oss-security - CVE-2025-32463: sudo local privilege escalation via chroot option
"CVE-2025-32463: sudo local privilege escalation via chroot option"
An attacker can leverage sudo's -R (--chroot) option to run
arbitrary commands as root, even if they are not listed in the sudoers file.
Sudo versions 1.9.14 to 1.9.17 affected.
www.openwall.com/lists/oss-se... #infosec #cve
02.07.2025 07:40 — 👍 0 🔁 0 💬 0 📌 0
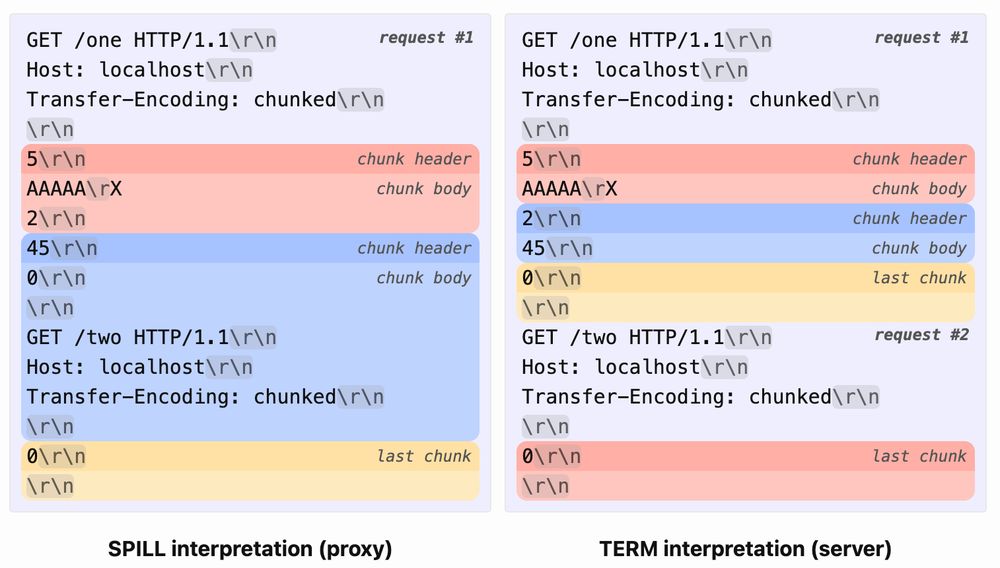
"Funky chunks: abusing ambiguous chunk line terminators for request smuggling"
w4ke.info/2025/06/18/f... #infosec
19.06.2025 08:44 — 👍 0 🔁 0 💬 0 📌 0
Getting RCE on Monero forums with wrapwrap
breakpoint of no return
"Getting RCE on Monero forums with wrapwrap"
Cool finding. This would make a cool CTF challenge 👍
swap.gs/posts/monero... #rce #ctf
12.06.2025 18:04 — 👍 0 🔁 0 💬 0 📌 0
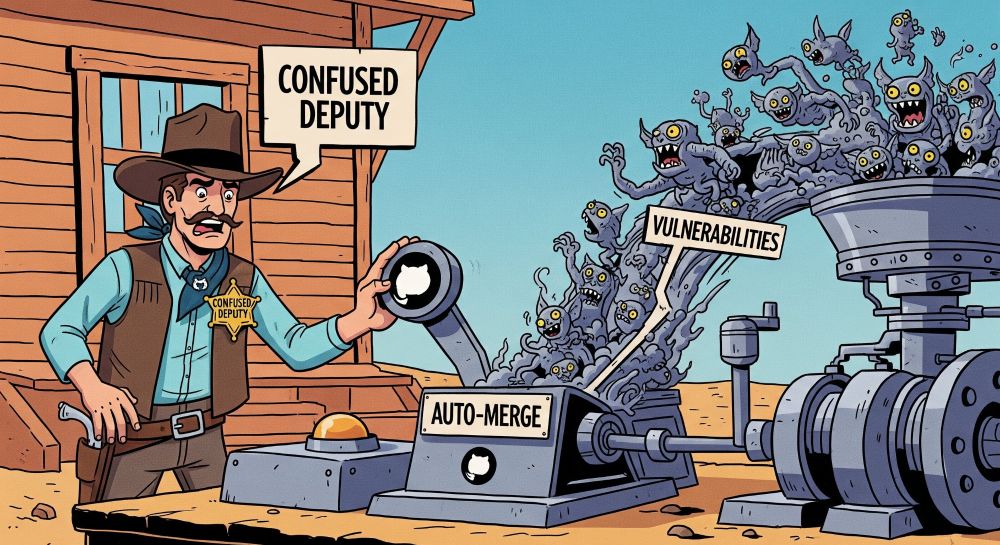
Weaponizing Dependabot: Pwn Request at its finest
Learn how Dependabot can be co-opted to exploit some sensitive workflows, through the Confused Deputy Problem and branch name injections.
"Weaponizing Dependabot: Pwn Request at its finest"
TL;DR: Through "Confused Deputy" attacks Dependabot (and other GitHub bots), can be tricked into merging malicious code. It can escalate to full command injection via crafted branch names.
boostsecurity.io/blog/weaponi... #infosec
06.06.2025 17:34 — 👍 0 🔁 0 💬 0 📌 0
Root Shell on Credit Card Terminal
"Root Shell on Credit Card Terminal"
stefan-gloor.ch/yomani-hack #infosec #re #reverseengineering
04.06.2025 07:51 — 👍 0 🔁 0 💬 0 📌 0
Part 2 - From Reverse ... | ADMinions
Introduction
In this guide, we’ll walk step-by-step through building a fully functional internal che...
"From Reverse Engineering to Cheat Development: Internal Game Hacks with AssaultCube"
Bit outdated (DirectX9) but still some very valuable info and a great writeup 👍
adminions.ca/books/articl... #infosec #re
29.05.2025 07:55 — 👍 0 🔁 0 💬 0 📌 0
cve-2025-26817 netwrix rce
Authenticated Remote Code Execution Vulnerability in Netwrix Password Secure
"Authenticated Remote Code Execution in Netwrix Password Secure (CVE-2025-26817)"
That will make a nice CTF challenge ^
www.8com.de/cyber-securi... #infosec #cve #rce
28.05.2025 08:21 — 👍 0 🔁 0 💬 0 📌 0
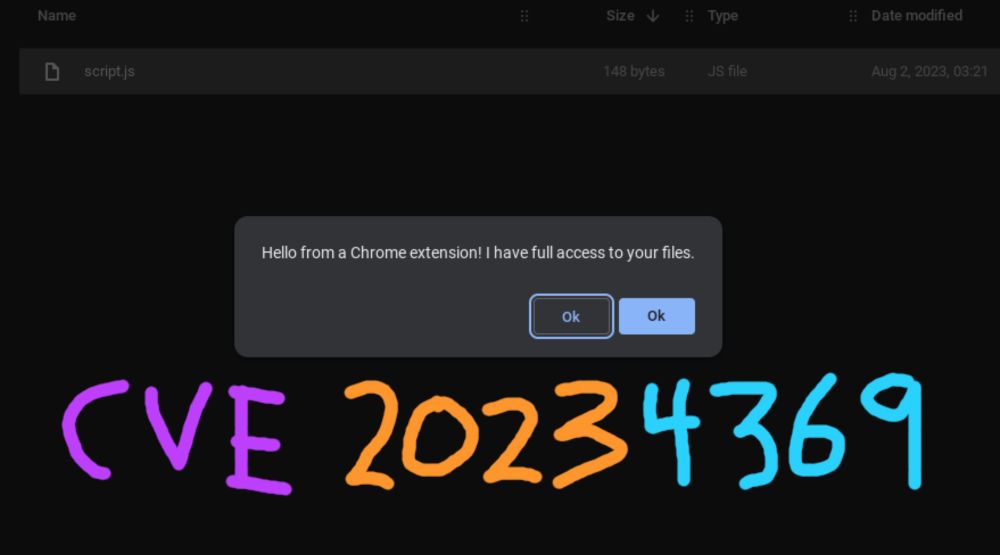
Uncovering a crazy privilege escalation from Chrome extensions
What's the worst thing a Chrome extension could do to you?
"Uncovering a crazy privilege escalation from Chrome extensions - CVE-2023-4369" (2023)
0x44.xyz/blog/cve-202... #infosec #cve #privesc
28.05.2025 08:18 — 👍 0 🔁 0 💬 0 📌 0
"Compromising Real-WorldLLM-Integrated Applications with Indirect Prompt Injection"
arxiv.org/pdf/2302.12173
21.05.2025 15:34 — 👍 0 🔁 0 💬 0 📌 0

Google's Approach for Secure AI Agents
"An Introduction to Google's Approach for Secure AI Agents"
research.google/pubs/an-intr... #infosec
21.05.2025 09:18 — 👍 0 🔁 0 💬 0 📌 0
Go Cryptography Security Audit
Go's cryptography libraries underwent an audit by Trail of Bits. Read more about the scope and results.
Three Trail of Bits engineers audited core Go cryptography for a month and found only one low-sev security issue... in unsupported Go+BoringCrypto! 🍾
Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆
19.05.2025 19:07 — 👍 580 🔁 85 💬 15 📌 4

"Dolla dolla bill, y'all" - Reverse engineering a banknote validator.
something.fromnothing.blog/posts/dolla-... #infosec #reverseengineering
19.05.2025 08:28 — 👍 0 🔁 0 💬 0 📌 0
Prodaft CATALYST
"Skitnet(Bossnet) Malware Analysis"
catalyst.prodaft.com/public/repor... #infosec #malware
19.05.2025 08:13 — 👍 0 🔁 0 💬 0 📌 0

Commit Stomping
Manipulating Git Histories to Obscure the Truth
"Commit Stomping: Manipulating Git Histories to Obscure the Truth"
blog.zsec.uk/commit-stomp... #infosec #redteam
19.05.2025 08:11 — 👍 0 🔁 0 💬 0 📌 0
Stateful Connection With Spoofed Source IP — NetImpostor
Overview
"Stateful Connection With Spoofed Source IP — NetImpostor"
Tl;Dr: Writeup reviews the technique for establishing a full stateful TCP connection with a spoofed source IP address from the same subnet using ARP poisoning.
tastypepperoni.medium.com/stateful-con... #infosec
18.05.2025 09:12 — 👍 0 🔁 0 💬 0 📌 0
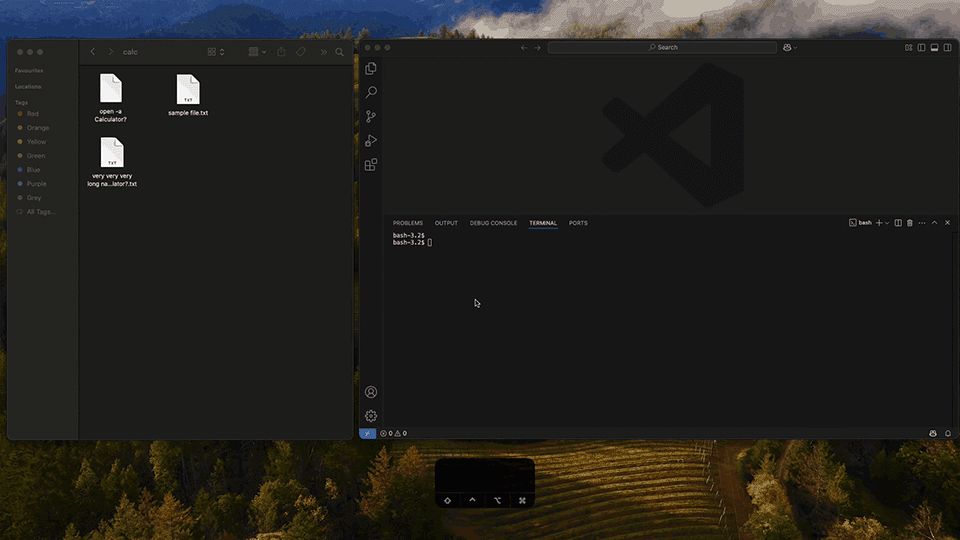
"Drag and Pwnd: Leverage ASCII characters to exploit VS Code"
portswigger.net/research/dra...
14.05.2025 08:38 — 👍 0 🔁 0 💬 0 📌 0
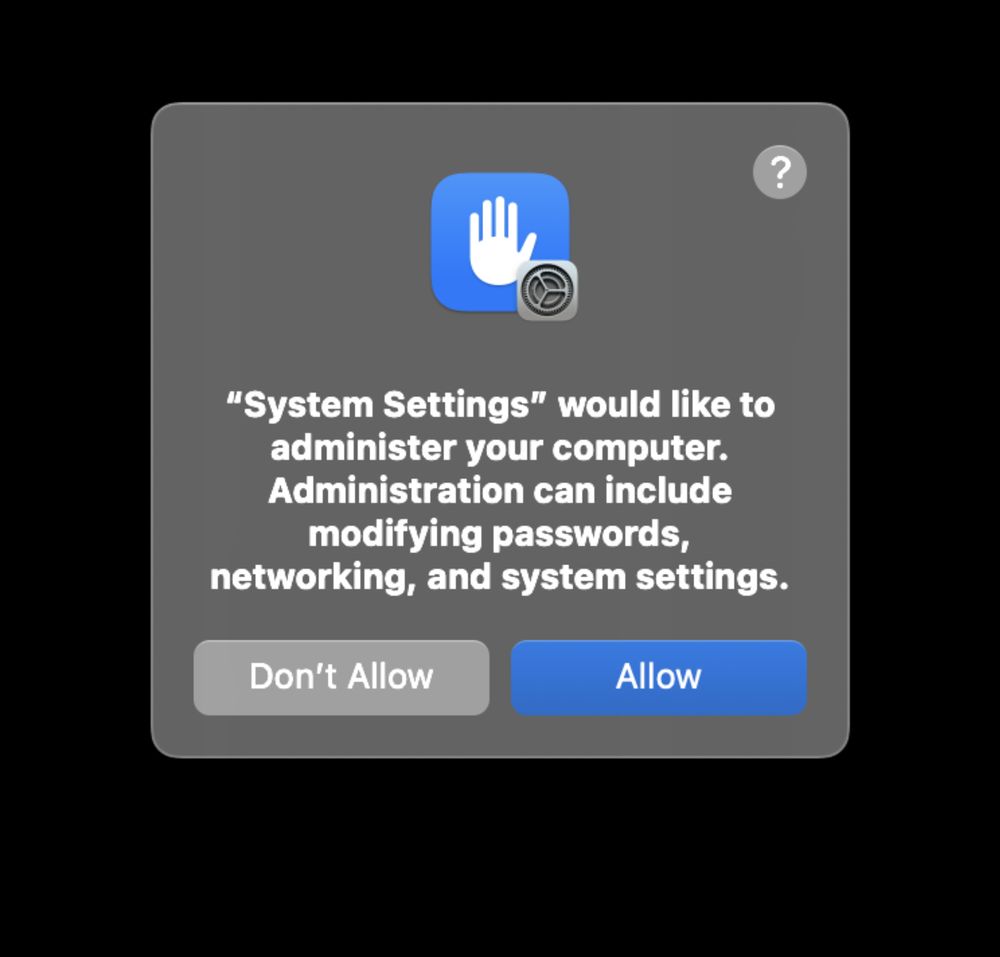
Can You Really Trust That Permission Pop-Up On macOS? (CVE-2025-31250) | Watch This Space
A security research blog.
CVE-2025-31250 - Great research and vulnerability write-up on the MacOS permission pop-up. It's time for Apple to make improvement to the terrible UX here.
"Can you trust that permission pop-up on macOS?" - wts.dev/posts/tcc-who/
13.05.2025 09:45 — 👍 0 🔁 0 💬 0 📌 0
Trouble maker, insolent and a pain in the neck. Into distributed-systems. Mostly-retired DJ. Triathlete-wannabe. 🇵🇹
reverse engineering, cryptography, exploits, hardware, file formats, and generally giving computers a hard time
Fedi: @retr0id@retr0.id
Macroblog: https://www.da.vidbuchanan.co.uk/blog/
Neovim is a hyperextensible Vim-based text editor
Ways to support the project:
- https://github.com/sponsors/neovim
- https://store.neovim.io
- Have fun using it and spread the word
Principal Training Architect @ HackTheBox
CTF Addict
"Potentially a legit researcher"
he/him
Website: https://0xdf.gitlab.io/
YouTube: https://www.youtube.com/c/0xdf0xdf
Twitter: 0xdf_
Discord: 0xdf
Mastadon: 0xdf@infosec.exchange
The largest collection of malware source code, samples, and papers on the internet.
Password: infected
(unofficial, this is a bot! Maintained by @yjb.bsky.social, the bot can't handle retweets, video, and maybe a few other things)
Hardware / software necromancer
collector of Weird Stuff
maker of Death Generators.
she/they
Global Bug Bounty & VDP Platform - #YesWeRHackers
🔗 http://yeswehack.com/programs (Public programs)
🔍 http://firebounty.com (BB & VDP search engine)
#BugBounty
SIG Security Chair kubernetes.io
container escape artist
goose in the mainframe
Minneapolis. They/them.
Founder of Azeria Labs, Trainer, Author of Blue Fox: Arm Assembly Internals & Reverse Engineering
RC F'13, F2'17
Cryptogopher / Go cryptography maintainer
Professional open source maintainer
https://filippo.io / https://github.com/FiloSottile
https://mkcert.dev / https://age-encryption.org
https://sunlight.dev / https://filippo.io/newsletter
programming and exclamation marks
I have DMs muted from people I don’t follow.
[bridged from https://social.jvns.ca/@b0rk on the fediverse by https://fed.brid.gy/ ]
I like juggling, Bash, chess puzzles, and good exploits. Worked on Metasploit for some years. 💙💜🩷
@egypt@mastodon.social
Security Engineer @ XTX. MSc in eng. physics & CompSci, dev & gamer. ❤️ music & long distance running. Wanna do a PhD sometime. Same U/N on all other sites
security, for the internet, at Wiz
opinionated about security.
knowledge hubs at rami.wiki, thoughts at ramimac.me
Cloud Threat Detection @google. Kubernetes SRC & Containerd Security Advisor.
security enthusiast that loves hunting for bugs in the wild. co-founder and player of @justCatTheFish.
infosec at @google. opinions are mine.
From: https://twitter.com/terjanq
Security Researcher @ Datadog. 🐶 Head in the (Azure) clouds.
Sometimes blogging, always curious. Aim to be, rather than to seem.
Blogs at https://kknowl.es.
Creator of Detection Engineering Weekly (https://detectionengineering.net), Sec Research/Intel/Detection @ Datadog