RFC 9001: Using TLS to Secure QUIC
This document describes how Transport Layer Security (TLS) is used to secure QUIC.
Wow, QUIC Retry Packets use AES-GCM with a fixed key/nonce, empty plaintext, and associated data prefixed with a secret as a sort of MAC. That's... terrifying?
They essentially do MAC(K, v) = AES-GCM(key=const, nonce=const, plaintext=empty, aad=K||v). Does that actually hold?
24.11.2025 10:51 — 👍 43 🔁 7 💬 6 📌 0

Claude Code Can Debug Low-level Cryptography
Surprisingly (to me) Claude Code debugged my new ML-DSA implementation faster than I would have, finding the non-obvious low-level issue that was making Verify fail.
I had a bug in my new ML-DSA implementation that caused Verify to reject all signatures. I gave up after half an hour. On a whim, I threw Claude Code at it. Surprisingly (to me!) it one-shotted it in 5 minutes.
A small case study of useful AI tasks that aren't generating code that requires review.
01.11.2025 18:26 — 👍 89 🔁 19 💬 7 📌 5

Abstract. The European Commission’s 2022 proposal for a regulation on child sexual abuse material, popularly labelled ChatControl, obliges online services to detect, report, and remove prohibited content, through client-side scanning.
This paper examines the proposal as a case of undone science in computer security ethics: a domain where technical feasibility and rights-compatibility questions remain systematically underexplored. Combining legal analysis with philosophy of technology, the paper argues that client-side scanning transforms end-to-end encryption from a right to secrecy into a conditional privilege of use. By integrating Isaiah Berlin’s concept of negative liberty, Langdon Winner’s account of the politics of artifacts, and David Hess’s notion of undone science, the analysis traces how design choices become moral constraints.
The discussion situates the European debate within broader concerns about proportionality, epistemic selectivity, and the governance of digital infrastructures. Ultimately, the study shows that the controversy over ChatControl is not only about privacy or child protection but about the epistemic norms that define what counts as legitimate technological knowledge.

Image showing part 2 of abstract.
What is Cryptography Hiding from Itself? (Diego F. Aranha, Nikolas Melissaris) ia.cr/2025/1951
20.10.2025 01:09 — 👍 12 🔁 5 💬 0 📌 0
Why haven't quantum computers factored 21 yet?
Craig Gidney's computer science blog
Why factoring (of numbers that aren’t 15) isn’t a good benchmark for tracking the progress of quantum computers.
algassert.com/post/2500
31.08.2025 15:40 — 👍 2 🔁 1 💬 0 📌 0
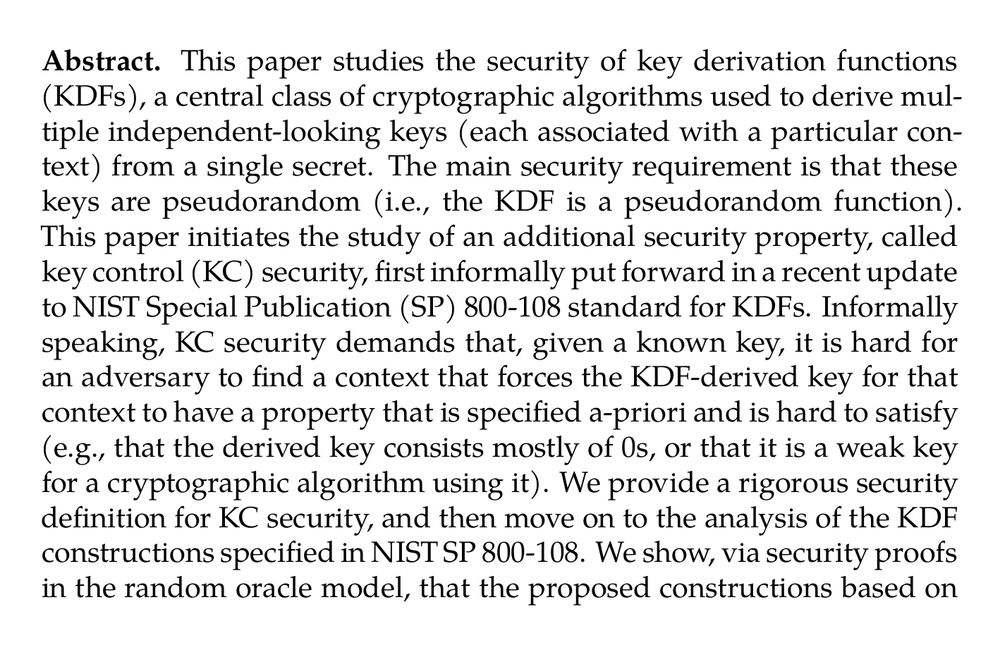
Abstract. This paper studies the security of key derivation functions (KDFs), a central class of cryptographic algorithms used to derive multiple independent-looking keys (each associated with a particular context) from a single secret. The main security requirement is that these keys are pseudorandom (i.e., the KDF is a pseudorandom function). This paper initiates the study of an additional security property, called key control (KC) security, first informally put forward in a recent update to NIST Special Publication (SP) 800-108 standard for KDFs. Informally speaking, KC security demands that, given a known key, it is hard for an adversary to find a context that forces the KDF-derived key for that context to have a property that is specified a-priori and is hard to satisfy (e.g., that the derived key consists mostly of 0s, or that it is a weak key for a cryptographic algorithm using it). We provide a rigorous security definition for KC security, and then move on to the analysis of the KDF constructions specified in NIST SP 800-108. We show, via security proofs in the random oracle model, that the proposed constructions based on XOFs or hash functions can accommodate for reasonable security margins (i.e., 128-bit security) when instantiated from KMAC and HMAC. We also show, via attacks, that all proposed block-cipher based modes of operation (while implementing mitigation techniques to prevent KC security attacks affecting earlier version of the standard) only achieve at best 72-bit KC security for 128-bit blocks, as with AES.

Image showing part 2 of abstract.
Cryptographic Treatment of Key Control Security – In Light of NIST SP 800-108 (Ritam Bhaumik, Avijit Dutta, Akiko Inoue, Tetsu Iwata, Ashwin Jha, Kazuhiko Minematsu, Mridul Nandi, Yu Sasaki, Meltem Sönmez Turan, Stefano Tessaro) ia.cr/2025/1123
16.06.2025 21:21 — 👍 4 🔁 3 💬 0 📌 0

Three white icons on a gradient background that transitions from blue on the left to pink on the right. The first icon, on the left, is a microchip with a padlock in the center. The middle icon is a flowchart diagram with connected shapes. The third icon, on the right, consists of two angle brackets facing each other.
We're rewriting parts of Microsoft's SymCrypt cryptographic library in Rust to improve memory safety and defend against side-channel attacks, enabling formal verification while maintaining backward compatibility via a Rust-to-C compiler: msft.it/6011SU7Fc
10.06.2025 16:30 — 👍 32 🔁 9 💬 1 📌 1
Oh wow, this is really great work. Recent results on PCGs allowed much more efficient MPC preprocessing (among other things) using somewhat new assumptions. Apparently, these assumptions are too strong.
Congratulations to the authors on their IACR grant slam of breaks :)
20.05.2025 04:02 — 👍 5 🔁 1 💬 0 📌 0
quite surprising indeed, seems to be due to a high visa overstay rate of Bhutanese nationals in the US bestofbhutan.com/bhutans-shoc...
16.03.2025 08:46 — 👍 1 🔁 0 💬 0 📌 0
Awesome to see my Cortex-M4/7 Keccak implementations further improved by SLOTHY, a very promising optimization tool!
05.03.2025 06:49 — 👍 0 🔁 0 💬 0 📌 0

AMD: Microcode Signature Verification Vulnerability
### Summary
Google Security Team has identified a security vulnerability in some AMD Zen-based CPUs. This vulnerability allows an adversary with local administrator privileges (ring 0 from outside...
Confidential computing is a pretty cool paradigm; in theory, you don’t need to trust your cloud provider to not steal or tamper with your data anymore, you *just* have to trust the hardware. In practice, don’t forget about defense in depth & co 😉
04.02.2025 07:03 — 👍 10 🔁 5 💬 1 📌 0

Abstract. The Fiat-Shamir (FS) transform is a prolific and powerful technique for compiling public-coin interactive protocols into non-interactive ones. Roughly speaking, the idea is to replace the random coins of the verifier with the evaluations of a complex hash function.
The FS transform is known to be sound in the random oracle model (i.e., when the hash function is modeled as a totally random function). However, when instantiating the random oracle using a concrete hash function, there are examples of protocols in which the transformation is not sound. So far all of these examples have been contrived protocols that were specifically designed to fail.
In this work we show such an attack for a standard and popular interactive succinct argument, based on the GKR protocol, for verifying the correctness of a non-determinstic bounded-depth computation. For every choice of FS hash function, we show that a corresponding instantiation of this protocol, which was been widely studied in the literature and used also in practice, is not (adaptively) sound when compiled with the FS transform. Specifically, we construct an explicit circuit for which we can generate an accepting proof for a false statement.
We further extend our attack and show that for every circuit C and desired output y, we can construct a functionally equivalent circuit C^(*), for which we can produce an accepting proof that C^(*) outputs y (regardless of whether or not this statement is true). This demonstrates that any security guarantee (if such exists) would have to depend on the specific implementation of the circuit C, rather than just its functionality.
Lastly, we also demonstrate versions of the attack that violate non-adaptive soundness of the protocol – that is, we generate an attacking circuit that is independent of the underlying cryptographic objects. However, these versions are either less practical (as the attacking circuit has very large depth) or make some additional (reasonable) assumptions on the underlying cryptographic primitives.

Image showing part 2 of abstract.
How to Prove False Statements: Practical Attacks on Fiat-Shamir (Dmitry Khovratovich, Ron D. Rothblum, Lev Soukhanov) ia.cr/2025/118
27.01.2025 01:58 — 👍 38 🔁 17 💬 0 📌 6
Awesome! 👏 Is there any chance you will release some code for the threshold variant in the future?
07.12.2024 08:59 — 👍 1 🔁 0 💬 1 📌 0

Very excited to share our first exploration of threshold MAYO (yes, the PQC algorithm)! 🎉 Joint work with the amazing
Daniel Escudero and Guilhem Niot. The ideas can extend to UOV as well—let’s have MV-based threshold cryptography!
📄 eprint.iacr.org/2024/1960.pdf
06.12.2024 16:34 — 👍 21 🔁 8 💬 1 📌 0
Researcher at CNRS. Feminist. I work on microarchitectural security.
https://cmaurice.fr
Researcher in Cryptography (symmetric-key, white-box, post-quantum, etc.)
https://affine.group
Security reporter for WIRED Magazine. she/her/my man. Signal +1 (347) 722-1347
Applied cryptographer. Mainly working in the cryptography auditing industry, but sometimes venturing back into academia. Hobbyist puzzle game author. https://nadim.computer
PhD, Post-Quantum cryptography.
https://error0024.github.io/
Share my learning journey in the field of Blockchain, Crypto and Web3. Security Engineer at taurushq.com
See my blog https://rya-sge.github.io/access-denied
Professor at DTU Compute. Passionate about Cryptography, Hummus and coffee.
Professor in Information Security at UCL
Alumnus of EPFL and University of Passau
https://philippjovanovic.com/
Cryptographer who likes to implement multi-party computation and works for CSIRO's Data61. Views my own. 🏳️🌈🇨🇭🇦🇺 (he/him)
https://cryptologie.net/ | founder of @zksecurity.bsky.social | research advisor ArchetypeVC | author of Real-World Cryptography | Previously architect for Mina (at O(1) Labs), security lead for Libra (at Facebook), cryptography services at NCC Group
Cryptographic & Security Engineering
www.fredericjacobs.com
https://ger.mx/A-RGsldmQt0iXfnzPgXNzLzA5_jvDbWHabqz1yJrt2ma#did:plc:oxwmqopgbm3driwzues7odpz
Cryptographer @ NTU Singapore
drawing cryptographers, one talk at a time
Security Engineer interested in cryptography, information security, & privacy engineering.
Proud LatinAmerican. "Legendary quantum lady/cryptographer". Researcher @brave she/they hrpc co-chair @inretafo anti-fraud @w3c @otr_im @LondonU
Founder of Azeria Labs, Trainer, Author of Blue Fox: Arm Assembly Internals & Reverse Engineering
cryptography • neuro • cloud • biscuits
ORD-DCA-NYC-BCN ✈️
kennwhite@mastodon.social
Cryptography, privacy, zero knowledge, Rust, Zcash dev, gaming, hardware hackery, art appreciation. He/him.
https://str4d.xyz
https://abyssdomain.expert/@str4d
age18f63qx4gk8x7p4lfuwwglqcan7snvp406q5vmk26g9fmpe9c799qqzzr3w
applied cryptographer - certified nerd god - head of cryptography & research at duokey - founder modulo p - ex-Snap - co-founder ex-strong.codes - has-been professor - trail runner - aidjolat












