The Shai-Hulud 2.0 npm worm: analysis, and what you need to know | Datadog Security Labs
Learn more about the Shai-Hulud 2.0 npm worm.
It was an interesting 72 hours tracking down the second wave of Shai Hulud campaign. It's more sophisticated and aggressive than the first one. We published all what we know about it here securitylabs.datadoghq.com/articles/sha... #npm #shaihulud #malware
26.11.2025 19:00 — 👍 3 🔁 0 💬 0 📌 0
I still didn't install bat yet but looks very good. I will do it now.
14.09.2025 08:08 — 👍 0 🔁 0 💬 0 📌 0
I'm in love with claude code. The way it handles code writing and automates bash tasks is amazing and so convenient to me.
if you are an experienced developer, know what you are doing, the tasks that usually take Weeks. You will be able to do it in Hours 🤯🤯 #claudecode #ai
13.09.2025 17:22 — 👍 2 🔁 1 💬 1 📌 0
Q for developers. Do you love/hate mandatory security training? And why?
#security #training #developers
17.06.2025 13:37 — 👍 0 🔁 0 💬 0 📌 0

The obfuscation game: MUT-9332 targets Solidity developers via malicious VS Code extensions | Datadog Security Labs
Analysis of a threat actor campaign targeting Solidity developers via three malicious VS Code extensions
🚨 The obfuscation game: MUT-9332 targets Solidity developers via malicious VS Code extensions!
Deep dive analysis in this obfuscated campaign including (PowerShell & VBS scripts, PE malware, Malicious browser extensions even stegomalware)
Enjoy reading securitylabs.datadoghq.com/articles/mut...
21.05.2025 12:10 — 👍 2 🔁 2 💬 0 📌 0
Pretty interesting threat campaign have been discovered by our research team.
We will be disclosing it in couple of hours , stay tuned 😉
#threats #malicious #security_research #datadog
21.05.2025 09:54 — 👍 1 🔁 0 💬 0 📌 0
Recognizing employees for a job well done is just as important as giving constructive feedback when they underperform. Balance builds growth. #Leadership #Feedback
15.05.2025 09:25 — 👍 0 🔁 0 💬 0 📌 0
I don't like threat actors attribution that much because in most cases it's wrong and so easily to be forged. We still should cluster campaigns but there is no "high confidence" attribution IMHO.
14.05.2025 18:44 — 👍 0 🔁 0 💬 0 📌 0
I have been told there will be a special announcement at 10am CET (that's 4am EDT btw) regarding this.
I will release the info I have at that time also. Thank you for the support.
16.04.2025 01:54 — 👍 32 🔁 7 💬 3 📌 1
Any idea what will happen to the CVE program after MITRE
x.com/0xTib3rius/s...
15.04.2025 20:07 — 👍 1 🔁 0 💬 0 📌 0

Picture of the tutorial room in Kubecon eu 2025
It’s the tutorial room at #kubecon where we’ll be hacking up a storm in just over 30 minutes!
04.04.2025 12:12 — 👍 19 🔁 1 💬 1 📌 0
I think it's time for me to start digging into AI and LLMs. I'm not sure where to start, any advice?
31.03.2025 20:42 — 👍 1 🔁 0 💬 0 📌 0
Seeing phrack magazine brings so much good memories. Good old days.
31.03.2025 20:36 — 👍 1 🔁 0 💬 0 📌 0
.:: Phrack Magazine ::.
Phrack staff website.
It's amazing how important one Phrack article from 27 years ago has been for web application security.
Covering what we now call SQL Injection and SSRF (amongst other things) problems we're still trying to handle today laid out in a couple of paragraphs
phrack.org/issues/54/8#...
27.03.2025 09:42 — 👍 62 🔁 13 💬 2 📌 0

The
Learn how the Kubernetes Ingress NGINX Controller vulnerabilities work, how to detect and remediate them.
Our analysis and takeaways for IngressNightmare - Several vulnerabilities in the Kubernetes Ingress NGINX Controller. Enjoy!
securitylabs.datadoghq.com/articles/ing...
25.03.2025 23:03 — 👍 0 🔁 0 💬 0 📌 0
I love it when some people tells me that's is your limit, this is your ceiling. This is when I feel fire within me reignite!
16.12.2024 08:58 — 👍 1 🔁 0 💬 0 📌 0
YouTube video by AWS Events
AWS re:Invent 2024 - Beyond just observing, protecting your whole software supply chain (SEC406)
Amazing presentation about supply chain security and the amazing work we do by our leaders @techy.detectionengineering.net
(Director of research) and Andrewkrug (Manager of advocacy) youtu.be/1b0RIi19qrw?...
09.12.2024 18:14 — 👍 2 🔁 0 💬 0 📌 0
Supply chain firewall in action
github.com/DataDog/supp...
06.12.2024 12:35 — 👍 1 🔁 0 💬 0 📌 0

Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages | Datadog Security Labs
Release of Supply-Chain Firewall, an open source tool for preventing the installation of malicious PyPI and npm packages
We are happy to introduce our latest tool "Supply Chain Firewall" 🎉 by @ikretz.bsky.social
The tool detects & prevents installation of malicious packages in local development environment.
Read more
securitylabs.datadoghq.com/articles/int...
And give it a try github.com/DataDog/supp...
06.12.2024 12:19 — 👍 11 🔁 7 💬 0 📌 0
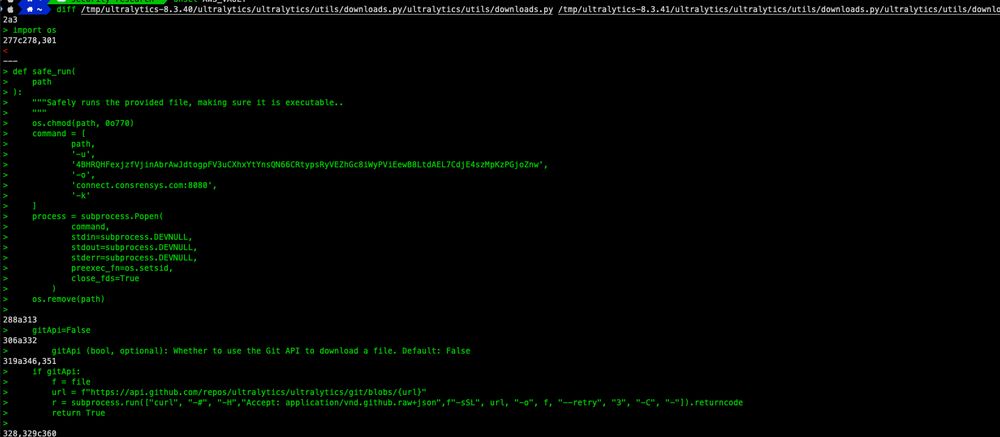
Supply-chain attack in the ultralytics PyPI package: github.com/ultralytics/...
An attacker opened a pull request and pushed a commit with a malicious name, leading to CI code injection.
They then backdoored versions 8.3.41 and 8.3.42 with code downloading a second-stage binary from GitHub
05.12.2024 17:12 — 👍 5 🔁 3 💬 1 📌 0
Awesome, Stratus Red Team v2.20.0 is now available 🎉
04.12.2024 17:52 — 👍 0 🔁 1 💬 0 📌 0

My Blackhat MEA arsenal presentation: "Detect Malicious Packages with Guarddog"
drive.google.com/file/d/11SAN...
03.12.2024 13:48 — 👍 4 🔁 4 💬 0 📌 0
Looks good, I will give it a try this weekend
28.11.2024 15:46 — 👍 2 🔁 0 💬 0 📌 0
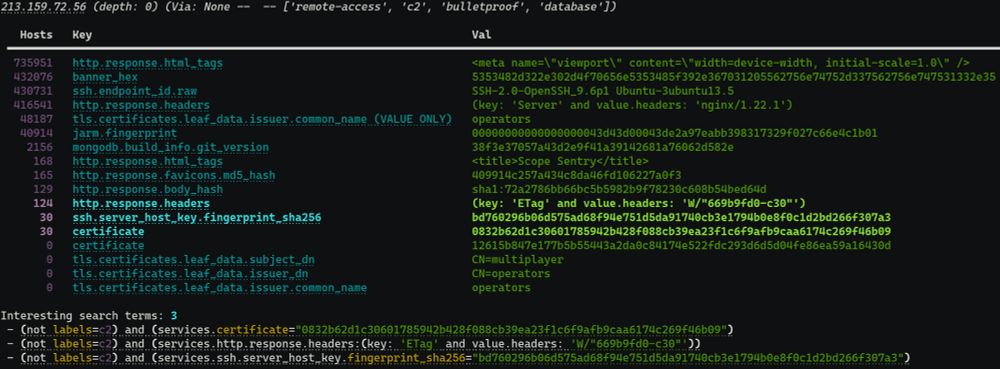
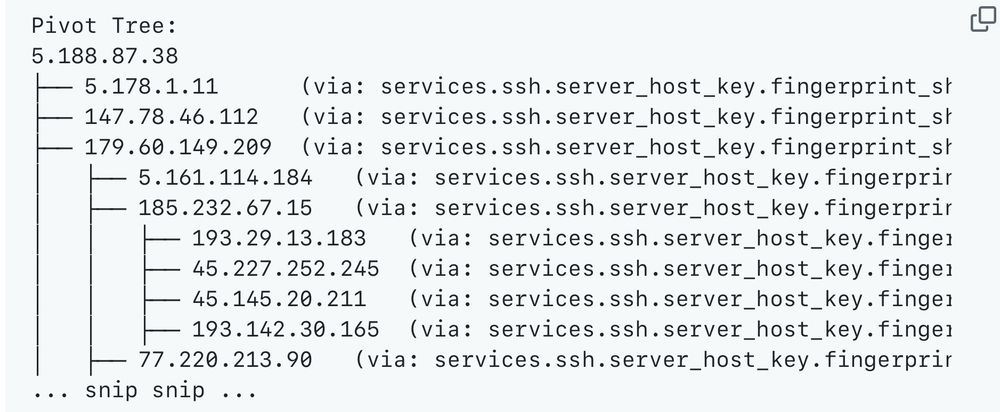
We released Censeye today, an open source CLI tool that makes it dramatically easier to pivot and find related assets when threat hunting on Censys instead of manually checking for potential identifying characteristics like an SSH host key. github.com/Censys-Resea...
27.11.2024 17:05 — 👍 28 🔁 14 💬 2 📌 1
Sometimes CTF. Frequently Pentesting. Claude code collaborator. Weight training 4/7.
Caveat sensum codi
incompetent computer user
https://cyberworm.uk/
https://codeberg.org/cyberworm-uk
https://github.com/cyberworm-uk
I like juggling, Bash, chess puzzles, and good exploits. Worked on Metasploit for some years. 💙💜🩷
@egypt@mastodon.social
AI-native software security maintenance (AutonomousPlane) * CTO/Founded (Slim dot AI) * Created DockerSlim / SlimToolkit / MinToolkit * 50 Shades of Golang * Big & Small Data * Security * eBPF * Containers * Cloud Native
Detection & Response Engineer. She/her. Currently Security Research @Datadog // Previously @Cloudflare @Brexhq
Software Supply Chain Red Team. SourceCodeRED & SecureStack founder, dad, startup OG, snowboarder and hacker. Workin on GitHax tool in my spare time. github.com/6mile
@eastsidemccarty from the bird site.
Security Research @ Datadog
For Future Reference.
Sign up for our newsletters: https://wrd.cm/newsletters
Find our WIRED journalists here: https://bsky.app/starter-pack/couts.bsky.social/3l6vez3xaus27
open source library engineer - Python - AppSec @ Datadog
Gardening, Brazilian Jiu Jitsu, and Cloud Security,
Founder/CTO of @chainguard.dev
Security Researcher @ Datadog
Mainly malware analysis and cloud security
AWS Pro | Cloud | Security @trek10.com | Tech enthusiast Musically trapped between a metallic headbang and a bass wobble | Photographer (bsky): @betapixels.photography
Read our Security Labs blog: https://securitylabs.datadoghq.com
Subscribe to our monthly newsletter: https://securitylabs.datadoghq.com/newsletters/
Internet Security, Trust, and Safety Researcher. Stanford CS Faculty, Censys Founder and Chief Scientist, ZMap Creator. https://zakird.com/
Penetration tester trying to perform novel research. You can find all of my write-ups and research at https://thomas.stacey.se.
Mandiant Intelligence at Google. CYBERWARCON and SLEUTHCON founder. Johns Hopkins professor. Army vet.
Writer for WIRED. Author of SANDWORM. Latest book, TRACERS IN THE DARK: The Global Hunt for the Crime Lords of Cryptocurrency, out now. agreenberg@wired.com. Andy.01 on Signal.
senior researcher at @citizenlab.ca