
Just below the creators?:)
Have you played the bg railroad ink?
I think that would be cool to introduce some random patterns challenge for the level “if you build a snake pattern get 100 extra points” or smth🤷♂️
@error024.bsky.social
PhD, Post-Quantum cryptography. https://error0024.github.io/

Just below the creators?:)
Have you played the bg railroad ink?
I think that would be cool to introduce some random patterns challenge for the level “if you build a snake pattern get 100 extra points” or smth🤷♂️

Come be part of Cedarcrypt, our historic new initiative to grow cryptography research, development and representation in the Levant region!
We're seeking speakers and workshop leaders: our call for submissions is open! Learn more: cedarcrypt.org
Please spread the word!




Stumbled upon some art from one of my favorite childhood cartoons: Treasure Planet. What a great adaptation of Treasure Island. Should go rewatch it.
31.01.2026 12:55 — 👍 0 🔁 0 💬 0 📌 0
Abstract. In this work, we initiate the study of aborting hash functions, i.e., hash functions that may abort on a non-negligible fraction of inputs. We introduce the aborting random oracle model (aROM), an idealized framework that extends the standard random oracle model (ROM) to account for aborts. Within this model, we derive bounds for various security notions and establish generic indifferentiability results demonstrating how to construct aborting random oracles from standard ones. Consequently, the derived bounds ultimately hold in the standard ROM. In this way, the aROM and its associated bounds provide a convenient and easy-to-use framework for analyzing cryptographic constructions that rely on potentially aborting hash functions. To illustrate the utility of our framework, we apply our techniques to two settings: (1) the analysis of SNARK-friendly incomparable hypercube encodings, a core primitive in hash-based signature schemes, and (2) the analysis of grinding in Fiat–Shamir-based non-interactive arguments. Through our generic indifferentiability results, we can easily translate these analyses into concrete security bounds in the standard (non-aborting) random oracle model.

Image showing part 2 of abstract.
Aborting Random Oracles: How to Build them, How to Use them (Gottfried Herold, Dmitry Khovratovich, Mikhail Kudinov, Stefano Tessaro, Benedikt Wagner) ia.cr/2026/016
09.01.2026 02:47 — 👍 2 🔁 2 💬 0 📌 0
keymaterial.net/2025/12/13/a...
Sophie Schmieg’s “very unscientific guide” to PQC security provides a nice summary of the security of PQ schemes. I am not sure if I would personally put Codes below the Lattices, but I am also not an expert in Codes.

NEW EPISODE!
The IACR lost the keys to decrypt their encrypted election results. We welcome Matt Bernhard who works on secure voting systems to explain which Helios bits are homomorphically additive or not and more:
securitycryptographywhatever.com/2025/12/30/i...
www.youtube.com/watch?v=euw_...
 31.12.2025 11:05 — 👍 0 🔁 0 💬 0 📌 0
31.12.2025 11:05 — 👍 0 🔁 0 💬 0 📌 0
 27.12.2025 21:45 — 👍 1 🔁 0 💬 0 📌 0
27.12.2025 21:45 — 👍 1 🔁 0 💬 0 📌 0

AsiaCrypt Afterparty 🌊
14.12.2025 07:59 — 👍 6 🔁 1 💬 0 📌 0Interesting read
lawrencecpaulson.github.io//2025/12/05/...

More ties between Durov and Russia:
The FT says Telegram founder invited Jan Marsalek to invest in Telegram’s TON crypto. Marsalek now wanted in Europe for large-scale fraud and identified as an agent who coordinated Russian espionage operations in Europe.
“Mr. Freedom of speech”
Should we add a vote for the best talk award for the iacr conferences? Gives a bit more motivation for the speakers to polish their talks.
11.12.2025 01:22 — 👍 0 🔁 0 💬 0 📌 0
Will be giving a talk today at AsiaCrypt 2025 in Melbourne, come see!
Did you know you can use salts as short as 72 bits for hash-and-sign?
We’ll be sharing our results on the security of hash functions in the QROM, including new tools for working in the QROM and tight bounds for M-eTCR.
We take a look at hash-based schemes, and how they fit in Bitcoin. The paper gives a broad overview of different schemes, including SPHINCS+ and several recent modification. For readers seeking a gentle introduction to hash-based schemes, we hope this work offers a helpful starting point.
09.12.2025 00:22 — 👍 4 🔁 1 💬 0 📌 0Thought HB schemes were running out of surprises, but new ideas keep coming. We recently looked at the “At the Top of the Hypercube” encoding for faster Winternitz-style verification, and now Abri & Katz show new optimizations for few-time signatures eprint.iacr.org/2025/2069! Still room to improve!
13.11.2025 11:55 — 👍 1 🔁 0 💬 0 📌 0
🎓 After 4 years, 7 papers, countless joyful moments, and meeting so many great people along the way, I’m excited to share that I’ve officially obtained my PhD!
It’s been an incredible journey of learning, persistence, and growth.
My thesis is now available here:
🔗 pure.tue.nl/ws/portalfil...
Delete twitter from the phone. So you only get there from you computer (if you even need that)
09.10.2025 12:21 — 👍 0 🔁 0 💬 1 📌 0We are alarmed by reports that Germany is on the verge of a catastrophic about-face, reversing its longstanding and principled opposition to the EU’s Chat Control proposal which, if passed, could spell the end of the right to privacy in Europe. signal.org/blog/pdfs/ge...
03.10.2025 16:14 — 👍 3976 🔁 2409 💬 40 📌 141I’m flagging this nice book/paper on FHE schemes not necessarily because it’s correct and I endorse it, but because it looks pretty useful. arxiv.org/pdf/2503.05136
22.09.2025 19:21 — 👍 27 🔁 4 💬 1 📌 0
CryptoCorgi
20.09.2025 20:22 — 👍 2 🔁 0 💬 0 📌 0Some can always find a way to communicate and get uncensored information. But the goal is to disconnect the general audience from accessing independent news. It is important to fight censorship not for your own access, but for those who won’t fight.
18.09.2025 18:09 — 👍 1 🔁 0 💬 0 📌 0I get mine from news.zksecurity.com :)
And zkmesh.substack.com

EU Chat Control criticized by 500 cryptographers over privacy risks
Over 500 cryptographers warn the EU draft “Chat Control” could weaken end‑to‑end encryption. The EU council votes on the Danish text on Sep 12, 2025. https://getnews.me/eu-chat-control-criticized-by-500-cryptographers-over-privacy-risks/ #euchatcontrol #privacy #cryptography
09.09.2025 11:37 — 👍 3 🔁 3 💬 0 📌 0Will there be a recording?
25.08.2025 17:27 — 👍 0 🔁 0 💬 1 📌 0That is wild! I am envious of your students; that is top-level material!
06.08.2025 18:19 — 👍 1 🔁 0 💬 0 📌 0I'm thrilled to announce that after months of intensive work, the complete materials for my Applied Cryptography course at the American University of Beirut are now finished: both Part 1 (Provable Security) and Part 2 (Real-World Cryptography)!
06.08.2025 08:01 — 👍 32 🔁 9 💬 4 📌 1
I made a video about my upcoming applied cryptography course: youtu.be/z6kK7rIbyB0
28.07.2025 08:51 — 👍 23 🔁 3 💬 3 📌 0 26.07.2025 20:56 — 👍 2 🔁 0 💬 0 📌 0
26.07.2025 20:56 — 👍 2 🔁 0 💬 0 📌 0
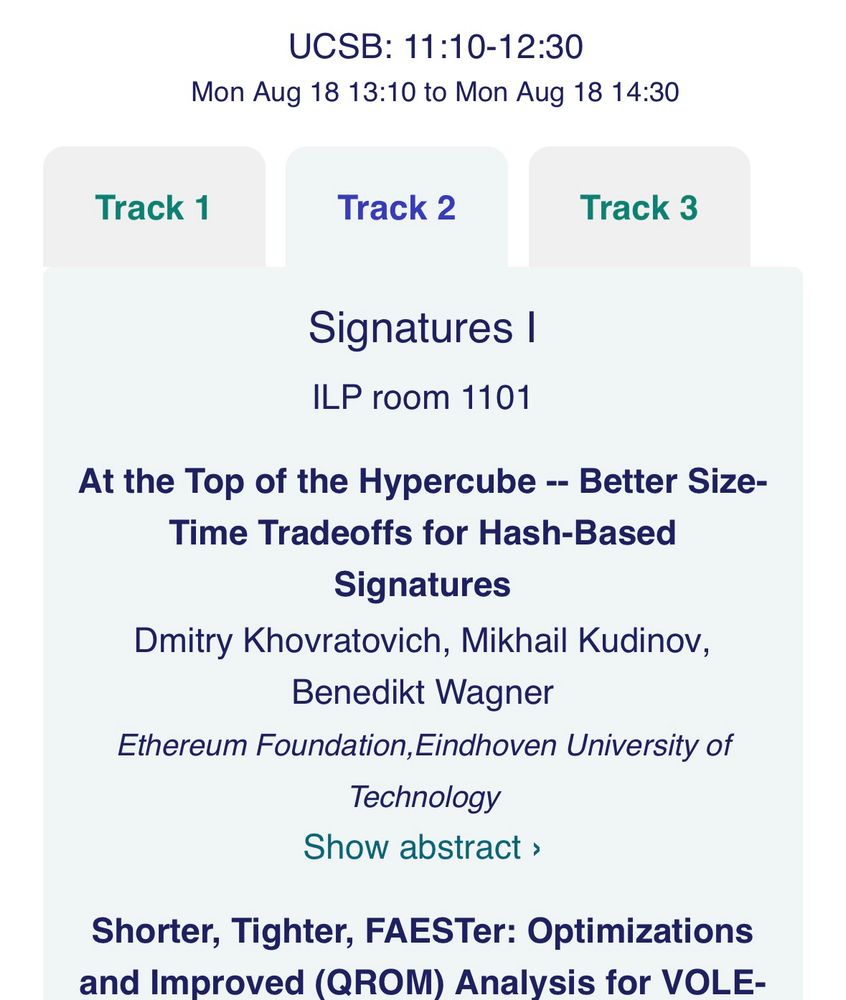
Crypto 2025 is just around the corner! Check out the full program here:
crypto.iacr.org/2025/program...
Join us on Monday for our talk where we explore the tradeoffs of hash-based signatures.
We then apply these findings to propose post-quantum Ethereum PoS signatures:
eprint.iacr.org/2025/1332