
Take back control: A modern guide to mastering application control
Learn how a robust app control policy can have a meaningful, measurable impact on your organization’s security posture.
New on the @redcanaryco.bsky.social blog this week: Your one stop shop for all things app control. Was fun pulling together this guide on some of the common failures and tips on how to succeed rolling out a policy in 2026: redcanary.com/blog/securit...
11.02.2026 15:40 — 👍 0 🔁 0 💬 0 📌 0

When adversaries bring their own virtual machine for persistence
We peel back the layers on a threat involving an adversary who brought their own VM into an environment following aggressive spam bombing.
This week on the @redcanaryco.bsky.social blog: Had a lot of fun untangling this research from our Intelligence team on an adversary who brought their own VM into an environment following a spam bombing attack. Good longread on a thorough forensic investigation: redcanary.com/blog/threat-...
10.12.2025 14:14 — 👍 0 🔁 1 💬 0 📌 0

A guide to building reliable AI agents for your SOC
Read our practical guide on how to build reliable AI agents for security operations—along with open source code and a workflow graph
Launch day yesterday over at @redcanaryco.bsky.social for a comprehensive new 20-page guide I helped write with our Director of Machine Learning. The guide lays out everything you need for building reliable AI agents for security operations: redcanary.com/blog/securit...
20.11.2025 13:22 — 👍 1 🔁 0 💬 0 📌 0

ATT&CK v18: Detection Strategies, More Adversary Insights,
ATT&CK v18 is released with new Detection Strategies, Analytics, and revamped Data Components!
ATT&CK v18 is now out! Today marks the release of Detection Strategies, where we've moved from single-sentence notes to structured, behavior-focused strategies across the board. A new blog post describes the changes medium.com/mitre-attack... with details at attack.mitre.org/resources/up....
28.10.2025 14:56 — 👍 9 🔁 5 💬 0 📌 2
Answered my own question! Neon Williams - a great follow on Instagram (www.instagram.com/neon_williams/) has it now.
24.10.2025 17:40 — 👍 1 🔁 0 💬 0 📌 0

Hardly ever in Lynn but was today. Sad to learn the rug store with this iconic neon sign apparently closed recently. Wonder what happened to the sign.
24.10.2025 17:32 — 👍 5 🔁 1 💬 1 📌 0

Noticed authors love to do this in the @nytimes.com Book Review: Mention a new book that hasn’t even been announced yet, let alone released. Someone did this a few years ask with an Emily St. John Mandel book. This Jami Attenberg book doesn’t exist—yet.
23.10.2025 22:42 — 👍 0 🔁 0 💬 0 📌 0

Node problem: Tracking recent npm package compromises | Red Canary
Recent npm supply chain attacks highlight why robust mitigation and response strategies are required for both developers and users.
Some helpful and topical content posted to @redcanaryco.bsky.social yesterday. Distilled some great guidance from @forensicitguy.bsky.social on securing npm packages + responding to a compromise: redcanary.com/blog/threat-...
24.09.2025 18:59 — 👍 0 🔁 0 💬 0 📌 0

Understanding OAuth application attacks and defenses | Red Canary
Red Canary’s Threat Hunting team recently uncovered a malicious OAuth application attack, demonstrating the need for specific defenses.
@redcanaryco.bsky.social's Threat Hunting team recently investigated an incident that illustrates how stealthy and patient an OAuth application attack can be. We breakdown the campaign (and how to defend against these attacks) in this blog:
05.09.2025 13:37 — 👍 0 🔁 0 💬 0 📌 0

Front page ad for Prager in the NYT today 🥴
31.08.2025 15:13 — 👍 0 🔁 0 💬 0 📌 0

Deer Isle Oysters at Pilgrim’s Inn. Could eat a lot of these.
10.08.2025 16:47 — 👍 0 🔁 0 💬 0 📌 0
Ugh, @noupside.bsky.social posted yesterday about this happening to her, too!
24.07.2025 18:01 — 👍 1 🔁 0 💬 0 📌 0

10 Black Hat talks we want to see in 2025 | Red Canary
Talks on bypassing SOCs and initial access—we scoured this year’s list of sessions at Black Hat to find 10 talks worth making time for.
Another new @redcanaryco.bsky.social blog: I'm not going to @blackhatevents.bsky.social this year but if I were, these are the talks I'd try to attend. Lots of stories + intel for defenders: redcanary.com/blog/securit...
24.07.2025 14:42 — 👍 0 🔁 0 💬 0 📌 0

Summercon Foundation
Hey, Summercon is streaming today: www.youtube.com/@SummerconFo...
11.07.2025 15:17 — 👍 0 🔁 0 💬 0 📌 0
Understanding the threat landscape for MCP and AI workflows
We break down the cybersecurity landscape of Model Context Protocol (MCP) servers and agentic AI workflows, including monitoring advice
MCP servers allow developers to facilitate AI agents to execute code. MCP doesn't include security mechanisms however—the onus is on developers to implement standard security best practices. @redcanaryco.bsky.social's Jesse Griggs navigates the MCP threat landscape: redcanary.com/blog/threat-...
11.07.2025 13:14 — 👍 0 🔁 0 💬 0 📌 0
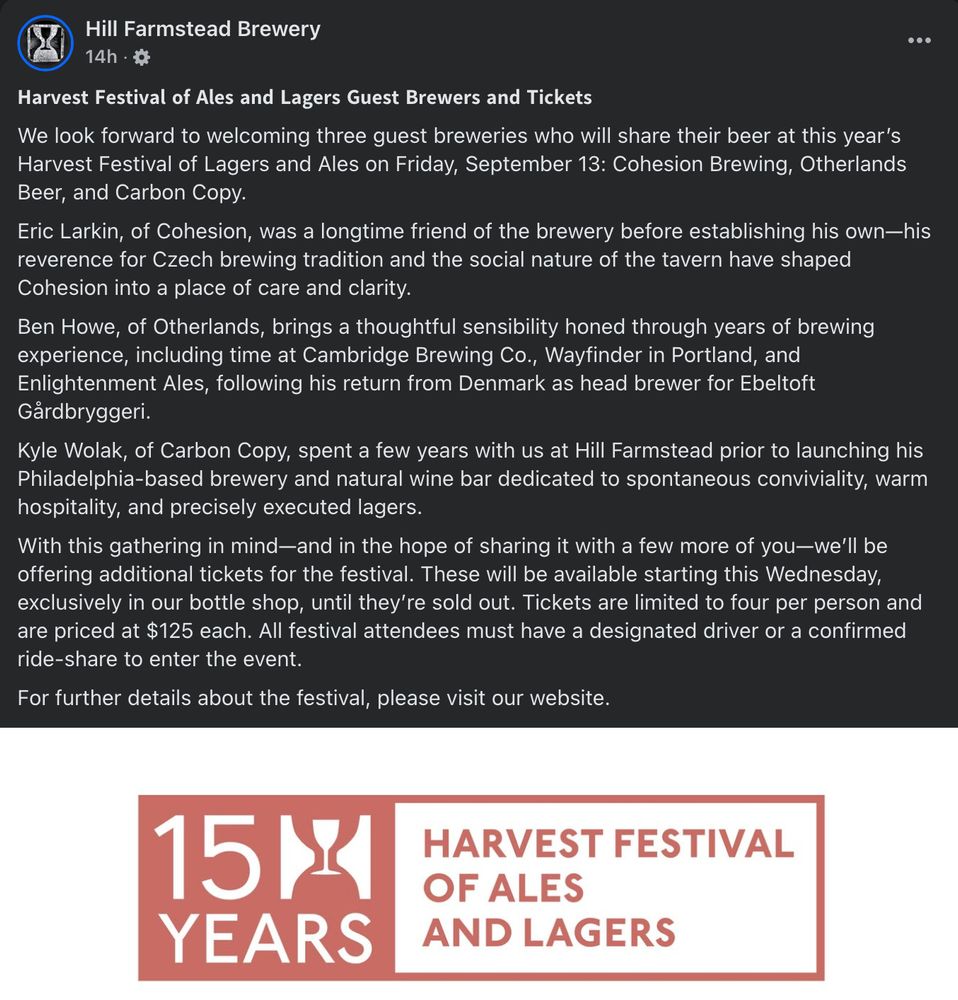
Appreciate what #HillFarmstead does for its Harvest Festival re: curated guest taps, almost like a mini-FW Invitational. I don't think I've been to one since 2011? Whenever you used to be able to camp there afterwards.
08.07.2025 13:18 — 👍 0 🔁 0 💬 0 📌 0

All about that baseline: Detecting anomalies with Surveyor | Red Canary
The Surveyor open source tool can help organizations establish a baseline of their environment, verify activity, and investigate anomalies.
💫 @redcanaryco.bsky.social has a handful of helpful free, open-source tools, including Surveyor, which can help orgs establish a baseline of their environment and in turn, detect potential anomalies—like unsanctioned RMM tool usage that can be abused for initial access: redcanary.com/blog/threat-...
05.06.2025 15:20 — 👍 0 🔁 0 💬 0 📌 0
Take a bad thing and make it worse
20.05.2025 18:02 — 👍 25 🔁 7 💬 3 📌 0
We have two. The Hario Blue Bottle one which looks nice and fits easily in the fridge but doesn't make that much and the OXO, which we use more often but makes a bunch but takes up a bit of room on the counter.
08.05.2025 18:29 — 👍 0 🔁 0 💬 1 📌 0
Haim industrial complex is working overtime this year.
28.04.2025 19:54 — 👍 0 🔁 0 💬 0 📌 0

ATT&CK v17: New Platform (ESXi), Collection Optimization, & More Countermeasures
By: Amy Robertson and Adam Pennington
New ATT&CK @attack.mitre.org version (v7) includes ESXi + four new techniques designed for it, expanded cloud security + Linux coverage, new mobile techniques: medium.com/mitre-attack...
23.04.2025 13:10 — 👍 1 🔁 0 💬 0 📌 0
Finally finished The Antidote. Fitting to end with a Land Lost Acknowledgement.
18.04.2025 02:12 — 👍 1 🔁 0 💬 0 📌 0
YouTube video by Lana Del Rey
Lana Del Rey - Henry, come on (Audio)
New Lana song titled something I say literally everyday: www.youtube.com/watch?v=nDYY...
11.04.2025 18:39 — 👍 0 🔁 0 💬 0 📌 0

The RSA Conference talks worth catching in 2025 | Red Canary
How AI agents can help purple teaming, inside the stolen credential ecosystem, and more: We read through the RSA agenda so you don't have to.
Did a deep dive on this year's #RSAC schedule (500+ sessions!) for Red Canary and found what I thought were some interesting talks on adversary emulation, detection engineering, and yes, AI—it's unavoidable! redcanary.com/blog/securit...
03.04.2025 17:45 — 👍 0 🔁 0 💬 0 📌 0
Three Buddy Problem
https://securityconversations.com
Sharing information on malicious network traffic and malware samples at https://www.malware-traffic-analysis.net/
MITRE ATT&CK® - A knowledge base for describing the behavior of adversaries. Replying/Following/Reposting ≠ endorsement.
As long as we got a dollar left, we eat good in this house. Words about baseball, board games, food, and more.
Securing data everywhere with Zero Trust + AI to protect your workforce, branches, and clouds.
Senior Intelligence Analyst at Red Canary, former DFIR at Mandiant. Psychology and history nerd. When I am not computering, I go outside and play!
Security without fear since 2018.
https://decipher.sc
https://www.youtube.com/@DecipherSec
https://www.buzzsprout.com/228511/supporters/new
24/7/365 threat detection and response across your cloud, identity, endpoints and everything in-between. We got you!
For more information visit: https://redcanary.com/
Principal Analyst @Forrester, covering #DataSecurity. All opinions are my own. She/Her
Community + Content @ Red Canary
Comms by day, craft beer by night. Other half of Gentile Brewing. Wisconsinite turned Masshole.
Researching conservative news and right-wing media. PhD in American Studies from NYU. I teach at but don't speak for the University of Alabama.
News on the Right (http://bit.ly/2YgUcZX).
Pre-order *Making the Liberal Media* (https://shorturl.at/e31nU)!
Former door-to-door knife salesman from Georgia. Current ne'er-do-well in South Philly
Writer. Boston Globe correspondent + words at Boston.com, Down East, Edible, GovTech, Different Leaf, etc. Stop sending alcohol pitches. :)
Herr Doktor Professor Deth Vegetable -- CULT OF THE DEAD COW -- .ooM
Hacker / Archaeologist / Gadabout / Professional Something-or-Other. Anti-fascist and Pro-science. As the old axiom says, reality has a liberal bias.
Nazis need to be punched.
🧑🏻💻Communications & PR Consultant | Part-time gambler | Co-Founder of Handigraphs | Listens to Phish ⭕️ | Philly native, Former Californian | I also DJ 🎧
Let’s count the rings around my eyes
Writer/Editor in Brooklyn. Talk to me about infosec, pop music, and black cats.
https://www.nytimes.com/2024/04/16/style/tiny-love-modern-love-stories-the-one-liners-kept-coming.html?smid=nytcore-ios-share&referringSource=articleShare
























