

I have created a website, where you can share your sample analysis (via links or posts) and search samples for training based on tags and difficulty.
If you write analysis blogs, you can share them there.
samplepedia.cc
@pipzero.bsky.social
Information security practitioner. All things cti collection.


I have created a website, where you can share your sample analysis (via links or posts) and search samples for training based on tags and difficulty.
If you write analysis blogs, you can share them there.
samplepedia.cc

You can now pull Ghidra databases straight into your workflow in Binary Ninja 5.2! Open a .gbf on its own, import Ghidra data into an existing session, or bring parts of a full project into a Binary Ninja project on Commercial and above.
25.11.2025 21:30 — 👍 5 🔁 2 💬 1 📌 0
Members of Gen Digital Threat Labs uncover two new DPRK toolsets - Kimsuky’s HttpTroy backdoor and Lazarus’s upgraded BLINDINGCAN remote access tool - and explain how these tools work. www.gendigital.com/blog/insight...
03.11.2025 12:11 — 👍 1 🔁 1 💬 0 📌 0
🚨 The obfuscation game: MUT-9332 targets Solidity developers via malicious VS Code extensions!
Deep dive analysis in this obfuscated campaign including (PowerShell & VBS scripts, PE malware, Malicious browser extensions even stegomalware)
Enjoy reading securitylabs.datadoghq.com/articles/mut...

Leaving SF right in time before all the AI diarrhea. Thank you Hack The Bay and Pacific Hackers for having me, I’ll be back next year.
29.04.2025 03:19 — 👍 1 🔁 0 💬 0 📌 0
Catch me speaking intelligence collection at scale today at HackTheBay #PHACK
28.04.2025 20:07 — 👍 1 🔁 0 💬 0 📌 0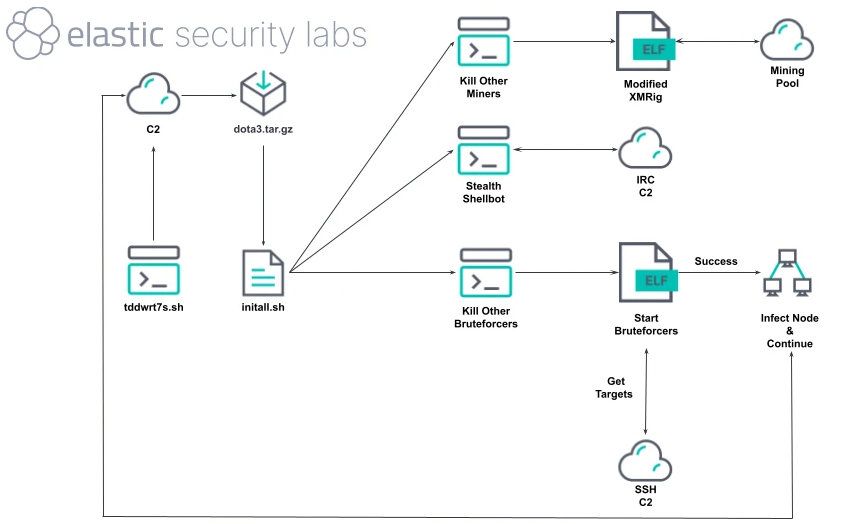
Diagram showing an overview of the OUTLAW infection chain.
Elastic Security Labs researchers report on Outlaw, a persistent yet unsophisticated auto-propagating Linux coinminer. Despite lacking stealth and advanced evasion techniques, it remains active and effective by leveraging simple but impactful tactics. www.elastic.co/security-lab...
02.04.2025 12:18 — 👍 2 🔁 1 💬 0 📌 0
Green card holders detained. A French researcher denied entry for anti-Trump messages. A new travel ban on 40+ countries coming.
Given all these encroachments on travelers' civil liberties, we've updated our guide to digital privacy while crossing US borders. www.wired.com/2017/02/guid...
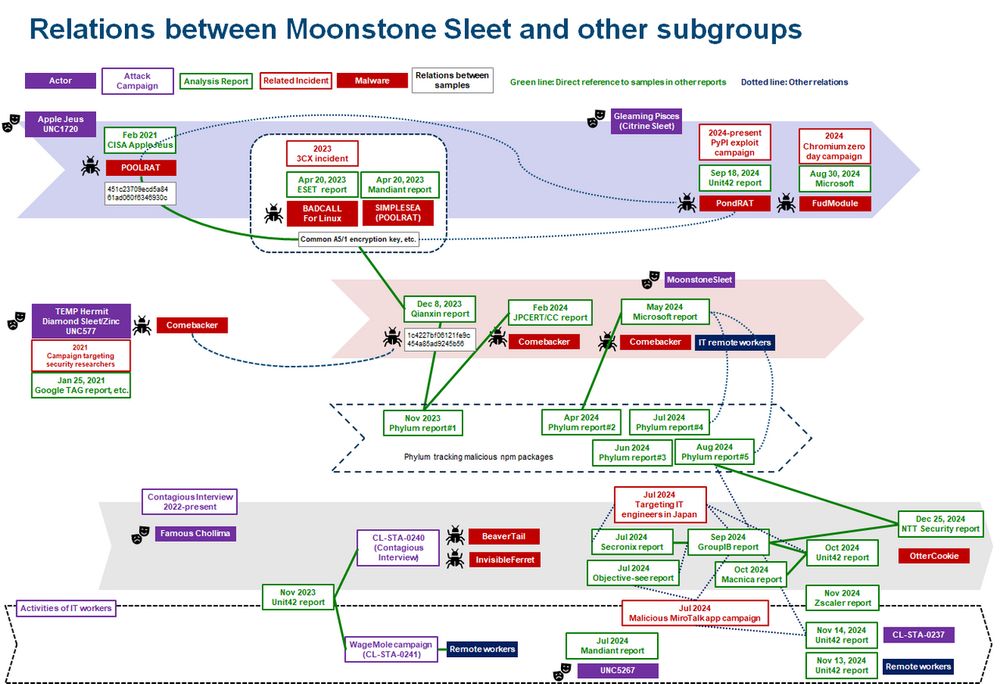
Graphic showing relations between Moonstone Sleet and other subgroups
JPCERT/CC's 佐々木 勇人 (Hayato Sasaki) looks into the practical challenges of attribution in the case of Lazarus’s subgroup. blogs.jpcert.or.jp/en/2025/03/c...
25.03.2025 13:58 — 👍 2 🔁 1 💬 0 📌 0Both Wiz and Palo Alto Networks have found evidence that the compromise of the Changed-Files GitHub Action might have been a complex multi-tier supply chain attack targeting tools used by Coinbase developers
www.wiz.io/blog/new-git...
unit42.paloaltonetworks.com/github-actio...
AI and blockchain software expert Armin Ranjbar released Landrun, a lightweight, secure sandbox for running Linux processes
github.com/Zouuup/landrun

Someone has done an excellent job collecting RATs and documenting them by version. They also included images.
A+ work. This is amazing (we're going to ingest this eventually)
github.com/Cryakl/Ultim...
⚠️🧵 RL researchers have found 2 malicious #VSCode extensions, "ahban.shiba" & "ahban.cychelloworld," that deliver #ransomware in development to it's users. #Dev #SoftwareSupplyChainSecurity
19.03.2025 13:46 — 👍 8 🔁 9 💬 1 📌 0
Just over 600 GitHub repos were impacted by Changed-Files supply chain attack
www.endorlabs.com/learn/blast-...

Podcast: risky.biz/RBNEWS400/ (400, woohoo! 🎉)
Newsletter: risky.biz/risky-bullet...
-China says Taiwan's military is behind PoisonIvy APT
-Google buys Wiz for $32 billion
-11 APTs abuse a Windows zero-day
-Judge tells CISA to reinstate fired workers
-Supply-chain attack hits car dealership sites

If you're critical of the US government and you are planning to cross the US border any time soon, today is a good day to review EFF's border search pocket guide: www.eff.org/document/eff...
19.03.2025 19:46 — 👍 2354 🔁 1443 💬 66 📌 73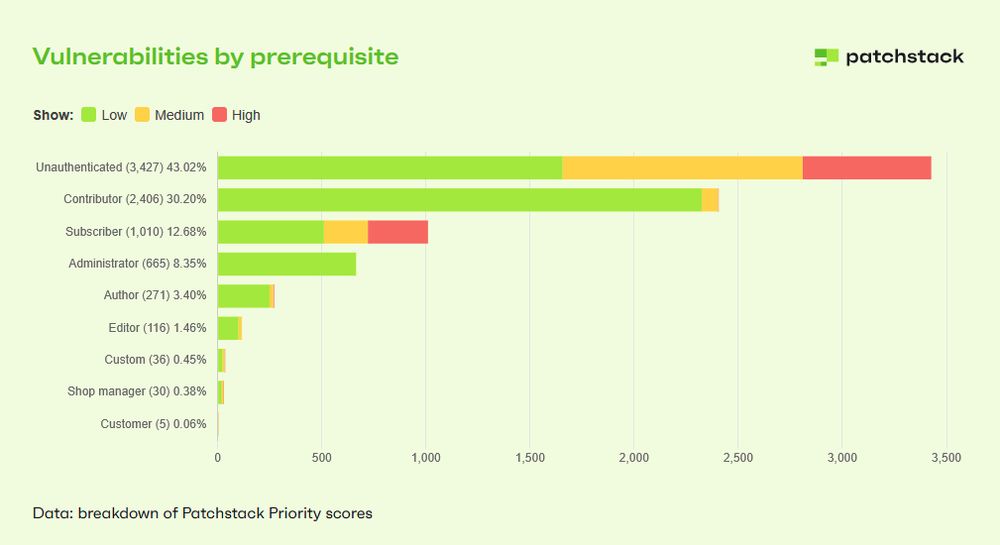
-43% of WP vulns last year didn't require authentication to exploit
-96% of WP vulns impacted plugins
-22 new WP vulns published daily
-over 500k WP websites hacked last year
patchstack.com/whitepaper/s...
Introducing MalChela. A YARA and Malware Analysis utility written in Rust. #DFIR #MalwareAnalysis #YARA #Hashing
03.03.2025 20:10 — 👍 7 🔁 3 💬 0 📌 0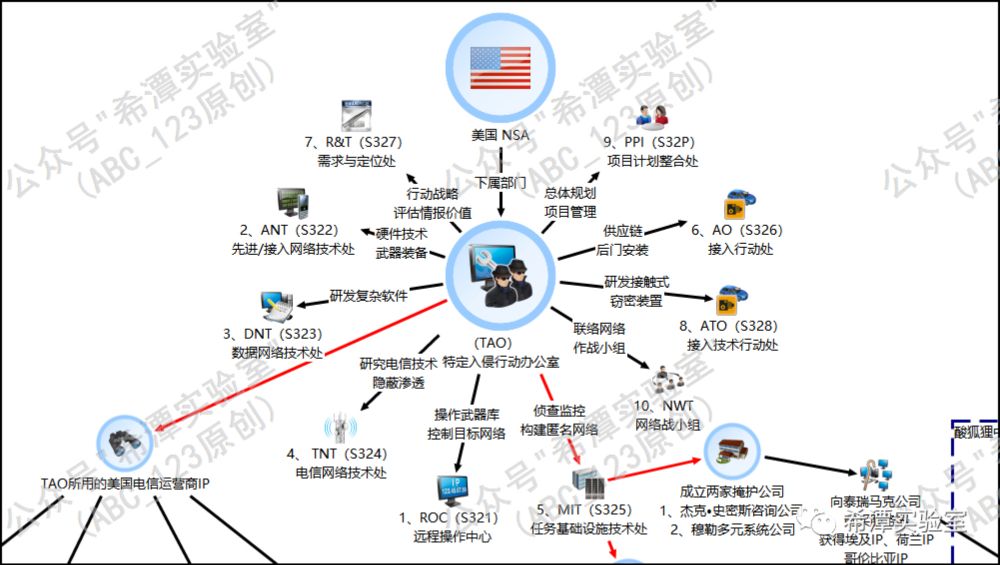
Xintra founder Lina Lau has published a report that untangles and puts more clarity on how Chinese authorities claim the Equation Group (US NSA) hacked the Xi'an Northwestern Polytechnical University
www.inversecos.com/2025/02/an-i...
Agenda for SunSecCon is up www.sunseccon.org
05.02.2025 22:39 — 👍 0 🔁 0 💬 0 📌 0
Threat insights from Datadog Security Labs for Q4 2024
securitylabs.datadoghq.com/articles/202...
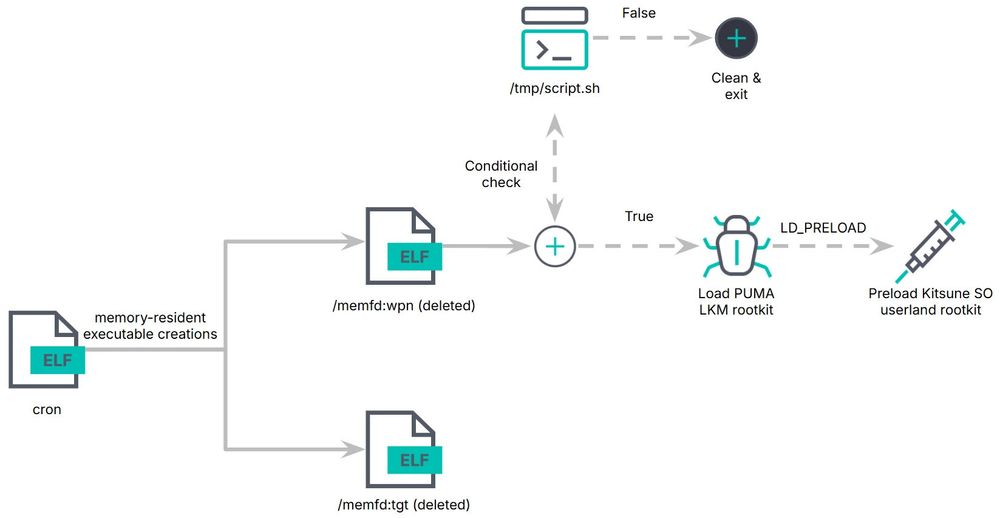
Elastic Security Labs' Remco Sprooten & Ruben Groenewoud analyse PUMAKIT, a loadable kernel module (LKM) rootkit that employs advanced stealth mechanisms to hide its presence and maintain communication with command-and-control servers. www.elastic.co/security-lab...
20.01.2025 10:31 — 👍 0 🔁 1 💬 0 📌 0Link? If you can.
08.01.2025 02:10 — 👍 0 🔁 0 💬 1 📌 0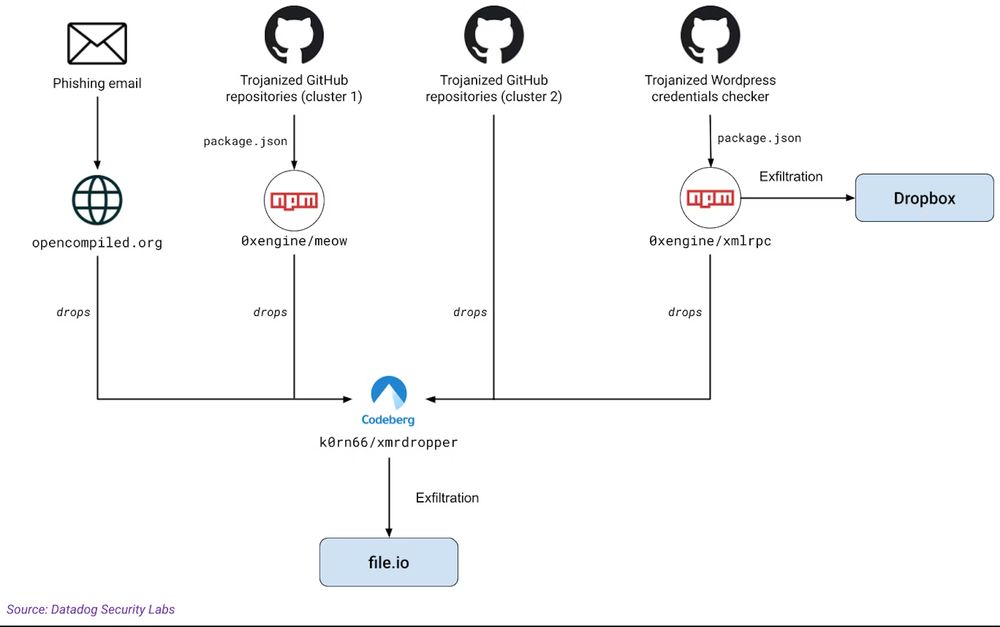
Overview of the attack flow
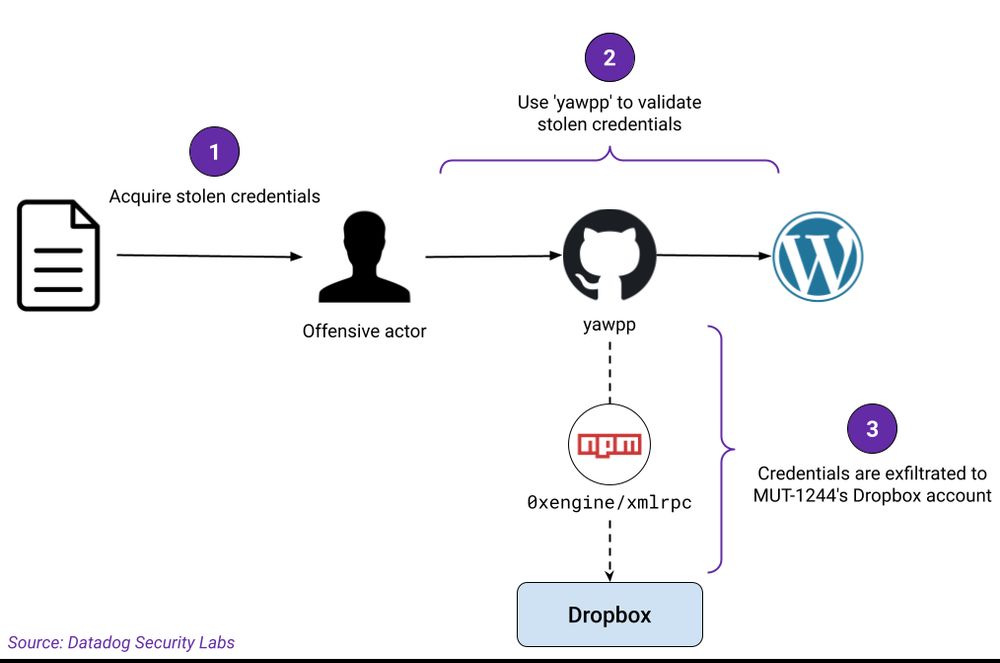
Overview of how a large number of credentials were leaked
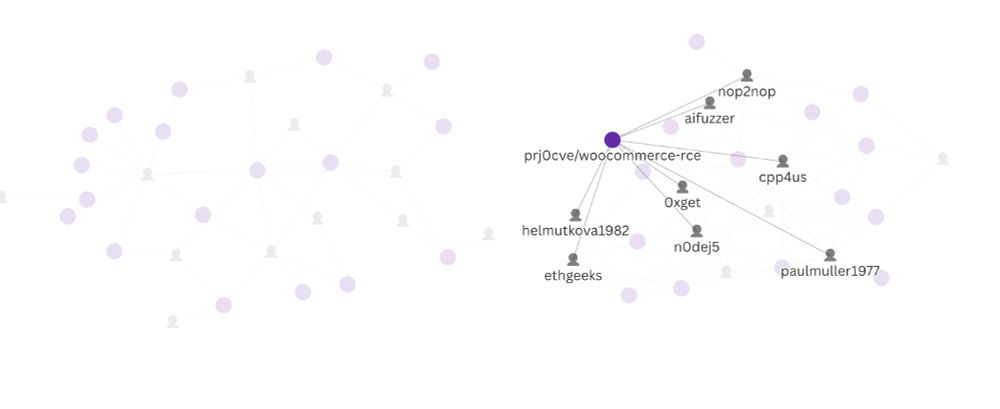
Clusters of fake GitHub profiles
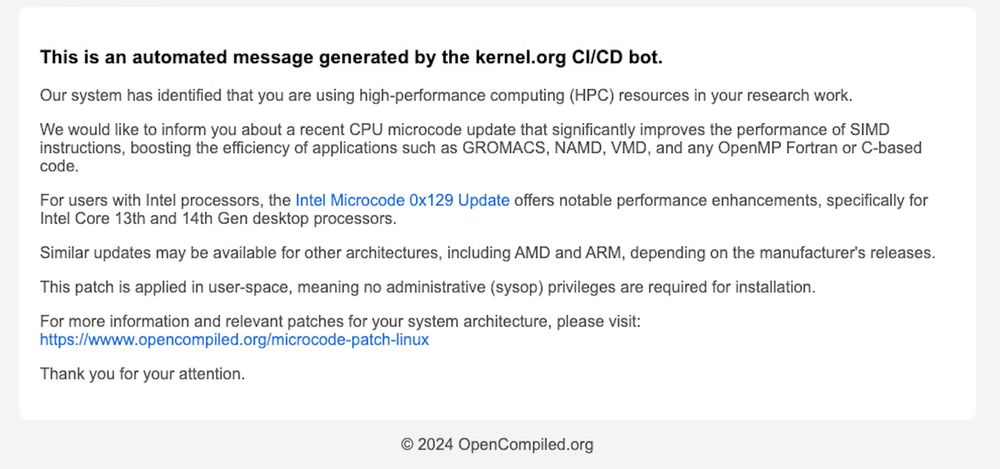
Phishing e-mail
New research: We've been monitoring a threat actor publishing dozens of trojanized GitHub repositories targeting threat actors, leaking hundreds of thousands of credentials along the way
securitylabs.datadoghq.com/articles/mut...

We are happy to introduce our latest tool "Supply Chain Firewall" 🎉 by @ikretz.bsky.social
The tool detects & prevents installation of malicious packages in local development environment.
Read more
securitylabs.datadoghq.com/articles/int...
And give it a try github.com/DataDog/supp...
Mistakes happen to everyone!
❤️ @binaryninja.bsky.social
Exclusive: The backdoor inserted in v1.95.7 adds an "addToQueue" function which exfiltrates the private key through seemingly-legitimate CloudFlare headers.
Calls to this function are then inserted in various places that (legitimately) access the private key.

🚨 A supply chain attack has been detected in versions 1.95.6 and 1.95.7 of the popular #Solana web3.js library. The injected code captures private keys and transmits them to a hardcoded address. This is a developing story. socket.dev/blog/supply-... #crypto #cybersecurity
03.12.2024 22:10 — 👍 14 🔁 8 💬 0 📌 3PHACK, some friends and I are creating a Security track in the famous SCALE in LA (Pasadena). CFP is open and early birds tickets are for sale!
If your in LA come check us out! www.sunseccon.org www.phack.org www.socallinuxexpo.org/scale/22x
@socallinuxexpo.bsky.social #infosec
Sites that don’t let you copy/paste in the password field.
Let me try to type this 24 char (because the site doesn’t allow longer) randomly generated string.
Fail.
Reset password.
Let’s trying again…