Exploiting the Tesla Wall connector from its charge port connector
An interesting attack surface Over the past few years, Synacktiv has been analyzing Tesla vehicles for the Pwn2Own competition.
ICYMI, @synacktiv.com's Pwn2Own walkthrough, exploiting a Tesla Wall via the charging port is a good Friday read.
After a firmware downgrade, they found a debug shell via the access point used during setup, ultimately using this to gain EIP.
www.synacktiv.com/en/publicati...
18.07.2025 16:22 —
👍 0
🔁 1
💬 0
📌 0
Everyone needs to see this once in awhile.
09.06.2025 16:17 —
👍 0
🔁 1
💬 0
📌 0
Fuzz Introspector: enabling rapid fuzz introspection tool development
"Fuzz Introspector: enabling rapid fuzz introspection tool development" -- a new blog post on Fuzz Introspector and how it is moving into supporting analysis as a pure python library. #fuzzing #program-analysis See the blog post: adalogics.com/blog/fuzz-in...
14.02.2025 13:07 —
👍 3
🔁 1
💬 0
📌 1
AIScholar - Paper Database
aischolar.0x434b.dev Pretty cool project by @434b.bsky.social: A neat web interface to explore security (and in particular: Fuzzing) papers with AI summaries. Seems super useful to get/stay up to date with recent papers :)
04.02.2025 15:29 —
👍 10
🔁 6
💬 0
📌 0
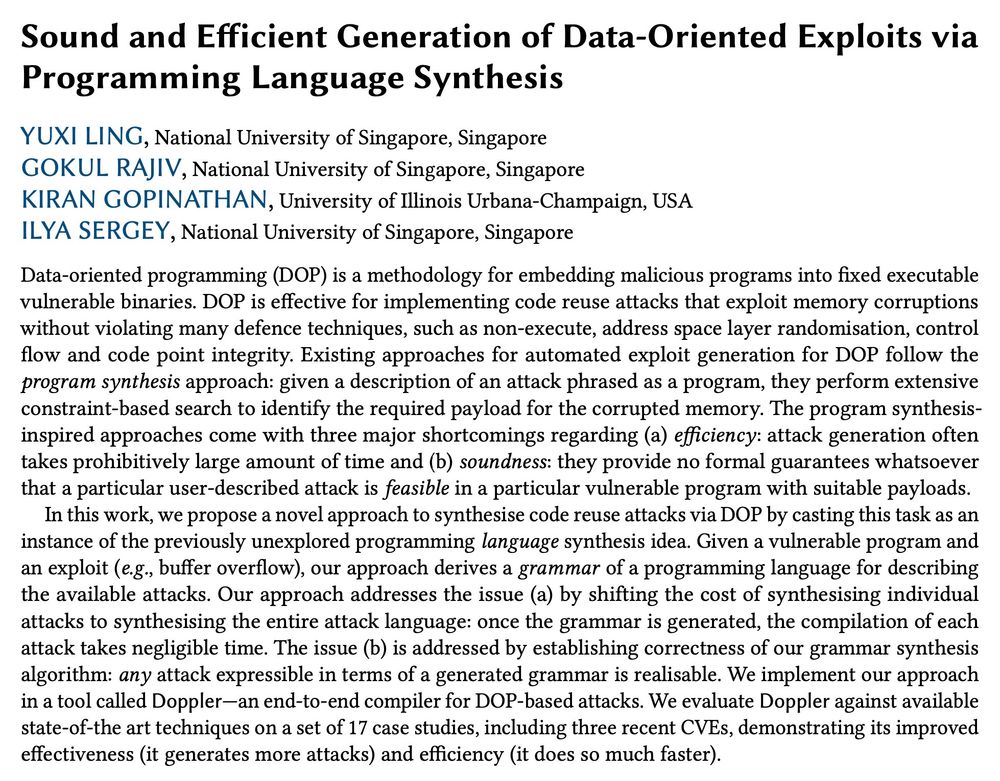
Our paper on efficient automated exploit generation has been accepted to USENIX Security '25.
The gist: instead of generating individual attacks, we synthesise the whole *programming language* that expresses many exploits and guarantees their realisability.
Paper: ilyasergey.net/assets/pdf/p...
02.02.2025 06:35 —
👍 47
🔁 7
💬 2
📌 0
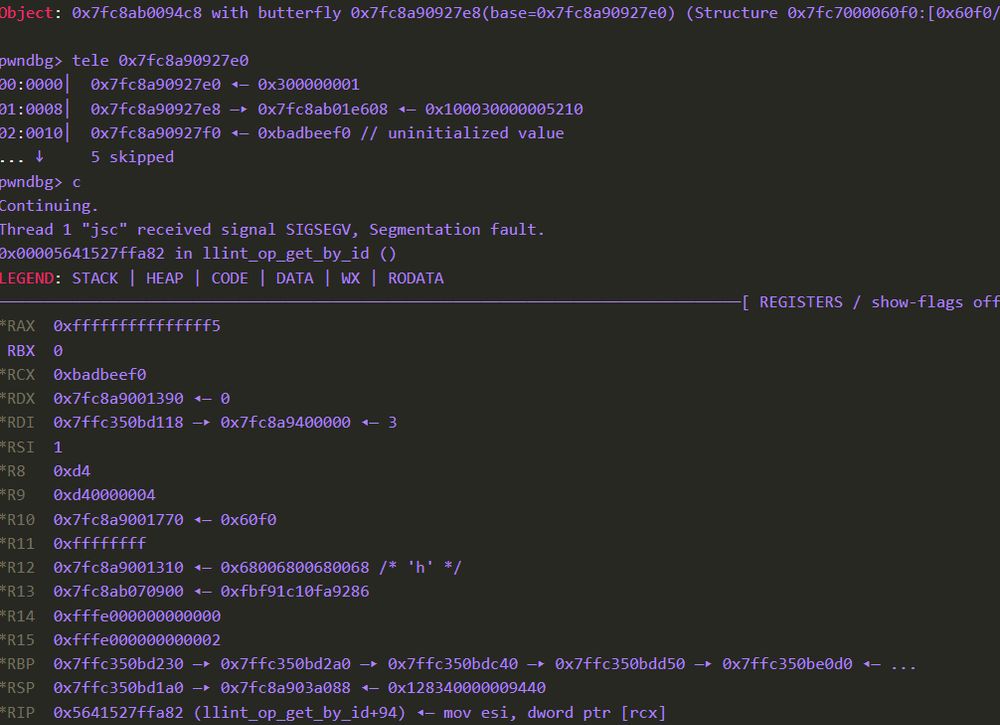
A Brief JavaScriptCore RCE Story:
qriousec.github.io/post/jsc-uni...
#cybersecurity #informationsecurity #rce #javascript #vulnerability
19.01.2025 14:31 —
👍 3
🔁 1
💬 0
📌 0
🥳📰 Very happy and proud that our paper on finding backdoors with fuzzing was accepted at the main track of @icseconf.bsky.social!
More details to follow soon 🙂
Congratulations and thank you to my students Dimitri Kokkonis and Emilien Decoux and co-supervisor Stefano Zacchiroli!
20.01.2025 10:35 —
👍 9
🔁 2
💬 1
📌 0
Futex is an under-appreciated Linux system call that backs almost everything you do that involves concurrency behind the scenes. HuguesEvrard and I wrote a paper on using model checking to analyse futex-based concurrency primitives. Check it out! doc.ic.ac.uk/~afd/papers/...
20.01.2025 13:46 —
👍 2
🔁 2
💬 1
📌 1
2024 is almost done, so here’s a thread on my 5 favorite fuzzing papers published this year. In no particular order…🧵
30.12.2024 21:17 —
👍 6
🔁 2
💬 1
📌 0
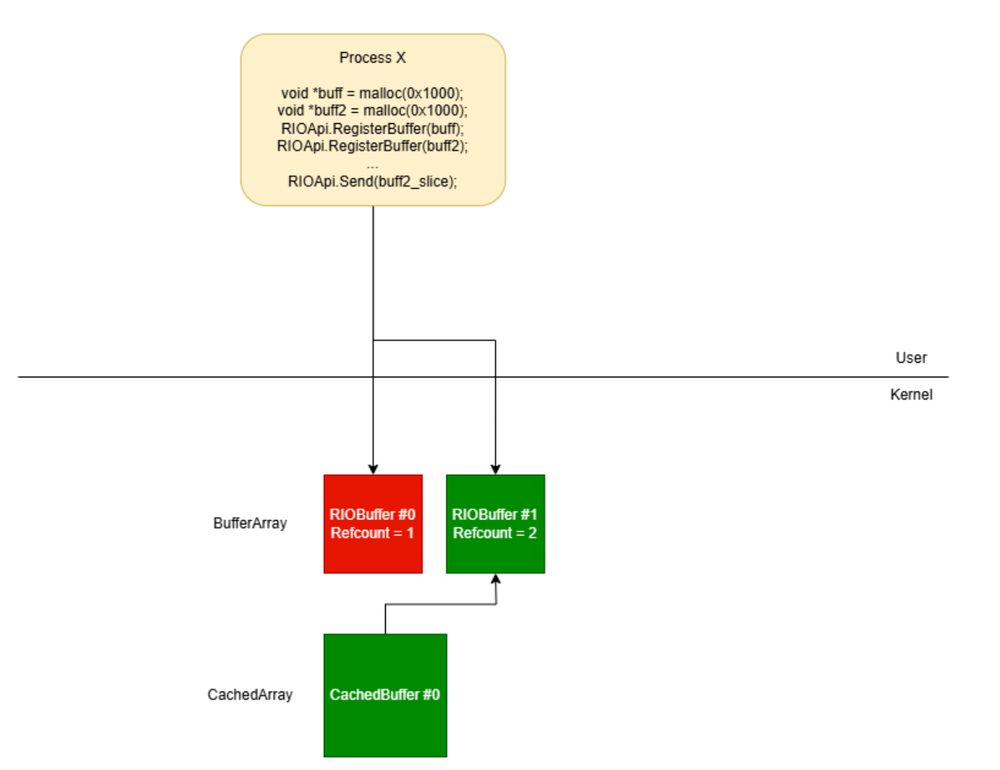
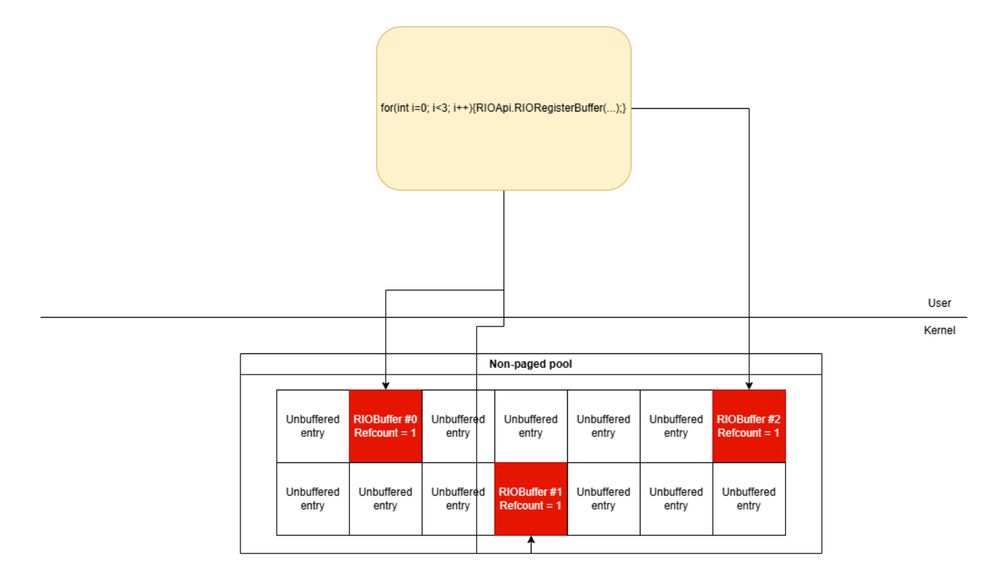
Exploiting a use-after-free vulnerability in the afd.sys Windows driver (CVE-2024-38193)
blog.exodusintel.com/2024/12/02/
Credits Luca Ginex
#windows #infosec
15.12.2024 11:20 —
👍 9
🔁 2
💬 0
📌 0
Pishi: Coverage guided macOS KEXT fuzzing.
This blog post is the result of some weekend research, where I delved into Pishi, a static macOS kernel binary rewriting tool. During the weekdays, I focus on Linux kernel security at my job and would...
This awesome fuzzing blog post by @r00tkitsmm.bsky.social covers a super reliable macOS kernel binary rewriting to instrument any KEXT or XNU at BB or edge level. Mandatory reading for anyone interested in fuzzing whether you use MacOS or not. So many good system internals and fuzzing references!
10.11.2024 02:21 —
👍 37
🔁 15
💬 2
📌 0