I'd like to thank all of our sponsors for 2025. I'd also really, really, really, want to thank @MDSecLabs, @TrustedSec, @TorGuard, ... and all the individual donors.
Thanks to you, I don't need to beg for money on the internet and can focus on kitty cat pictures and malware.
14.01.2026 19:20 — 👍 13 🔁 1 💬 0 📌 0

macOS DYLIB Injection at Scale: Designing a Self-Sufficient Loader
Let’s explore Dylib injection and Dylib proxying on macOS (the equivalent of Windows DLL injection)
Binary injection vulnerabilities can be found in many MacOS apps. Those may be abused to bypass EDR, hide backdoor, access memory, or bypass TCC!
DarwinOps provides
- An advanced injection vulnerability scanner
- A redteam scenario to exploit them
#redteam
blog.balliskit.com/macos-dylib-...
17.09.2025 16:25 — 👍 4 🔁 2 💬 0 📌 0
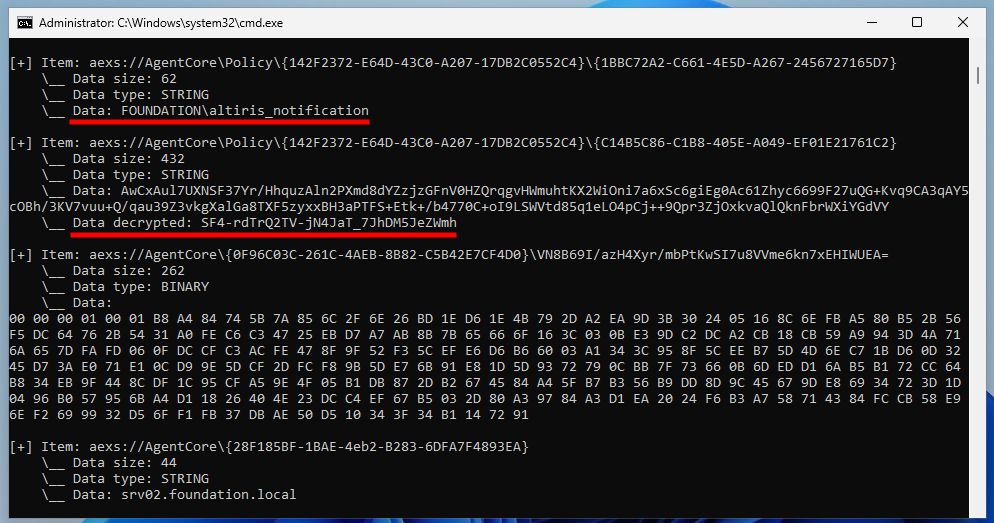
Screenshot showing the output of the proof-of-concept tool "SMAStorageDump", where ACCs are dully decrypted.
🆕 New blog post!
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
15.06.2025 16:33 — 👍 11 🔁 4 💬 3 📌 0
We are proud to introduce #dAWShund to the world: a framework for putting a leash on naughty AWS permissions. dAWShund helps blue and red teams find resources in #AWS, evaluate their access levels and visualize the relationships between them.
falconforce.nl/dawshund-fra...
#blueteaming #redteaming
11.04.2025 11:54 — 👍 11 🔁 3 💬 1 📌 0
With putty, there’s a nice little trick you can do to enable connection sharing and piggy back off their session… helps get around things like mfa 🙃
10.04.2025 21:49 — 👍 4 🔁 0 💬 1 📌 0

Our red team is growing and we have a rare open position for a Principal RT Operator - if this sounds like you, get in touch 🙏
09.04.2025 18:55 — 👍 4 🔁 3 💬 0 📌 0

Fileless lateral movement with trapped COM objects | IBM
New research from IBM X-Force Red has led to the development of a proof-of-concept fileless lateral movement technique by abusing trapped Component Object Model (COM) objects. Get the details.
[Blog] This ended up being a great applied research project with my co-worker Dylan Tran on weaponizing a technique for fileless DCOM lateral movement based on the original work of James Forshaw. Defensive recommendations provided.
- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...
25.03.2025 21:21 — 👍 15 🔁 11 💬 0 📌 1
Prodaft has published a technical analysis of Anubis, a new Python-based backdoor linked to Savage Ladybug (FIN7) operations
catalyst.prodaft.com/public/repor...
16.03.2025 10:39 — 👍 8 🔁 2 💬 0 📌 0
GitHub - decoder-it/KrbRelayEx-RPC
Contribute to decoder-it/KrbRelayEx-RPC development by creating an account on GitHub.
KrbRelayEx-RPC tool is out! 🎉
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
14.03.2025 10:18 — 👍 9 🔁 10 💬 0 📌 0

C2 Beaconing Detection with MDE Aggregated Report Telemetry
Detecting C2 Beaconing using MDE Aggregated Report Telemetry.
🚨 Detect C2 Beacons!
New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection!
🔗
academy.bluraven.io/blog/beaconi...
#ThreatHunting #DetectionEngineering #MDE
14.03.2025 14:13 — 👍 8 🔁 3 💬 0 📌 0
Haha you’re clutching at straws there!
You should be honoured to get my first post 😂
13.03.2025 06:02 — 👍 0 🔁 0 💬 1 📌 0
So when’s your last day at Fortra? 🙃
12.03.2025 22:11 — 👍 1 🔁 0 💬 1 📌 0

It appears Microsoft quietly mitigated most of the risk of the "Intune company portal" device compliance CA bypass by restricting the scope of Azure AD graph tokens issued to this app, making them almost useless for most abuse scenarios. Thx @domchell.bsky.social for the heads up.
20.02.2025 11:08 — 👍 29 🔁 9 💬 0 📌 0
Infosec, Detection Engineering, Threat Research, Threat Hunting, OffSec, Conference Organizer.
security "research" / opinions my own
Red Team | Co-Lead for @redteamvillage_ | OSCP
Windows Internals Author, Developer, Reverse Engineer, Security Researcher, Speaker, Trainer, and most recently Nation State Hacker.
Core OS Platform Developer at Apple, Hyper-V Vendor at Microsoft, Chief Architect at CrowdStrike and now Director at CSE.
Cybersecurity news, techniques, exploits, and tools every week at http://blog.badsectorlabs.com 🐘@badsectorlabs@infosec.exchange
Detection @Splunk | previously @nextronsystems | @sigma_hq & @magicswordio maintainer | Eternal Learner
Security researcher.
I have a blog: https://sapirxfed.com
Tester of Pens, Ex-Teamer of Red things, now with a more purpley shade. Biker and Recovering Eve-Online Addict. o7
https://blog.scriptmonkey.uk
Hunt & Response @ Huntress
Author of Constructing Defense
🇨🇦
Outsmart, Outmaneuver, Redefine the Tactics blog 👉 https://posts.redteamtacticsacademy.com/
learn 👉 https://masterclass.redteamtacticsacademy.com
[ 'cto @sensepost.com', '@orangecyberdef', 'caffeine fueled', '(╯°□°)╯︵ ┻━┻', 'security guy', 'metalhead', 'i saw your password', 'KOOBo+KXleKAv+KXlSnjgaM=' ]
MITRE ATT&CK® - A knowledge base for describing the behavior of adversaries. Replying/Following/Reposting ≠ endorsement.
Kerberoast Guy • RedSiege CEO • Hater of Pants • Former SANS 560 Author, Senior Instructor • Packers owner • Work Req: http://redsiege.com/contact
Sometimes I help stop bad people from doing bad things on the internet.
since 1985
https://phrack.org
Red Team enthusiast | Malware development enjoyer | Adversary Simulation at @quarkslab.bsky.social
I do security. Speaker at DEF CON, Black Hat, BSides. Building community @BSidesABQ, @OWASP. R&D @AIVillage_DC. YT @CyberDose. ☕️++
Geek, entrepreneur and criminologist working on threat intelligence led red teaming via Cyberdefense B.V. #TIBER #TLPT #RT











