Are you ready to pivot?!
Come to Malaga on May 8-10, 2024!
#PIVOTcon24 is crafted to bring together professionals from diverse backgrounds – private sector, government, law enforcement, military, academics, and investigative journalists.
#ThreatIntel #CTI
14.12.2023 14:10 —
👍 9
🔁 7
💬 1
📌 1

Sneak preview of my #cyberwarcon slides 👀
03.11.2023 00:10 —
👍 5
🔁 0
💬 0
📌 0

"You compile me. You had me at RomCom" - When cybercrime met espionage"
Get ready for a #CYBERWARCON talk full of romantic comedy memes!
www.cyberwarcon.com/you-compile-...
06.10.2023 17:33 —
👍 3
🔁 1
💬 0
📌 0
That’s the only one I’ve seen so far
06.07.2023 21:41 —
👍 2
🔁 0
💬 0
📌 0
Notable Storm-0875 tradecraft (cont’d)
4. Multiple methods of persistence (RMM deployment, remote access internet facing RDP, identity provider federation, golden saml, VMs spun up in victim cloud infrastructure)
5. Generally shy away from deployment of backdoors
6. Social engineering
06.07.2023 12:58 —
👍 1
🔁 0
💬 1
📌 0
Notable Storm-0875 tradecraft
1. Initial Access: Sms phishing + AITM or purchase infostealer logs (bypasses most defenses)
2. Privilege escalation via SIM swapping or call number forwarding global admin’s personal phone
3. Time from initial access to global admin often occurs within hours
06.07.2023 12:56 —
👍 4
🔁 1
💬 1
📌 0

IMO: Storm-0875 (overlaps UNC3944/Scattered Spider) is the most dangerous financial threat actor right now
Some recent developments:
1. Now deploying ransomware (had been extorting orgs before)
2. In last few months targeting large/well known enterprises (not just telcos/help desk/crypto orgs)
06.07.2023 12:45 —
👍 8
🔁 5
💬 1
📌 2
Wouldn’t a middle ground be to require orgs to notify authorities if they pay an extortion and report the crypto wallet/address and any other pertinent identifiers (copy of ransom note, email addresses used…etc)
17.06.2023 21:16 —
👍 1
🔁 0
💬 1
📌 0
“Ransom deployment of a cl0p payload”
Thanks autocorrect
17.06.2023 21:14 —
👍 1
🔁 0
💬 0
📌 0
Clop/Lace Tempest operates in two modes
1) traditional enterprise compromise/priv esc (using backdoors like truebot), data exfil, and random deployment of a clip ransom payload
2) broad exploitation of file transfer software that leads to data extortion only
They stop doing #1 when focused on #2
17.06.2023 21:14 —
👍 1
🔁 0
💬 2
📌 0
if i was a FVEY CI officer, my first thought on a RU-based company publishing on FSB ops wouldn’t be “look at the analytic freedom!” — it would be “why is the FSB comfortable with the world knowing about this now? did they figure out we were onto it in some way?”
16.06.2023 21:22 —
👍 2
🔁 2
💬 1
📌 0
I’ve been in touch w/different victims of MOVEit exploitation by Lace Tempest. One thing orgs should be prepared for is initial $ demand that is (in some cases) order of magnitude or more than a typical org would pay (relative to size of payment in other ransom/extortion cases)
15.06.2023 01:14 —
👍 0
🔁 0
💬 0
📌 0
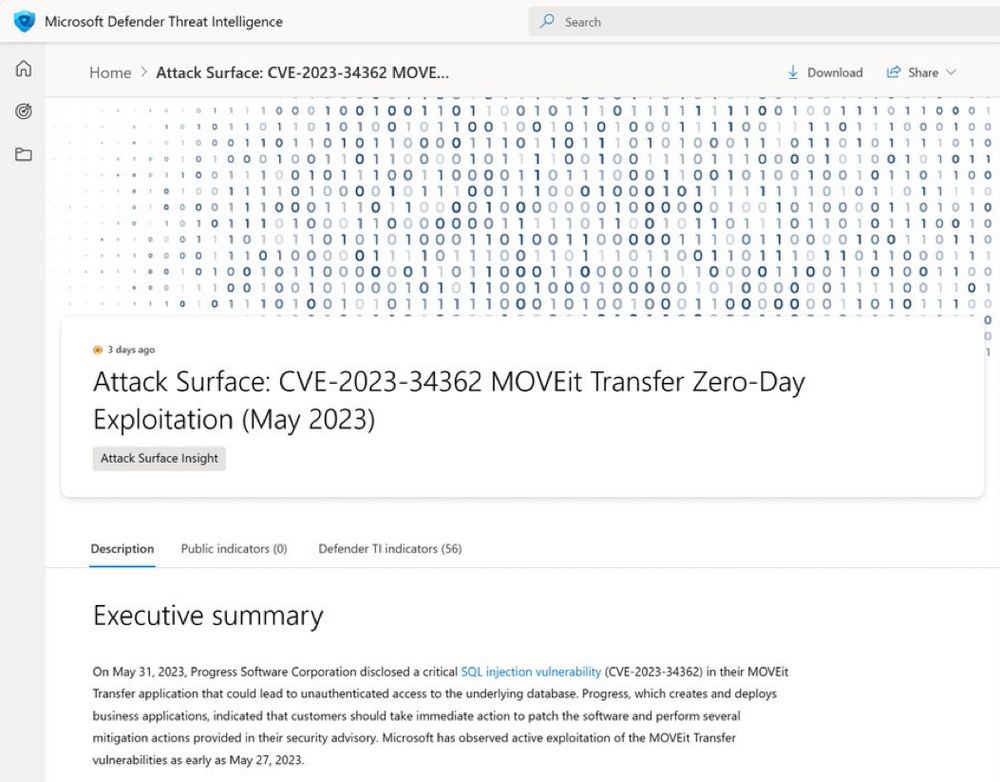
Attribution update from MSTIC on MOVEit Transfer 0-day exploitation by Lace Tempest. Victims w/ data theft are likely to be extorted via the cl0p leak site in coming weeks
We’ve shared intel on dozens of exfil IP addresses used in attacks w/customers & industry partners
15.06.2023 01:13 —
👍 1
🔁 0
💬 0
📌 1




