github.com/SlimKQL/Hunt...
03.01.2025 12:11 — 👍 0 🔁 0 💬 0 📌 0Steven Lim
@stevenlim.bsky.social
#Cybersecurity #Sentinel #DefenderXDR #KQL #Azure #M365 #KQLWizard https://detections.ai/user/KQLWizard
@stevenlim.bsky.social
#Cybersecurity #Sentinel #DefenderXDR #KQL #Azure #M365 #KQLWizard https://detections.ai/user/KQLWizard
github.com/SlimKQL/Hunt...
03.01.2025 12:11 — 👍 0 🔁 0 💬 0 📌 0
LDAPNightmare POC Detection
www.safebreach.com/blog/ldapnig...
Custom detection code:
github.com/SlimKQL/Hunt...
Custom detection code:
github.com/SlimKQL/Hunt...

𝗖𝘂𝘀𝘁𝗼𝗺 𝗗𝗲𝗳𝗲𝗻𝗱𝗲𝗿𝗫𝗗𝗥 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 - 𝗕𝗹𝗼𝗰𝗸𝗶𝗻𝗴 2️⃣4️⃣ 𝗠𝗮𝗹𝗶𝗰𝗶𝗼𝘂𝘀 𝗖𝗵𝗿𝗼𝗺𝗲 𝗘𝘅𝘁𝗲𝗻𝘀𝗶𝗼𝗻𝘀🛡️
www.extensiontotal.com/cyberhaven-i...

Hunting 16 Malicious Chrome Extension🔥
thehackernews.com/2024/12/16-c...
github.com/SlimKQL/Hunt...

🚨 Reports suggest US authorities may ban TP-Link Wi-Fi routers in 2025. Regulated industries, ensure your end users aren't connected to TP-Link routers. Use MDE discovery and DefenderXDR's SeenBy() to detect connections. 🛡️📡
22.12.2024 16:28 — 👍 1 🔁 0 💬 0 📌 0
Advanced Vishing KQL Detection by sending your Teams PSTN call log to ADX 🎯
www.trendmicro.com/en_us/resear...
Thanks! :) The threat actor social engineering attacks are targeting normal business users, uers with role are technical in nature and tend not to follow these type of instruction, hence I exclude this group of privilege roles users.
17.12.2024 07:28 — 👍 0 🔁 0 💬 1 📌 0
PowerShell Self-Pwn Detection
Proofpoint highlights a social engineering tactic where users are tricked into running malicious PowerShell scripts, leading to malware infections. Despite needing user interaction, the attack's success relies on clever social engineering.
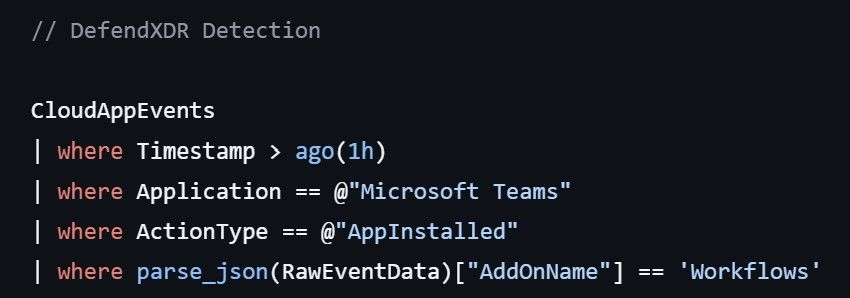
Detecting Teams Red Team Tool ConvoC2
cybersecuritynews.com/red-team-too...
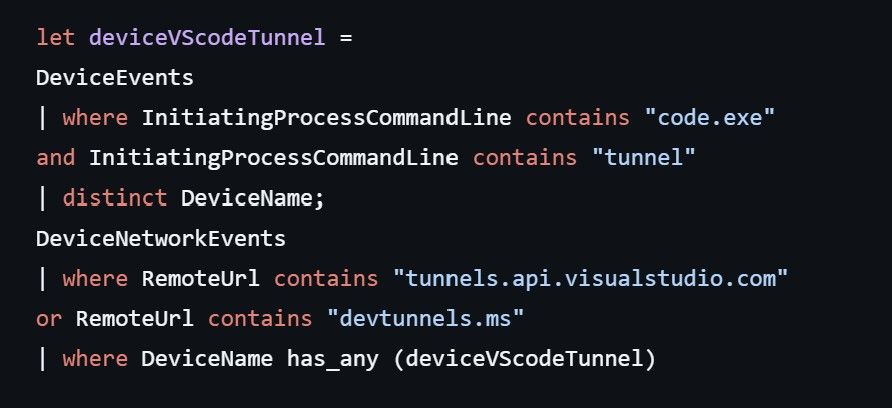
SentinelLab observed threat actor targeting service providers in Southern Europe abusing Visual Studio Code tunnels to maintain persistent remote access to compromised systems. www.bleepingcomputer.com/news/securit... KQL to detect such abuse.
10.12.2024 23:50 — 👍 2 🔁 1 💬 0 📌 0
Detect Black Basta Ransomware Campaign RMMTools Deployment - Social Engineering Attack via Teams where the ransomware operator sends a SharePoint link to user to download portable RMM tools to evade detection from web proxy. www.rapid7.com/blog/post/20...
10.12.2024 05:35 — 👍 2 🔁 0 💬 0 📌 0Thank you! 😄🙏
07.12.2024 09:11 — 👍 1 🔁 0 💬 0 📌 0
The KQL Grimoire 📖
A collection of the most sought-after KQL spells for Microsoft Sentinel and DefenderXDR
www.linkedin.com/pulse/slims-...

𝗡𝗲𝘄 𝗨𝗥𝗟 𝗙𝗶𝗹𝗲 𝗡𝗧𝗟𝗠 𝗛𝗮𝘀𝗵 𝗗𝗶𝘀𝗰𝗹𝗼𝘀𝘂𝗿𝗲 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝘆 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 (0️⃣𝗱𝗮𝘆)
A highly accurate DefenderXDR exposure management detection for URL File NTLM Hash Disclosure Vulnerability (0day) www.bleepingcomputer.com/news/securit...
github.com/SlimKQL/Hunt...
02.12.2024 06:01 — 👍 1 🔁 0 💬 0 📌 0
In AD environments, Timeroasting exploits NTP authentication to request password hashes of computer/trust accounts. If non-standard or legacy passwords are used, offline brute-forcing is possible. I've created a KQL query to detect such activities. #KQL #Timeroast
02.12.2024 06:01 — 👍 4 🔁 1 💬 2 📌 0github.com/SlimKQL/Hunt...
01.12.2024 12:38 — 👍 0 🔁 0 💬 0 📌 0
Sharing a Sentinel KQL detection for ShadowHound by Friends-Security, which enhances AD enumeration for security assessments. Beware: it can be misused by threat actors & red teamers for reconnaissance. My KQL rule helps identify and mitigate these risks. #KQL #ShadowHound
01.12.2024 12:37 — 👍 5 🔁 1 💬 1 📌 0
Hunting Rockstar 2FA:
github.com/SlimKQL/Hunt...

Hunting Rockstar 2FA: A Key Player in Phishing-as-a-Service (PaaS)
www.trustwave.com/en-us/resour...

KQL Code:
github.com/SlimKQL/Hunt...

Social Engineering Attack Alert - Teams & Emails
Kevin Beaumont shared insights on helping orgs recover from ransomware attacks. Key tactic: social engineering. Attackers used phone recon to gather contacts, then flooded users with emails & Teams messages. Custom KQL script for early detection:

CloudApp BEC Defense Policy - Axios
Attackers bypass MFA using a phishing framework with Axios HTTP client. Detect compromise in sign-in logs with user agent axios/1.7.7. Proposing auto-detection & isolation for SecOps assessment.
Sources: Asger Deleuran Strunk / Stephan Berger

𝗧𝗵𝗲 𝗣𝗲𝗿𝗳𝗲𝗰𝘁 𝗖𝘂𝘀𝘁𝗼𝗺 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 ... 😘
Using CloudApp & Behaviour Analytics to detect malicious threat actor Copilot Agent.
#Cybersecurity #DefenderXDR #CloudApp #CopilotAgent #KQL

Copilot Agent: The Good, the Bad, and the Ugly
www.linkedin.com/pulse/copilo...
KQL can be downloaded from my KQL repository:
github.com/SlimKQL/Hunt...

Phishing by Design: Two-Step Attacks Using .vsdx Files
I have crafted a precise KQL using Microsoft Defender for Office 365 and Endpoint to detect such abuse scenarios.
perception-point.io/blog/phishin...
#Cybersecurity #KQL #Phishing #Evasion #TrustedPlatform