APT folks... is UNC3886 becoming a top-tier actor?
www.trendmicro.com/en_us/resear...
www.sygnia.co/blog/fire-an...
supportportal.juniper.net/s/article/20...
cloud.google.com/blog/topics/...
29.07.2025 10:06 — 👍 15 🔁 3 💬 2 📌 0
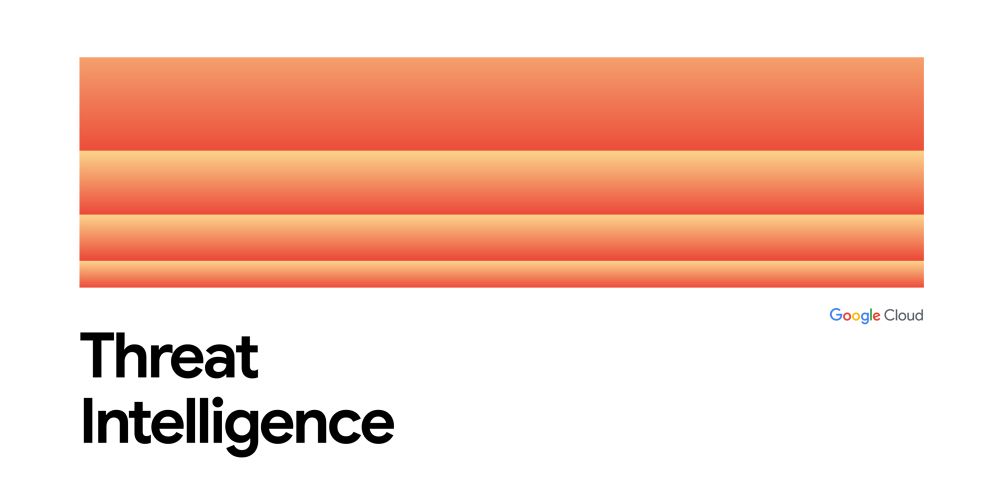
Text-to-Malware: How Cybercriminals Weaponize Fake AI-Themed Websites | Google Cloud Blog
Cybercriminals are using fake AI-themed ads and websites to deliver malware such as infostealers and backdoors.
This campaign deploys malware like STARKVEIL, XWORM & FROSTRIFT. Our report covers their TTPs including the use of Unicode Braille patterns to obfuscate executable file names and their continuous rotation of domains to evade detection.
cloud.google.com/blog/topics/...
28.05.2025 20:40 — 👍 1 🔁 0 💬 0 📌 0
New @mandiant.com research: UNC6032 (Vietnam-nexus actor 🇻🇳) is exploiting interest in AI tools, using fake AI video generator sites & malicious ads to spread malware.
The campaign, active since mid-2024, aims to steal credentials, cookies & financial data.
28.05.2025 20:40 — 👍 6 🔁 0 💬 1 📌 0
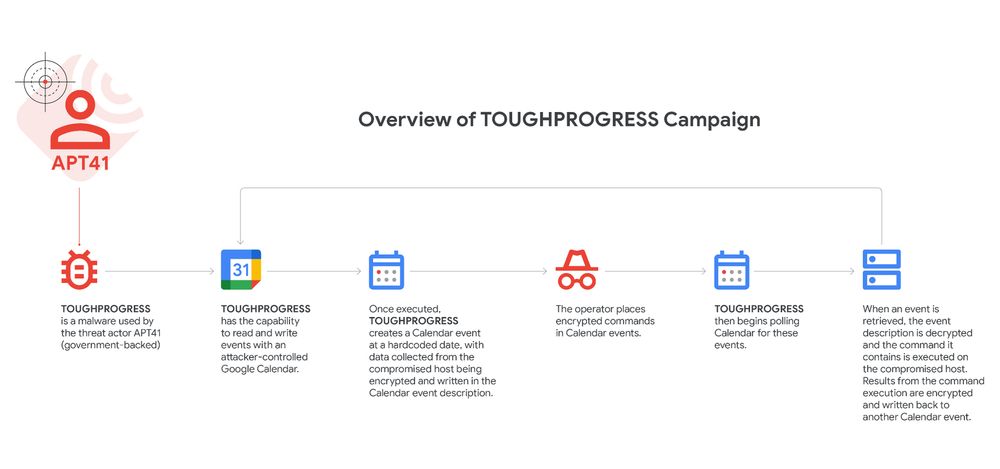
🚨 Heads up! 🚨 APT41 is using Google Calendar 🗓️ as their latest C2 trick. GTIG just pulled back the curtain 🎭 on the TOUGHPROGRESS malware campaign and how we shut it down 💪. Dive into the details here: 🚀https://cloud.google.com/blog/topics/threat-intelligence/apt41-innovative-tactics
28.05.2025 14:11 — 👍 8 🔁 4 💬 1 📌 3
Original post on cyberplace.social
Google’s M-Trends 2025 report is out - data from Mandiant’s incident response engagements. Direct PDF link to avoid the sales pitch wall:
https://services.google.com/fh/files/misc/m-trends-2025-en.pdf
Thread about my main observations:
- Firstly, no mention of generative AI or GenAI again […]
24.04.2025 06:07 — 👍 32 🔁 31 💬 1 📌 0
Confirming that CISA has stopped using VirusTotal and Censys.
"Makes their jobs a lot harder," a person familiar with the matter told me, adding, "There's a possibility that more services might be limited or cut due to budget."
18.04.2025 17:39 — 👍 52 🔁 26 💬 3 📌 1
Windows Remote Desktop Protocol: Remote to Rogue | Google Cloud Blog
A novel phishing campaign by Russia-nexus espionage actors targeting European government and military organizations.
Excellent breakdown of the “Rogue RDP” TTP we’ve seen susp Russian APT UNC5837 using in their campaigns written by my colleague Rohit (@IzySec over on X)
07.04.2025 15:06 — 👍 16 🔁 8 💬 0 📌 0
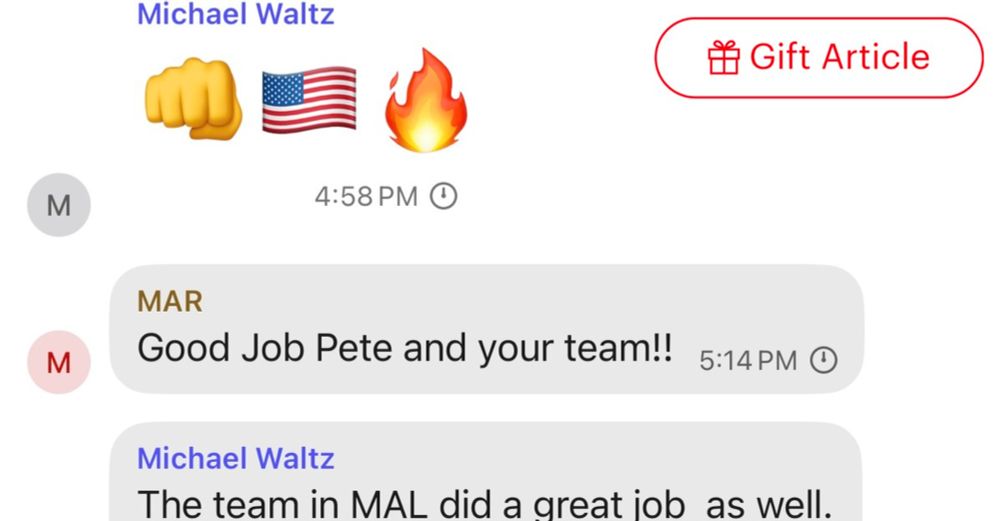
The Trump Administration Accidentally Texted Me Its War Plans
U.S. national-security leaders included me in a group chat about upcoming military strikes in Yemen. I didn’t think it could be real. Then the bombs started falling.
In 25 years of covering national security, I’ve never seen a story like this: Senior Trump officials discussed planning for the U.S. attack on Yemen in a Signal group--and inadvertently added the editor-in-chief of The Atlantic. www.theatlantic.com/politics/arc...
24.03.2025 16:11 — 👍 16823 🔁 6584 💬 800 📌 2642
Ghost in the Router: China-Nexus Espionage Actor UNC3886 Targets Juniper Routers | Google Cloud Blog
We discovered China-nexus threat actors deployed custom backdoors on Juniper Networks’ Junos OS routers.
🚨 Following a months-long investigation stemming back to mid-2024, Mandiant just published details on a campaign by China-nexus actor UNC3886 targeting Juniper routers. Our investigation uncovered a custom malware ecosystem on end-of-life Juniper MX devices.
cloud.google.com/blog/topics/...
12.03.2025 19:36 — 👍 4 🔁 0 💬 0 📌 1
Hundreds protested at the national labs today in Boulder, Colorado. #SaveOurServices #resist #NOAA #NIST #NCAR #ScienceSavesLives
03.03.2025 20:34 — 👍 843 🔁 214 💬 12 📌 17

It Was an Ambush
Today marked one of the grimmest days in the history of American diplomacy.
Today was a grim, terrible day for the United States and the cause of democracy. Putin, along with other dictators around the world, can finally look at Trump with confidence and think: one of us.
www.theatlantic.com/ideas/archiv...
01.03.2025 00:56 — 👍 5361 🔁 1474 💬 285 📌 113

Army soldier linked to Snowflake attack spree allegedly tried to sell data to foreign spies
Federal prosecutors accuse Cameron Wagenius of searching how to defect to Russia days after he tried to sell stolen data to a foreign intelligence service.
A 21-year-old U.S. Army soldier linked to last year's Snowflake attack spree allegedly tried to sell stolen data to a foreign intelligence service after searching for information about how to defect to Russia. Hat tip to @nixonnixoff.bsky.social @austinlarsen.me cyberscoop.com/army-soldier...
27.02.2025 23:03 — 👍 28 🔁 12 💬 2 📌 1

DHS has terminated the memberships of everyone on its advisory committees.
This includes several cyber committees, like CISA's advisory panel and the Cyber Safety Review Board, which was investigating Salt Typhoon.
That review is "dead," person familiar says.
www.documentcloud.org/documents/25...
21.01.2025 20:43 — 👍 1084 🔁 614 💬 54 📌 186
Cloudflare Issue Can Leak Chat App Users' Broad Location
A security researcher made a tool that let them quickly check which of Cloudflare's data centers had cached an image, which allowed them to figure out what city a Discord, Signal, or Twitter/X user mi...
A bug in Cloudflare (and just the nature of how CDNs work) let an attacker learn the broad location of Discord, Signal, Twitter users by just sending them an image, according to a security researcher. It works because check which data center cached the image www.404media.co/cloudflare-i...
21.01.2025 14:40 — 👍 2450 🔁 666 💬 101 📌 39

Ivanti Connect Secure VPN Targeted in New Zero-Day Exploitation | Google Cloud Blog
Zero-day exploitation of Ivanti Connect Secure VPN vulnerabilities since as far back as December 2024.
🔥 new blog detailing 0day exploitation of Ivanti appliances as well as some newly observed malware families tracked as PHASEJAM and DRYHOOK. We also detail activity related to the previously observed SPAWN* malware ecosystem tied to China-nexus cluster UNC5337.
cloud.google.com/blog/topics/...
09.01.2025 00:42 — 👍 34 🔁 23 💬 0 📌 4
Ivanti Community
Patch immediately, run the Ivanti external ICT checker, read our latest research for a detailed breakdown of the threat, and checkout Ivanti's advisory for the latest guidance:
forums.ivanti.com/s/article/Se...
09.01.2025 00:42 — 👍 0 🔁 0 💬 1 📌 0
🛡️ Persistence: Threat actors are installing persistent backdoors on compromised appliances that can survive across system reboots and upgrades. Mandiant identified the actors using backdoors including SPAWN, SPAWNANT, SPAWNMOLE, SPAWNSNAIL, SPAWNSLOTH, DRYHOOK, and PHASEJAM.
09.01.2025 00:42 — 👍 0 🔁 0 💬 1 📌 0
🛡️ ICT Evasion: Threat actors are manipulating the Ivanti Integrity Checker Tool (ICT) manifest to include their own malicious files, effectively bypassing this detection mechanism.
09.01.2025 00:42 — 👍 0 🔁 0 💬 1 📌 0
🛡️ Fake Upgrade: Threat actors are deploying PHASEJAM malware to block legitimate system upgrades while simultaneously displaying a fake upgrade progress bar. This creates a convincing facade of a successful update, when in reality, the malware silently prevents the actual upgrade from taking place.
09.01.2025 00:42 — 👍 0 🔁 0 💬 1 📌 0
This threat showcases how China-nexus cyber espionage actors continue to evolve, becoming more agile, stealthy, and difficult for defenders to detect. They employed several interesting techniques to maintain access to compromised Ivanti appliances and evade defenders. Here's what you need to know:
09.01.2025 00:42 — 👍 0 🔁 0 💬 1 📌 0

Ivanti Connect Secure VPN Targeted in New Zero-Day Exploitation | Google Cloud Blog
Zero-day exploitation of Ivanti Connect Secure VPN vulnerabilities since as far back as December 2024.
🚨 New: Zero-day vulnerability #CVE-2025-0282 in Ivanti Connect Secure VPN is being actively exploited, including by suspected China-nexus cyber espionage groups. Our team at Mandiant in partnership with Ivanti just published our initial findings. 🧵
cloud.google.com/blog/topics/...
09.01.2025 00:42 — 👍 7 🔁 1 💬 1 📌 0

>IQ levels when you are a cybercriminal that tries to extort the president, but you are government property and Krebs is calling your mom :(
31.12.2024 04:06 — 👍 80 🔁 14 💬 1 📌 2
Something completely underappreciated in how Google Chrome revolutionized the web and security and software in general — was the silent background auto-update + and non-admin user-level installs. It set a bar that changed everything on ability to make progress & address threats. Broke IT paradigms.
20.12.2024 03:39 — 👍 732 🔁 71 💬 16 📌 5
Who wants to be next?
(Waifu arrest footage released by WSJ)
www.wsj.com/tech/cyberse...
08.12.2024 02:39 — 👍 124 🔁 23 💬 12 📌 3
Assemblymember. Democratic Nominee for Mayor of NYC. Running to freeze the rent, make buses fast + free, and deliver universal childcare. Democratic Socialist. zohranfornyc.com
Editorial Director at National Security Archive. FOIA enthusiast. Colombia specialist. Bluegrass guitarist. He/Him nsarchive.gwu.edu
Cyber Threat Intelligence
U.S. Senator for Maryland
vanhollen.senate.gov
We’re determined to make organizations secure against cyber threats and confident in their readiness.
Always fighting for the people.
Wife, Momala, Auntie. She/her.
107 Days, my behind-the-scenes account of the shortest campaign in history, is available for pre-order now.
#threatintel @Recorded Future | Formerly @PwC GTI | Malware & infrastructure analysis with a side of cyberpunk. 🌃🌌 She/her, support 🏳️🌈🏳️⚧️✨
Native plant nerd. Recovering soil scientist. Compost freak. Beginning birder. CoCoRaHS observer. Community, equity, climate. Great Plains bordering on Southern Rockies. Yeah, I’m concerned about authoritarianism.
journalist / founder @ thehandbasket.co
email: MKwrites4000@proton.me
signal: https://signal.me/#eu/VssgH88q6WQu7MtH5wF-08JdgWh4iAPWD13eXiOcXQNGdZUXijJBZInD-UtLJKFG
venmo: venmo.com/u/Marisa-Kabas
ko-fi: https://ko-fi.com/marisakabas
I am eminently qualified to speak from experience about a variety of dumpster fires.
ICS DFIR at Dragos, martial artist, marksman, humanist, level 14 Neutral Good rogue, USAF retired. I post *very serious* things about infosec. Thoughts my own. Enby. 🏳️🌈
Senior editor of @propublica.org's data journalism teams. Super gay. Sometimes printmaker.
Reporter @cyberscoop.bsky.social covering cybercrime and software defects • Grateful lifelong Californian • matt.49 on Signal • matt.kapko@cyberscoop.com • mattkapko.com
soccer & security 🤠 she/her
Follow/RT/links NOT endorsement. 🔞
Husband, dad, veteran, writer, and proud Midwesterner. 19th US Secretary of Transportation and former Mayor of South Bend.
Just asking questions.
Senior Editor, Lawfaremedia.org.
Send story ideas and tips to anna.bower@lawfaremedia.org
Signal username: annabower.24
Organizer, writer, mom. Philly partisan. IIWFJU member.
She/they.