🫡
27.06.2025 16:15 — 👍 2 🔁 1 💬 0 📌 0@alexhevans.bsky.social
@alexhevans.bsky.social
🫡
27.06.2025 16:15 — 👍 2 🔁 1 💬 0 📌 0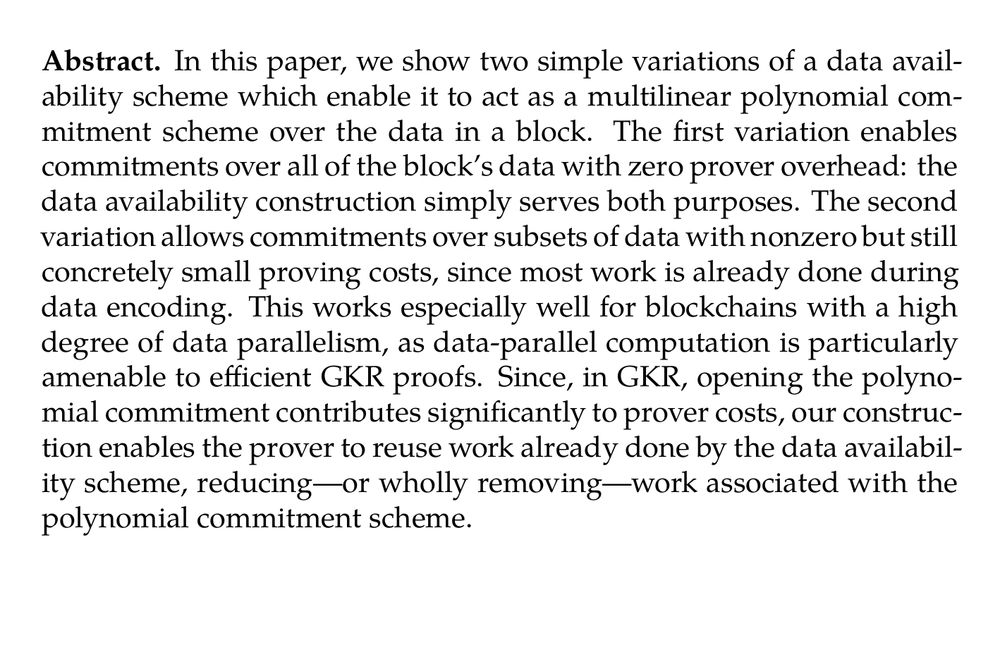
Abstract. In this paper, we show two simple variations of a data availability scheme which enable it to act as a multilinear polynomial commitment scheme over the data in a block. The first variation enables commitments over all of the block’s data with zero prover overhead: the data availability construction simply serves both purposes. The second variation allows commitments over subsets of data with nonzero but still concretely small proving costs, since most work is already done during data encoding. This works especially well for blockchains with a high degree of data parallelism, as data-parallel computation is particularly amenable to efficient GKR proofs. Since, in GKR, opening the polynomial commitment contributes significantly to prover costs, our construction enables the prover to reuse work already done by the data availability scheme, reducing—or wholly removing—work associated with the polynomial commitment scheme.
The Accidental Computer: Polynomial Commitments from Data Availability (Alex Evans, Guillermo Angeris) ia.cr/2025/918
23.05.2025 02:41 — 👍 2 🔁 1 💬 0 📌 1
Very informal experimentation with combining two worlds I like ☺️
www.notion.so/Verifiable-...
2/2

Some thoughts about how verifications in Bluesky can be extended to ZK-based methods, to achieve Verifiable Verifications
This builds on ideas from the recent verification protocol, and explores both direct integrations and lightweight ones, with different points in the tradeoff space of trust
1/2
🧵 The AT Protocol shows the power of a personal data store. All of our public atproto data is easy to find and access. We can interact with it flexibly in myriad ways and combinations.
Wouldn't it be nice to do the same for our private and collaborative data? 👇
The last of @grjte.sh’s Groundmist experiments, combining #localfirst with ATProto
Private, local first sync that is user centric using Lexicons, rather than app-specific sync.
ZK provers on mobile?
some thoughts on what needs to change to uphold the security guarantees we work so hard to get
tl;dr - the deployment supply chain, at least, should be better
www.kobi.one/The-Lies-Our...
🧵 The AT Protocol (atproto), which underlies Bluesky, lets us to interface with the same data in as many ways as we can conceive of through AppViews that each provide a different "view" of the network.
Can we make our local-first software as interoperable as the AT Protocol? 👇
Second in the #groundmist series - #localfirst + ATProto
I’m actively using the local first essay editor (using @inkandswitch.com Automerge + tiny essay editor) - I can login with my ATProto account and work on private drafts and then publish to @whtwnd.com.
🧵 I've been experimenting with combining local-first software and the AT Protocol (atproto) to play with the design space of apps that live at both ends of the privacy spectrum - maximally private AND maximally public, without some of the downsides of the modern web.
Why? 👇

When Andrija and @lmao.bsky.social told me they're writing an extremely fast cryptography library in Julia I didn't know what to think...
And then they showed me the following cool stuff:
baincapitalcrypto.com/releasing-c...
1/4
friendly reminder that building on atproto gives you immediate access to >30 million users, an existing social graph, and a huge network of open data & content
it's increasingly becoming a no-brainer to build new social apps on atproto
congrats to the skylight team on the launch 🙌
anon, what if you could train your own personal offline model, on your phone, suited to your tastes, filtering posts with ~ bad vibes ~ and letting good ones through?
well, have i got the thing for you
15 weeks ago I sat down and wrote up some ideas about how custom feeds could become a high-leverage mechanism for fundamentally changing the economics of the attention economy.
Today was my last day at my day job- I’m now full time @graze.social! Incredibly excited to give this all I got!

This week's ZK Podcast episode was on ZODA & The Accidental Computer from @baincapitalcrypto.com research team, with the trio @alexhevans.bsky.social @guilleangeris.bsky.social @nicomnbl.bsky.social chatting with @arro.bsky.social about these innovations.
Ep: https://zeroknowledge.fm/podcast/349/

ZK Whiteboard Sessions - S2M7: FRI and Proximity Proofs (Part.1) with @danboneh.bsky.social
https://youtu.be/MBDBrEr2XQg?feature=shared ☝️
ZK Whiteboard Sessions - S2M8: FRI and Proximity Proofs (Part.2) with @danboneh.bsky.social
https://youtu.be/CWbx_rnj7LI?feature=shared ✌️
it's funny, for a long time, i always assumed that computation was this very sacred, brittle, difficult thing: so many things need to work "exactly" right to get an output
but i’ve realized that it’s actually much *harder* to make a thing that doesn't accidentally enable ~ arbitrary computation!
These two lectures by @danboneh.bsky.social for @zkhack.bsky.social are the best explanation of IOPPs, FRI and its variants by a country mile. Cannot recommend them enough
zkhack.dev/whiteboard/s...
zkhack.dev/whiteboard/s...
ZK Whiteboard Sessions - S2M2: The Sum-Check Protocol with Justin Thaler
https://youtu.be/gfy8rotcas4?feature=shared
programmable* cryptography
* programming difficulty may vary, developer discretion is advised.

Abstract. The Fiat-Shamir (FS) transform is a prolific and powerful technique for compiling public-coin interactive protocols into non-interactive ones. Roughly speaking, the idea is to replace the random coins of the verifier with the evaluations of a complex hash function. The FS transform is known to be sound in the random oracle model (i.e., when the hash function is modeled as a totally random function). However, when instantiating the random oracle using a concrete hash function, there are examples of protocols in which the transformation is not sound. So far all of these examples have been contrived protocols that were specifically designed to fail. In this work we show such an attack for a standard and popular interactive succinct argument, based on the GKR protocol, for verifying the correctness of a non-determinstic bounded-depth computation. For every choice of FS hash function, we show that a corresponding instantiation of this protocol, which was been widely studied in the literature and used also in practice, is not (adaptively) sound when compiled with the FS transform. Specifically, we construct an explicit circuit for which we can generate an accepting proof for a false statement. We further extend our attack and show that for every circuit C and desired output y, we can construct a functionally equivalent circuit C^(*), for which we can produce an accepting proof that C^(*) outputs y (regardless of whether or not this statement is true). This demonstrates that any security guarantee (if such exists) would have to depend on the specific implementation of the circuit C, rather than just its functionality. Lastly, we also demonstrate versions of the attack that violate non-adaptive soundness of the protocol – that is, we generate an attacking circuit that is independent of the underlying cryptographic objects. However, these versions are either less practical (as the attacking circuit has very large depth) or make some additional (reasonable) assumptions on the underlying cryptographic primitives.

Image showing part 2 of abstract.
How to Prove False Statements: Practical Attacks on Fiat-Shamir (Dmitry Khovratovich, Ron D. Rothblum, Lev Soukhanov) ia.cr/2025/118
27.01.2025 01:58 — 👍 38 🔁 17 💬 0 📌 6
ZK Whiteboard Sessions - S2M1: What is Zero Knowledge (like, actually)? with
David Wong
https://youtu.be/ksTTyt0GTvQ?feature=shared
oh hello @zkhack.bsky.social 👀👀
23.01.2025 00:58 — 👍 3 🔁 1 💬 2 📌 0



Welcome Mark Fiorentino to BCV!
As Matt Harris writes, Mark is constantly learning w/ a career+life trajectory powered by changes, pivots & the quest for new experiences (ask him about being a Sommelier or upcoming CrossFit competitions).
baincapitalventures.com/insight/mark... #fintech #SaaS #AI

ZODA w/ @alexhevans.bsky.social and @nicomnbl.bsky.social : now up on eprint!
(with a few updates and smol changes to the appendix)
Cool checking out @graze.social -- ability to generate, share, (one day monetize?) your own type of feed.
I wonder when we'll have dynamic, prompted LLM-style feeds. Aka say "make me smarter, show me things that are funnier" and the feed will be curated as such
this is a great writeup on the differences between atproto & activity pub
it also highlights the most meaningful ways to make bluesky more resilient
Maybe the most interesting DeFi research in recent years
01.01.2025 00:20 — 👍 4 🔁 2 💬 0 📌 0
Everyone on the X is too distracted with immigration, so I’m giving a sneak peek of some research here
Decentralized Perpetuals have long been the dream but they’ve been too capital inefficient
Many advances pushed DEX-CEX market share to >6% — but how are how are they related?
We answer this!
if someone tells you “succinct proofs are too short to leak information about the witness”, please send them this. The ZK property is not just a cool acronym.
baincapitalcrypto.com/chosen-insta...
This was also the theme of the "Zeitgeist" puzzle at ZK Hack 5!