YouTube video by Virtual Routes
This was Binding Hook Live!
🙌 This was Binding Hook Live — a day filled with incredible conversations and discussions on and off stage. Read more insights from Binding Hook Live by our Managing Editors James Shires and @maxwsmeets.bsky.social: bindinghook.com/insights-fro...
🎞️ youtu.be/MOr-eZ_IJfo?...
12.11.2025 08:49 — 👍 3 🔁 2 💬 0 📌 0
🚨 #BindingHookLive tickets are going fast! 🚨 A little over a month to go until the very first Binding Hook Live! Don't miss the chance to be part of this one-of-a-kind event featuring a fantastic line-up of expert speakers. 🎟️ Request your invite: bindinghooklive.com
24.09.2025 08:38 — 👍 5 🔁 2 💬 0 📌 0

AI over Lunch: Manfred Boudreaux-Dehmer
Welcome to AI over Lunch, our new interview series exploring how leaders across sectors are grappling with the opportunities and risks of artificial intelligence.
💭 Introducing #AI over Lunch - a new interview series exploring how leaders across sectors are grappling with the opportunities and risks of artificial intelligence. Read the first interview with #NATO CIO Manfred Boudreaux-Dehmer: virtual-routes.org/ai-over-lunc...
04.09.2025 08:43 — 👍 4 🔁 2 💬 0 📌 0
Where is #AI really shaping #ransomware – and where is it just hype? Join experts Ciaran Martin, Jamie MacColl, Will Thomas, Taylor Grossman & Max Smeets as they discuss AI’s role in ransomware. 📅 To join, register as a member: docs.google.com/forms/d/e/1F...
21.08.2025 13:11 — 👍 1 🔁 3 💬 1 📌 0

Is the Ransomware Trust Paradox Breaking?
And, is that a good thing?
I've been thinking a lot about @maxwsmeets.bsky.social Ransomware Trust Paradox and how I think it's breaking. My analysis below (btw: if you haven't you should buy Max's book).
20.08.2025 14:18 — 👍 8 🔁 4 💬 0 📌 0
Expert commentary on tech and security - Binding Hook
Original, insightful analysis on digital and emerging technologies and security
With more writers joining and more readers returning, we felt it was time for a better space. Our new @bindinghook.bsky.social website is now live! bindinghook.com
19.08.2025 08:28 — 👍 2 🔁 0 💬 0 📌 0
New from me: China has been ramping up its public attribution against Taiwan, likely in an attempt to shift the conversation on cyber intrusions and pressure the island and they're using their private sector cybersecurity companies to do it. Read the piece, but a few highlights, take aways in this 🧵
22.07.2025 18:38 — 👍 8 🔁 5 💬 1 📌 0

Time to ditch the AI arms race analogy
You don’t need AI to beat AI. Most threats still fail in the face of ordinary, well-applied defences
The increasingly popular narrative that #AIthreats need to be fought with #AIsecuritysolutions fall short upon closer inspection, argue @virtualroutes.bsky.social’s Jamie Collier and @maxwsmeets.bsky.social in their latest: bindinghook.com/articles-bin...
15.07.2025 07:33 — 👍 4 🔁 2 💬 0 📌 0
mailchi.mp/bindinghook....
30.06.2025 10:53 — 👍 0 🔁 0 💬 0 📌 0
YouTube video by Virtual Routes
Virtual Routes at CyCon 2025
Our #CyCon2025 #ransomware workshop, now in video! 🎞️ Watch the recap and join us for a quick trip back to Tallinn. 👇 @maxwsmeets.bsky.social @jamesshires.bsky.social www.youtube.com/watch?v=gb7G...
02.06.2025 12:11 — 👍 4 🔁 2 💬 0 📌 0

🎙️ The new episode of the @sansinstitute.bsky.social #CyberLeadersPodcast featuring @maxwsmeets.bsky.social is out now! Have a listen: sans.org/u/1Bxx
13.06.2025 13:08 — 👍 4 🔁 2 💬 0 📌 0
On Lawfare Daily, @jshermcyber.bsky.social and Jonathan Cedarbaum spoke to @maxwsmeets.bsky.social about his book “Ransom War,” the history of ransomware, how the threats have evolved, and some of the major drivers of innovation within the ecosystem. www.lawfaremedia.org/article/lawf...
26.06.2025 14:44 — 👍 10 🔁 2 💬 0 📌 0

bindinghooklive.com
31.05.2025 11:31 — 👍 3 🔁 0 💬 0 📌 0
Ransom War is now available as an audiobook! www.amazon.com/Ransom-War-B...
28.05.2025 08:46 — 👍 6 🔁 0 💬 0 📌 0

⏰ Hurry up - only 1️⃣ week left until the deadline! 📝 Submit your Lightning Talk proposal by May 31: bindinghooklive.com
24.05.2025 08:52 — 👍 3 🔁 1 💬 0 📌 0

Updates to our speakers list! Looking forward to the talks by Mattijs Dijkstra & Zawadi Done (@huntandhackett.com), @joshagoldstein.bsky.social (Georgetown's CSET), & @maxwsmeets.bsky.social (@virtualroutes.bsky.social + @ethz.ch). Registration closing 1 June: www.thehagueprogram.nl/the-hague-ti...
20.05.2025 08:36 — 👍 4 🔁 3 💬 0 📌 0
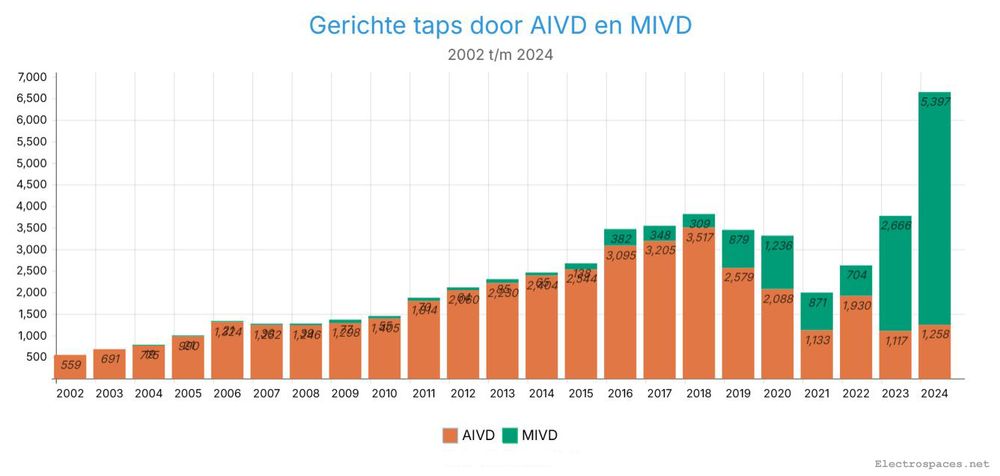
Het aantal gerichte taps door de #AIVD is de laatste 5 jaar aanzienlijk gedaald, daarentegen is het aantal taps door de #MIVD de afgelopen twee jaar geëxplodeerd:
20.05.2025 06:23 — 👍 4 🔁 2 💬 1 📌 1
The Hague Program: Hague TIX 2025 Welcome
Excited to be speaking at The Hague TIX this year. Great line up once again from @monicakello.bsky.social and team!
www.thehagueprogram.nl/the-hague-ti...
16.05.2025 18:10 — 👍 5 🔁 0 💬 0 📌 0
We are excited to launch a new program in the Netherlands. The goal is to give students hands-on experience in cybersecurity, with courses like malware reverse engineering, digital forensics, and ransomware economics.
14.05.2025 07:50 — 👍 19 🔁 7 💬 0 📌 0

Ransomware groups are not always out of reach
The arrest of a suspect after a spate of ransomware attacks in the Netherlands is an unusual win for law enforcement, but a more holistic approach is required.
The arrest of a suspect after a spate of #RansomwareAttacks in the Netherlands is an unusual win for law enforcement, but a more holistic approach is required. Read the new piece by @jamesshires.bsky.social and @maxwsmeets.bsky.social: bindinghook.com/articles-hoo...
14.05.2025 07:38 — 👍 5 🔁 2 💬 0 📌 0

Binding Hook Live
Binding Hook Live is a one-of-a-kind event bringing together leading voices in digital and emerging technologies and global affairs. This exclusive event takes place at the iconic Underbelly Boulevard...
⏳ 𝗦𝘂𝗯𝗺𝗶𝘁 𝘆𝗼𝘂𝗿 𝗟𝗶𝗴𝗵𝘁𝗻𝗶𝗻𝗴 𝗧𝗮𝗹𝗸 𝗳𝗼𝗿 𝗕𝗶𝗻𝗱𝗶𝗻𝗴 𝗛𝗼𝗼𝗸 𝗟𝗶𝘃𝗲 𝗯𝘆 𝗠𝗮𝘆 𝟯𝟭, 𝟮𝟬𝟮𝟱!
We're looking for talks on:
👉 Cyber & AI
👉 Surveillance
👉 Info ops
👉 Critical infra
👉 Cybercrime and more
✅ If accepted you’ll receive a 𝗳𝗿𝗲𝗲 𝘁𝗶𝗰𝗸𝗲𝘁 to the event and a £𝟱𝟬𝟬 𝗵𝗼𝗻𝗼𝗿𝗮𝗿𝗶𝘂𝗺.
📝 𝗦𝘂𝗯𝗺𝗶𝘁 𝘆𝗼𝘂𝗿 𝗽𝗿𝗼𝗽𝗼𝘀𝗮𝗹: bindinghooklive.com
13.05.2025 13:16 — 👍 2 🔁 3 💬 0 📌 0

Sowing the seeds of enhanced cybersecurity cooperation within the G7
Officials from the Italian National Cybersecurity Agency discuss the challenges and successes of creating the new G7 Cybersecurity Working Group
The G7 Cybersec Working Group has finally put nat cyber agencies in one room to align on critical infra and AI safeguards. Now let us see if a small task force can truly overcome the deep institutional silos that have long slowed collective cyber security/defense:
bindinghook.com/articles-hoo...
12.05.2025 07:52 — 👍 7 🔁 1 💬 0 📌 0

Binding Hook Live
Binding Hook Live is a one-of-a-kind event bringing together leading voices in digital and emerging technologies and global affairs. This exclusive event takes place at the iconic Underbelly Boulevard...
One month left to submit a proposal for a Lightning Talk at Binding Hook Live. 10-minute presentations that should fit the same editorial scope as Binding Hook. We are interested in how digital and emerging technologies shape security.
bindinghooklive.com
29.04.2025 05:12 — 👍 2 🔁 0 💬 0 📌 0

Published a new Pharos report today - and learned a lot in the process from @milenkowski.bsky.social Jiro, @julianferdinand.bsky.social @tgrossman.bsky.social. The report takes a closer look at how states are using ransomware.
virtual-routes.org/wp-content/u...
23.04.2025 20:19 — 👍 14 🔁 9 💬 1 📌 1
North Korea’s financially driven approach, embedding itself deep within the ecosystem, is also striking. And then there is Iran.. which may be the most versatile in its use. We found it harder to pin down, but much of it mirrors their hacktivist tactics with wipers, offering a similar kind of cover.
23.04.2025 20:19 — 👍 2 🔁 1 💬 0 📌 0
Prof at FGV Law School, heading CTS.FGV.br and CyberBRICS.info
Director of CPDP.lat
Personal Views
Minister van Defensie | VVD | Brabander | Minister of Defence of The Netherlands | Personal account
PhD Candidate & Consultant | digital policy and regulation - cyber risk, readiness and resilience
Butlerian jihadist. Cyber stuff sometimes. Writing stuff always. He/him.
Infosec bod, thinker of silly thoughts
Onderzoeksjournalist Volkskrant
Going dark
h.modderkolk at volkskrant.nl
Signal: hmodderkolk.20
Cyber Threat Intelligence at Microsoft | Former Yahoo & Secret Squirrel | Thoughts my own
Technologist @ Human Rights Watch (previously Amnesty, Citizen Lab)
Malware, Threats, Online Investigations, Disinformation, Human Rights and silly memes.
On Mastodon: tek@todon.eu
Also on https://maynier.eu/
We build software for cyber #threatintelligence analysts.
https://www.dogesec.com/
Pattern recognizer *Author: China’s Digital Colonialism, Diamond Model for Influence Operations * Public Speaker
Sharing information on malicious network traffic and malware samples at https://www.malware-traffic-analysis.net/
Head of Research and Discovery @Google Threat Intelligence. Leading multidisciplinary teams to defeat adversaries. Posts are attributable to me—not my employer.
Three Buddy Problem
https://securityconversations.com
I look for ICS threats, and spend a lot of time reverse engineering.
Distinguished Malware Analyst @ Dragos.
Lead Analyst on TRISIS and PIPEDREAM.
He/Him
All things cybersecurity, incident response, threat Intel, AI, and law. Founded @AdvancedCyberLaw.com after forever @MSFT. Host of @AdvancingCyber.com Podcast on Apple Podcast and Spotify. Mom to humans, dog, and cat. Seeks big mountains and lakes.
Interests include politics, cyber security, threat intelligence, wildlife conservation, history, and ice hockey. Here for information and stimulating conversation.
Now Google Threat Intelligence & doing fun things at DistrictCon, fmrly GreyNoiseIO and RecordedFuture, SAISHopkins MASCI alumna | ♡s & rts are my own, my employer definitely doesn’t like Taylor Swift that much
Senior security researcher and reverse engineer @Intezer
Principal Threat Researcher at Trend Micro





















