Gonna tell my kids this is the eras tour
04.08.2025 14:35 — 👍 0 🔁 0 💬 0 📌 0Andy Robbins
@andyrobbins.bsky.social
aka wald0
@andyrobbins.bsky.social
aka wald0
Gonna tell my kids this is the eras tour
04.08.2025 14:35 — 👍 0 🔁 0 💬 0 📌 0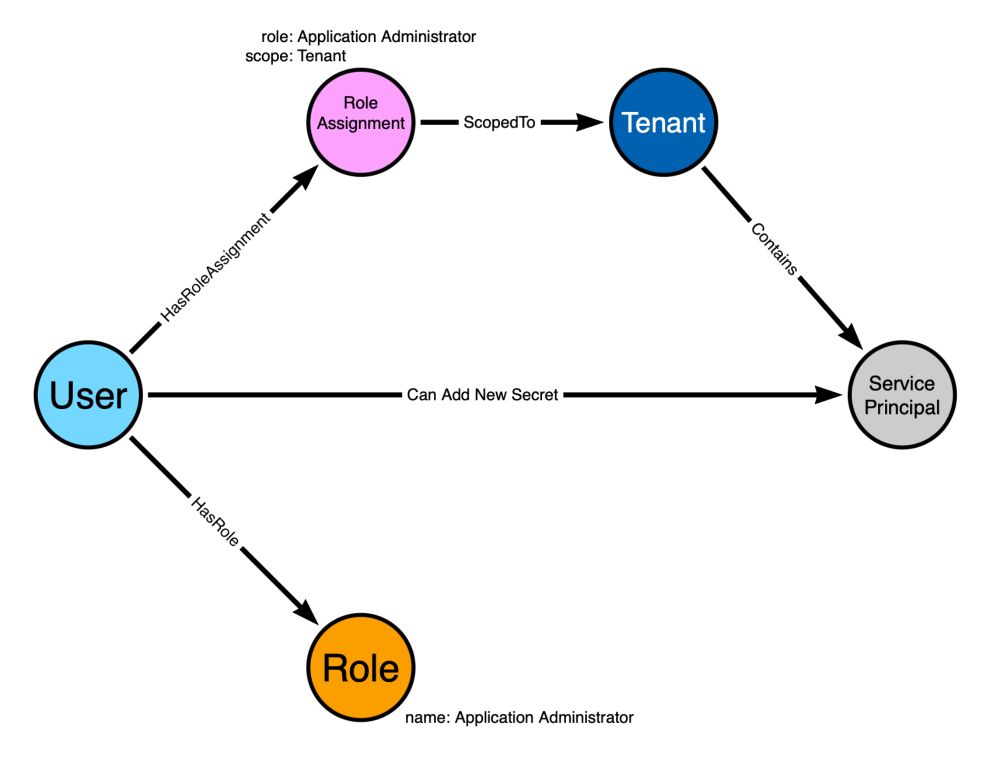
In this blog post I explain the fundamental building blocks, vocabulary, and principles of attack graph design for BloodHound: specterops.io/blog/2025/08...
01.08.2025 16:21 — 👍 4 🔁 0 💬 0 📌 1Drive safe
01.08.2025 01:22 — 👍 1 🔁 0 💬 0 📌 0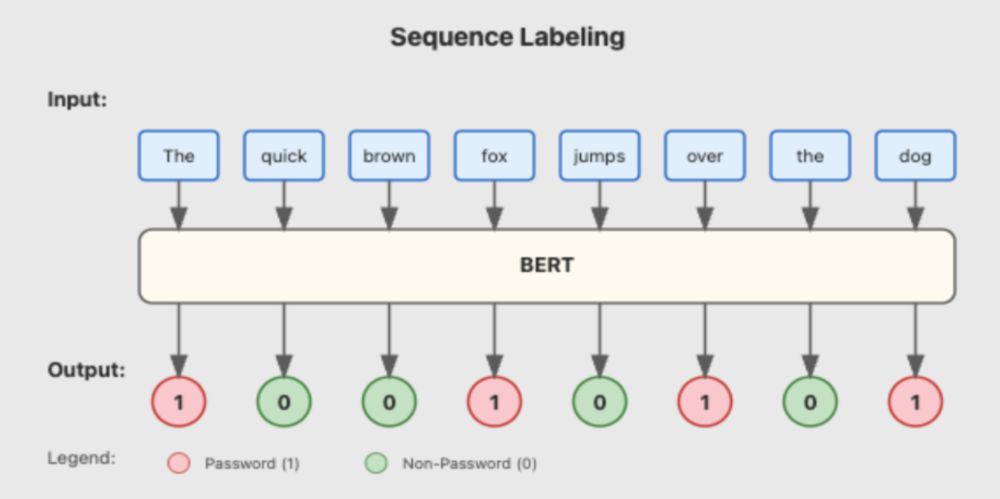
Red teamers know the drill: endless file churning, hunting for passwords & tokens. 🔍
Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA

Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass.
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
@egyp7.bsky.social Hey dude ✌️
30.07.2025 01:37 — 👍 0 🔁 0 💬 1 📌 0BloodHound v8.0 is here! 🎉
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
Great minds
21.07.2025 18:42 — 👍 0 🔁 0 💬 0 📌 0
Happy Friday! @tifkin.bsky.social and I are happy to announce that we have cut the release for Nemesis 2.0.0 - check out the CHANGELOG for a (brief) summary of changes, and dive into our new docs for more detail! We're extremely proud and excited for this release github.com/SpecterOps/N...
28.06.2025 04:14 — 👍 11 🔁 7 💬 0 📌 0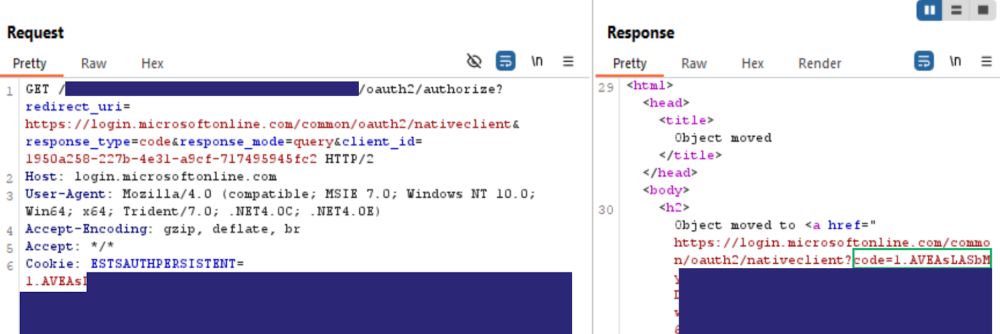
So you've compromised a host that isn’t cloud-joined. Antero Guy breaks down how to request OAuth tokens & enumerate an Entra ID tenant by using an SSO cookie from a non cloud-joined device.
Read more: ghst.ly/445tQKL
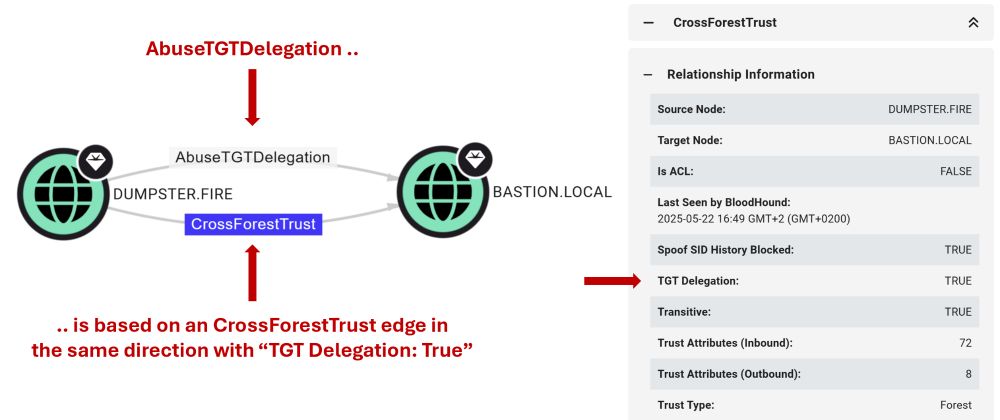
I publish two blog posts today! 📝🐫
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳

🕵️♀️ I'll be presenting "I SPy: Rethinking Entra ID research for new paths to Global Admin” at fwd:cloudsec June 30-July 1, alongside some fantastic other speakers: fwdcloudsec.org/conference/n...
If you can’t make it, talks are streamed at: www.youtube.com/@fwdcloudsec

New tricks, same impact
posts.specterops.io/update-dumpi...

Recently, Microsoft changed the way the Entra Connect Sync agent authenticates to Entra ID.
Check out our latest blog post from @hotnops.bsky.social to learn how the agent works now & how these changes affect attacker tradecraft. ghst.ly/3ZpMc6y
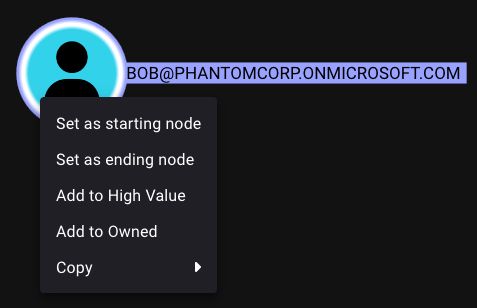
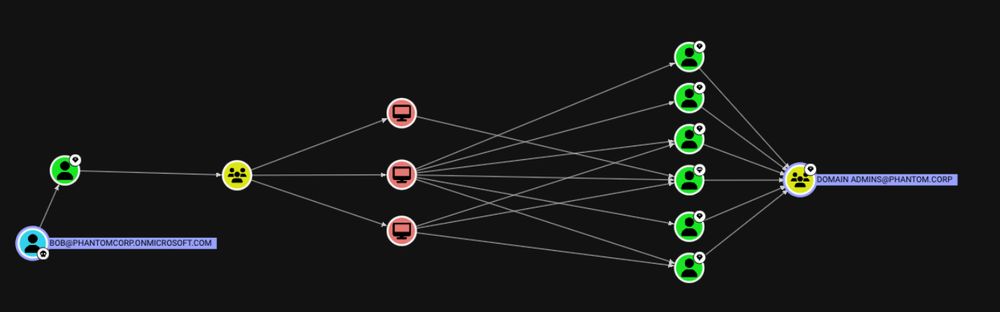
🚨 New #BloodHoundBasics courtesy of @scoubi.bsky.social!
You've successfully compromised Bob in marketing's account in an engagement. Mark it as Owned by right-clicking ➡️ "Add to Owned" ➡️ run the query "Shortest Paths from Owned objects to Tier Zero" & see your new attack paths!
(1/2)

Andy Robbins: The Evolution of Bloodhound podcasters.spotify.c...
27.05.2025 23:48 — 👍 7 🔁 3 💬 0 📌 0MATCH (c1:Computer)-[:MemberOf*1..]->(g:Group) WHERE g.objectsid ENDS WITH '-516' WITH COLLECT(c1[.]name) AS dcs MATCH (c2:Computer) WHERE c2.enabled = true AND (c2.operatingsystem contains '2025') AND (c2[.]name IN dcs) RETURN c2[.]name
If this query hits, you're DA: www.akamai.com/blog/securit...
This is why "y'all" is the best word. Friendly. Inclusive. Down-to-earth.
19.04.2025 19:39 — 👍 1 🔁 0 💬 0 📌 0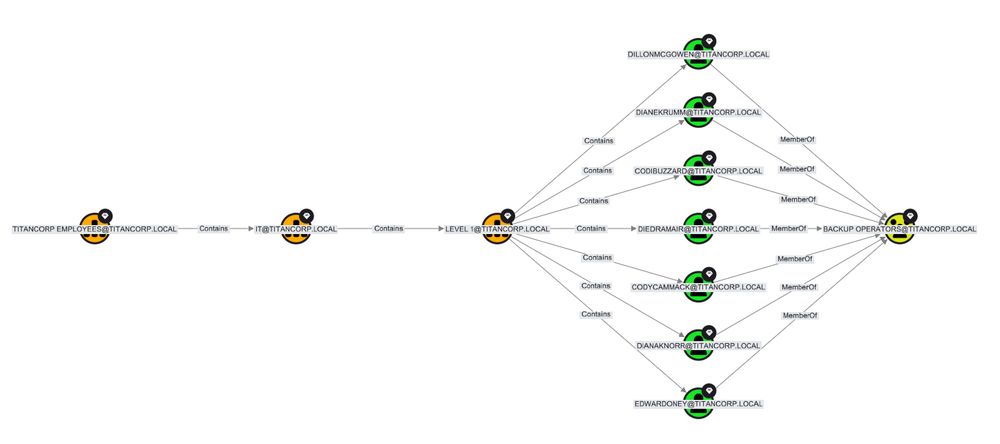
It's #BloodHoundBasics day!
Let's talk Tier 0 inheritance. If you're trying to unravel why some of the objects in your environment show up as Tier 0, this query will demonstrate the nuances of inheritance in 2 ways: inheritance up w/ OUs, & inheritance down w/ Groups.
🧵 1/3
hi
18.04.2025 16:07 — 👍 2 🔁 0 💬 0 📌 0"NTLM better stand for Nice Treats to be Licked by Me"
14.04.2025 23:24 — 👍 4 🔁 0 💬 0 📌 0We are BACK with another #BloodHoundBasics post, this week courtesy of @andyrobbins.bsky.social.
ICYMI: The BloodHound BACK button is BACK. Just use your browser's BACK button to go BACK. 🔙
There are trans Americans right now looking out at this world and wondering if anyone is going to stand up for them and for their simple right to exist.
Well, I am. We are. We will.

Excited to be at @specterops.bsky.social SO-CON this week!! If you're around, I'll be presenting "Abusing AUs, Confusing the SOC" tomorrow bright & early:
31.03.2025 14:39 — 👍 15 🔁 7 💬 1 📌 0👀
28.02.2025 01:03 — 👍 1 🔁 0 💬 1 📌 0
Introducing a new tool designed to help you install & manage BloodHound instances...🥁 BloodHound CLI!
Check out @printingprops.com's blog post to learn how this tool dramatically simplifies installation and server management. ghst.ly/40zXAxI
Thank you!
15.01.2025 21:15 — 👍 0 🔁 0 💬 0 📌 0Karl Madden (www.linkedin.com/in/karl-m-93...)
Corné de Jong (www.linkedin.com/in/corn%C3%A...)
Dr. Nestori Syynimaa (x.com/DrAzureAD)
Rudy Ooms (x.com/Mister_MDM)
With thanks and acknowledgement to:
Chris Thompson (x.com/_Mayyhem)
Dirk-jan Mollema (@dirkjanm.io)
Adam Chester (@xpnsec.com)
Brett Hawkins (@h4wkst3r.bsky.social)
Thibault Van Geluwe de Berlaere (www.linkedin.com/in/thibault-...)
(continues)
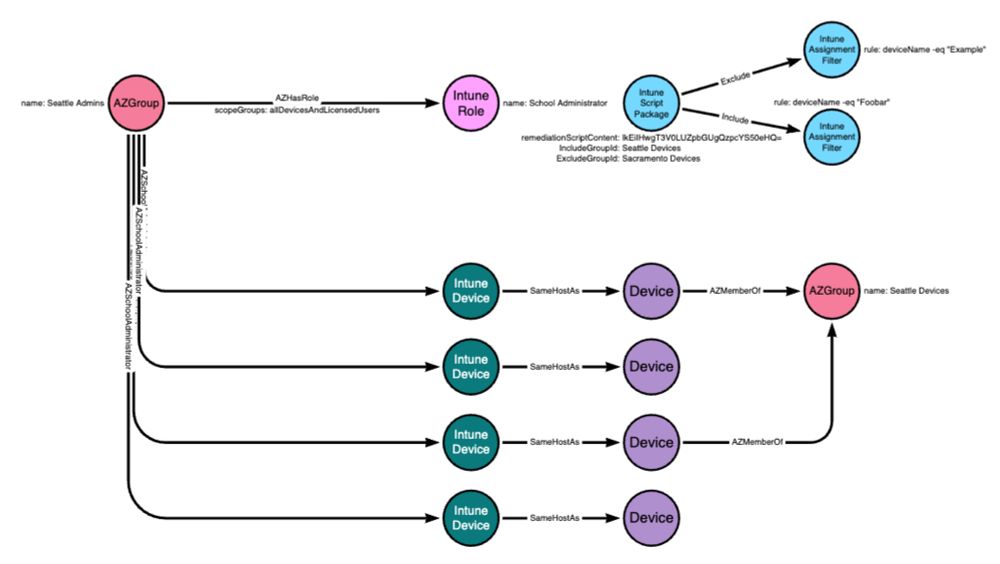
In Part 1 of my Intune Attack Paths series, I discuss the fundamental components and mechanics of Intune that lead to the emergence of attack paths: posts.specterops.io/intune-attac...
15.01.2025 17:33 — 👍 41 🔁 19 💬 2 📌 0