
True academic, editing slides up to the last minute 😅 Happy to be presenting Golden at today’s NY Crypto Day!
eprint.iacr.org/2025/1924

True academic, editing slides up to the last minute 😅 Happy to be presenting Golden at today’s NY Crypto Day!
eprint.iacr.org/2025/1924


Spending the week in beautiful Okinawa at the OIST workshop on isogeny-based cryptography
03.02.2026 04:48 — 👍 1 🔁 0 💬 0 📌 0One step closer- mapping execution flow from the interactive distinguisher Z and finally understanding the dummy adversary
23.01.2026 15:56 — 👍 4 🔁 0 💬 1 📌 0My mom told me a quote today that my grandmother used to say after she would sign up for every free giveaway under the sun - “you can’t win if you don’t play.” And I kind of love that mentality for trying something in the face of overwhelming possibility of failure - generally the case in research
22.01.2026 19:58 — 👍 2 🔁 0 💬 0 📌 0Happy new year! One of my New Year’s resolutions this year is to finally finish my gentle introduction to writing proofs in UC, for myself as well.. if anyone is interested in reviewing/contributing, please let me know! 🙌
12.01.2026 16:42 — 👍 7 🔁 1 💬 1 📌 1
I’m at SBC and Simon’s for the next week, looking forward to seeing everyone!
Will be giving a talk on Thursday at Simon’s on our recent impossibility results on the adaptive security of threshold signatures- simons.berkeley.edu/talks/chelse...
Thank you!! Wow you are lucky
15.01.2025 04:46 — 👍 0 🔁 0 💬 0 📌 02025: started out with Covid, got better, then relapsed into Covid 🤦♀️
15.01.2025 00:39 — 👍 1 🔁 0 💬 2 📌 0Back to blue sky and happy new year!!!
04.01.2025 16:31 — 👍 12 🔁 0 💬 0 📌 0
After 3 years & 12 drafts, the RFC for FROST is complete! We hope this makes implementing FROST easier with fewer bugs 🐛
Thank you to everyone who helped by reviewing FROST security, submitting comments, and implementing the draft, this was a team effort 🙌💪
www.rfc-editor.org/rfc/rfc9591....
Awesome! Added to the list for next year :)
03.06.2024 15:05 — 👍 0 🔁 0 💬 0 📌 0In Croatia? Have fun!! Hopefully I’ll make it one day 🤞
01.06.2024 15:54 — 👍 0 🔁 0 💬 1 📌 0There's a mergesort step on page 12 that is costed at N log N. So I don't think this improves on Sam Jaques' eprint 2024/080 from a theoretical perspective. Nice implementation work though!
20.05.2024 16:25 — 👍 4 🔁 3 💬 0 📌 0
Consider donating your eclipse glasses to Eclipse Glasses USA so schoolchildren in South America can use them in October. eclipse23.com/pages/donate...
08.04.2024 20:49 — 👍 928 🔁 737 💬 7 📌 15
First podcast, check it out! :) zeroknowledge.fm/318-2/
05.04.2024 01:13 — 👍 12 🔁 5 💬 0 📌 0
This is jaw-dropping, wild news and should be criminal
techcrunch.com/2024/03/26/f...
It's not a choice of one or the other.
Use the appendix, as an author, to make reviewers see the value of sticky reviews and make them more likely to ask chairs to turn them on!
Good point!
31.03.2024 18:02 — 👍 0 🔁 0 💬 0 📌 0If you are on a PC for an IACR conference, consider reaching out to the PC chairs to request “sticky reviews”, to allow reviews from prior submissions to IACR conferences to be visible! Let’s make science better! 💪
30.03.2024 20:25 — 👍 6 🔁 3 💬 0 📌 0It is good to know you feel this way, as a potential future book-writer :)
30.03.2024 19:41 — 👍 1 🔁 0 💬 0 📌 0Will do! Thanks Nigel 🙏
30.03.2024 18:20 — 👍 1 🔁 0 💬 1 📌 0Well, I would like this feature as a reviewer :)
30.03.2024 18:10 — 👍 0 🔁 0 💬 1 📌 0Great to hear this is possible!! So it is just a matter of promoting it to be more of the norm 🤔
30.03.2024 18:03 — 👍 2 🔁 0 💬 1 📌 0I wish conferences asked papers to submit feedback received from prior submission attempts and a discussion of how the authors improved the paper since then… so much context is lost between submission attempts across different venues
30.03.2024 17:04 — 👍 7 🔁 1 💬 1 📌 0
Thanks for the amazing time #RealWorldCrypto, fantastic talks and conversations as always! See you next year in Europe :)
29.03.2024 15:55 — 👍 8 🔁 0 💬 0 📌 0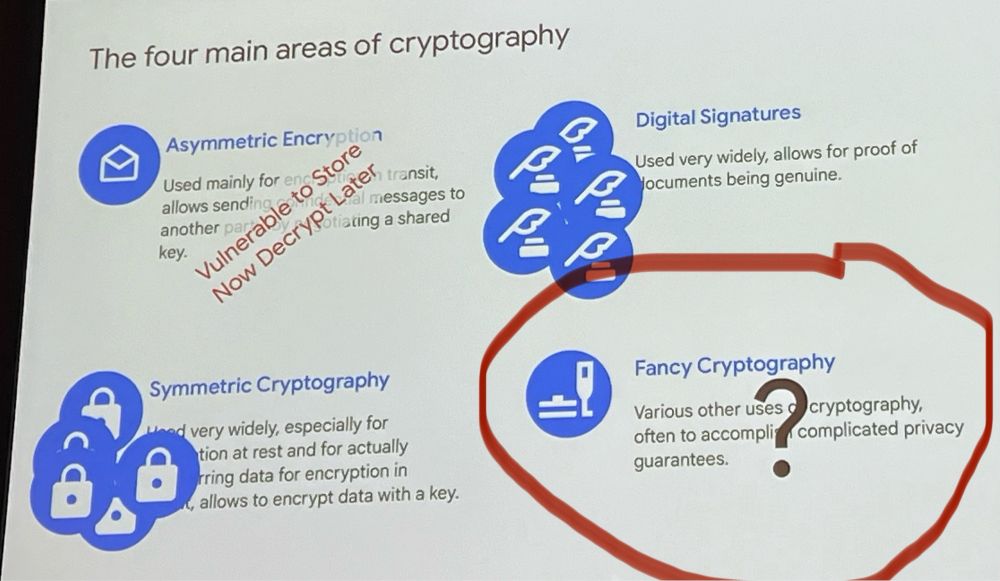
Changing my job title to “fancy cryptographer” thanks #RealWorldCrypto
25.03.2024 15:11 — 👍 18 🔁 2 💬 1 📌 0
Abstract. Threshold Schnorr signatures are seeing increased adoption in practice, and offer practical defenses against single points of failure. However, one challenge with existing randomized threshold Schnorr signature schemes is that signers must carefully maintain secret state across signing rounds, while also ensuring that state is deleted after a signing session is completed. Failure to do so will result in a fatal key-recovery attack by re-use of nonces. While deterministic threshold Schnorr signatures that mitigate this issue exist in the literature, all prior schemes incur high complexity and performance overhead in comparison to their randomized equivalents. In this work, we seek the best of both worlds; a deterministic and stateless threshold Schnorr signature scheme that is also simple and efficient. Towards this goal, we present Arctic, a lightweight two-round threshold Schnorr signature that is deterministic, and therefore does not require participants to maintain state between signing rounds. As a building block, we formalize the notion of a Verifiable Pseudorandom Secret Sharing (VPSS) scheme, and define Shine, an efficient VPSS construction. Shine is secure when the total number of participants is at least 2t − 1 and the adversary is assumed to corrupt at most t − 1; i.e., in the honest majority model. We prove that Arctic is secure under the discrete logarithm assumption in the random oracle model, similarly assuming at minimum 2t − 1 number of signers and a corruption threshold of at most t − 1. For moderately sized groups (i.e., when n ≤ 20), Arctic is more than an order of magnitude more efficient than prior deterministic threshold Schnorr signatures in the literature. For small groups where n ≤ 10, Arctic is three orders of magnitude more efficient.
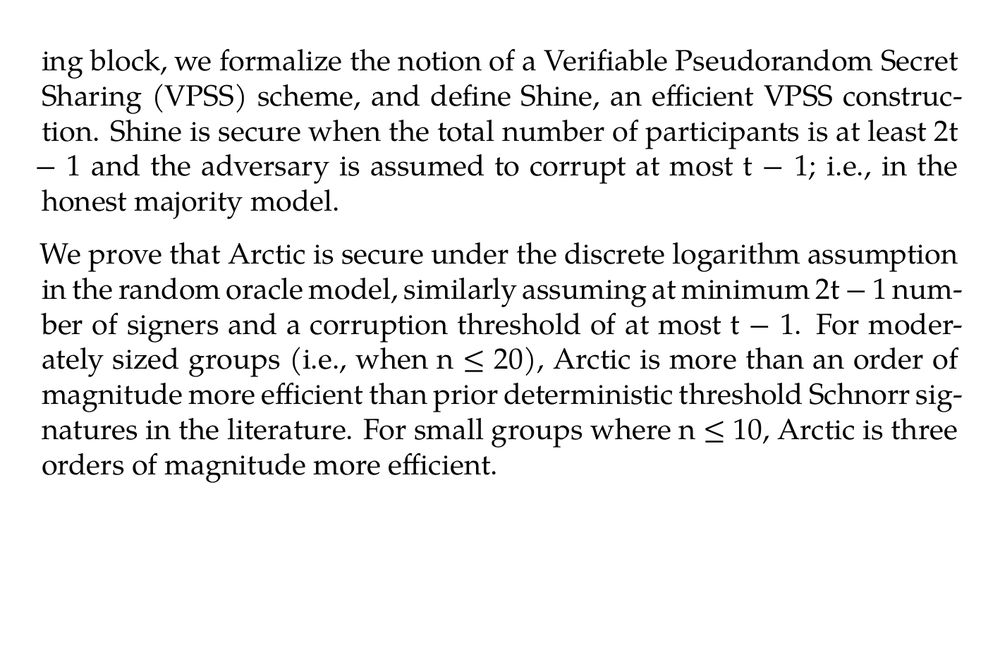
Image showing part 2 of abstract.
Arctic: Lightweight and Stateless Threshold Schnorr Signatures (Chelsea Komlo, Ian Goldberg) ia.cr/2024/466
22.03.2024 21:42 — 👍 5 🔁 3 💬 0 📌 0Hi Toronto! Looking forward to seeing everyone at #RealWorldCrypto 🇨🇦
21.03.2024 00:30 — 👍 4 🔁 0 💬 0 📌 0
I was asked today what the upper bound is on number of signers in threshold signature schemes used in practice today and I didn’t have a good answer…
I’m assuming consensus schemes are larger, but does anyone know of signing groups of > 20? That seems on the larger side
Apparently those leading the anti-diversity programs at US public universities believe “a healthy society requires patriarchy”- why in 2023 are women with voices and brains considered to be such a threat www.nytimes.com/interactive/...
22.01.2024 11:03 — 👍 3 🔁 2 💬 0 📌 0