Fortunately, humans still learn to walk first, even though the car has been invented.
07.02.2026 22:19 — 👍 1 🔁 0 💬 0 📌 0Frycos
@frycos.bsky.social
Private account! Red teamer @codewhitesec. @frycos@infosec.exchange @frycos@X
@frycos.bsky.social
Private account! Red teamer @codewhitesec. @frycos@infosec.exchange @frycos@X
Fortunately, humans still learn to walk first, even though the car has been invented.
07.02.2026 22:19 — 👍 1 🔁 0 💬 0 📌 0Highly recommend the writeup from our @fl0mb.bsky.social and congrats on this well-deserved achievement!
05.02.2026 16:15 — 👍 4 🔁 3 💬 0 📌 0[RSS] [Blog] Unauthenticated RCE in NetSupport Manager - A Technical Deep Dive
code-white.com ->
CVE-2025-34164, CVE-2025-34165
Original->
Crazy work by my colleague Fabian. High impact target: one might be amazed at how widespread this product is in industrial networks.
23.01.2026 12:33 — 👍 3 🔁 2 💬 0 📌 0Medical 🫣
20.12.2025 12:40 — 👍 0 🔁 0 💬 0 📌 0
In 2025 my colleague and me pwned several widespread medial devices. Check our vuln list for some impressions and get ready for cool blog posts and hopefully conference talks in 2026. 🤞🏻
code-white.com/public-vulne...

Our 2024 applicants challenge is officially #roasted: the full BeanBeat × Maultaschenfabrikle walkthrough is now online. Unwrap the write-up at apply-if-you-can.com/walkthrough/... and revisit the hacks that escalated from cold brew to full breach.
05.12.2025 12:47 — 👍 6 🔁 6 💬 0 📌 0
Just sayin‘ 🤷
15.11.2025 08:57 — 👍 4 🔁 2 💬 0 📌 0A somewhat wild internal story from the last few weeks
29.10.2025 13:08 — 👍 0 🔁 0 💬 0 📌 0Did you encounter the Supabase? Might wanna try my newest tooling or have a read about quickwins? There you go:
blog.m1tz.com/posts/2025/1...
On your way to @brucon! Are you interested in technical discussions or would you like to know what makes our company so unique? Just talk to us.
24.09.2025 04:42 — 👍 3 🔁 1 💬 0 📌 0Tired of dull, standard interviews? Talk to Kurt. Also, a few of my colleagues and I will be attending BruCON next week. Feel free to come and talk to us.
15.09.2025 07:44 — 👍 6 🔁 1 💬 0 📌 0New AI-generated "technical" blog posts are stealing my time. 🤬
03.09.2025 07:35 — 👍 2 🔁 0 💬 0 📌 0Yes, there’s another phishing campaign contacting fediverse users to fill out a form to avoid being suspended or whatever. Stay calm and just report them and be sure to check the option to inform their home instance so the account gets suspended for everyone.
Also, please consider enabling […]

We always love a good challenge. That’s why we’re sponsoring the 10th FAUST CTF. Game on at 2025.faustctf.net
28.08.2025 12:22 — 👍 7 🔁 6 💬 0 📌 0Today I have a more serious topic than usual, please consider reposting for reach:
My wife and I are urgently looking for a specialist in neuropediatrics or a similar field for our autistic child with a diagnosed, but not further specified, movement disorder [1/4]

We've added a new demo to NewRemotingTricks that makes deploying a MarshalByRefObject (e.g., WebClient) even easier: System.Lazy<T> creates an instance of T on serialization, which is probably more likely to be allowed than a XAML gadget getting through. github.com/codewhitesec...
05.08.2025 15:11 — 👍 4 🔁 4 💬 0 📌 1Wow, I wrote with an author of a cool VR blog post yesterday. Just asked for some more explanations and maybe references. Tl;dr: he couldn’t explain or elaborate because exactly this part of the blog was written by GPT…
29.07.2025 06:08 — 👍 2 🔁 0 💬 0 📌 0
We have reproduced "ToolShell", the unauthenticated exploit chain for CVE-2025-49706 + CVE-2025-49704 used by @_l0gg (on X) to pop SharePoint at #Pwn2Own Berlin 2025, it's really just one request! Kudos to @mwulftange.bsky.social
14.07.2025 13:00 — 👍 4 🔁 5 💬 1 📌 1A quick-and-dirty late night blog post on discovering an nday variant in Zyxel NWA50AX Pro devices
frycos.github.io/vulns4free/2...
Oh no, it's a variant of CVE-2024-29974...I accidentally found that a similar vuln affected Zyxel NWA50AX (Pro) and tested against devices (obviously) lacking the latest patches. This CVE was never publicly related to NWA50AX, though. Well, nice nday exercise then.
16.06.2025 21:34 — 👍 4 🔁 0 💬 0 📌 0B03701066A0F762E75BAA67816EDB223F8681C9444C34E0B768DE518268025A0
Am I on vacation in the mountains? Yes. Do they have network equipment there? Yes. Can I refrain from doing VR? No.
You know the drill: disclosure and blog post planned. 😄
Yes, we're beating a dead horse. But that horse still runs in corporate networks - and quietly gives attackers the keys to the kingdom. We're publishing what’s long been exploitable. Time to talk about it. #DSM #Ivanti code-white.com/blog/ivanti-...
13.05.2025 06:45 — 👍 8 🔁 8 💬 0 📌 1If you are in the US and upset at the AfD being subject to more surveillance now:
The bar to be declared "in conflict with the democratic order" is *very* high. It is literally the AfD definition of "Germanness" by your ancestry, declaring ppl of other ancestries inferior, that did it, justifiedly.
My blog post on some vulns in GFI MailEssentials
frycos.github.io/vulns4free/2...

🧵 THREAD: A federal whistleblower just dropped one of the most disturbing cybersecurity disclosures I’ve ever read.
He's saying DOGE came in, data went out, and Russians started attempting logins with new valid DOGE passwords
Media's coverage wasn't detailed enough so I dug into his testimony:

That sums up my week's vacation pretty well. And I have to say, I like it.
16.04.2025 20:46 — 👍 2 🔁 0 💬 0 📌 0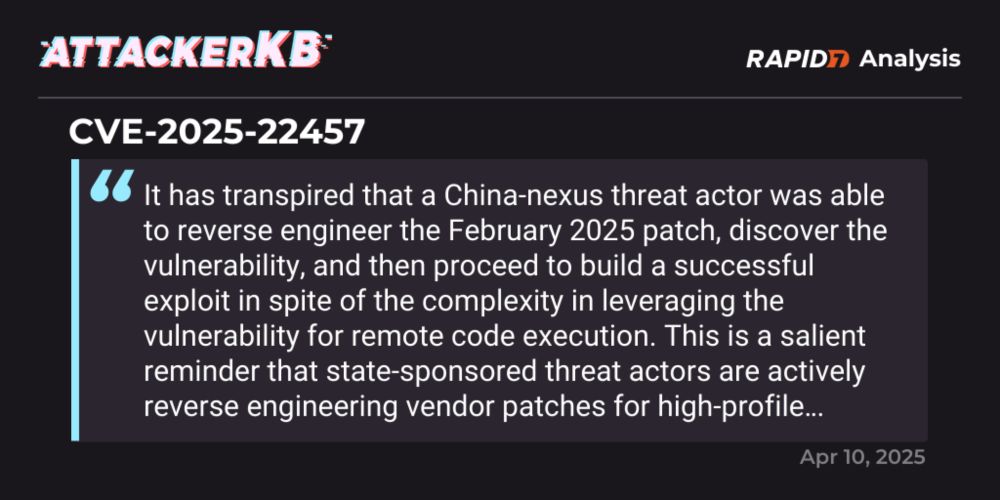
We have just published our AttackerKB @rapid7.com Analysis of CVE-2025-22457, an unauthenticated stack based buffer overflow in Ivanti Connect Secure. Difficult to exploit due to severe character restrictions, we detail our full RCE technique here: attackerkb.com/topics/0ybGQ...
10.04.2025 18:19 — 👍 3 🔁 4 💬 1 📌 0