Tom Scott making good stuff as always (11 years ago)
youtu.be/RIuf1V1FhpY
@jade.packet.science
they/them PhD Student @cs.umass.edu Privacy-Enhancing Technologies && Internet Censorship Website: https://packet.science/

Tom Scott making good stuff as always (11 years ago)
youtu.be/RIuf1V1FhpY
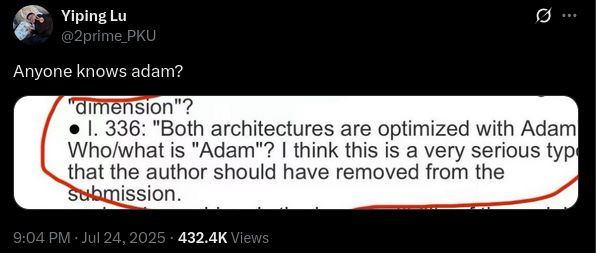
Getting into big security conferences may be difficult, but I'm grateful to have never seen anything as bad as "who is adam"
26.07.2025 02:01 — 👍 1 🔁 0 💬 0 📌 0
GWU was very welcoming of @pet-symposium.bsky.social attendees. The nearby whole foods, not so much.
19.07.2025 00:43 — 👍 0 🔁 0 💬 0 📌 0We found some other strange things too, like bizarre teredo-prefixed IPv6 addresses.
You can read the details in our extended abstract here
www.petsymposium.org/foci/2025/fo...
One of these IPs hosted a simple SSH server, implying some VPS got caught in the list somehow. But the other... is an *adult content website*.
In the process of trying to block human rights websites, the architects of the GFW send kids looking for Youtube videos to adult videos.
This approach bears suspicious resemblance to proposals by Fang Binxing (github.com/net4people/b...), the so-called "Father of the GFW".
Additionally, we found hosts in the GFW's injector pool that redirect users not just to these suspicious responding IPs, but to IPs *hosting content*
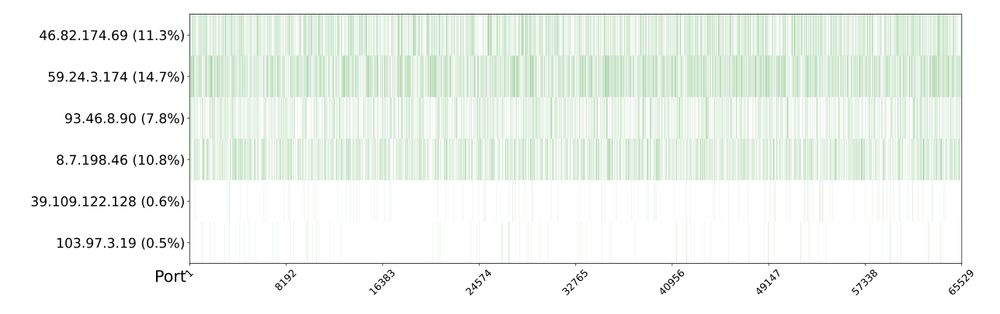
Of the 1922 IPv4 addresses we collected from the GFW's injectors, these 6 would respond on ports roughly distributed across the port spectrum
This strange phenomenon poses some risks. The GFW, or anyone else, could be using traffic received by these hosts to surveil censored users.
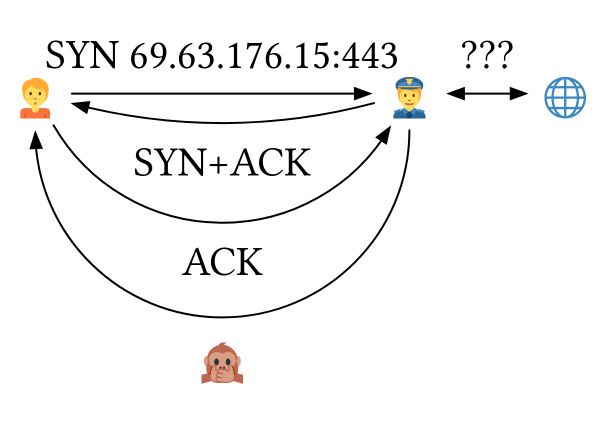
The inspiration for this work was a weird observation. Instead of just blackholing connections, some of the IPs injected by the GFW's DNS injector would respond with a S+A. (when you gaze into the abyss....)
16.07.2025 15:09 — 👍 0 🔁 0 💬 1 📌 0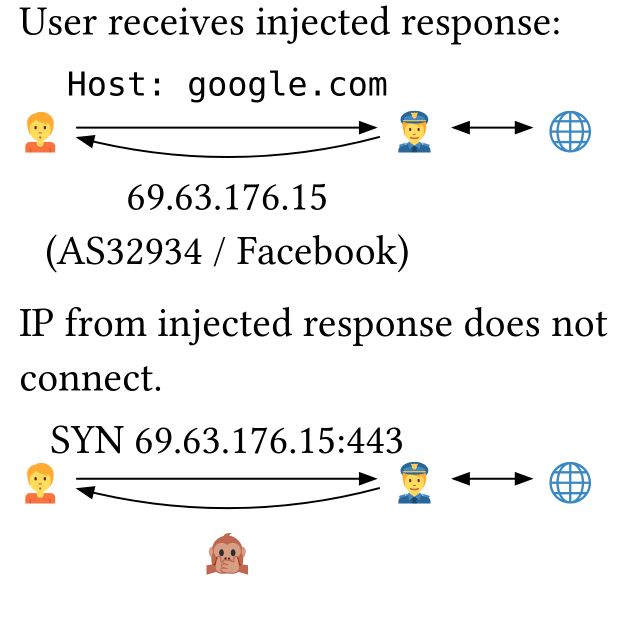
Users under China's censorship regime receive injected responses for bogus black-hole IP addresses when they try to do DNS lookups for censored domains. But what if those IPs weren't just bogus, but potentially malicious?
This week we presented our work: "I'll Shake Your Hand" to FOCI about this.
ICEBlock is incredibly false privacy claims for marketing. They falsely claim it provides complete anonymity when it doesn't. They're ignoring both data kept by Apple and data available to the server but not stored. They're also spreading misinformation about Android:
www.iceblock.app/android
I'm excited to start work for SPHERE (sphere-project.net) on reproducible internet censorship research this summer!
31.05.2025 14:48 — 👍 0 🔁 0 💬 0 📌 0OTF President Laura Cunningham: The immediate consequence is that if this holds, over 45 million people will lose access to trusted and secure VPNs, leaving them exposed to authoritarian surveillance and persecution.
17.03.2025 19:27 — 👍 10 🔁 12 💬 0 📌 1
Someone passed this along: Mullvad is debuting a new traffic-analysis prevention service that adds generated cover traffic and uses constant packet sizes. mullvad.net/en/blog/intr...
06.03.2025 13:59 — 👍 55 🔁 10 💬 2 📌 0
Reminds me of this meme I have locked and loaded for something I'm about to assign students
01.03.2025 18:49 — 👍 4 🔁 2 💬 0 📌 0
So here’s a simple request to Apple. Apple iMessage needs to enable “disappearing messages.” And they need to do it soon. blog.cryptographyengineering.com/2025/03/01/d...
01.03.2025 17:02 — 👍 80 🔁 31 💬 4 📌 2My contribution to this work was ultimately fairly minor, though I'm really happy to see this published. I've been captivated by how China could allow such a critical vulnerability ever since first learning about this project.
26.02.2025 03:07 — 👍 1 🔁 0 💬 0 📌 0Wallbleed: A Memory Disclosure Vulnerability in the Great Firewall of China
gfw.report/publications...
Protip for anyone teaching a binary exploitation course: Gradescope's Docker container has ASLR enabled, but a cloud-init vm running in qemu-system-x86_64 does not :D
26.02.2025 00:11 — 👍 0 🔁 0 💬 0 📌 0Hello, world!
25.02.2025 23:51 — 👍 1 🔁 0 💬 0 📌 0