, Drea London, @jags.bsky.social, and @stonepwn3000.bsky.social discuss the hidden forces shaping our digital world.
03.04.2025 21:23 — 👍 5 🔁 3 💬 1 📌 2