One the craziest elements about cybersecurity is you have half the industry sat worrying about cyberwar!1! and going on about quantum and AI, then you have you have the operational reality of what is actually happening on the ground - it bares no resemblance, at all, to what people are focused on.
01.10.2025 15:21 — 👍 247 🔁 36 💬 9 📌 1
Gebt den Sondierungen noch zwei Wochen und Markus Söder baut uns allen kiffend ne Wärmepumpe ein.
05.03.2025 13:44 — 👍 12033 🔁 2800 💬 369 📌 206
There are two wolves inside of you. If the first acquires lock A and the second acquires lock B, and then the first attempts to acquire lock B while the first attempts to acquire lock A, they will deadlock. Teach your wolves concurrency.
17.02.2025 05:58 — 👍 375 🔁 76 💬 12 📌 2

CVSS is dead to us
<p>CVSS is short for <a href="https://en.wikipedia.org/wiki/Common_Vulnerability_Scoring_System">Common Vulnerability Scoring System</a> and is according to Wikipedia <em>a technical standard for assessing the severity of vulnerabilities in computing systems</em>.</p>
<p>Typically you use an online CVSS calculator, click a few checkboxes and radio buttons and then you magically get a number from 0 to 10. There are also different versions of CVSS.</p>
<p>Every CVE filed to MITRE is supposed to have a CVSS score set. CVEs that are registered that lack this information will get “amended” by an ADP (Authorized Data Publishers) that think of it as their job. In the past NVD did this. Nowadays CISA does it. More on this below.</p>
<h2 class="wp-block-heading">Problems</h2>
<p>Let’s say you write a tool and library that make internet transfers. They are used literally everywhere, in countless environments and with an almost impossible number of different build combinations, target operating systems and CPU architectures. Let’s call it <a href="https://curl.se/">curl</a>.</p>
<p>When you find a theoretical security problem in this product (theoretical because most problems are never actually spotted exploited), how severe is it? The CVSS calculation has a limited set of input factors that tend to result in a fairly high number for a network product. What if we can guess that the problem is only used by a few or only affects an unusual platform? Not included.</p>
<p>The CVSS scoring is really designed for when you know exactly when and how the product is used and how an exploit of the flaw affects it. Then it <em>might </em>at least work. For a generic code base shipped in a tarball that runs in more than twenty billion installations it does less so.</p>
<p>If you look around you can easily find numerous other (and longer) writings about the problems and challenges with CVSS. We are not alone thinking this.</p>
<h2 class="wp-block-heading">CVSS is used</h2>
<p>At the same time, it seems the popularity of <em>security scanners</em> have increased significantly over the last few years. The kind of products that scan your systems checking for vulnerable products and show you big alerts and warnings when they do.</p>
<p>The kind of programs that looks for a product, figures out a version number and then shouts if it finds a registered CVE for that product and version with a CVSS score above a certain threshold.</p>
<p>This kind of product that indirectly tricks users to <a data-id="22214" data-type="post" href="https://daniel.haxx.se/blog/2023/04/24/deleting-system32curl-exe/">deleting operating system components to silence these alerts</a>. We even hear of people who have contractual agreements that say they <strong>must</strong> address these alerts with N number of business days or face consequences.</p>
<p>Just days ago I was contacted by users on macOS who were concerned about a curl CVE that their scanner found in the libcurl version shipped by Apple. Was their tool right or wrong? Do you think anyone involved in that process actually can tell? Do you think Apple cares?</p>
<h2 class="wp-block-heading">curl skips CVSS</h2>
<p>In the curl project we have given up trying to use CVSS to get a severity score and associated severity.</p>
<p>In the curl security team we instead work hard to put all our knowledge together and give a rough indication about the severity by dividing it into <a href="https://curl.se/dev/vuln-disclosure.html#severity-levels">one out of four levels</a>: <strong>low</strong>, <strong>medium</strong>, <strong>high</strong>, <strong>critical</strong>.</p>
<p>We believe that because we are not tied to any (flawed and limited) calculator and because we are intimately familiar with the code base and how it is used, we can assess and set a better security severity this way. It serves our users better.</p>
<p>Part of our reason to still use these four levels is that our <a href="https://curl.se/docs/bugbounty.html">bug-bounty</a>‘s reward levels are based on the level.</p>
<p>As a comparison, The Linux kernel does not even provide that course-grained indication, based on similar reasoning to why we don’t provide the numeric scores.</p>
<h2 class="wp-block-heading">This is not treated well</h2>
<p>The curl project is a <a data-id="23736" data-type="post" href="https://daniel.haxx.se/blog/2024/01/16/curl-is-a-cna/">CNA</a>, which means that we reserve and publish our own CVE Ids to the CVE database. There is no middle man interfering and in fact no one else can file curl CVE entries <a data-id="22951" data-type="post" href="https://daniel.haxx.se/blog/2023/08/26/cve-2020-19909-is-everything-that-is-wrong-with-cves/">anymore</a> without our knowledge and us having a saying about it. That’s good.</p>
<p>However, the CVE system itself it built on the idea that every flaw has a CVSS score. When someone like us creates CVE entries without scores, that leaves something that apparently is considered a gaping sore in the system that someone needs to “fix”.</p>
<p>Who would “fix” this?</p>
<h2 class="wp-block-heading">Authorized Data Publishers</h2>
<p>A while ago this new role was added to the CVE ecosystem called ADPs. This job was previously done a little on the side but roughly the same way by NVD who would get all the CVEs, edit them and then publish them all themselves to the world with their additions. And the world really liked that and used the NVD database.</p>
<p>However NVD kind of drowned themselves by this overwhelming work and it has instead been replaced by CISA who is an “ADP” and is thus allowed to <em>enrich</em> CVE entries in the database that they think needs “improvement”.</p>
<p>The main thing they seem to detect and help “fix” is the lack of CVSS in published CVE entries. Like every single curl CVE because we don’t participate in the CVSS dance.</p>
<h2 class="wp-block-heading">No clues but it must get a score</h2>
<p>Exactly in the same way this system was broken before when NVD did it, this new system is broken when CISA does it.</p>
<p>I don’t have the numbers for exactly how many CVE entries they do this “enrichment” for (there were over 40,000 CVEs last year but a certain amount of them had CVSS filed in by their CNAs). I think it is safe to assume that the volume is high and since they are filed for products in all sorts of categories it is certainly impossible for CISA to have experts in the many products and technologies each CVE describes and affects.</p>
<p>So: given limited time and having no real clue what the issues are about, the individuals in this team click some buttons in a CVSS calculator, get a score, a severity and then (presumably) quickly move on the next issue. And the next. And the next. In a never-ending stream of incoming security issues.</p>
<p>How on earth does anyone expect them to get this right? I mean sure, in some or perhaps even many cases they might get close because of luck, skill or something but the system is certainly built in a way that just screams: <em>this will end up crazy wrong ever so often</em>.</p>
<h2 class="wp-block-heading">A recent example</h2>
<p>In the end of 2024 I was informed by friends that several infosec related websites posted about a new curl-related <em>critical</em> security problem. Since we have not announced any critical security problems since 2013, that of course piqued my interest so I had a look.</p>
<p>It turned out that CISA had decided that <a href="https://curl.se/docs/CVE-2024-11053.html">CVE-2024-11053</a> should be earned a CVSS 9.1 score: CRITICAL, and now scanners and news outlets had figured that out. Or would very soon.</p>
<p>The curl security team had set the severity to LOW because of the low risk and special set of circumstances that are a precondition for the problem. Go read it yourself – the fine thing with CVEs for Open Source products is that the source, the fix and everything is there to read and inspect as much as we like.</p>
<p>The team of actual experts who <em>knows</em> this code and <em>perfectly understands</em> the security problem says LOW. The team at CISA overrides that and insists that are all wrong and that this problem risks breaking the Internet. <em>Because we apparently need a CVSS at all costs.</em></p>
<h2 class="wp-block-heading">A git repository</h2>
<p>One positive change that the switch to CISA from NVD brought is that now they host their additional data in <a href="https://github.com/cisagov/vulnrichment">GitHub repository</a>. Once I was made aware of this insane 9.1 score, I took time of my Sunday afternoon with my family and made <a href="https://github.com/cisagov/vulnrichment/pull/151">a pull-request there</a> urging them to at least lower the score to 5.3. That was a score I could get the calculator to tell me.</p>
<p>I wanted to have this issue sorted and <em>stomped down</em> as quickly as possible to if possible reduce the risk that security scanners everywhere would soon start alerting on this and we would get overloaded with queries from concerned and worried users.</p>
<p>It’s not like CISA gets overloaded by worried users when they do this. Their incompetence here puts a load on no one else but the curl project. But sure, they got their CVSS added.</p>
<p>After my pull request it took less than ninety minutes for them to <a href="https://github.com/cisagov/vulnrichment/commit/91fadb2bf6b461638c8155978b9f20cf17e51fe3">update the curl records</a>. Without explanation, with no reference to my PR, they now apparently consider the issue to be CVSS 3.4.</p>
<p>I’m of course glad it is no longer marked critical. I think you all understand exactly how arbitrary and random this scoring approach is.</p>
<p>A problem with the initial bad score getting published is of course that a certain number of websites and systems are really slow or otherwise bad at <em>updating</em> that information after they initially learned about the critical score. There will linger websites out there speaking about this “critical” curl bug for a long time now. Thanks CISA!</p>
<h2 class="wp-block-heading">Can we avoid this?</h2>
<p>In the curl security team we have discussed setting “fixed” (fake) scores on our CVE entries just in order to prevent CISA or anyone else to ruin them, but we have decided not to since that would be close to lying about them and we actually work fiercely to make sure we have everything correct and meticulously described.</p>
<p>So no, since we do not do the CVSS dance, we unfortunately will continue having CISA do this to us.</p>
<h2 class="wp-block-heading">Stop mandatory CVSS?</h2>
<p>I am of course advocating strongly within the CNA ecosystem that we should be able to stop CISA from doing this, but I am just a small cog in a very large machine. A large machine that seems to love CVSS. I do not expect to have much success in this area anytime soon.</p>
<p>And no, I don’t think switching to CVSS 4.0 or updates to this system is ultimately going to help us. The problem is grounded in the fact that a single one-dimensional score is just too limited. Every user or distributor of the project should set score for their different use cases. Maybe even different ones for different cases. Then it could <em>perhaps</em> work.</p>
<p>But I’m not in this game for any quick wins. I’m on the barricades for better (Open Source) security information, and to stop security <em>misinformation</em>. Ideally for the wider ecosystem, because I think we are far from alone in this situation.</p>
<p>The love of CVSS is strong and there is a lot of money involved based on and relying on this.</p>
<p></p>
CVSS is dead to us
https://daniel.haxx.se/blog/2025/01/23/cvss-is-dead-to-us/
#curl
23.01.2025 10:43 — 👍 20 🔁 23 💬 4 📌 5
The OSS-Fuzz team is hiring a PhD intern for this summer. Come join us and build something interesting that will have immediate impact on 1000+ open source projects.
www.google.com/about/career...
Also reach out if you have already applied!
16.01.2025 03:46 — 👍 5 🔁 4 💬 0 📌 0
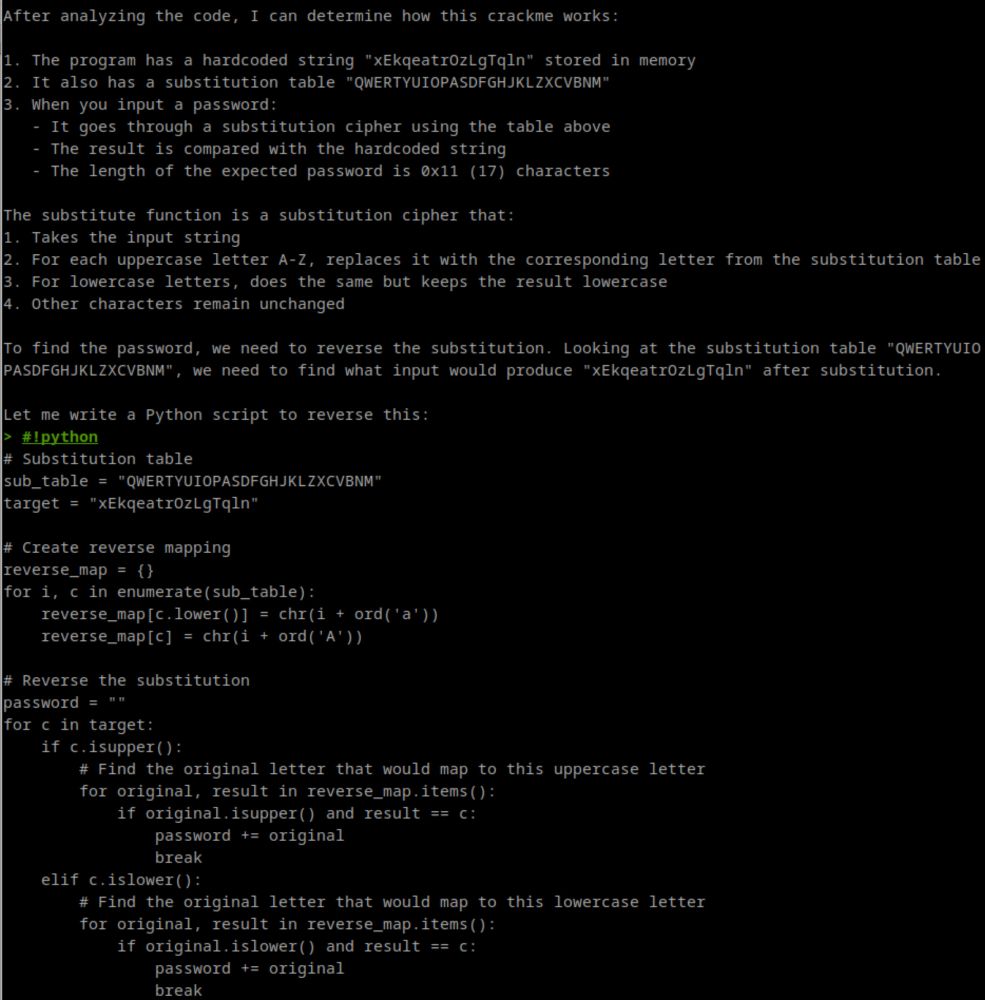
Cracking my own CrackMe with r2ai
Recently, I viewed the excellent “Cracking binaries with r2ai visual mode” by Daniel Nakov, at r2con 2024. In September 2024, I had tried…
r2ai solves my CrackMe in a few seconds. The solution is both elegant and educational.
cryptax.medium.com/cracking-my-...
+ recommended view: www.youtube.com/watch?v=UxE5...
#r2con #radare2 #ai #crackme #ctf
07.01.2025 08:05 — 👍 4 🔁 3 💬 0 📌 0
(please re-post for reach - thank you!)
Learned a cool new Linux trick? Know an interesting quirk in a network protocol? Or have something else to share?
Write a 1-page article for the #6 issue of Paged Out! :)
pagedout.institute?page=cfp.php
Soft deadline is Feb 1st.
07.01.2025 07:41 — 👍 30 🔁 33 💬 0 📌 0
I am convinced 99% of websites should use magic links + passkeys.
It bypasses all (debatable) portability objections to passkeys, it’s at least as secure as email-based recovery, as fast as a password manager, it’s available to all users… and importantly, no passwords!
02.01.2025 15:26 — 👍 157 🔁 31 💬 20 📌 3
30.12.2024 14:56 — 👍 5547 🔁 1185 💬 104 📌 49
just a friendly reminder that mars colonization is 100% science fiction.
take mount everest, stack four more mountains of equal size on top of it, and then try to live there.
it’s absolute nonsense.
30.12.2024 22:42 — 👍 3975 🔁 644 💬 314 📌 89
I got a remarkable for that. Works decently ok.
28.12.2024 11:56 — 👍 1 🔁 0 💬 0 📌 0

Microsoft and OpenAI have a financial definition of AGI: Report | TechCrunch
Microsoft and OpenAI have a very specific, internal definition of artificial general intelligence (AGI) based on the startup's profits, according to a new
"The two companies reportedly signed an agreement last year stating OpenAI has only achieved AGI when it develops AI systems that can generate at least $100 billion in profits."
"AGI is when I have heaps of money," is one hell of a position.
techcrunch.com/2024/12/26/m...
27.12.2024 00:42 — 👍 265 🔁 60 💬 20 📌 19
I keep putting off my blog post on "random" but I generally feel that platform and SDK developers are failing their users by not using a CSPRNG by default, everywhere.
13.12.2024 16:50 — 👍 23 🔁 5 💬 5 📌 0
True crazy real story. Maybe 2019, we had a C Suite exec hacked, threats, etc. All traced back to a car the guy synced his phone with. In Iceland.
13.12.2024 04:46 — 👍 8 🔁 5 💬 0 📌 0

Crypto’s Legacy Is Finally Clear
An anti-establishment technology for an anti-establishment age
The legacy of crypto isn’t a technology revolution but instead that it created a culture where get rich quick mentality, grifting and Ponzi schemes were a virtue. Then made these people rich enough that they could influence elections.
That and being the financial instrument for ransomware payments
12.12.2024 12:57 — 👍 175 🔁 28 💬 4 📌 2
TIL when you use "from module import function" python still loads the entire module. Saw this in my memory flame graph. I moved some functions with heavy deps to a separate file and it deleted a whole "flame" of memory allocations
12.12.2024 12:51 — 👍 33 🔁 9 💬 3 📌 0
if arguing online changed anything we'd all be running Linux
12.12.2024 20:28 — 👍 7175 🔁 948 💬 178 📌 59
Reminder from your friendly neighborhood astronomer/pilot: Anything can be a #UFO if you suck enough at identifying normal objects in the sky.
12.12.2024 22:50 — 👍 62 🔁 12 💬 3 📌 2

30 Years of Decompilation and the Unsolved Structuring Problem: Part 1
A two-part series on the history of decompiler research and the fight against the unsolved control flow structuring problem. In part 1, we revisit the histor...
Found this insanely helpful post on the state of the art in decompilation. Specifically, it dives into the "structuring problem" : trying to identify "if"s, "while"s and other patterns in a CFG while minimizing the use of "goto".
mahaloz.re/dec-history-...
26.11.2024 20:49 — 👍 1 🔁 1 💬 0 📌 0
Sure yeah you all hate CEOs now, but you'll change your tune when you need someone who can disrupt workplace engagement paradigms and offer bold innovations in the metrics sector
06.12.2024 20:23 — 👍 2910 🔁 435 💬 67 📌 18
Security Engineering @ Apple, Ex-UK Gov
The intersection of technology (device and national security), and liberal arts (public policy)
Dev/hacker | Improving human understanding of code | A picture's worth 1KLOC
Malware hunter ☣ && Assistant Professor 👨🏻🔬 @EURECOM
X: https://x.com/packm4d
WWW: https://simoneaonzo.it/
LinkedIn: https://www.linkedin.com/in/simone-aonzo-290b05180/
i work on rust mostly
https://errs.io
A young Open-Source developers, with a passion for compilers, procedural generation, and Rust.
Currently working on compiling Rust to C(and .NET):
https://github.com/FractalFir/rustc_codegen_clr
#rustlang, #jj-vcs, atproto, shitposts, urbanism. I contain multitudes.
Working on #ruelang but just for fun.
Currently in Austin, TX, but from Pittsburgh. Previously in Bushwick, the Mission, LA.
Abgeordnete des Deutschen Bundestags. Wahlkreis Backnang Schwäbisch-Gmünd. Hier als Humor-Beauftragte der Grünen.
CTF player, Security engineer at Google, http://infosec.exchange/@spq ; @_spq__ on Twitter
Post-channel side-quantum guy
Professor of Computer Science at RUB/HGI/CASA, Chief Scientific Advisor at NEC Labs, Decentralized Security
We secure software with deep-dive audits, cutting-edge research, and in-depth trainings.
Android malware analysis. Ph0wn CTF founder. IoT hacking. Frequent speaker at Virus Bulletin, Insomnihack etc. Based in France.
Currently testing Bluesky. Otherwise on Mastodon.social.
WE ARE ISEC: The Institute of Information Security at TU Graz
🔒 Professor of IT Security @ University of Luebeck
💡 Research in systems security, applied cryptography, and side channels
🌐 More info: its.uni-luebeck.de
The 22nd Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA '25)
✨July 9 to 11, 2025 ✨in Graz, AUSTRIA 🇦🇹
PhD Student TU Graz trying to improve computer security.
Follow me on instagram for photos and videos: @jonas.juffinger
he/him
https://www.jonasjuffinger.com
Professor of Computer Science | Director GameLabGraz GameDevDays | #GameDev Research Science Tech VR AI | @TUGraz | past LMU ETH MIT EA | Forbes 30u30 Science | mountains ⛰️
twitch.tv/JoeyPrink
youtube.com/@JoeyPrink
jpirker.com
Research Scientist at Intel Labs. Working on (post-quantum) cryptography, hardware design, and side-channel analysis.






